Segment-routing + Opendaylight SDN + Pathman-SR + PCEP


This is a second technical post related to segment-routing, I did a basic introduction to this technology on Juniper MX here;
Segment Routing on JUNOS – The basics
For this post I’m looking at something a bit more advanced and fun – performing Segment-routing traffic-engineering using an SDN controller, in this case OpenDaylight Beryllium – an open source SDN controller with some very powerful functionality.
This post will use Cisco ASR9kV virtual routers running on a Cisco UCS chassis, mostly because Cisco currently have the leading-edge support for Segment-routing at this time, Juniper seem to be lagging behind a bit on that front!
Lets check out the topology;
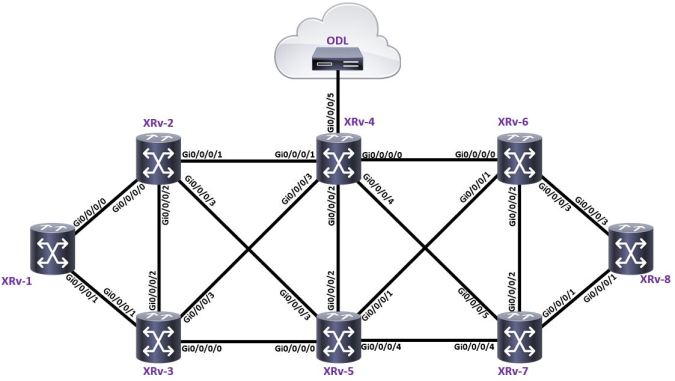
It’s a pretty simple scenario – all of the routers in the topology are configured in the following way;
- XRV-1 to XRV-8; PE routers (BGP IPv4)
- XRV 2 to XRV7; P routers (ISIS-Segment-routing)
- XRV4 is an in-path RR connecting to the ODL controller

The first thing to look at here is BGP-LS “BGP Link-state” which is an extension of BGP that allows IGP information (OSPF/ISIS) to be injected into BGP, this falls conveniently into the world of centralised path computation – where we can use a controller of some sort to look at Continue reading
Worth Reading: 4G and 5G Mobile Backhaul
The post Worth Reading: 4G and 5G Mobile Backhaul appeared first on 'net work.
Best practices for lowering cyber insurance costs and cyber risk
Although vendor-written, this contributed piece does not advocate a position that is particular to the author’s employer and has been edited and approved by Network World editors.
With cybersecurity threats on the rise, companies are increasingly taking advantage of cybersecurity insurance. And while cyber insurance can be worth it, it’ll cost you. Last year, U.S. insurers earned $1B in cyber premiums. You can minimize your premiums by showing your insurance company you’re actively mitigating cyber risks, which is a win-win: lower your risk and secure a more cost-effective insurance plan.
To read this article in full or to leave a comment, please click here
Electoral college should ignore Lessig
Reading this exchange between law profs disappoints me. [1] [2] [3] [4] [5]The decision Bush v Gore cites the same principle as Lessig, that our system is based on "one person one vote". But it uses that argument to explain why votes should not be changed once they are cast:
Having once granted the right to vote on equal terms, the State may not, by later arbitrary and disparate treatment, value one person's vote over that of another.Lessig cites the principle of "one person one vote", but in a new and novel way. He applies in an arbitrary way that devalues some of the votes that have already been cast. Specifically, he claims that votes cast for state electors should now be re-valued as direct votes for a candidate.
The United States isn't a union of people. It's a union of states. It says so right in the name. Compromises between the power of the states and power of the people have been with us for forever. That's why states get two Senators regardless of size, but Representatives to the House are assigned proportional to population. The Presidential Continue reading
AWS Activates a DDoS Shield & Gives Users X-Ray Vision
 The biggest security concern of the moment gets some AWS attention.
The biggest security concern of the moment gets some AWS attention.
On the ‘Net: Engineer Versus Complexity
The post On the ‘Net: Engineer Versus Complexity appeared first on 'net work.