Baidu’s Cloud Playbook Goes ‘All Out’ for AI
 Baidu, China’s search and ad giant, has aggressively re-focused its business on artificial intelligence and connected vehicles as the U.S.-China trade war heats up and online advertising becomes less profitable.
Baidu, China’s search and ad giant, has aggressively re-focused its business on artificial intelligence and connected vehicles as the U.S.-China trade war heats up and online advertising becomes less profitable.
Netskope IDs New Google Cloud Attack, McAfee Finds Ransomware
 Threat researchers at Netskope and McAfee this week described new and potentially dangerous networking vulnerabilities.
Threat researchers at Netskope and McAfee this week described new and potentially dangerous networking vulnerabilities.
Linux Foundation Launches LF Edge Group With 5 Projects
 The new group’s list of founding members reads like a who’s who of chipmakers, telecommunications companies, cloud providers, edge infrastructure vendors, and others.
The new group’s list of founding members reads like a who’s who of chipmakers, telecommunications companies, cloud providers, edge infrastructure vendors, and others.
Vodafone Loses Its Head of Cloud, Automation Fran Heeran to Nokia
 This is the latest in a series of major changes at Vodafone, which just said goodbye to a number of executives and announced large real estate changes in the U.K.
This is the latest in a series of major changes at Vodafone, which just said goodbye to a number of executives and announced large real estate changes in the U.K.
IBM’s Multi-Million Dollar Cloud Wins Keep on Coming
 Another day, another multi-million dollar cloud deal for IBM, which signed a $260 million agreement with the Bank of the Philippine Islands.
Another day, another multi-million dollar cloud deal for IBM, which signed a $260 million agreement with the Bank of the Philippine Islands.
HTTP/3: From root to tip
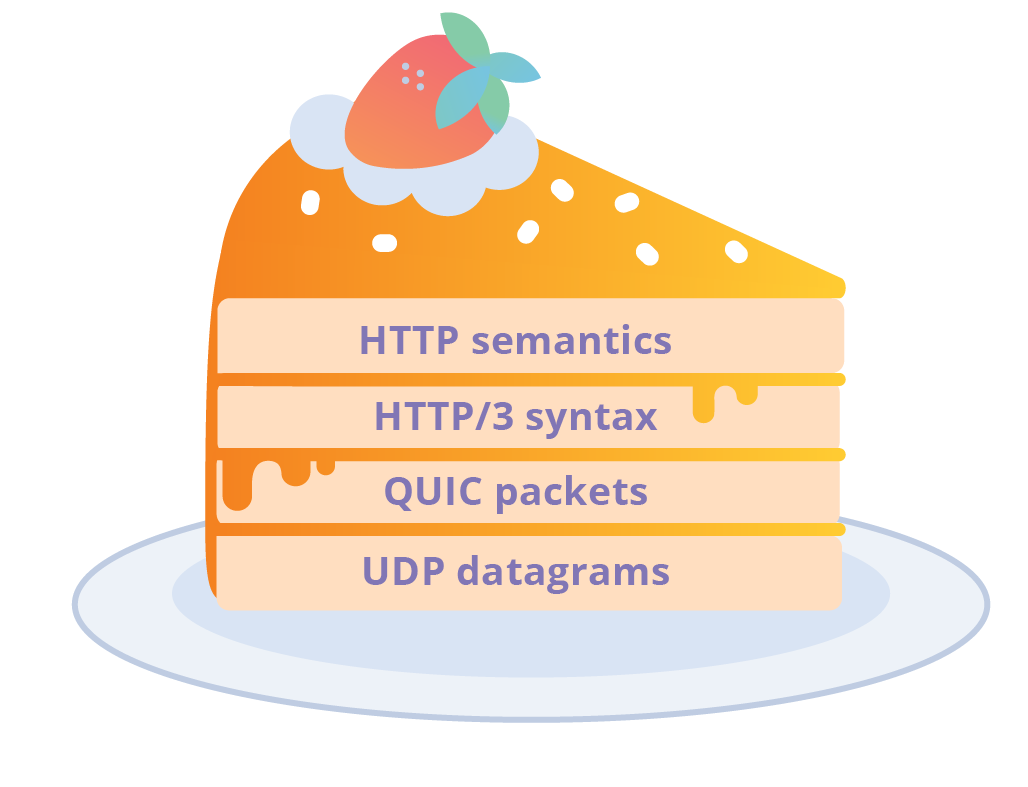
HTTP is the application protocol that powers the Web. It began life as the so-called HTTP/0.9 protocol in 1991, and by 1999 had evolved to HTTP/1.1, which was standardised within the IETF (Internet Engineering Task Force). HTTP/1.1 was good enough for a long time but the ever changing needs of the Web called for a better suited protocol, and HTTP/2 emerged in 2015. More recently it was announced that the IETF is intending to deliver a new version - HTTP/3. To some people this is a surprise and has caused a bit of confusion. If you don't track IETF work closely it might seem that HTTP/3 has come out of the blue. However, we can trace its origins through a lineage of experiments and evolution of Web protocols; specifically the QUIC transport protocol.
