Google Cloud Gains U.K. Gov’t Foothold
The cloud giant signed a deal to provide services to different U.K. government agencies at...
Enabling IPv6 in AWS Deployments
IPv6 is old enough to buy its own beer (in US, not just in Europe), but there are still tons of naysayers explaining how hard it is to deploy. That’s probably true if you’re forced to work with decades-old boxes, or if you handcrafted your environment with a gazillion clicks in a fancy GUI, but if you used Terraform to deploy your application in AWS, it’s as hard as adding a few extra lines in your configuration files.
Nadeem Lughmani did a great job documenting the exact changes needed to get IPv6 working in AWS VPC, including adjusting the IPv6 routing tables, and security groups. Enjoy ;)
Rakuten Mobile Taps NEC for Homegrown 5G Core
Rakuten Mobile isn’t going far, less than 10 miles in fact, for the procurement of its 5G core.
Adtran Grows SD-Access Portfolio
The company claims these new appliances will help to support a wider array of operator use cases...
The Hedge Podcast Episode 38: Evan Knox and Personal Marketing
Personal branding and marketing are two key topics that surface from time to time, but very few people talk about how to actually do these things. For this episode of the Hedge, Evan Knox from Caffeine Marketing to talk about the importance of personal marketing and branding, and some tips and tricks network engineers can follow to improve their personal brand.
Stack Overflow Survey Reconfirms Developer Love for Docker
The 2020 Stack Overflow Developer Survey confirms what we already knew: there’s a lot of developer love out there for Docker and it is continuing from last year.
Docker was the #1 most wanted platform and #2 most loved platform, according to the survey results published last week. We also ranked as the #3 most popular platform.
That’s no fluke. The results are based on nearly 65,000 people who code. And it’s the second year running we’ve acquitted ourselves so admirably in the annual survey. As we shared with you here last summer, developers ranked Docker as the #1 most wanted platform, #2 most loved platform and #3 most broadly used platform in the 2019 Stack Overflow Developer Survey. Those responses came from nearly 90,000 developers from around the world.
- This year, in the most wanted platform category, nearly 25 percent of developers expressed interest in developing with Docker, ahead of AWS (20.2 percent), Kubernetes (18.5 percent) and Linux (16.6 percent).
- In the most loved platform category, 73.6 percent of developers expressed interest in continuing to develop with Docker, trailing only first-placed Linux (76.9 percent), and leading Kubernetes (71.1 percent) and AWS (66. Continue reading
Cooling Magma Is A Challenge That Lawrence Livermore Can Take On
With 5.4 petaflops of peak performance crammed into 760 compute nodes, that is a lot of computing capability in a small space generating a considerable amount of heat. …
Cooling Magma Is A Challenge That Lawrence Livermore Can Take On was written by Ken Strandberg at The Next Platform.
MEF Boasts 8 Carrier Ethernet Orchestration Deployments
Early adopting service providers include AT&T, Bestel, Bloomberg, Colt Technology Services,...
Introduction to YAML
Introduction
YAML, previously known as Yet Another Markup Language, but now YAML Ain’t Markup Language, is a human friendly data serialization standard for programming languages.
YAML and JSON, JavaScript Object Notation, are related to each other, where YAML, according to YAML 1.2 specification, is a superset of JSON.
YAML supports using scalars, sequences, and mappings. A scalar is a string, a number, or boolean, a sequence is a list, and a mapping is a key/value pair.
YAML is commonly used by configuration files in open source tools and Ansible, a network automation tool, uses YAML to run its playbooks.
When it comes to YAML syntax, be aware of the following:
- Indentation matters!
- Tabs aren’t allowed
- Normally two spaces used when indenting
- A single YAML file may contain multiple documents
- Every document starts with three dashes
- YAML is case sensitive
Scalars
Scalars are single values. It can be a string, number, or a boolean value. Strings don’t need to be quoted, except for some special cases:
- The string starts with a special character
- !#%@&*`?|>{[ or –
- The string starts or ends with whitespace characters
- The string contains : or # character sequences
- The string ends with a Continue reading
GNMI. Part 4. Configuring Arista EOS and Nokia SR OS with gRPC/gNMI and OpenConfig/YANG.
