Daily Roundup: VMware Patches Critical Bug
VMware patched a critical bug; Ericsson scored a 5G win with Nex-Tech Wireless deal; and...
VMware patched a critical bug; Ericsson scored a 5G win with Nex-Tech Wireless deal; and...
Our sponsor today is Silver Peak, and we’re talking about how to improve QoE using SD-WAN with their customer C&S Wholesale Grocers, the largest wholesale grocer in the United States. Our guest is Leonard Bernstein, Senior Director of Infrastructure and Service Delivery.
The post Tech Bytes: Improving QoE With Silver Peak SD-WAN (Sponsored) appeared first on Packet Pushers.


Almost exactly two years ago, we launched Cloudflare Spectrum for our Enterprise customers. Today, we’re thrilled to extend DDoS protection and traffic acceleration with Spectrum for SSH, RDP, and Minecraft to our Pro and Business plan customers.
When we think of Cloudflare, a lot of the time we think about protecting and improving the performance of websites. But the Internet is so much more, ranging from gaming, to managing servers, to cryptocurrencies. How do we make sure these applications are secure and performant?
With Spectrum, you can put Cloudflare in front of your SSH, RDP and Minecraft services, protecting them from DDoS attacks and improving network performance. This allows you to protect the management of your servers, not just your website. Better yet, by leveraging the Cloudflare network you also get increased reliability and increased performance: lower latency!
While access to websites from home is incredibly important, being able to remotely manage your servers can be equally critical. Losing access to your infrastructure can be disastrous: people need to know their infrastructure is safe and connectivity is good and performant. Usually, server management is done through SSH (Linux or Unix based servers) and RDP (Windows based Continue reading
Take a Network Break! Grab a virtual donut, sit back and relax, and take a journey with us through Elysian fields of tech news analysis. We’ve got stories today on Cisco, VMware, a new PCAP appliance, a Tech Byte from sponsor Silver Peak with their SD-WAN customer C&S Wholesalers, and more.
The post Network Break 279: Cisco Acquires Fluidmesh; VMware NSX 3.0; MS Events Virtual Until July 2021 appeared first on Packet Pushers.
Many networking solutions purport great Opex savings through automation, simulation and continuous integration. Similarly, there is a school of thought where network designs will have a single point in a network perform multiple roles. This will short change an initial Capex cost of purchasing additional switches with the intention of overlapping features on that single device.
Let’s take the simplest example. We have a 3 rack environment with dual-leaf per rack and 2 spines for inter-rack connectivity. In this design, we are leveraging VXLAN as the data plane overlay with BGP/EVPN as the control plane. Additionally, all 3 racks are compute, leaving no additional leafs to act as the service/border/exit leafs.

A network designer will look at the infrastructure and try to overlap features by repurposing the spines as exit leafs. Why will they think this way, you ask? Well, this is only an 8 switch design. Spending money on an additional 2 switches to act as dedicated border leafs uplifts my capex cost by 25 percent! I would then be required to buy 10 total switches instead of 8.

So instead, we end up overlaying the VXLAN onto the spines. So now the spines act as both interconnections between Continue reading
The Kansas-based operator plans to launch its 5G service before July.
The vulnerability could allow a hacker to “extract highly sensitive information which could be...

Last week, the U.S. Congress passed the third stimulus bill in response to the COVID-19 pandemic. This bill primarily focused on economic relief for companies, individuals, cities, states, and tribal communities. It allocates over $2 trillion in funds for a variety of measures intended to ease the burden of COVID-19.
Some of the included measures have been in the news for weeks, including those related to individual checks for those financially impacted by the virus. But there is an element to this bill that is equally important, not only for our ability to cope with the virus now but also to permanently change our country for the better.
These emergency funds allocate $150 billion to states and territories, including $8 billion specifically for Tribal governments, for “coronavirus relief.” What that relief looks like, however, is relatively vague. If a community was financially impacted by the pandemic between March and December of this year, in a way that they did not originally anticipate in their budgets, this fund covers most of those expenses.
And what is one of the biggest impacts we’ve seen? Millions of people have been forced to isolate themselves at home and carry out their daily Continue reading
Recently we have released a new Edge version 2.2.3.0 of Docker Desktop for Windows. This can be considered as a release candidate for the next Stable version that will officially support WSL 2. With Windows 10 version 2004 in sight we are giving the next version of Docker Desktop the final touches to give you the best experience running Linux containers on Windows 10.
One of the great benefits is that with the next update of Windows 10 we will also support running Docker Desktop on Windows 10 Home. We worked closely with Microsoft during the last few months to make Docker Desktop and WSL 2 fit together.
In this blog post we look behind the scenes at how we set up new WSL 2 capable test machines to run automated tests in our CI pipeline.
Let’s keep in mind that all automation somehow starts with manual steps and you evolve from there to get better and more automated. At the beginning of this project we were given a laptop back at KubeCon 2019 with an early version of WSL 2.
With that single laptop our development team could start getting their Continue reading
Several years ago, the HPC systems designed for wide-ranging scientific computing were quite a bit different than those built for intense scalability and maximum peak performance. …
Building Innovative HPC for Massively Mixed Workloads was written by Nicole Hemsoth at The Next Platform.

