Summer 2024 weather report: Cloudflare with a chance of Intern-ets

During the summer of 2024, Cloudflare welcomed approximately 60 Intern-ets from all around the globe on a mission to #HelpBuildABetterInternet. Over the course of their internships, our wonderful interns tackled real-world challenges from different teams all over the company and contributed to cutting-edge projects. As returning interns, we – Shaheen, Aaron, and Jada – would like to show off the great work our cohort has done and experiences we’ve had throughout our time here.

Putting the SHIP in internSHIP
Cloudflare interns take pride in driving high-impact initiatives, playing a vital role in advancing Cloudflare's mission. With our diverse roles and projects this summer, we'd love to highlight some of the exciting work we've been involved in:
Rahul, a Software Engineer intern, built a system to autograde intern application assignments for future students looking to join Cloudflare. It was built entirely on the Cloudflare Developer Platform, using Cloudflare Access, Browser Rendering, D1, Durable Objects, R2, and Workers!
Jessica, a Software Engineer intern, created a new threads api for the Workers AI team that automatically recalls past messages when running inference, helping developers to Continue reading
Why Are OSPF Type 5 LSAs Flooded?
I recently saw a great question on Reddit, on why Type-5 (AS-external) LSAs are flooded, in comparison to Type-3 (Summary) that are regenerated at the ABR. To investigate this, we’ll use the following simple topology where R2 and R3 are ABRs:

OSPF Behavior Type-3 LSAs
Let’s see how OSPF handles Summary LSAs. Let’s first look at Area 1, where R4 is advertising 169.254.0.0/24 into it. This can be seen in the LSDB of R2:
R2#show ip ospf data router 203.0.113.4
OSPF Router with ID (203.0.113.2) (Process ID 1)
Router Link States (Area 1)
LS age: 74
Options: (No TOS-capability, DC)
LS Type: Router Links
Link State ID: 203.0.113.4
Advertising Router: 203.0.113.4
LS Seq Number: 80000009
Checksum: 0x1DF0
Length: 84
Number of Links: 5
Link connected to: a Stub Network
(Link ID) Network/subnet number: 169.254.0.0
(Link Data) Network Mask: 255.255.255.0
Number of MTID metrics: 0
TOS 0 Metrics: 1
Link connected to: another Router (point-to-point)
(Link ID) Neighboring Router ID: 203.0.113.3
(Link Data) Router Interface address: 192.0.2.14
Number of MTID metrics: 0
TOS 0 Continue reading
BGP Session and Address Family Parameters
As I was doing the final integration tests for netlab release 1.9.0, I stumbled upon a fascinating BGP configuration quirk: where do you configure the allowas-in parameter and why?
A Bit of Theory
BGP runs over TCP, and all parameters related to the TCP session are configured for a BGP neighbor (IPv4 or IPv6 address). That includes the source interface, local AS number (it’s advertised in the per-session OPEN message that negotiates the address families), MD5 password (it uses MD5 checksum of TCP packets), GTSM (it uses the IP TTL field), or EBGP multihop (it increases the IP TTL field).
How to Create VyOS Firewall Rules?