Hello my friend,
We have received a lot of positive feedbacks in the social media regarding our previous post about collecting info from Nokia SR OS and Arista EOS using gRPC/gNMI. Thank you! Today we will cover the configuration part; hence, you will learn how to configure Arista EOS and Nokia SR OS using the gRPC transport with gNMI specification and OpenConfig YANG modules.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Start your network automation journey
Just in two weeks we start the new network automation training! This time we have ever biggest agenda with all the cutting edge technologies (NETCONF, REST API, gNMI), data models (YANG, Protobuf, JSON, XML, YAML), vendors (Cisco, Nokia, Arista, Cumulus) and a lot of programming (Ansible, Python, Bash) salted with Linux administration, virtualisation, containerisation and many more
In one place you will learn all the technologies and tolls you need to start or improve your career in the world of the Continue reading
Noction Flow Analyzer v 20.05.0
Today we are excited to announce the release of Noction Flow Analyzer v 20.05.0 The new version is now even more powerful,
The post Noction Flow Analyzer v 20.05.0 appeared first on Noction.
Open networking post Nvidia-Mellanox-Cumulus acquisition
Subscribe to Kernel of Truth on iTunes, Google Play, Spotify, Cast Box and Sticher!
Click here for our previous episode.
With the recent acquisition of Cumulus Networks by Nvidia, what does that mean for open networking? Kernel of Truth host Roopa Prabhu is joined by Partho Mishra and Amit Katz to discuss what does the acquisition mean for the future of accelerated data center and for open networking in the data center. This is a must listen episode!
Guest Bios
Roopa Prabhu: Roopa Prabhu is Chief Linux Architect at Cumulus Networks. At Cumulus she and her team work on all things kernel networking and Linux system infrastructure areas. Her primary focus areas in the Linux kernel are Linux bridge, Netlink, VxLAN, Lightweight tunnels. She is currently focused on building Linux kernel dataplane for E-VPN. She loves working at Cumulus and with the Linux kernel networking and debian communities. Her past experience includes Linux clusters, ethernet drivers and Linux KVM virtualization platforms. She has a BS and MS in Computer Science. You can find her on Twitter at @__roopa.
Amit Katz: Amit is Vice President Ethernet Switch at Mellanox, Nvidia Business Unit. Amit served as Senior Director of Continue reading
Gaining Intuition with Network Designs
I care a lot about network design. I think it’s too hard to design networks well and I think that all the tools necessary to do it well don’t exist. At least I haven’t seen them. The lack of tools affects the biggest networks, but it affects all networks. I...SDxCentral Condemns the Murder of George Floyd
SDxCentral also condemns police brutality and the rash of racially motivated murders of the black,...
Mitsubishi Corporation and NTT complete investment in HERE Technologies
Mitsubishi Corporation (“MC”) and Nippon Telegraph and Telephone Corporation...
Maxie McCoy: Work Will Never Be the Same
Workplace expert Maxie McCoy says the COVID-19 era has changed almost everything about the office,...
Daily Roundup: Plug Pulled on Cisco Live
Cisco Live postposed in light of recent events; Dell, VMware supercharged AI; and Chipmakers...
