A New Survey Shows Few Actively Encrypting More Because of Internet Distrust

A new survey shows that only a handful of people who said they distrust the Internet are actively choosing encryption in response.
The survey, called the CIGI-Ipsos Global Survey on Internet Security and Trust, was conducted by Ipsos on behalf of the Canadian think tank the Centre for International Governance Innovation (CIGI). The Internet Society (ISOC) and the United Nations Conference on Trade and Development (UNCTAD) are partners in the survey, which is now in its fifth year.
The survey asked more than 25,000 individuals in 25 economies their opinion on Internet security, privacy, and trust.
Trust is very personal. The word “trust” may mean different things to different people. What we consider to be trust is constantly evolving and is shaped by many factors including our culture, our education, and our experience.
The survey asked users how much they agree or disagree with the statement “Overall, I trust the Internet”. We did not ask users how much they trust the Internet to perform in specific ways or to provide a specific user experience. However, the question provides a rough indicator of positive or negative attitudes towards the Internet.
74% of respondents in 2019 agreed with the statement Continue reading
Use Per-Link Prefixes in Network Data Models
We got pretty far in our data deduplication in network data model journey, from initial attempts to network modeled as a graph… but we still haven’t got rid of all the duplicate information.
For example, if we have multiple devices connected to the same subnet, why should we have to specify IP address and subnet mask for every device (literally begging the operators to make input errors). Wouldn’t it be better (assuming we don’t care about exact IP addresses on core links) to assign IP addresses automatically?
Cisco CEO Takes High Road on 5G, China
 Besides macro radio access network equipment, "we have virtually everything else you need to build...
Besides macro radio access network equipment, "we have virtually everything else you need to build...
Cisco Clarifies Vision, Need for Modern Networking at Cisco Live
 Cisco kicked off Cisco Live with a series of updates to its intent-based networking architecture to...
Cisco kicked off Cisco Live with a series of updates to its intent-based networking architecture to...
Americans Deserve Better User Privacy

On May 15th, the White House tweeted it had created a new online surveying tool for Americans to report instances of social media censorship due to political bias. Setting aside the politics of this move, there are serious privacy and security concerns that come with hosting such a survey on its website.
When users visit the reporting site, they’re required to give personal information including their name, citizenship status, zip code, phone number, and email address, all before any questions are actually asked about the alleged social media bias. They are then prompted to include links to their social media platforms, usernames, and other digitally-intrusive information.
Sound fishy? It should.
That is a significant amount of personal, highly-identifiable information to give up as a part of a selective survey. The irrelevance of most of this information to the survey’s purpose begs the question: why does the government need it and what will they use it for?
Neither question is answered anywhere in the survey or its related materials. That alone poses a serious privacy concern. If users don’t know how their data will be used, how can they trust that their information is secure and being used only for the Continue reading
Viavi Enterprise Provides Unexpected Network Insights

Many of us will have experienced the challenges of taking a performance alert (or user complaint) and drilling down to root cause. Performance issues can be intermittent, and it can be difficult to get visibility of what caused a problem at a particular time. Viavi Enterprise thinks it has the answer, combining analysis of packet feeds (e.g. from taps and mirror ports) and IPFix, xFlow and cloud service flow logs to monitor application performance as it would be experienced by a user. Sounds good? It looked pretty good, too.
Johnny Five Need Input!
Nothing can happen without data, and that comes from a number of potential sources.
Observer Gigastor

The Observer Gigastor product is available as a virtualized solution (to capture east-west traffic in virtualized environments), a portable appliance for tactical deployment, and two hardware appliance models (in a charming shade of purple) which can provide from 96TB to 1.2PB of storage. The idea of Gigastor is to capture packets at line rate and retain the raw packet data in case it’s needed later. The packets are analyzed, and that metadata is fed to the reporting and visualization system, Observer Apex.
Observer GigaFlow
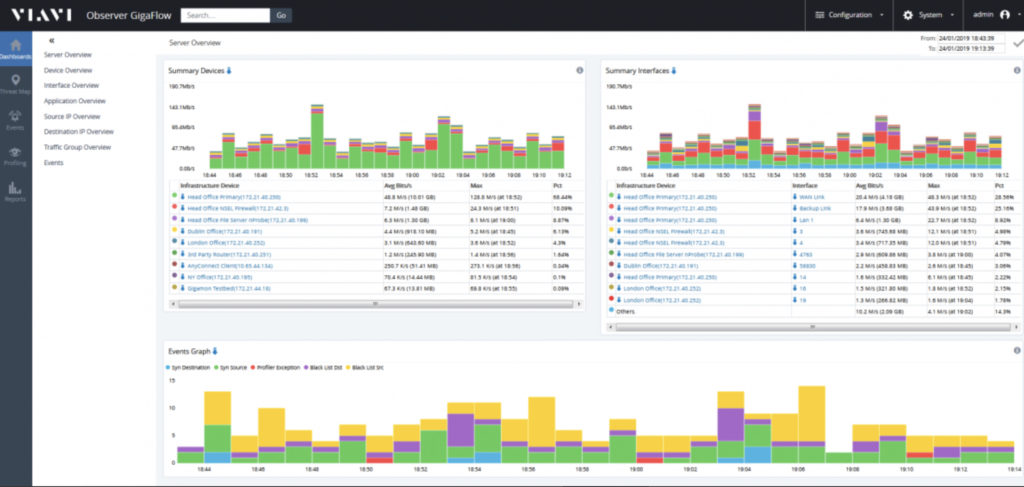
It’s not always possible Continue reading
The CCIE Times Are A Changing

