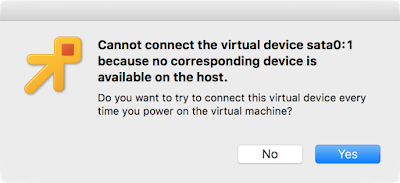
Cannot connect the virtual device … because no corresponding device is available on the host
Recently I've been building some VM templates on my MacBook and launching instances of them in VMware. Each time it produced following error:Cannot connect the virtual device sata0:1 because no corresponding device is available on the host.
Either button caused the guest to boot up. The "No" button ensured that it booted without error on subsequent reboots, while choosing "Yes" allowed me to enjoy the error with each power-on of the guest.
Sata0 is, of course a (virtual) disk controller, and device 1 is an optical drive. I knew that much, but the exact meaning of the error wasn't clear to me, and googling didn't lead to a great explanation.
I wasn't expecting there to be a "corresponding device ... available on the host" because the host has neither a SATA controller nor an optical drive, and no such hardware should be required for my use case, so, what did the error mean?
It turns out that I was producing the template (a .ova file) with the optical drive "connected" (VMware term) to ... something. The issue isn't related to the lack of a device on the host, but that there's no ISO file "inserted" into the virtual drive.
Here's the Continue reading
AT&T Outlines 3 Pillars of Its 5G Strategy
 They are mobile 5G, fixed wireless, and edge computing, and AT&T says it is building its networks to allow “LTE to work efficiently in parallel with 5G.” “
They are mobile 5G, fixed wireless, and edge computing, and AT&T says it is building its networks to allow “LTE to work efficiently in parallel with 5G.” “
Accenture Upgrades Linux Foundation Membership, Expands ONAP Work
 Accenture has been working on a commercial version of ONAP to support providers’ transition from hardware-based to software-based networks.
Accenture has been working on a commercial version of ONAP to support providers’ transition from hardware-based to software-based networks.
Security VC Funding Hit Record $5.3 Billion in 2018
 But “this rate of investment is not sustainable,” Strategic Cyber Ventures warns. There are likely many security “zombies” that initially raised big rounds but now growth has slowed.
But “this rate of investment is not sustainable,” Strategic Cyber Ventures warns. There are likely many security “zombies” that initially raised big rounds but now growth has slowed.
When Metaphors Fail
We often use metaphors to describe a particular part of a thing or the thing itself. For instance, we might say “I’m as hungry as a horse,” to describe how much we think we could eat (although a more appropriate saying might be “as hungry as a bird,” as it turns out!). Network operators and engineers are no exception to this making of metaphors, of course.
Metaphors have a reductionistic tendency. For instance, when saying I am as hungry as a horse, I am relating the amount of food a horse might eat to the amount of food I feel like eating. The metaphor reduces the entire person and the entire horse so the turn on a single point—a quantity of food. In using this kind of comparison, I am not claiming to have the same number of legs as a horse, or perhaps a swishing tail like a horse.
The danger in using a metaphor is that you can take the part to be the whole. When this happens, the metaphor says things it should not say, and can cause us to misunderstand the scope, complexity, or solution to a problem. For some reason, we tend to do Continue reading
LDP Multipath/ECMP
In one of our last posts on MPLS – we showed how LDP can be used to dynamically exchange labels between MPLS enabled routers. This was a huge improvement from statically configured LSPs. We saw that LDP was tightly coupled to the underlying IGP but we didn’t spend a lot of time showing examples of that. In this post, I want to extend our lab a little bit to show you exactly how tightly this coupling is. To do so, we’ll use part of the extended lab that we created at the end of our last post on the JunOS routing table. For the sake of being thorough, we’ll provide the entire configuration of each device. The lab will look like what’s shown below…

For a base configuration – we’re going to start with mostly everything there with the exception of MPLS and LDP. We’ll then add that in stages so we can see how things look before and after we have multiple IGP paths to the same destination…
vMX1 Configuration…
system {
host-name vmx1.lab;
}
interfaces {
ge-0/0/0 {
unit 0 {
family inet {
address 10.2.2.0/31;
}
}
}
ge-0/0/1 {
unit 0 {
Continue reading
Cisco, Akamai Participate In EdgeMicro Live Testing
 According to EdgeMicro, these proof-of-concept edge computing tests are the last step before deployment.