Cyberattacks since the murder of George Floyd
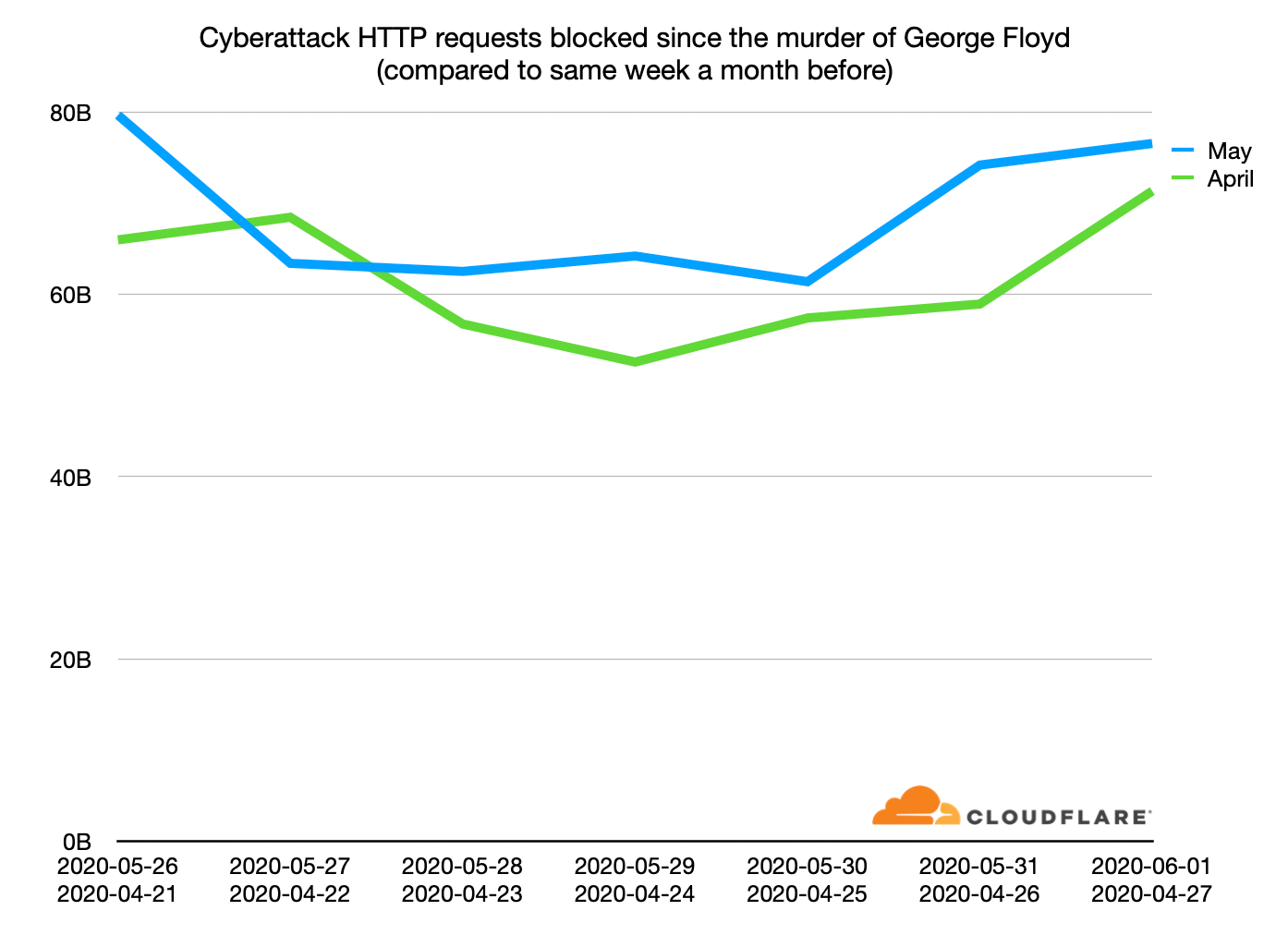
As we’ve often seen in the past, real world protest and violence is usually accompanied by attacks on the Internet. This past week has been no exception. The shocking murder of George Floyd on May 25 was followed, over the weekend of May 30/31, by widespread protests and violence in the US. At the same time, Cloudflare saw a large uptick in cyberattacks, particularly cyberattacks on advocacy organizations fighting racism.
This chart shows the number of cyberattack HTTP requests blocked by Cloudflare over the last week (blue line) compared to the corresponding week in April a month before (green line). Cloudflare’s scale means that we are blocking attacks in the many 10s of billions per day, but even with that scale it’s clear that during the last week there have been even more attacks than before. And those attacks grew over the weekend.
