Briefings In Brief 102: ZPE Systems Melds Universal CPE With Out-Of-Band Management
ZPE Systems presented at a recent Network Field Day. Founded in 2013, ZPE Systems focuses on two markets: providing out-of-band management for infrastructure, and providing universal CPE for remote and edge locations. The uCPE gear can run third-party VNFs, including firewalling and SD-WAN functions from your favorite vendors.
The post Briefings In Brief 102: ZPE Systems Melds Universal CPE With Out-Of-Band Management appeared first on Packet Pushers.
New in NFA v21.09: additional MPLS and pseudowire information elements, BGP community filtering/grouping capability, and more.
We have recently released the new Noction Flow Analyzer v 21.09, offering users a variety of new features and capabilities. Check out
The post New in NFA v21.09: additional MPLS and pseudowire information elements, BGP community filtering/grouping capability, and more. appeared first on Noction.
Launching New Services and Products at the Speed of Cloud: Automating Your Hardware Test Lab
Whether the concept behind a new product is evolutionary or revolutionary, launching new technology and services isn’t for the faint...
The post Launching New Services and Products at the Speed of Cloud: Automating Your Hardware Test Lab appeared first on Pluribus Networks.
Real-Time Communications at Scale


For every successful technology, there is a moment where its time comes. Something happens, usually external, to catalyze it — shifting it from being a good idea with promise, to a reality that we can’t imagine living without. Perhaps the best recent example was what happened to the cloud as a result of the introduction of the iPhone in 2007. Smartphones created a huge addressable market for small developers; and even big developers found their customer base could explode in a way that they couldn’t handle without access to public cloud infrastructure. Both wanted to be able to focus on building amazing applications, without having to worry about what lay underneath.
Last year, during the outbreak of COVID-19, a similar moment happened to real time communication. Being able to communicate is the lifeblood of any organization. Before 2020, much of it happened in meeting rooms in offices all around the world. But in March last year — that changed dramatically. Those meeting rooms suddenly were emptied. Fast-forward 18 months, and that massive shift in how we work has persisted.
While, undoubtedly, many organizations would not have been able to get by without the likes of Slack, Zoom and Teams as Continue reading
Serverless Live Streaming with Cloudflare Stream


We’re excited to introduce the open beta of Stream Live, an end-to-end scalable live-streaming platform that allows you to focus on growing your live video apps, not your codebase.
With Stream Live, you can painlessly grow your streaming app to scale to millions of concurrent broadcasters and millions of concurrent users. Start sending live video from mobile or desktop using the industry standard RTMPS protocol to millions of viewers instantly. Stream Live works with the most popular live video broadcasting software you already use, including ffmpeg, OBS or Zoom. Your broadcasts are automatically recorded, optimized and delivered using the Stream player.
When you are building your live infrastructure from scratch, you have to answer a few critical questions:
- “Which codec(s) are we going to use to encode the videos?”
- “Which protocols are we going to use to ingest and deliver videos?”
- “How are the different components going to impact latency?”
We built Stream Live, so you don’t have to think about these questions and spend considerable engineering effort answering them. Stream Live abstracts these pesky yet important implementation details by automatically choosing the most compatible codec and streaming protocol for the client device. There is no Continue reading
Announcing Cloudflare TV as a Service


In June 2020, Cloudflare TV made its debut: a 24/7 streaming video channel, focused on topics related to building a better Internet (and the people working toward that goal). Today, over 1,000 live shows later, we’re excited to announce that we're making the technology we used to build Cloudflare TV available to any other business that wants to run their own 24x7 streaming network. But, before we get to that, it’s worth reflecting on what it's been like for us to run one ourselves.
Let’s take it from the top.
Cloudflare TV began as an experiment in every way you could think of, one we hoped would help capture the serendipity of in-person events in a world where those were few and far between. It didn’t take long before we realized we had something special on our hands. Not only was the Cloudflare team thriving on-screen, showcasing an amazing array of talent and expertise — they were having a great time doing it. Cloudflare TV became a virtual watercooler, spiked with the adrenaline rush of live TV.