Hi all, welcome back to another blog post on VyOS. In the previous post, we covered how to install VyOS and set up the initial configurations. In this blog post, we'll cover how to configure firewall rules in VyOS. To demonstrate, we'll create a hypothetical office setup with a VyOS router/firewall. The router will have two interfaces - one facing the Users and another facing the Internet. Our goal is to allow the Users subnet to access the Internet for ICMP, DNS, and general web traffic.
Diagram
Our example is based on the following diagram. I don't have a public IP address on my lab but just play along and pretend that 10.10.0.7 is a public IP 😊 (This IP is behind my ISP's router)
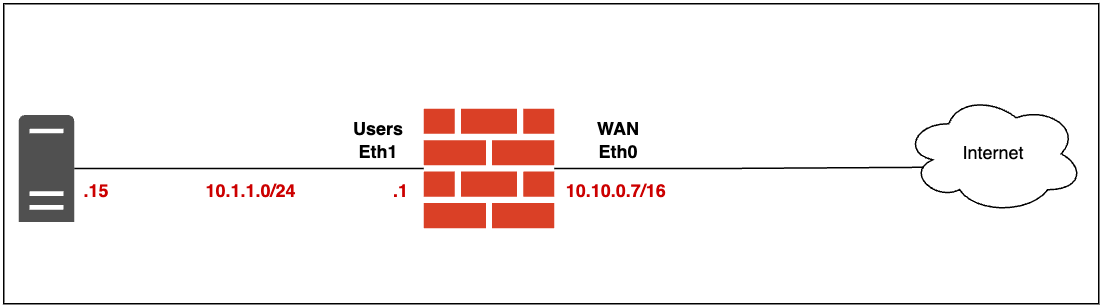
As you can see in the diagram, the VyOS router has two interfaces. The interface connected to the Users subnet (Eth1) has an IP address of 10.1.1.1/24. There's also a test machine in this subnet with the IP address 10.1.1.15. Our goal is to ensure that this test machine can successfully ping an Internet IP address and browse the general Internet.
VyOS Firewall Basics
Palo Alto Firewall For Absolute Beginners

Hi all, if you are here, I assume you're looking to learn about Palo Alto Firewalls, and you've come to the right place. In this blog post, we will cover the very basics of Palo Alto firewalls and how to get started.
Prerequisites
This blog post assumes you have a basic understanding of networking concepts such as routing, Layer 3 interfaces, traffic flow, subnets, and the necessity of a firewall. If you’ve previously used firewalls from different vendors, that’s even better, and you should find it easier to understand the concepts. When I first started with Palo Alto firewalls, I was already working as a network engineer and had experience with Cisco ASA firewalls. However, it still took some time for me to fully understand the nuances. Therefore, my focus here is to explain the nuances of Palo Alto firewalls using simple examples.
What We Will Cover?
In this post, we’ll touch on several key topics related to Palo Alto firewalls, providing an overview without diving too deep into any single area. I’ve written numerous posts on Palo Alto firewalls, and I will include links to those for more in-depth exploration. Here’s what we’ll cover.
- Firewall Basics and Why We Continue reading
Inter-Domain Traffic-Engineering Based MPLS-LSPs
Recently I was exploring solution to have inter-domain traffic-engineerig based MPLS LSPs and came up with following writeup (after going through relevant rfc and vendor Implementation document (my favourite Junos). Please glance through it on my github home page. thanks
https://github.com/kashif-nawaz/Inter-Domain-Traffic-Engineering-and-MPLS-LSPs

HN745: Using Abstractions in Automation
Today’s episode of Heavy Networking comes to you from AutoCon1 in Amsterdam, recorded live on premises. In today’s network automation discussion, we cover abstraction layers with guest Jaakko Rautanen. Practically speaking, what are abstractions, and how do they help make your network automation project successful? We’ll also discuss some of our guest’s automation projects, how... Read more »A wild week in phishing, and what it means for you
Being a bad guy on the Internet is a really good business. In more than 90% of cybersecurity incidents, phishing is the root cause of the attack, and during this third week of August phishing attacks were reported against the U.S. elections, in the geopolitical conflict between the U.S., Israel, and Iran, and to cause $60M in corporate losses.
You might think that after 30 years of email being the top vector for attack and risk we are helpless to do anything about it, but that would be giving too much credit to bad actors, and a misunderstanding of how defenders focused on detections can take control and win.
Phishing isn’t about email exclusively, or any specific protocol for that matter. Simply put, it is an attempt to get a person, like you or me, to take an action that unwittingly leads to damages. These attacks work because they appear to be authentic, visually or organizationally, such as pretending to be the CEO or CFO of your company, and when you break it down they are three main attack vectors that Cloudflare has seen most impactful from the bad emails we protect our customers Continue reading
A wild week in phishing, and what it means for you
This post is also available in 한국어, 日本語, 简体中文, 繁體中文, Français, Deutsch and Español.

