The Future Comes Back Into The Equation For IT Spending
For nearly two years, the world has been coping with the coronavirus pandemic and it has had obvious and consequential effects on the market for hardware, software, and services in the datacenter. …
The Future Comes Back Into The Equation For IT Spending was written by Timothy Prickett Morgan at The Next Platform.
Designing Uber

This is a guest post by Ankit Sirmorya. Ankit is working as a Machine Learning Lead/Sr. Machine Learning Engineer at Amazon and has led several machine-learning initiatives across the Amazon ecosystem. Ankit has been working on applying machine learning to solve ambiguous business problems and improve customer experience. For instance, he created a platform for experimenting with different hypotheses on Amazon product pages using reinforcement learning techniques. Currently, he is in the Alexa Shopping organization where he is developing machine-learning-based solutions to send personalized reorder hints to customers for improving their experience.
Requirements
In Scope
More: Hardware Differences between Routers and Switches
Aaron Glenn sent me his thoughts on hardware differences between routers and switches based on the last paragraph of Dmytro Shypovalov’s views on the topic
To conclude, what is the difference between routers and switches in my opinion? I have absolutely no idea.
More: Hardware Differences between Routers and Switches
Aaron Glenn sent me his thoughts on hardware differences between routers and switches based on the last paragraph of Dmytro Shypovalov’s views on the topic
To conclude, what is the difference between routers and switches in my opinion? I have absolutely no idea.
Meta Buys, Rather Than Builds And Opens, Its Massive AI Supercomputer
If you thought it took a lot of compute and storage to build Facebook’s social network, you ain’t seen nothing yet. …
Meta Buys, Rather Than Builds And Opens, Its Massive AI Supercomputer was written by Timothy Prickett Morgan at The Next Platform.
What to Expect from Network as a Service (NaaS) Technology
NaaS is gaining momentum. Is your organization going to jump onboard?Tech Bytes: Managing SaaS Risks With Smarter, Cloud-Delivered Security (Sponsored)
On today’s Tech Bytes podcast, sponsored by Palo Alto Networks, we’re going to talk about how a SASE architecture and a next-generation CASB, or Cloud Access Security Broker, can help security teams manage SaaS risks.Tech Bytes: Managing SaaS Risks With Smarter, Cloud-Delivered Security (Sponsored)
On today’s Tech Bytes podcast, sponsored by Palo Alto Networks, we’re going to talk about how a SASE architecture and a next-generation CASB, or Cloud Access Security Broker, can help security teams manage SaaS risks.
The post Tech Bytes: Managing SaaS Risks With Smarter, Cloud-Delivered Security (Sponsored) appeared first on Packet Pushers.
Getting Started with Ansible.utils Collection for Playbook Creators: Part 2
Use Case: Operational state assessment using ansible.utils collection
In ansible.utils, there are a variety of plugins which we can use for operational state assessment of network devices. I overviewed the ansible.utils collection in part one of this two part blog series. If you have not reviewed part one, I recommend you do so, since I will build on this information in this part two blog. We will see how the ansible.utils collection can be useful in operational state assessment as an example use case.
In general, state assessment workflow has following steps:
-
Retrieve (Source of Truth)
- Collect the current operational state from the remote host.
- Convert it into normalized structured data. Structured data can be in json, yaml format or any other format.
- Store is an inventory variable.
Validate
- Define the desired state criteria in a standard based format, for example, as defined in a json schema format.
- Retrieve operational state at runtime.
- Validate the current state data against the pre-defined criteria to identify if there is any deviation.
Remediate
- Implement required configuration changes to correct drift.
- Report on the change as an audit trail.
How can ansible.utils collection Continue reading
Getting Started with Ansible.utils Collection for Playbook Creators: Part 1
The Ansible ansible.utils collection includes a variety of plugins that aid in the management, manipulation and visibility of data for the Ansible playbook developer. The most common use case for this collection is when you want to work with the complex data structures present in an Ansible playbook, inventory, or returned from modules. See each plugin documentation page for detailed examples for how these utilities can be used in tasks. In this two-part blog we will overview this collection in part one and see an example use case of using the utils collection in detail in part two.