If you're not familiar with QUIC, my colleagues have done a great job of tackling different angles. John's blog describes some of the real-world annoyances of today's HTTP, Alessandro's blog tackles the nitty-gritty transport layer details, and Nick's blog covers how to get hands on with some testing. We've collected these and more at https://cloudflare-quic.com. And if that tickles your fancy, be sure Continue reading
CoreDNS Becomes First CNCF Graduate of 2019
 CoreDNS replaced kube-dns as the default DNS server in the most recent update of Kubernetes. It is the fourth project to graduate CNCF.
CoreDNS replaced kube-dns as the default DNS server in the most recent update of Kubernetes. It is the fourth project to graduate CNCF.
EU Trumpets 5G Progress as Number of Trials Hits 138
 The most important 5G pilot in the EU to date, according to the report, was carried out by Elisa in Finland because it used at least two cell sites and involved end users.
The most important 5G pilot in the EU to date, according to the report, was carried out by Elisa in Finland because it used at least two cell sites and involved end users.
Thoughts before CLEUR 2019
In just 3 days time I will be leaving for Cisco Live 2019 in Barcelona. Im thinking about what sort of event it will be and what to expect in term of announcements.
Especially one thought keeps reappearing and thats the thought of the transformation of Cisco. It is no longer a company with a future in just selling hardware. It itself has been disrupted by the emergence of “everything software” and merchant silicon.
The issues and consequences of merchant silicon has been discussed in many places, so I won’t mention them in this post, other than saying it has in some way forced Cisco’s hands in going down the route of being a software and services company.
Especially the software component will be huge this year. If you need proof of this, just look at the very large following as well as events from the Cisco DevNet community. But is this transformation smooth sailing from here? — I think not.
Traditionally Cisco’s reputation in the industry when it comes to software has been very flaky, to say the least. Something a lot of engineers hope will change in the coming years.
That being said, I think a lot of Continue reading
IPv6 Buzz 018: Inside The IETF With Fred Baker
On today's IPv6 Buzz we examine the influence of the Internet Engineering Task Force (IETF) in today's technology landscape, particularly around the Internet Protocol (IP). Our guest is Fred Baker, emeritus chair of the IETF.IPv6 Buzz 018: Inside The IETF With Fred Baker
On today's IPv6 Buzz we examine the influence of the Internet Engineering Task Force (IETF) in today's technology landscape, particularly around the Internet Protocol (IP). Our guest is Fred Baker, emeritus chair of the IETF.
The post IPv6 Buzz 018: Inside The IETF With Fred Baker appeared first on Packet Pushers.
Pluribus Networks: Ready to Deliver
As we begin the new year, there are several powerful market trends converging, driving demand for our solutions and growth...Introducing a new software platform that offers improved Chapter management functionality and much more
On 31 January, 2019, we will be launching our new association management software (AMS) that will offer many new capabilities to Internet Society members and Chapters.
During the roll-out of the new platform, the current AMS will be offline for several days (details below).
Internet Society members will be familiar with our current AMS if you have ever clicked on the “Member Login” link in the upper right corner of this web page. You also used the AMS if you logged into our Connect member forums or took an online course using our Inforum system. Chapter leaders have become very familiar with our AMS over the years, as it is the way they have interacted with their members and performed administrative functions for the Chapter.
Due to some functional limitations with the current AMS, we are replacing the system with a new AMS that will provide:
- A more modern system with enhanced functionality and user interface
- Core chapter management functionality to meet long-standing requirements/requests of our chapters
- Improved global/regional performance, particularly in low-bandwidth environments, through the use of a content delivery network (CDN)
- Events management capabilities
- Complete server and software management by the vendor – consistent and timely updates/upgrades Continue reading
Battle of the Multi-Clouds: SD-WANs, VPNs, and More
 Expect network connectivity between clouds to get more complicated.
Expect network connectivity between clouds to get more complicated.