Being a bad guy on the Internet is a really good business. In more than 90% of cybersecurity incidents, phishing is the root cause of the attack, and during this third week of August phishing attacks were reported against the U.S. elections, in the geopolitical conflict between the U.S., Israel, and Iran, and to cause $60M in corporate losses.
You might think that after 30 years of email being the top vector for attack and risk we are helpless to do anything about it, but that would be giving too much credit to bad actors, and a misunderstanding of how defenders focused on detections can take control and win.
Phishing isn’t about email exclusively, or any specific protocol for that matter. Simply put, it is an attempt to get a person, like you or me, to take an action that unwittingly leads to damages. These attacks work because they appear to be authentic, visually or organizationally, such as pretending to be the CEO or CFO of your company, and when you break it down they are three Continue reading
Introducing high-definition portrait video support for Cloudflare Stream
Cloudflare Stream is an end-to-end solution for video encoding, storage, delivery, and playback. Our focus has always been on simplifying all aspects of video for developers. This goal continues to motivate us as we introduce first-class portrait (vertical) video support today. Newly uploaded or ingested portrait videos will now automatically be processed in full HD quality.
Why portrait video
In the past few years, the popularity of portrait video has exploded, motivated by short-form video content applications such as TikTok or YouTube Shorts. However, Cloudflare customers have been confused as to why their portrait videos appear to be lower quality when viewed on portrait-first devices such as smartphones. This is because our video encoding pipeline previously did not support high-quality portrait videos, leading them to be grainy and lower quality. This pain point has now been addressed with the introduction of high-definition portrait video.
The current stream pipeline
When you upload a video to Stream, it is first encoded into several different “renditions” (sizes or resolutions) before delivery. This is done in order to enable playback in a wide variety of network conditions, as well as to standardize the way a video is experienced. By using these adaptive Continue reading
Simplify cloud routing and object storage configurations with Cloud Connector
As part of Cloudflare's mission to help build a better Internet, we’re continuously integrating with other networks and service providers, ensuring ease of use for anyone, anywhere, anytime.
Today, we’re excited to announce Cloud Connector – a brand-new way to put Cloudflare in front of popular public cloud services, protecting your assets, accelerating applications, and routing your traffic between multiple cloud providers seamlessly.
Cloud Connector is a natural extension of Cloudflare's Connectivity Cloud, which aims to simplify and secure the complex web of connections across today’s enterprises. Imagine Origin Rules, but managed by Cloudflare, available for all plans, created with just a few clicks, and working out of the box without the need for additional rules. It allows you to route traffic to different public clouds without complicated workarounds. This means you can now direct specific requests to AWS S3, Google Cloud Storage, Azure Blob Storage, or our own R2, even if these services are not set as the DNS target for your hostname.
Whether you’re an e-commerce site looking to route image traffic to the best-performing cloud storage for faster load times, a media company distributing video content efficiently across various cloud providers, or Continue reading
Introducing high-definition portrait video support for Cloudflare Stream

Cloudflare Stream is an end-to-end solution for video encoding, storage, delivery, and playback. Our focus has always been on simplifying all aspects of video for developers. This goal continues to motivate us as we introduce first-class portrait (vertical) video support today. Newly uploaded or ingested portrait videos will now automatically be processed in full HD quality.
Why portrait video
In the past few years, the popularity of portrait video has exploded, motivated by short-form video content applications such as TikTok or YouTube Shorts. However, Cloudflare customers have been confused as to why their portrait videos appear to be lower quality when viewed on portrait-first devices such as smartphones. This is because our video encoding pipeline previously did not support high-quality portrait videos, leading them to be grainy and lower quality. This pain point has now been addressed with the introduction of high-definition portrait video.
The current stream pipeline
When you upload a video to Stream, it is first encoded into several different “renditions” (sizes or resolutions) before delivery. This is done in order to enable playback in a wide variety of network conditions, as well as to standardize the way a video is experienced. By using these adaptive bitrate Continue reading
Simplify cloud routing and object storage configurations with Cloud Connector