Plugins inside ansible.utils
Plugins are code which will augment ansible core functionality. This code executes on control node.it and gives options and extensions for the core features of Red Hat Ansible Automation Platform. This ansible.utils plugin collection includes:
- Filter plugins
- Lookup plugins
- Test plugins
- Modules
Filter plugins
Filter plugins manipulate data. With the right filter you can extract a particular value, transform data types and formats, perform mathematical calculations, split and concatenate strings, insert dates and times, and do much more. Ansible Automation Platform uses the standard filters shipped with Jinja2 and adds some specialized filter Continue reading
Network Break 366: Microsoft Spends $68.7 Billion On Games; Wi-Fi 7 On The Horizon
Take a Network Break! This week we examine the drivers behind Microsoft's proposed $68.7 billion acquisition of gaming company Activision Blizzard, Juniper integrates its SD-WAN portfolio with Mist Cloud, and Wi-Fi 7 emerges on the horizon. Cisco announces a new Catalyst switch for industrial use cases, Telia Carrier rebrands, and JP Morgan Chase discloses tidbits about its IT strategy.Network Break 366: Microsoft Spends $68.7 Billion On Games; Wi-Fi 7 On The Horizon
Take a Network Break! This week we examine the drivers behind Microsoft's proposed $68.7 billion acquisition of gaming company Activision Blizzard, Juniper integrates its SD-WAN portfolio with Mist Cloud, and Wi-Fi 7 emerges on the horizon. Cisco announces a new Catalyst switch for industrial use cases, Telia Carrier rebrands, and JP Morgan Chase discloses tidbits about its IT strategy.
The post Network Break 366: Microsoft Spends $68.7 Billion On Games; Wi-Fi 7 On The Horizon appeared first on Packet Pushers.
Introducing New NSX Upgrade Capabilities for NSX-T 3.2
We’re introducing new capabilities to help our customers prepare for upgrading to the latest releases — now available with NSX-T Data Center 3.2.0.1.
To ensure that existing NSX deployments can be successfully upgraded to NSX-T Data Center 3.2.x, we have provided an NSX Upgrade Evaluation Tool that operates non-intrusively as a separate downloadable tool to check the health and readiness of your NSX Managers prior to upgrade. Using NSX Upgrade Evaluation Tool can help avoid potential upgrade failures and save time by avoiding a rollback from a failed upgrade.
Customers upgrading to NSX-T 3.2.x are strongly encouraged to review the Upgrade Checklist and run the NSX Upgrade Evaluation Tool before starting the upgrade process.
In what follows, we’ll go over the details of the NSX Upgrade Evaluation Tool:
- How the tool works
- When to use the tool
- What the tool can and cannot do
- How to use the tool
How the NSX Upgrade Evaluation Tool Works

The main component of the NSX Upgrade Evaluation Tool is the database where a copy of NSX objects will be stored. The tool starts by making a secure copy of the database from an existing NSX Manager Continue reading
Burkina Faso experiencing second major Internet disruption this year

The early hours of Sunday, January 23, 2022, started in Burkina Faso with an Internet outage or shutdown. Heavy gunfire in an army mutiny could be related to the outage according to the New York Times (“mobile Internet services were shut down”). As of today, there are three countries affected by major Internet disruptions — Tonga and Yemen are the others.
Cloudflare Radar shows that Internet traffic dropped significantly in the West African country after ~09:15 UTC (the same in local time) and remains low more than 24 hours later. Burkina Faso also had a mobile Internet shutdown on January 10, 2022, and another we reported in late November 2021.