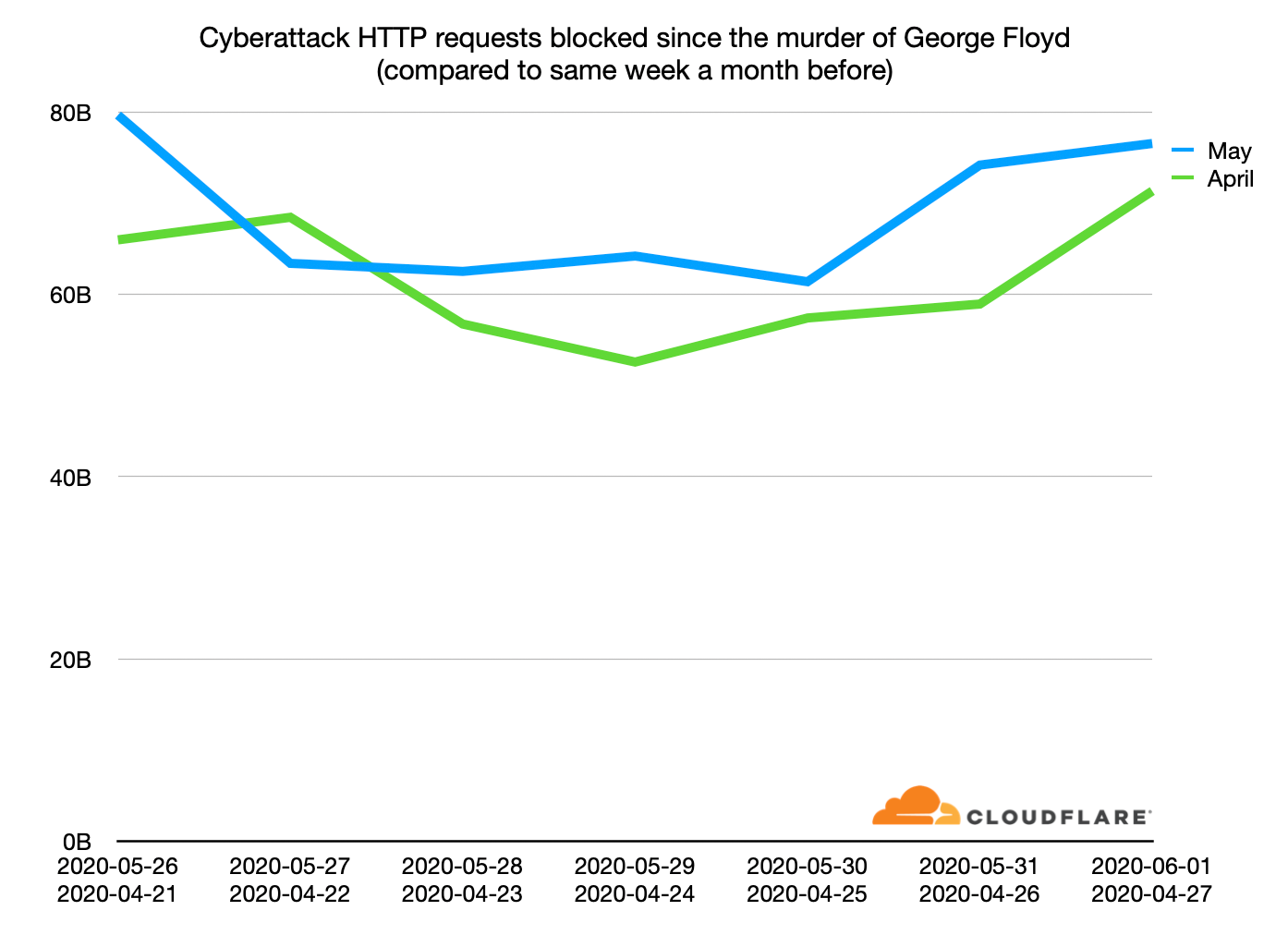
Digging in a little deeper we can compare the attacks over this past weekend with a corresponding weekend a month before. Over the weekend of April 25/26, Cloudflare blocked a total of 116,317,347,341 (a little over 116 billion cyberattack HTTP requests performing DDoS or trying to break into websites, apps or APIs were blocked).
Since 116,317,347,341 can Continue reading
Veeam Data Report: Legacy Is Out, Cloud Services Are In
Fear not slow migrators, legacy technologies are not obsolete – yet.