Tech Bytes: Leveraging Packets And Flows For NetOps And SecOps With VIAVI Solutions (Sponsored)
Find out how packet capture and flow data can serve both the network and security teams to solve performance problems and investigate security events in this sponsored Tech Bytes conversation with VIAVI Solutions. Our guest is Charles Thompson, Sr. Director, Product Management at VIAVI.
The post Tech Bytes: Leveraging Packets And Flows For NetOps And SecOps With VIAVI Solutions (Sponsored) appeared first on Packet Pushers.
Trump Campaign Revives Nationalized 5G Network Plan
 The plan calls for the government to take wireless spectrum from the Defense Department and use a...
The plan calls for the government to take wireless spectrum from the Defense Department and use a...
Juniper to Buy Mist Systems for $405 Million
 Juniper CEO called the purchase an "offensive move" against its networking competitors, namely...
Juniper CEO called the purchase an "offensive move" against its networking competitors, namely...
CrowdStrike Falcon Expands Wings to Target Mobile Device Security
 Falcon for Mobile identifies threats on mobile devices and provides visibility into situations...
Falcon for Mobile identifies threats on mobile devices and provides visibility into situations...
Network Break 224: Beware TLS Alternatives; Volta Networks And Veriflow Launch New Products
Today's Network Break examines a ETS, a proposed alternative to TLS 1.3 that enables decryption, looks at ICAAN's call for DNSSEC everywhere, discusses new products from startups Volta Networks and Veriflow, and much more tech news.
The post Network Break 224: Beware TLS Alternatives; Volta Networks And Veriflow Launch New Products appeared first on Packet Pushers.
Is it Balance, or Workism?
While we tend to focus on work/life balance, perhaps the better question is: how effective are we at using the time we use for work? From a recent study (which you may have already seen):
- Workers average just 2 hours and 48 minutes of productive device time a day
- 21% of working hours are spent on entertainment, news, and social media
- 28% of workers start their day before 8:30 AM (and 5% start before 7 AM)
- 40% of people use their computers after 10 PM
- 26% of work is done outside of normal working hours
- Workers average at least 1 hour of work outside of working hours on 89 days/year (and on ~50% of all weekend days)
- We check email and IM, on average, every 6 minutes
This is odd—we are starting work earlier, finishing later, and working over weekends, but we still only “work” less than three hours a day.
The first question must be: is this right? How are they measuring productive versus unproductive device time? What is “work time,” really? I know I don’t keep any sort of recognizable “office hours,’ so it seems like it would be hard to measure how much time I spend Continue reading
AT&T Claims Open ROADM Success Validates Interoperability Work
 The demonstration is using open APIs to connect the entire system to a programmable optical network...
The demonstration is using open APIs to connect the entire system to a programmable optical network...
Google, VMware Team Up With Lookout on Post-Perimeter Security Alliance
 Alliance members will demonstrate how their products and services work together to secure...
Alliance members will demonstrate how their products and services work together to secure...
Wireshark 3.0 Released
Recently, Wireshark dropped a major release which adds a few cool features (some new and some old). However outside of the new features, there is one major under the hood change this feature introduces. WireShark v3 for Windows now ships with Npcap as opposed to Winpcap that we have been used forever now. Npcap is […]Building fast interpreters in Rust
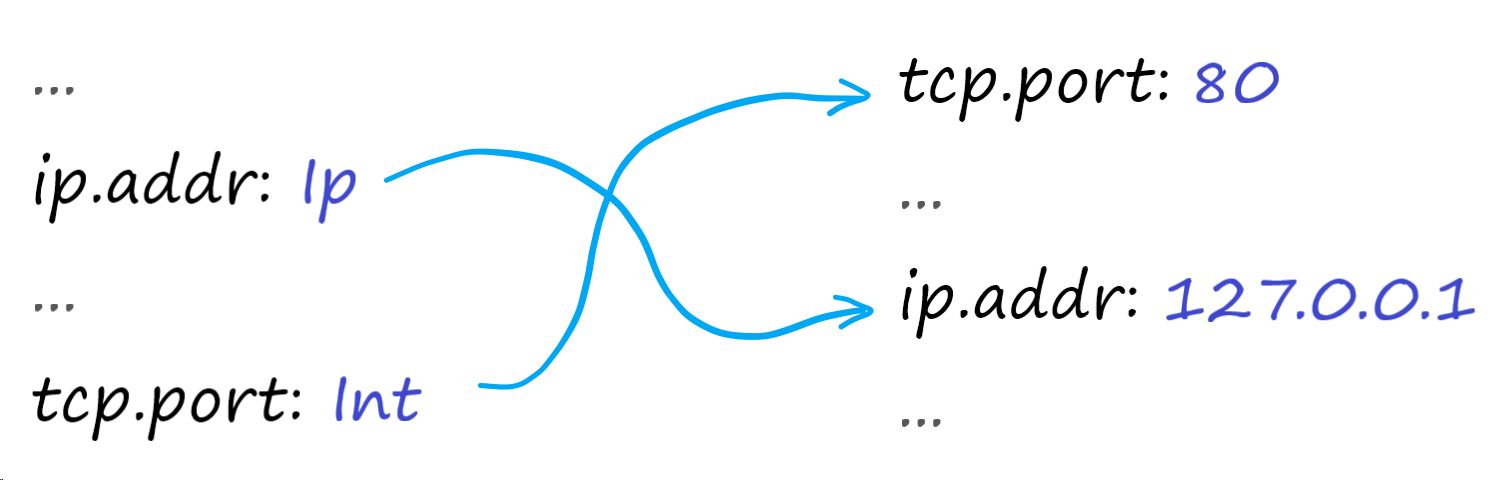
In the previous post we described the Firewall Rules architecture and how the different components are integrated together. We also mentioned that we created a configurable Rust library for writing and executing Wireshark®-like filters in different parts of our stack written in Go, Lua, C, C++ and JavaScript Workers.