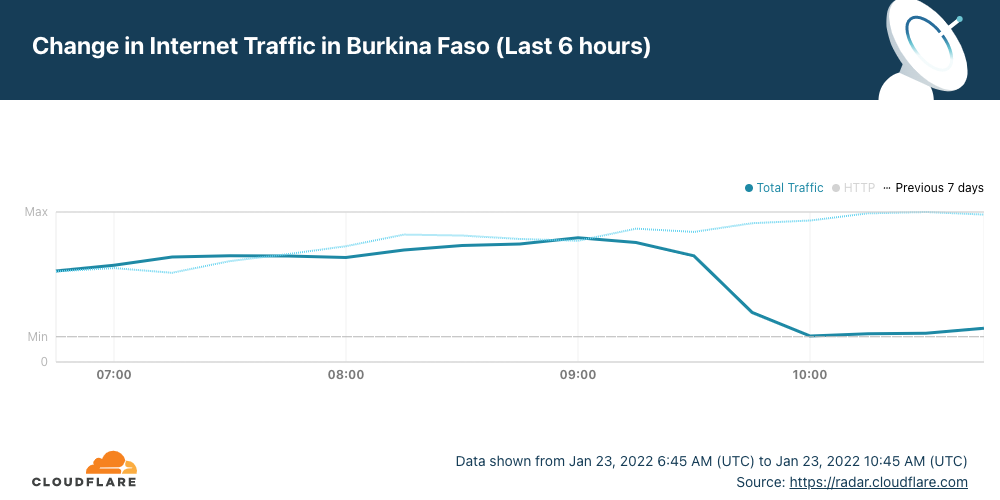
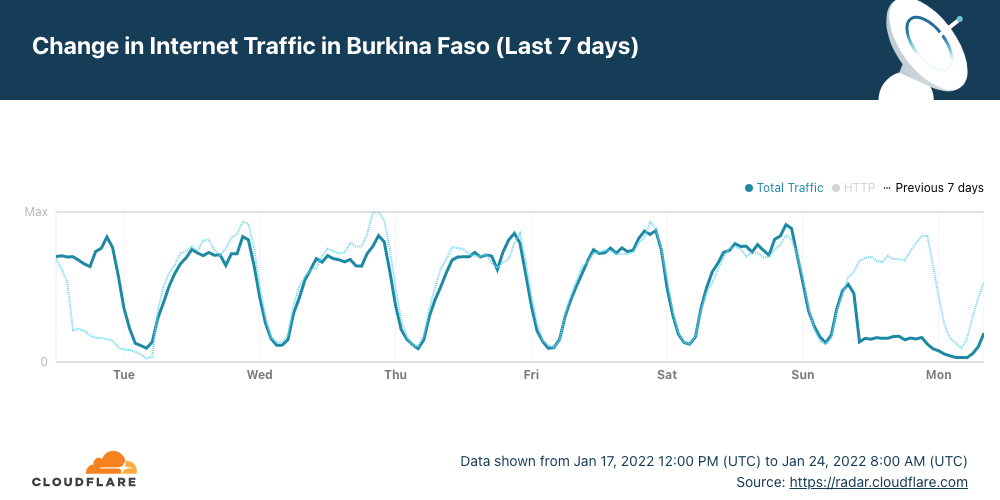
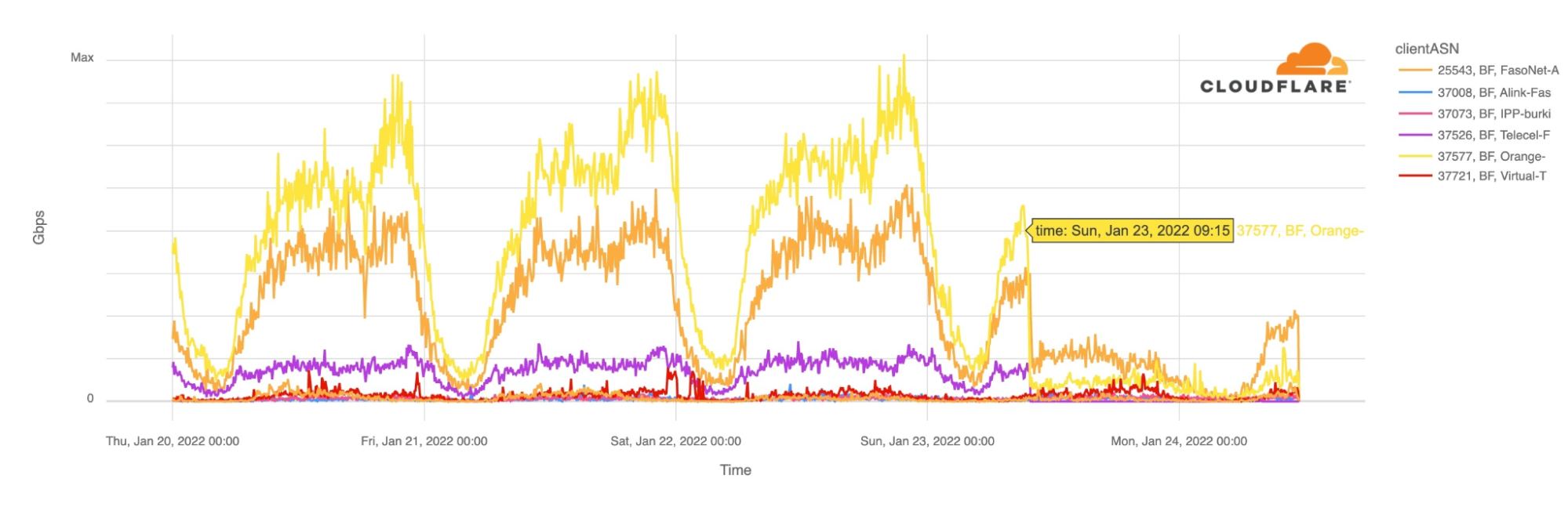
The main ISPs from Burkina Faso were affected. The two leading Internet Service Providers Orange and FasoNet lost Internet traffic after 09:15 UTC, but also Telecel Faso, as the next chart shows. This morning, at around 10:00 UTC there was some traffic from FasoNet but less than half of what we saw at the same time in preceding days.
