Uganda’s January 13, 2021 Internet Shut Down
Two days ago, through its communications regulator, Uganda's government ordered the "Suspension Of The Operation Of Internet Gateways" the day before the country's general election. This action was confirmed by several users and journalists who got access to the letter sent to Internet providers. In other words, the government effectively cut off Internet access from the population to the rest of the world.
Ahead of tomorrow’s election the Internet has been shutdown in Uganda (confirmed by a few friends in Kampala).
— Samira Sawlani (@samirasawlani) January 13, 2021
Letter from communications commission below: pic.twitter.com/tRpTIXTPcW
On Cloudflare Radar, we want to help anyone understand what happens on the Internet. We are continually monitoring our network and exposing insights, threats, and trends based on the aggregated data that we see.
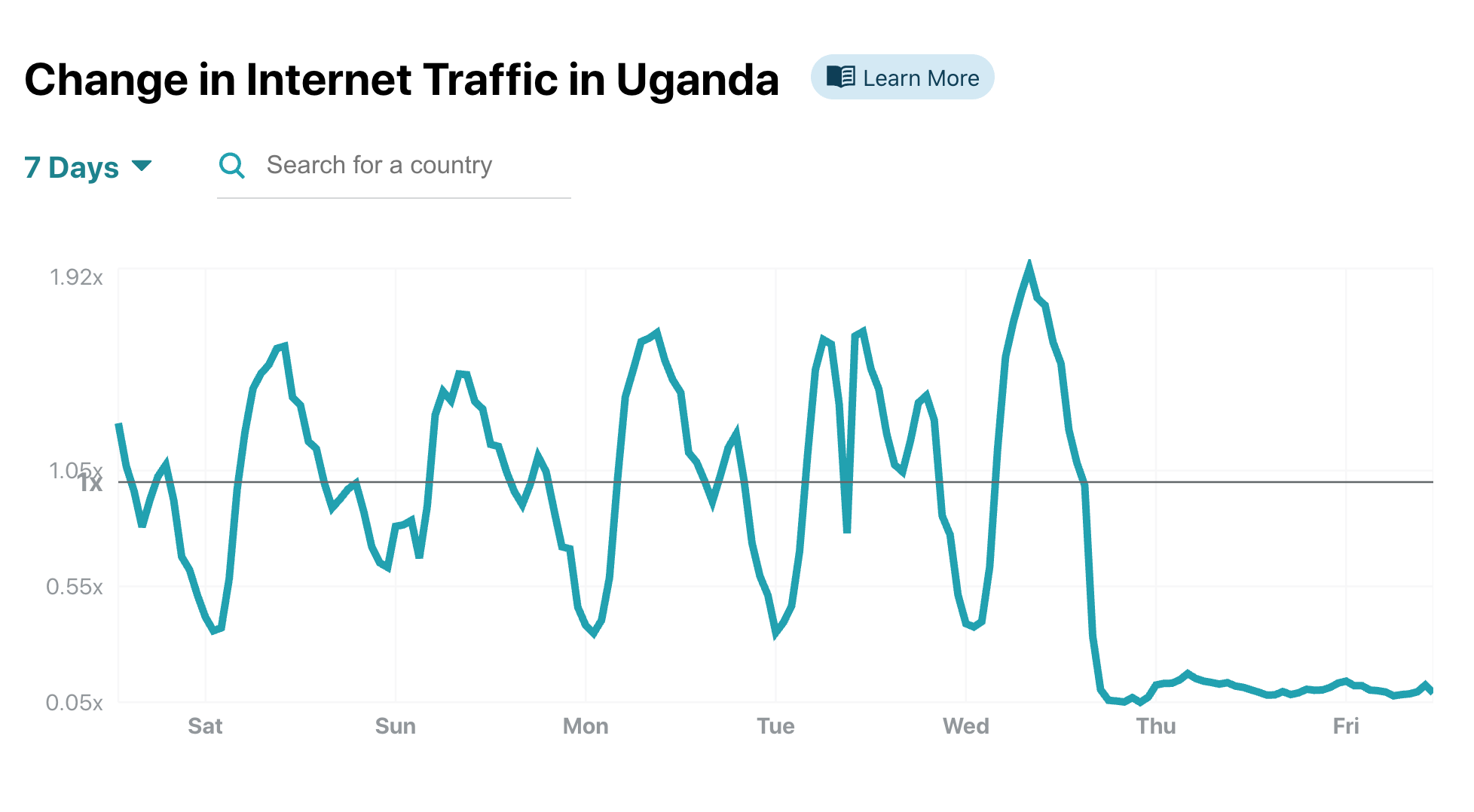
Uganda's unusual traffic patterns quickly popped up in our charts. Our 7-day change in Internet Traffic chart in Uganda shows a clear drop to near zero starting around 1900 local time, when the providers received the letter.
