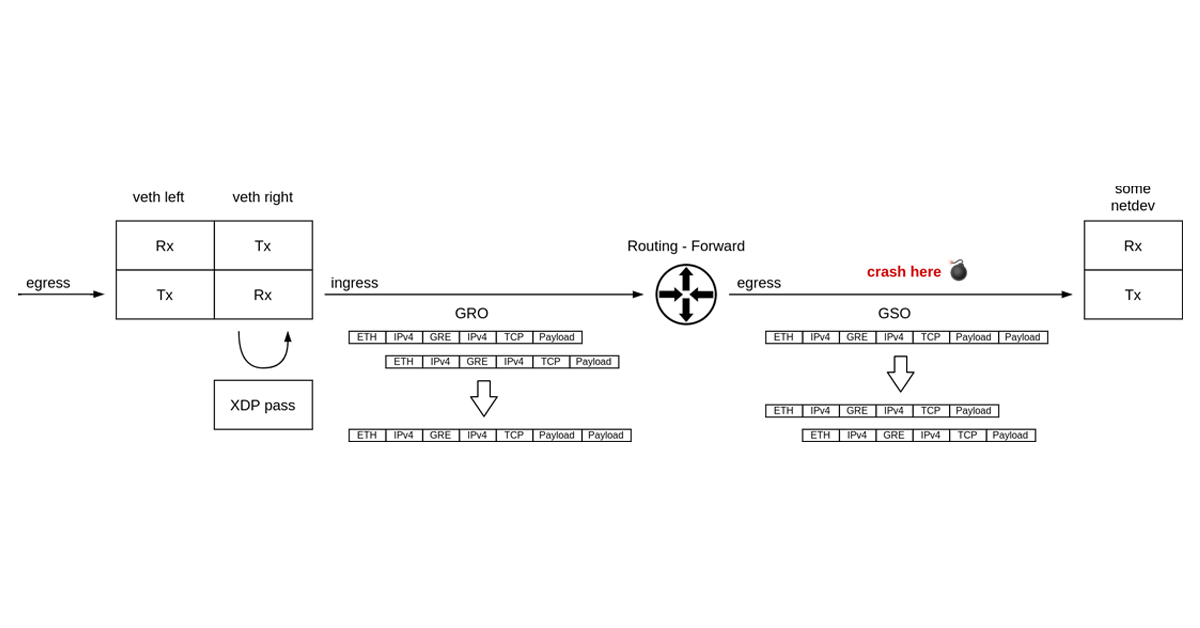
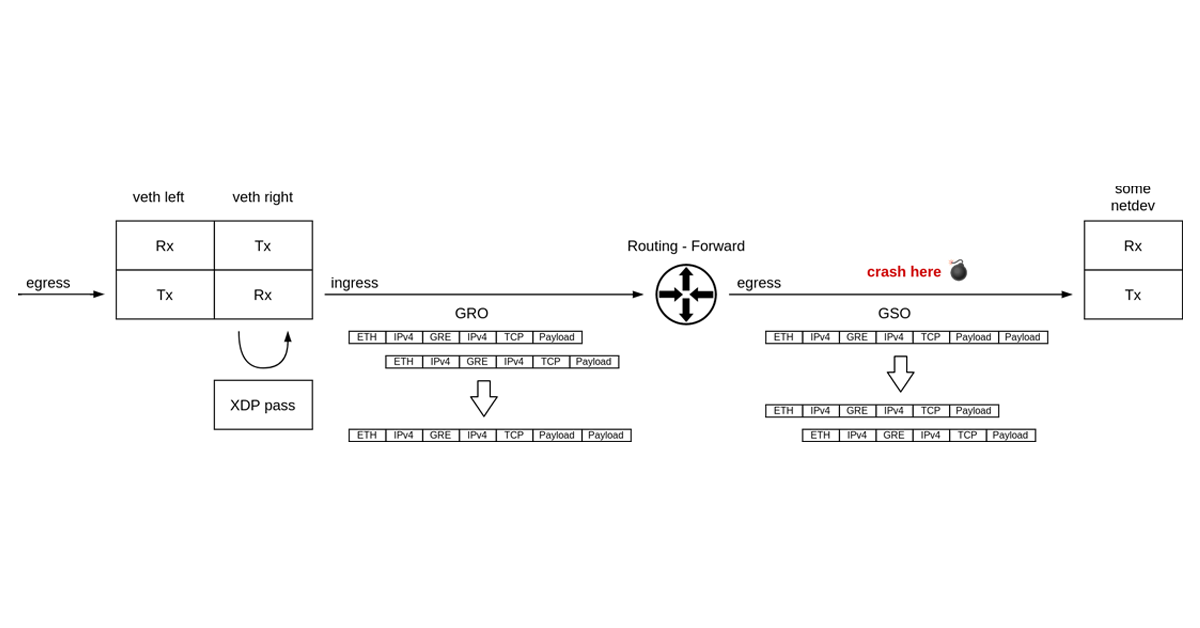
0
ITRenew has announced that Pluribus Netvisor ONE OS and the Adaptive Cloud Fabric controllerless SDN software are now available as part of Sesame by ITRenew rack-scale cloud solutions. Pluribus is very pleased to take part in this new circular approach to building data centers; one where we can deliver a cloud operating model with on-prem performance, while also helping our customers achieve their sustainability goals.
The timing of this partnership is apropos given the global attention to COP26, the United Nations Climate Change Conference and ongoing efforts worldwide to scale back emissions. While all industries have a responsibility on this front, the data center industry has specific, well-documented sustainability challenges that are only just starting to be properly addressed.
Most efforts to build the “green data center” have largely focused on increasing energy efficiency and using renewable energy sources, even though power used during the operational phase is only part of the problem. The bigger environmental culprit is that the industry continues to manufacture and deploy brand-new IT infrastructure equipment at a rapid pace.
In its report, “The Financial & Sustainability Case for Circularity,” ITRenew used a lifecycle model, assuming a typical 3-year operational lifetime for the equipment, Continue reading