One of the amazing things about Cloudflare TV has been the breadth of content it’s inspired. Since launching, CFTV has hosted over 1,000 Continue reading
NSX-T Edge Transport Node Packet Capture
NSX-T v3.0.1 and v3.1.3 were used to try the stuff described below As always with network engineers, even when working with SDN/SSDC solutions, sooner or later you will be asked to troubleshoot connectivity across your hops. And if working with VMware NSX-T platform, your next-hop for the North-South Datacenter traffic will almost always be NSX-T EDGE Transport Node VM. It will be really useful then to be able to get some packet traces out of that box in order to troubleshoot the traffic issues in detail. One of the examples would be simple routing or some sort of Loadbalancing traffic
The post NSX-T Edge Transport Node Packet Capture appeared first on How Does Internet Work.
Increased interest in Spanish media after the La Palma volcanic eruption
The Internet is a valuable source of knowledge but also a deeply interesting, interconnected, and complex place. And with Cloudflare Radar (our Internet trends and insights free tool for everyone — including journalists, like I was for several years) you get a sense of different trends in the collection of networks that form the Internet.
We saw that over the past week or so in Spain. Radar shows a clear increase in interest in Spanish media outlets (in comparison with the preceding days and Sundays) after the news of the eruption in La Palma (one of the Spanish Canary Islands) broke on Sunday, September 19.
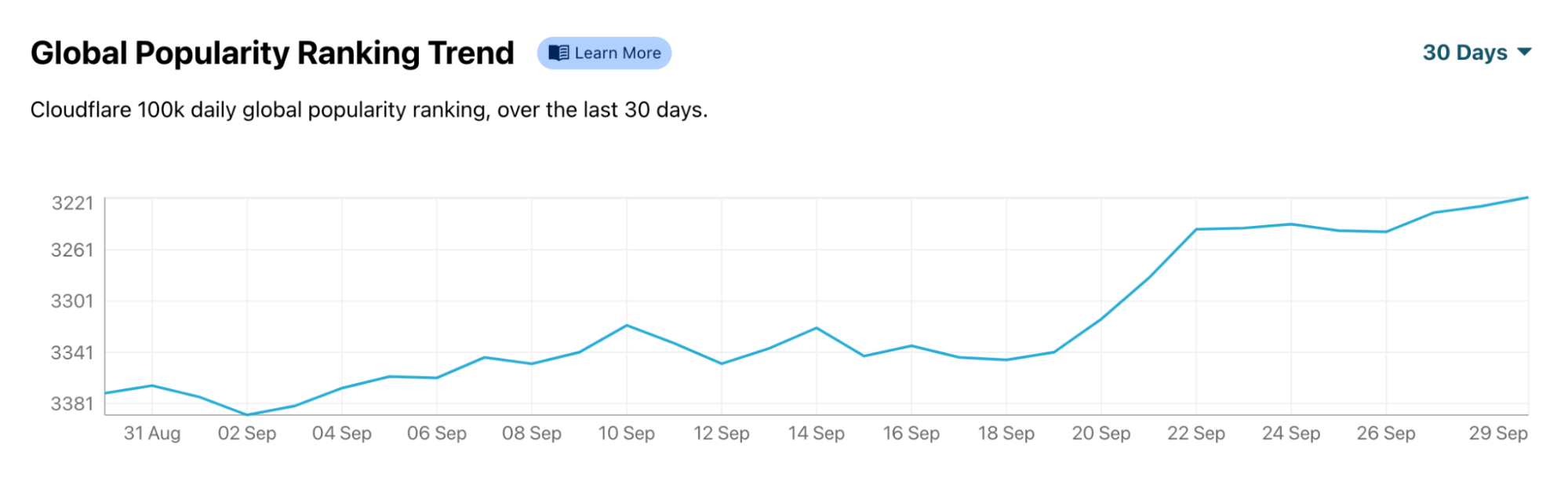
That is particularly clear looking at El País, one of the most well known media outlets in the country. Using our Global Popularity Ranking Trend available on Radar, we can see that ElPais.com jumped several positions in our ranking of most popular domains after September 19. That change is clear in the last seven days, but especially in the last 30, putting El País near the top 3,000 most popular domains in the world.