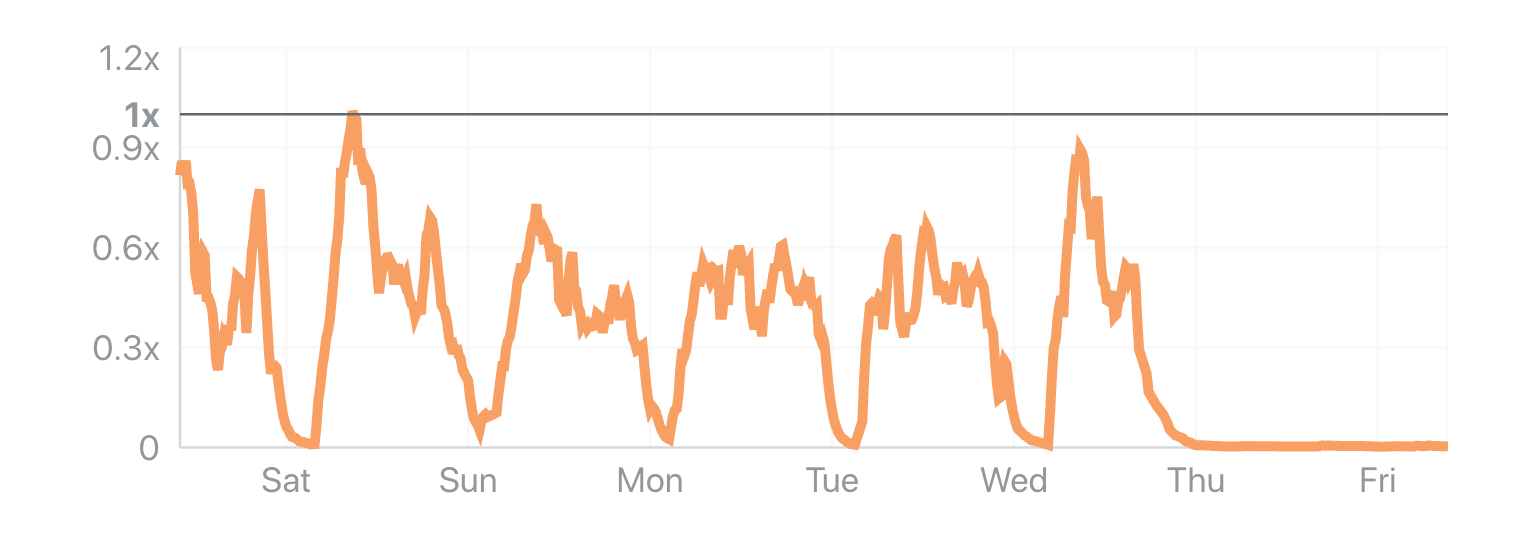
This is also obvious in the Application-level Attacks chart.
The traffic drop was also confirmed by the Uganda Internet eXchange point, a place where many providers exchange their data traffic, on their Continue reading
The Impending AMD Milan Versus Intel Ice Lake Server Showdown
What a strange server CPU world we live in. The dozen or so biggest customers in the world command something on the order of 45 percent of the server CPU shipments, but significantly lower share of the revenue because of the volume discounts they can command, and they not only shape the product rollouts, their opinions can kill off processor SKUs long before we even know about them on announcement day. …
The Impending AMD Milan Versus Intel Ice Lake Server Showdown was written by Timothy Prickett Morgan at The Next Platform.
Technology Short Take 136
Welcome to Technology Short Take #136, the first Short Take of 2021! The content this time around seems to be a bit more security-focused, but I’ve still managed to include a few links in other areas. Here’s hoping you find something useful!
Networking
- Jason Eckert provides an introduction to using WireGuard for VPN connectivity.