With a mixed set of requirements of performance, memory safety, low memory use, and the capability to be part of other products that we’re working on like Spectrum, Rust stood out as the strongest option.
We have now open-sourced this library under our Github account: https://github.com/cloudflare/wirefilter. This post will dive into its design, explain why we didn’t use a parser generator and how our execution engine balances security, runtime performance and compilation cost for the generated filters.
Parsing Wireshark syntax
When building a custom Domain Specific Language (DSL), the first thing we need to be able to do is parse it. This should result in an intermediate representation (usually called an Abstract Syntax Tree) that can be inspected, traversed, analysed and, potentially, serialised.
There are different ways to perform such conversion, such as:
- Manual char-by-char parsing using state machines, regular expression and/or native string APIs.
- Parser combinators, which use Continue reading
Microsoft Azure Sentinel Moves SIEM to the Cloud
 The vendor claims it’s the first cloud native security information and event management (SIEM)...
The vendor claims it’s the first cloud native security information and event management (SIEM)...
Short Take – Navigating Technology Change
In and industry where technology seems to change overnight sometimes, how should you decide what you should and shouldn’t invest time in? Are there techniques you can use to optimize navigating technology change? In this Short Take, Russ shares his take on how you should analyze new technologies and intelligently approach new tech to not be ahead or behind of the curve.
The post Short Take – Navigating Technology Change appeared first on Network Collective.
Improve Productivity. Shut Off Notifications. (YouTube)
Here’s a short car video where I recommend shutting off notifications as a way to increase productivity. Spoiler alert. That’s pretty much the summary of the entire video, so you can save yourself the four minutes. Or…watch it to get the nuance. I’ll be okay either way. I’m not making money on YouTube ads.
The Week in Internet News: Many Ugandans Quit Internet Services After Tax on Social Media

Taxing the Internet: A social media tax in Uganda has prompted many users to quit those same sites, The Guardian reports. The tax, intended to raise government revenues and discourage “idle talk,” amounts to 200 Ugandan shillings, or about U.S. 5 cents, per day. More than one million people have quit taxed mobile apps, the story says.
Tough measures: A large majority of Europeans support a proposal to require social media companies to direct all users who have seen take news toward fact-checks, Time.com says. A recent poll suggest that more than 86 percent of European residents surveyed support the Correct the Record proposal from advocacy group Avaaz.
Blockchain goes to pot: Blockchain technology can help marijuana dispensaries enforce daily legal limits on individual purchases, Forbes reports. Blockchain could help dispensaries keep track of attempts at smurfing, the practice of purchasing more than the daily legal limit by going to different dispensaries, and looping, purchasing more than the limit by returning later to the same seller, the story says.
Blockchain vs. censorship: A follow-up to a trend we noted earlier this year: China’s residents are turning to blockchain technologies to fight government censorship, The Conversation reports. Some users Continue reading
How we made Firewall Rules


Recently we launched Firewall Rules, a new feature that allows you to construct expressions that perform complex matching against HTTP requests and then choose how that traffic is handled. As a Firewall feature you can, of course, block traffic. The expressions we support within Firewall Rules along with powerful control over the order in which they are applied allows complex new behaviour.
In this blog post I tell the story of Cloudflare’s Page Rules mechanism and how Firewall Rules came to be. Along the way I’ll look at the technical choices that led to us building the new matching engine in Rust.
The evolution of the Cloudflare Firewall
Cloudflare offers two types of firewall for web applications, a managed firewall in the form of a WAF where we write and maintain the rules for you, and a configurable firewall where you write and maintain rules. In this article, we will focus on the configurable firewall.
One of the earliest Cloudflare firewall features was the IP Access Rule. It dates backs to the earliest versions of the Cloudflare Firewall and simply allows you to block traffic from specific IP addresses:
if request IP equals 203.0.113.1 then block Continue reading