According to EdgeMicro, these proof-of-concept edge computing tests are the last step before deployment.
Network Break 218: AWS Launches New Backup Service; Rubrik Rakes In VC Bucks
Today's Network Break analyzes a new AWS backup service, Rubrik's latest infusion of VC cash, whether the tech sector has reached its natural growth limit and what that means for how tech companies are valued, a Juniper/IBM deal, and more.
The post Network Break 218: AWS Launches New Backup Service; Rubrik Rakes In VC Bucks appeared first on Packet Pushers.
Tech Bytes: Understanding Cisco’s Smart Net Total Care (Sponsored)
On today's Tech Bytes, sponsored by Comstor, we're going to dive into Cisco's Smart Net Total Care. We discuss different service options and examine the Collector software that can help organizations get a handle on Cisco software licenses, updates, and bug fixes.
The post Tech Bytes: Understanding Cisco’s Smart Net Total Care (Sponsored) appeared first on Packet Pushers.
Dell’Oro: 5G NR to Boost RAN Investments to $160B in Five Years
 Research group sees reasons to be cheerful as mobile infrastructure market set to see turnaround after three consecutive years of declining revenues thanks to 5G New Radio.
Research group sees reasons to be cheerful as mobile infrastructure market set to see turnaround after three consecutive years of declining revenues thanks to 5G New Radio.
The Week in Internet News: IoT Hacked? Who Knows?

IoT survey: Nearly half of all companies using IoT devices don’t have mechanisms in place to detect if any of their devices have been hacked, according to a survey featured in a Fast Company story. Just 14 percent of the respondents to the Gemalto survey believe providing security is an ethical consideration.
Huge leak: More than 22 million unique passwords and 772 million email addresses were leaked and distributed by hackers in a folder named “Collection #1,” Mashable reports. The cache of emails and passwords were collected from several data, dating back to 2008.
Pushing back: WhatsApp is planning to fight India’s recent crackdown on encryption, FT.com reports. Indian policymakers have proposed rules that would allow authorities to trace the origin of encrypted messages, but WhatsApp says it will protest the proposals.
Fighting fake news: Japan’s government plans to come up with a plan to fight fake news by June, Japan Times says. The plan could include requiring social media companies to create codes of conduct. Several other attempts by governments to fight fake news have led to concerns about censorship, however.