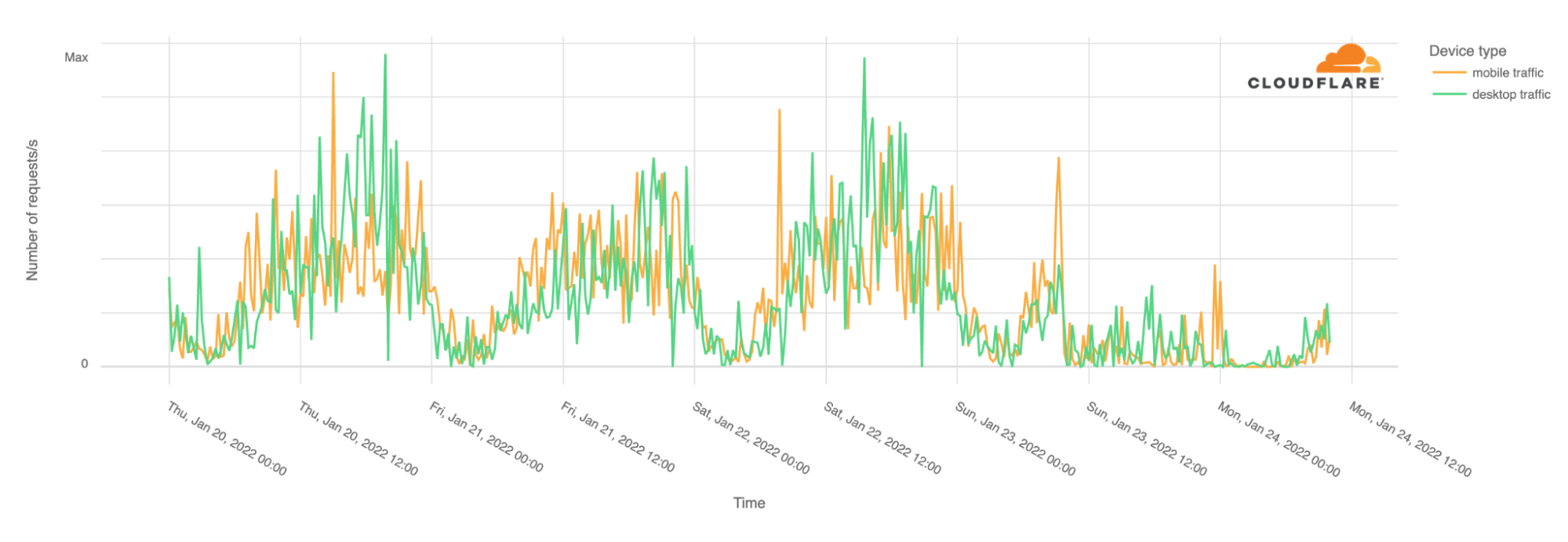
It’s not only mobile traffic that is affected. Desktop traffic is also impacted. In Burkina Faso, our data shows that mobile devices normally represent 70% of Internet traffic.
With the Burkina Continue reading