- Who else knew that HAProxy could route SSH connections?
- This article by Joshua Fox outlines how and when to use each of the various types of firewalls offered by AWS.
- Rory McCune points out that Kubernetes is a router, and users should not rely on the fact that pods are not accessible from the outside by default as any form of a security barrier.
Servers/Hardware
- Thinking of buying an M1-powered Mac? You may find this list helpful.
Security
- UEFI implants and executable PNGs? The (computing) world is getting to be a scary place, my friends. Compute safely.
- Scott Piper shares some lesser-known techniques for attacking AWS environments.
- The popular open source cryptography library known as Bouncy Castle has uncovered a severe authentication bypass vulnerability. More details are available in this article.
- From early December 2020, there’s also this reminder about the security updates released by Continue reading
Heavy Networking 557: User Experience Is A Full-Stack Responsibility (Sponsored)
Digital Experience Monitoring (DEM) is the topic on today's Heavy Networking. IT folks tend to view user experience from their own particular area of responsibility--networking, security, app development--but the reality is there's a common set of data that IT should consume and understand. Sponsor Catchpoint joins us to discuss its DEM platform and how it measures user experience using metrics that are relevant across the IT stack. Our guest is JP Blaho, Director, Product Marketing at Catchpoint.Heavy Networking 557: User Experience Is A Full-Stack Responsibility (Sponsored)
Digital Experience Monitoring (DEM) is the topic on today's Heavy Networking. IT folks tend to view user experience from their own particular area of responsibility--networking, security, app development--but the reality is there's a common set of data that IT should consume and understand. Sponsor Catchpoint joins us to discuss its DEM platform and how it measures user experience using metrics that are relevant across the IT stack. Our guest is JP Blaho, Director, Product Marketing at Catchpoint.
The post Heavy Networking 557: User Experience Is A Full-Stack Responsibility (Sponsored) appeared first on Packet Pushers.
Managing Leaders, Or Why Pat Gelsinger Is Awesome

In case you missed it, Intel CEO Bob Swan is stepping down from his role effective February 15 and will be replaced by current VMware CEO Pat Gelsinger. Gelsinger was the former CTO at Intel for a number of years before leaving to run EMC and VMware. His return is a bright spot in an otherwise dismal past few months for the chip giant.
Why is Gelsinger’s return such a cause for celebration? The analysts that have been interviewed say that Intel has been in need of a technical leader for a while now. Swan came from the office of the CFO to run Intel on an interim basis after the resignation of Brian Krzanich. The past year has been a rough one for Intel, with delays in their new smaller chip manufacturing process and competition heating up from long-time rival AMD but also from new threats like ARM being potentially sold to NVIDIA. It’s a challenging course for any company captain to sail. However, I think one key thing makes is nigh impossible for Swan.
Management Mentality
Swan is a manager. That’s not meant as a slight inasmuch as an accurate label. Managers are people that have things and Continue reading
KEMTLS: Post-quantum TLS without signatures


The Transport Layer Security protocol (TLS), which secures most Internet connections, has mainly been a protocol consisting of a key exchange authenticated by digital signatures used to encrypt data at transport[1]. Even though it has undergone major changes since 1994, when SSL 1.0 was introduced by Netscape, its main mechanism has remained the same. The key exchange was first based on RSA, and later on traditional Diffie-Hellman (DH) and Elliptic-curve Diffie-Hellman (ECDH). The signatures used for authentication have almost always been RSA-based, though in recent years other kinds of signatures have been adopted, mainly ECDSA and Ed25519. This recent change to elliptic curve cryptography in both at the key exchange and at the signature level has resulted in considerable speed and bandwidth benefits in comparison to traditional Diffie-Hellman and RSA.
TLS is the main protocol that protects the connections we use everyday. It’s everywhere: we use it when we buy products online, when we register for a newsletter — when we access any kind of website, IoT device, API for mobile apps and more, really. But with the imminent threat of the arrival of quantum computers (a threat that seems to be getting closer and closer), we need Continue reading
Video: Multi-Layer Switching and Tunneling
After discussing the technology options one has when trying to get a packet across the network, we dived deep into two interesting topics:
- How do you combine packet forwarding at multiple layers of OSI stack (multi-layer switching)?
- What happens when you do layer-N forwarding over layer-M transport core where N <= M (example: IPv6 packets over IPv4 packets) aka tunneling?
