10 Networking Startups To Watch In 2017
Check out these new vendors that aim to make a mark in networking.
Check out these new vendors that aim to make a mark in networking.
Our organization, like most large public bodies, is locked into formal bureaucratic procedures and, by general standards, is highly risk-averse. In addition, like other organizations of the United Nations System, it has a unique attribute which makes moving to the cloud a much greater leap than for most other organizations: UN System organizations enjoy a special status.
In the aftermath of World War II, countries negotiating the Charter for the future United Nations agreed the organization should be in a position to function without interference from any single Member State. For this reason, a regime of privileges and immunities was developed. It is this special legal regime that ensures UN organizations are immune from the jurisdiction of national courts, that their premises cannot be entered by national enforcement agencies without their consent, and that their archives – including their data – cannot be accessed without their agreement.
To read this article in full or to leave a comment, please click here
With January 6th the Christmas/New Year holidays are over even for most European countries, so it’s time to restart my blog and set some goals for 2017.
2015 was year of SDN, 2016 was year of network automation, and 2017 is shaping up to be the year of the cloud.
Read more ...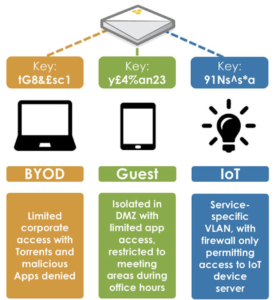 A fairly common question I get asked when talking to people about Aerohive Networks is “what makes us different?” In other words, why should they choose Aerohive to replace their existing wireless vendor? It is a fair question. After all, plenty of vendors sell APs that can serve the most basic wireless needs. All of the vendors I compete with do a lot of the same things when it comes to general wireless.
A fairly common question I get asked when talking to people about Aerohive Networks is “what makes us different?” In other words, why should they choose Aerohive to replace their existing wireless vendor? It is a fair question. After all, plenty of vendors sell APs that can serve the most basic wireless needs. All of the vendors I compete with do a lot of the same things when it comes to general wireless.
One of the things I like to talk to potential customers about is Aerohive’s Private Pre-Shared Key(PPSK) technology. For some organizations, PPSK is not something they are interested in. Maybe they already have a pretty solid 802.1X implementation and don’t have a need for WPA2 Personal(pre-shared key) security on their wireless network. That’s perfectly fine in my book. I have other things I can always talk about with regard to an Aerohive solution. For quite a few organizations though, they see the advantage of PPSK over standard pre-shared key implementations and jump right in to using it. I wanted to briefly discuss what PPSK is and how it can be utilized with an Aerohive solution. No configuration screenshots or long demonstration videos. Just a basic Continue reading
Happy new year to all the readers of the blog!
I’ve been lacking the time to update the blog lately which I’m sorry for. Work is keeping me busy with some interesting projects. I hope to get a bit more frequent with the updates and maybe do smaller posts than my traditional larger ones.
For 2017 I’m going to focus on a few different areas to stay sharp and broaden my skillset a bit.
Wireless – I haven’t worked much with wireless and I’m going to upskill in this area to be able to understand the wireless requirements better when designing enterprise networks.
Datacenter – There are a lot of DC projects right now. Many companies are at the end of their Catalyst 6500 lifecycle and are looking for new solutions in the datacenter. Cisco’s Application Centric Infrastructure (ACI) is a hot topic right now. I’ll probably be working more on DC projects and ACI in 2017.
Python – In my role as a network architect I don’t really have the need to do a lot of programming but I want to keep the brain sharp and know the basics of Python. I can use it to automate boring things Continue reading
2017 CCDE Exam dates has been announced.There are four CCDE exam every year. More precisely there are four CCDE Practical/Lab exam every year. There is no limitation for the CCDE Written exam. You can join CCDE Written exam anytime in any Pearson Vue Center. It is not only 4 times in a year. CCDE Practical […]
The post 2017 CCDE Exam Dates appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Is Cisco CCDE exam harder than CCIE exam ? This is one of the most commonly asked questions by the CCDE candidates. Short answer is no. But, you should know the differences between the CCIE vs. CCDE as well. CCDE exam is scenario based. You have four scenarios which is called as Lab or practical […]
The post Is Cisco CCDE exam harder than CCIE ? appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
We set out to change WiFi forever. Our uncompromising vision: a wireless router that secures your digital life, while delivering the highest level of performance. The result is Norton Core. Core uses advanced machine learning and Symantec’s global intelligence network to defend your home WiFi—and every device connected to it—against malware, viruses, hackers and much more.
Powerful, secure WiFi is now a thing.
Citrix and NSX integration to build departmental isolation between VDI desktops.
In this blog, I am going to focus on XenDesktop, NetScaler and NSX interoperability. I will discuss a field use case, see how to implement that in VMware NSX for XenDesktop and then look at a few micro-segmentation deployment scenarios, to showcase how XenDesktop and NetScaler in conjunction with NSX provides a compelling deployment model.
The ability to isolate and control desktops represents a major security and integrity enhancement. Using a Netscaler provides a single point of access into the data centre and can be integrated into the NSX overlay.
Adding NetScaler in this deployment would simplify the set up and allow the users of all the airlines (or tenants) access the same landing URL and still have complete isolation from each other’s data and resources.
Observation: NSX is an automation tool for connectivity between end points and offers isolation/segmentation as service. Added to Netscaler, we get orchestration to produce greater business benefits because the XenDesktop & NSX becomes a unified service.
No specific provisioning to make this happen. Thats an SDN outcome.
XenDesktop and XenApp Interoperability with VMware NSX | Citrix Blogs