Elpais.com
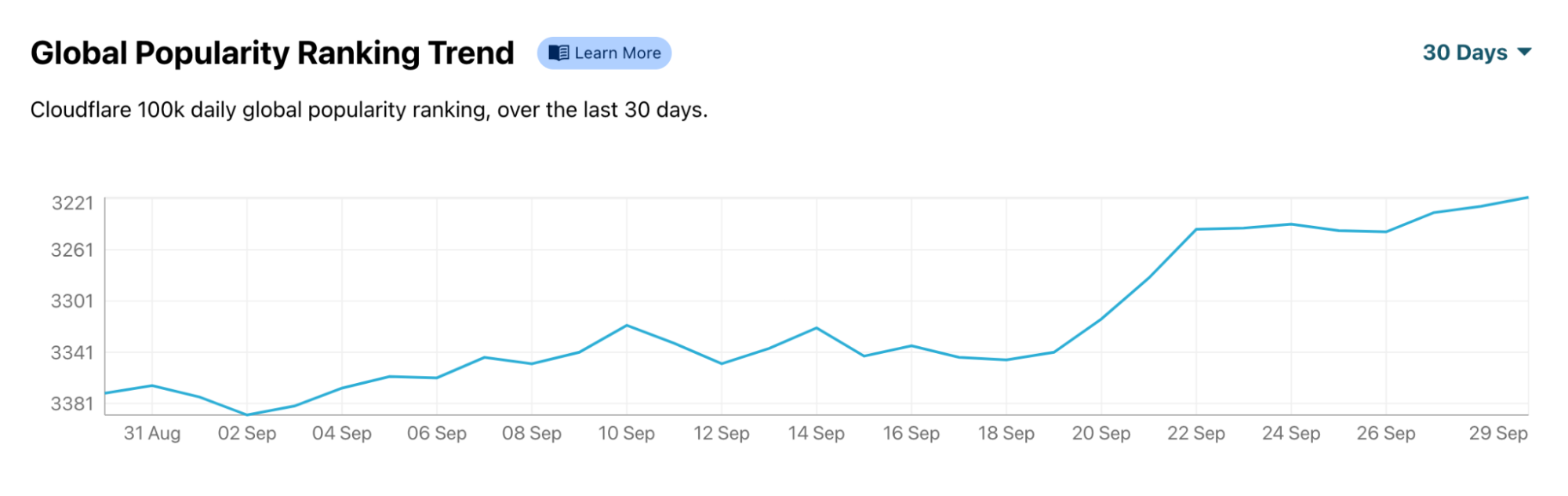
A similar trend is Continue reading
Reusing Underlay Network for Infrastructure Services
Boris Lazarov sent me an excellent question:
Does it make sense and are there any inherent problems from design perspective to use the underlay not only for transport of overlay packets, but also for some services. For example: VMWare cluster, vMotion, VXLAN traffic, and some basic infrastructure services that are prerequisite for the rest (DNS).
Before answering it, let’s define some terminology which will inevitably lead us to the it’s tunnels all the way down endstate.
Reusing Underlay Network for Infrastructure Services
Boris Lazarov sent me an excellent question:
Does it make sense and are there any inherent problems from design perspective to use the underlay not only for transport of overlay packets, but also for some services. For example: VMWare cluster, vMotion, VXLAN traffic, and some basic infrastructure services that are prerequisite for the rest (DNS).
Before answering it, let’s define some terminology which will inevitably lead us to the it’s tunnels all the way down endstate.
Pulumi Getting Started
Pulumi is an infrastructure as code tool that helps you build and manage environments such as AWS, Azure and GCP with the programming languages you already know. In this post, I will show you how to get up and running with Pulumi. Software The following software was used in this...continue reading
How Cloudflare provides tools to help keep IPFS users safe


Cloudflare's journey with IPFS started in 2018 when we announced a public gateway for the distributed web. Since then, the number of infrastructure providers for the InterPlanetary FileSystem (IPFS) has grown and matured substantially. This is a huge benefit for users and application developers as they have the ability to choose their infrastructure providers.
Today, we’re excited to announce new secure filtering capabilities in IPFS. The Cloudflare IPFS module is a tool to protect users from threats like phishing and ransomware. We believe that other participants in the network should have the same ability. We are releasing that software as open source, for the benefit of the entire community.
Its code is available on github.com/cloudflare/go-ipfs. To understand how we built it and how to use it, read on.
A brief introduction on IPFS content retrieval
Before we get to understand how IPFS filtering works, we need to dive a little deeper into the operation of an IPFS node.
The InterPlanetary FileSystem (IPFS) is a peer-to-peer network for storing content on a distributed file system. It is composed of a set of computers called nodes that store and relay content using a common addressing system.
Nodes communicate with each other Continue reading
AMD Draws 30X Efficiency Increase Line In The Datacenter Silicon
If you don’t measure something, you can’t manage it. And if you don’t set ambitious goals, then you can’t attain them. …
AMD Draws 30X Efficiency Increase Line In The Datacenter Silicon was written by Timothy Prickett Morgan at The Next Platform.