You’ll find more details (including other hybrids like Loose Source Routing) in Multi-Layer Switching and Tunneling video.
Video: Multi-Layer Switching and Tunneling
After discussing the technology options one has when trying to get a packet across the network, we dived deep into two interesting topics:
- How do you combine packet forwarding at multiple layers of OSI stack (multi-layer switching)?
- What happens when you do layer-N forwarding over layer-M transport core where N <= M (example: IPv6 packets over IPv4 packets) aka tunneling?
You’ll find more details (including other hybrids like Loose Source Routing) in Multi-Layer Switching and Tunneling video.
Addressing 2020
Time for another annual roundup from the world of IP addresses. Let’s see what has changed in the past 12 months in addressing the Internet and look at how IP address allocation information can inform us of the changing nature of the network itself.Webinar: How the Internet Really Works Part 1

On the 22nd, I’m giving a three hour course called How the Internet Really Works. I tried making this into a four hour course, but found I still have too much material, so I’ve split the webinar into two parts; the second part will be given in February. This part is about how systems work, who pays for what, and other higher level stuff. The second part will be all about navigating the DFZ. From the Safari Books site:
This training is designed for beginning engineers who do not understand the operation of the Internet, experienced engineers who want to “fill in the gaps,” project managers, coders, and anyone else who interacts with the Internet and wants to better understand the various parts of this complex, global ecosystem.
IPv6 Buzz 067: IPv6 In The Cloud With Ivan PepeInjak
Today's IPv6 Buzz episode examines the state of IPv6 in the public cloud, including capabilities and limitations with current v6 support in AWS and Azure, ongoing customer demand for v4, and more. Our guest is Ivan Pepelnjak.IPv6 Buzz 067: IPv6 In The Cloud With Ivan PepeInjak
Today's IPv6 Buzz episode examines the state of IPv6 in the public cloud, including capabilities and limitations with current v6 support in AWS and Azure, ongoing customer demand for v4, and more. Our guest is Ivan Pepelnjak.
The post IPv6 Buzz 067: IPv6 In The Cloud With Ivan PepeInjak appeared first on Packet Pushers.
Hedge #66: Tyler McDaniel and BGP Peer Locking
Tyler McDaniel joins Eyvonne, Tom, and Russ to discuss a study on BGP peerlocking, which is designed to prevent route leaks in the global Internet. From the study abstract:
Datacenter Infrastructure Is Still Only Partly Cloudy
If you want to understand datacenter infrastructure and how the market for wares is changing, it helps to start with an absolute, top-down, all-encompassing view that brings together all server, storage, and switching revenues into a single bucket, eliminating the overlaps that occur when talking about these three different categories separately. …
Datacenter Infrastructure Is Still Only Partly Cloudy was written by Timothy Prickett Morgan at The Next Platform.
Want to Make the Internet Even Better in 2021? Register for Our Special Edition Community Event

Early last year, as people across the world quarantined to slow the spread of the COVID-19 virus, the Internet became critical to maintaining a semblance of routine and getting the latest lifesaving information. But there was a stark reality. Those without Internet access would have to grapple without this vital resource amidst a global pandemic.
Internet Society volunteers around the world understood the gravity of the situation. They jumped in to enable secure access.
In North America, NYC Mesh, a community network supported by the Internet Society, rushed to connect as many households as they could. While it was still safe to do so, they crossed rooftops to bring connectivity to some of the city’s most underserved.
In Europe, the Internet Society Italy Chapter launched SOSDigitale to mobilize resources and volunteers to respond to urgent technology gaps. The Portugal Chapter followed with their own SOS Digital campaign to donate computers and digital support to at-risk youth.
And in Latin America, residents of El Cuy, in remote Patagonia, Argentina, were able to reduce their potential exposure to COVID-19 via their newly-established community network, accessing medical prescriptions, education, banking, and government resources online.
No one could have predicted the events of 2020. Continue reading
What’s Behind One NVMe Storage Company’s Meteoric Rise
There is plenty of potential to upset traditional storage via leveraging on-board NVMe devices and while the competition is thick and fierce, there are a few companies that are already standing out in 2021. …
What’s Behind One NVMe Storage Company’s Meteoric Rise was written by Nicole Hemsoth at The Next Platform.