No working from home: Working from home during the COVID-19 pandemic is tougher in some places than in others. Business Insider finds 17 U.S. cities where Internet access is lower than in much of the rest of the country. Many of the cities listed are across the South and in New Mexico.
Students need access: Alabama’s state schools superintendent is worried about a lack of access for some students while schools are shut down during the pandemic, AL.com reports. There are several “gaps” in access for students, but some school districts are using buses to deliver WiFi.
100,000 laptops: Meanwhile, in Arizona, more than 100,000 students need laptops in order to do school work from home, AZcentral.com reports. The Greater Phoenix Chamber Foundation has been running a laptop drive to reduce that number. Access is also a problem in some rural areas, with some areas having only 25 percent of households with Internet access.
Fundraising for access: In Maine, the Bangor School Department has turned to fundraising to provide 350 families with Internet access so students can participate in distance learning, the Bangor Daily News reports. The school department raised about $28,000 in a week on the Continue reading

The scale and complexity of modern infrastructures require not only that you be able to define a security policy for your systems, but also be able to apply that security policy programmatically or make changes as a response to external events. As such, the proper automation tooling is a necessary building block to allow you to apply the appropriate actions in a fast, simple and consistent manner.
Check Point has a certified Ansible Content Collection of modules to help enable organizations to automate their response and remediation practices, and to embrace the DevOps model to accelerate application deployment with operational efficiency. The modules, based on Check Point security management APIs* are also available on Ansible Galaxy, in the upstream version of Check Point Collection for the Management Server.
The operational flow is exactly the same for the API as it is for the Check Point security management GUI SmartConsole, i.e. Login > Get Session > Do changes > Publish > Logout.
Security professionals can leverage these modules to automate various tasks for the identification, search, and response to security events. Additionally, in combination with other modules that are part of Ansible security automation, existing Continue reading