Introduction
As part of Cloudflare's mission to help build a better Internet, we’re continuously integrating with other networks and service providers, ensuring ease of use for anyone, anywhere, anytime.
Today, we’re excited to announce Cloud Connector – a brand-new way to put Cloudflare in front of popular public cloud services, protecting your assets, accelerating applications, and routing your traffic between multiple cloud providers seamlessly.
Cloud Connector is a natural extension of Cloudflare's Connectivity Cloud, which aims to simplify and secure the complex web of connections across today’s enterprises. Imagine Origin Rules, but managed by Cloudflare, available for all plans, created with just a few clicks, and working out of the box without the need for additional rules. It allows you to route traffic to different public clouds without complicated workarounds. This means you can now direct specific requests to AWS S3, Google Cloud Storage, Azure Blob Storage, or our own R2, even if these services are not set as the DNS target for your hostname.
Whether you’re an e-commerce site looking to route image traffic to the best-performing cloud storage for faster load times, a media company distributing video content efficiently across various cloud providers, or Continue reading
Hedge 239: AI for Network Operations
There are (at least) three different aspects of AI in network engineering: network design to support AI, AI for development, and AI for operations. J.P. Vassuer joins Tom Ammon and Russ White to discuss AI for understanding and operating networks. What are the possibilities? What are the pitfalls? What can we expect to see?
NAN070: FakeNOS – An Open Source NOS for Network Testing
Today we spotlight an open-source project called FakeNOS. Whether you’re a network engineer looking to experiment in a controlled environment, or a DevOps engineer wanting to run a network testbed for your processes, you can use FakeNOS for your projects. My guests are FakeNOS creator Denis Mulyalin and the maintainer of this project, Enric Pitarch.... Read more »Paris 2024 Olympics recap: Internet trends, cyber threats, and popular moments

The Paris 2024 Summer Olympics wrapped up on August 11, 2024, with the Olympic flag being lowered in the Stade de France after 16 days of competitions. With 329 events across 32 sports, over 10,000 athletes from 204 nations participated in the pursuit of medals and glory, creating some viral online moments along the way. In this post, we turn our attention to the closing ceremony, the impact of various Olympic moments on Internet traffic, and the cyber attacks faced by sponsors. We also examine email trends related to the Olympics, including mentions of Simone Biles, Snoop Dogg, and Imane Khelif.
Cloudflare has a global presence with data centers in over 330 cities, supporting millions of customers with different tools and products, which provides a global view of what’s happening on the Internet. This is helpful for improving security, privacy, efficiency, and speed, but also for observing Internet disruptions and traffic trends.
In our previous blog post about the opening ceremony and the early days of the event, we showed how France was impacted by the Olympics, with clear drops in traffic during the main events. The opening ceremony caused the most significant drop—traffic decreased by as much as 20% Continue reading
Paris 2024 Olympics recap: Internet trends, cyber threats, and popular moments
The Paris 2024 Summer Olympics wrapped up on August 11, 2024, with the Olympic flag being lowered in the Stade de France after 16 days of competitions. With 329 events across 32 sports, over 10,000 athletes from 204 nations participated in the pursuit of medals and glory, creating some viral online moments along the way. In this post, we turn our attention to the closing ceremony, the impact of various Olympic moments on Internet traffic, and the cyber attacks faced by sponsors. We also examine email trends related to the Olympics, including mentions of Simone Biles, Snoop Dogg, and Imane Khelif.
Cloudflare has a global presence with data centers in over 330 cities, supporting millions of customers with different tools and products, which provides a global view of what’s happening on the Internet. This is helpful for improving security, privacy, efficiency, and speed, but also for observing Internet disruptions and traffic trends.
In our previous blog post about the opening ceremony and the early days of the event, we showed how France was impacted by the Olympics, with clear drops in traffic during the main events. The opening ceremony caused the most significant drop—traffic decreased by as much as 20% Continue reading
Arista cEOS Got Working MPLS Data Plane
Urs Baumann brought me a nice surprise last weekend. He opened a GitHub issue saying, “MPLS works on Arista cEOS containers in release 4.31.2F” and asking whether we could enable netlab to configure MPLS on cEOS containers.
After a few configuration tweaks and a batch of integration tests later, I had the results: everything worked. You can use MPLS on Arista cEOS with netlab release 1.9.0 (right now @ 1.9.0-dev2), and I’ll be able to create MPLS labs running in GitHub Codespaces in the not-too-distant future.