Today is the day that the CCIE changes. A little, at least. The news hit just a little while ago that there are some changes to the way the CCIE certification and recertification process happens. Some of these are positive. Some of these are going to cause some insightful discussion. Let’s take a quick look at what’s changing and how it affects you. Note that these changes are not taking effect until February 24, 2020, which is in about 8 months.
Starting Your Engines
The first big change comes from the test that you take to get yourself ready for the lab. Historically, this has been a CCIE written exam. It’s a test of knowledge designed to make sure you’re ready to take the big lab. It’s also the test that has been used to recertify your CCIE status.
With the new change on Feb. 24th, the old CCIE written will go away. The test that is going to be used to qualify candidates to take the CCIE lab exam is the Core Technology exam from the CCNP track. The Core Technology exam in each CCNP track serves a dual purpose in the new Cisco certification program. If you’re Continue reading
Salesforce Plunks Billions on the Table for Tableau
 The nearly $16-billion deal comes just days after Google acquired data analytics firm Looker for...
The nearly $16-billion deal comes just days after Google acquired data analytics firm Looker for...
Cloud Service Providers Slow Server Spending, Cuts Into Dell, HPE’s Bottom Line
 The Dell’Oro Group market report also found Dell is the No. 1 server vendor by revenue share...
The Dell’Oro Group market report also found Dell is the No. 1 server vendor by revenue share...
◎ Standards Bodies, Patents, Huawei and Unexpected Consquences

Without access to standards bodies Huawei loses patent rights to a wide range of technology.
The post ◎ Standards Bodies, Patents, Huawei and Unexpected Consquences appeared first on EtherealMind.
Three Joins UK’s 5G Party With an Initial FWA Focus
 5G rollouts are ramping up in Europe as Vodafone also announced commercial launches in Italy and...
5G rollouts are ramping up in Europe as Vodafone also announced commercial launches in Italy and...
Reaction: Overly Attached
The longer you work on one system or application, the deeper the attachment. For years you have been investing in it—adding new features, updating functionality, fixing bugs and corner cases, polishing, and refactoring. If the product serves a need, you likely reap satisfaction for a job well done (and maybe you even received some raises or promotions as a result of your great work).
Attachment is a two-edged sword—without some form of attachment, it seems there is no way to have pride in your work. On the other hand, attachment leads to poorly designed solutions. For instance, we all know the hyper-certified person who knows every in and out of a particular vendor’s solution, and hence solves every problem in terms of that vendor’s products. Or the person who knows a particular network automation system and, as a result, solves every problem through automation.
The most pernicious forms of attachment in the network engineering world are to a single technology or vendor. One of the cycles I have seen play out many times across the last Continue reading
Network Break 238: Google Borks Itself; Apple Slices IoT Gadgets Into Security Zones
On today's Network Break we dive into Google's self-inflicted outage, examine Apple's new HomeKit partnerships and Sign In, discuss the IEEE's reversal on Huawei, and parse other IT and tech news bits.
The post Network Break 238: Google Borks Itself; Apple Slices IoT Gadgets Into Security Zones appeared first on Packet Pushers.
The Week in Internet News: Better Broadband Boosts Employment

High-speed jobs: A new study suggests that better broadband service lowers unemployment rates, Vice.com reports. Researchers from the University of Tennessee at Chattanooga and Oklahoma State University tracked broadband availability and unemployment rates in Tennessee and found that counties with access to high-speed broadband had a slightly lower unemployment rate than those with slower service.
More moderation: YouTube plans to remove white supremacist, hate speech and hoax videos, the Washington Post reports. The new policy will go farther than YouTube’s former prohibition on videos that promote violence or hatred against people based on their age, religious beliefs, gender, religion, immigration status and sexual orientation.
Encryption fight: Yandex, a provider of Internet-related services in Russia and the former Soviet Union, has reached an agreement with the Russian FSB security service on handing over encryption keys, Reuters reports. Details of the agreement weren’t immediately available. Yandex had originally resisted the FSB’s demand for encryption keys, Reuters says.
Bigger than the weather: U.S. residents believe fake news is a bigger problem than climate change or racism, according to a new survey detailed at Business Insider. Half of those surveyed said made-up news is a major problem, while just 46 said the Continue reading
Repost: Automation Without Simplification
The No Scripting Required to Start Your Automation Journey blog post generated lively discussions (and a bit of trolling from the anonymous peanut gallery). One of the threads focused on “how does automation work in real life IT department where it might be challenging to simplify operations before automating them due to many exceptions, legacy support…”
Here’s a great answer provided by another reader:
Read more ...Weekly Top Posts: 2019-06-09
- Google Cloud Lassos Data Analytics Provider Looker for $2.6B
- Pluribus Unveils White Box Gateway Router With Deep Slicing Capabilities
- VMware Sees ‘Significant Opportunity’ in $10B JEDI Deal
- Arista Fills Out Its Cognitive Enterprise Portfolio
- Cisco Scoops Up IoT Security Startup Sentryo