The most impactful internship experiences involve building something meaningful from scratch and learning along the way. Those can be tough goals to accomplish during a short summer internship, but our experience with Cloudflare’s 2019 intern program met both of them and more! Over the course of ten weeks, our team of three interns (two engineering, one product management) went from a problem statement to a new feature, which is still working in production for all Cloudflare customers.
Cloudflare sits between customers’ origin servers and end users. This means that all traffic to the origin server runs through Cloudflare, so we know when something goes wrong with a server and sometimes reflect that status back to users. For example, if an origin is refusing connections and there’s no cached version of the site available, Cloudflare will display a 521 error. If customers don’t have monitoring systems configured to detect and notify them when failures like this occur, their websites may go down silently, and they may hear about the issue for the first time from angry users.
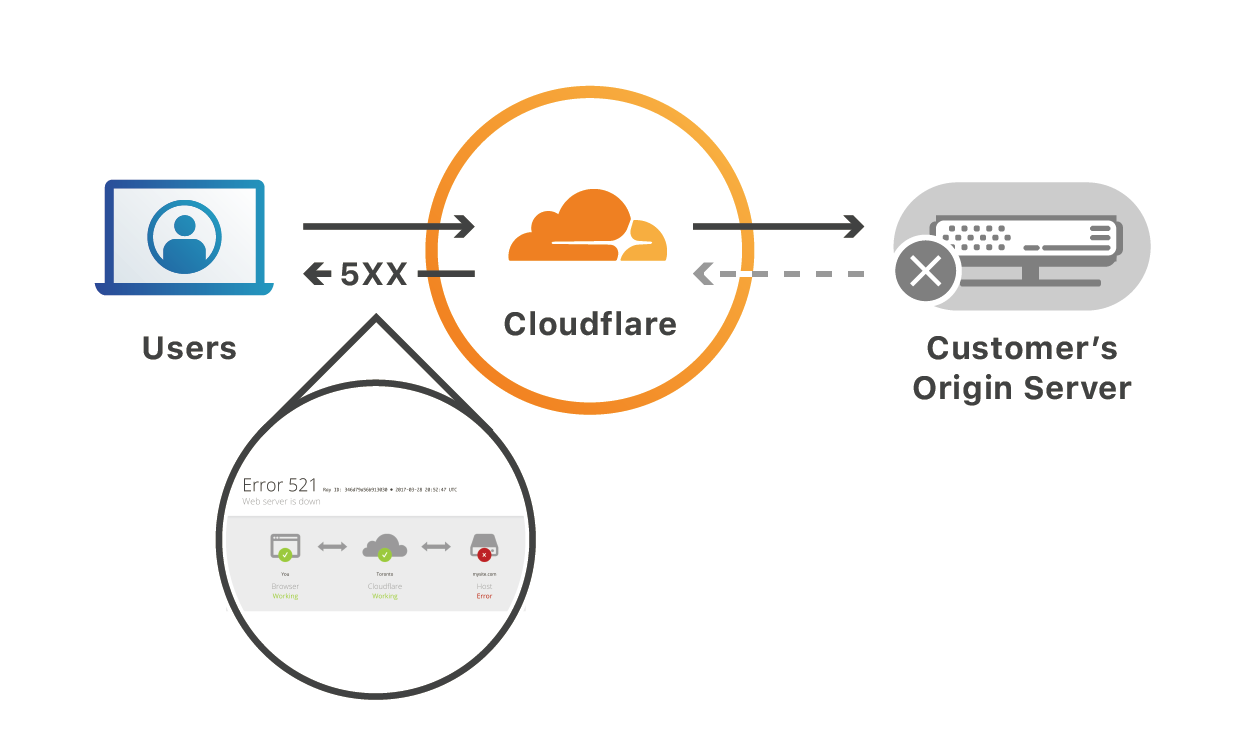

This problem became the starting Continue reading
Hello my friend,
Surprisingly for myself in the previous post about networking I’ve started completely new topic. It was about the Microsoft Azure SONIC running inside the Docker container and network between those containers. Why is that new? Why does it matter? What is in it for you?
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
To be able to understand and, more important, to create such a solutions, you need to have a holistic knowledge about the network automation. Come to our network automation training to get this knowledge and skills.

At this training we teach you all the necessary concepts such as YANG data modelling, working with JSON/YAML/XML data formats, Linux administration basics, programming in Bash/Ansible/Python for multiple network operation systems including Cisco IOS XR, Nokia SR OS, Arista EOS and Cumulus Linux. All the most useful things such as NETCONF, REST API, OpenConfig and many others are there. Don’t miss the opportunity to improve Continue reading
Numerous online companies are using the COVID-19 crisis to make their products better known (PacketPushers collected some of them). Nothing wrong with that - they’re investing into providing free- or at-cost resources, and hope to get increased traction in the market. Pretty fair and useful.
Then there are others… Here’s a recent email I got:
Last week I wrote a post on using Postman to launch an EC2 instance via API calls. Postman is a cross-platform application, so while my post was centered around Postman on Linux (Ubuntu, specifically) the steps should be very similar—if not exactly the same—when using Postman on other platforms. Users of macOS, however, have another option: a macOS-specific peer to Postman named Paw. In this post, I’ll walk through using Paw to issue API requests to AWS to launch an EC2 instance.
I’ll structure this post as a “diff,” if you will, that outlines the differences of using Paw to launch an EC2 instance via API calls versus using Postman to do the same thing. Therefore, if you haven’t already read the Postman post from last week, I strongly recommend reviewing it before proceeding.
This post assumes you’ve already installed Paw on your macOS system. It also assumes you are somewhat familiar with Paw; refer to the Paw documentation if not. Also, to support AWS authentication, please be sure to install the “AWS Signature 4 Auth Dynamic value” extension (see here or here). This extension is necessary in order to have the API requests sent Continue reading