AI as a weapon: Forbes.com has a story raising concerns about the weaponization of Artificial Intelligence. Continue reading
Argo Tunnel + DC/OS
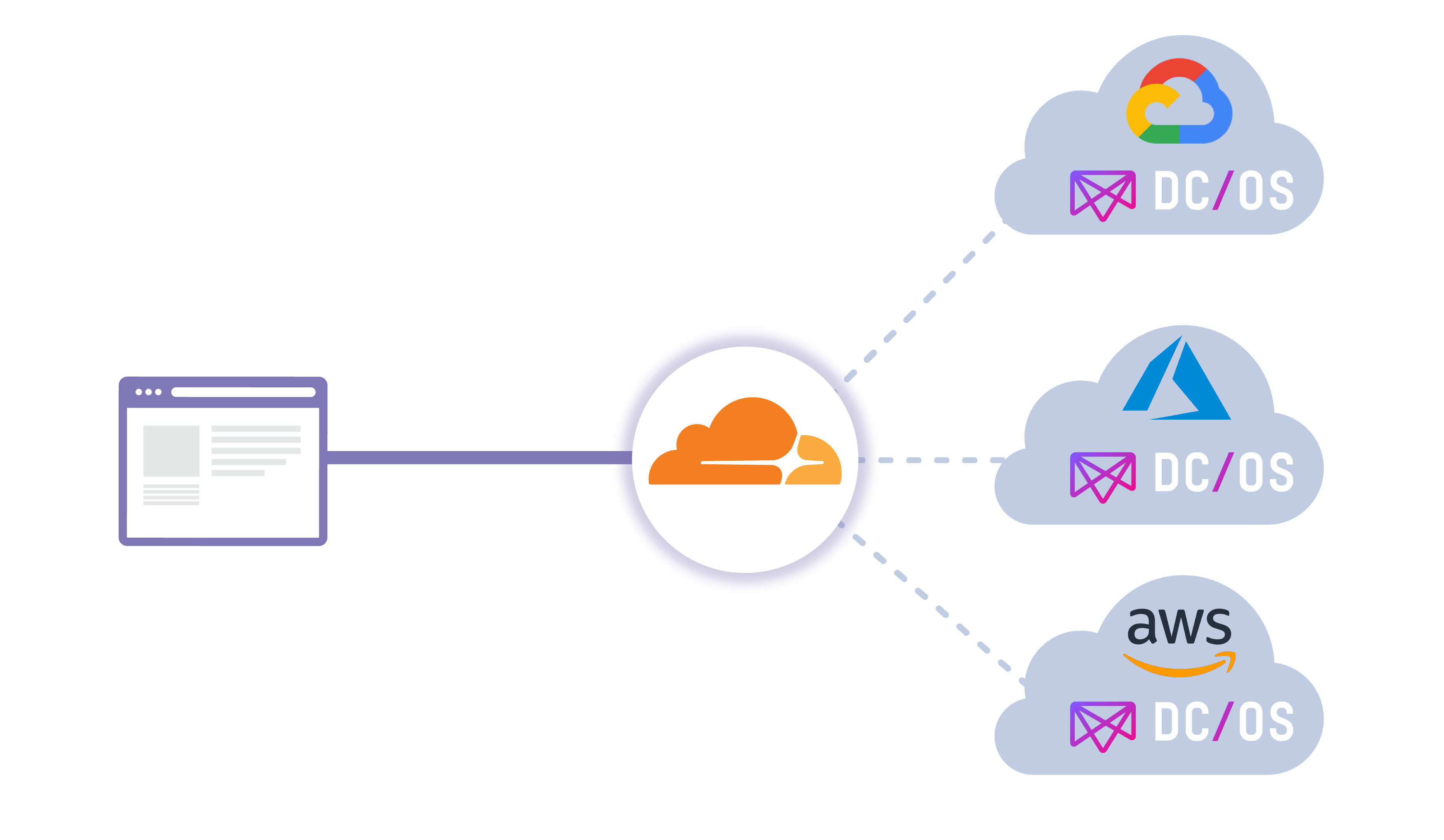
Cloudflare is proud to partner with Mesosphere on their new Argo Tunnel offering available within their DC/OS (Data Center / Operating System) catalogue! Before diving deeper into the offering itself, we’ll first do a quick overview of the Mesophere platform, DC/OS.
What is Mesosphere and DC/OS?
Mesosphere DC/OS provides application developers and operators an easy way to consistently deploy and run applications and data services on cloud providers and on-premise infrastructure. The unified developer and operator experience across clouds makes it easy to realize use cases like global reach, resource expansion, and business continuity.
In this multi cloud world Cloudflare and Mesosphere DC/OS are great complements. Mesosphere DC/OS provides the same common services experience for developers and operators, and Cloudflare provides the same common service access experience across cloud providers. DC/OS helps tremendously for avoiding vendor lock-in to a single provider, while Cloudflare can load balance traffic intelligently (in addition to many other services) at the edge between providers. This new offering will allow you to load balance through the use of Argo Tunnel.
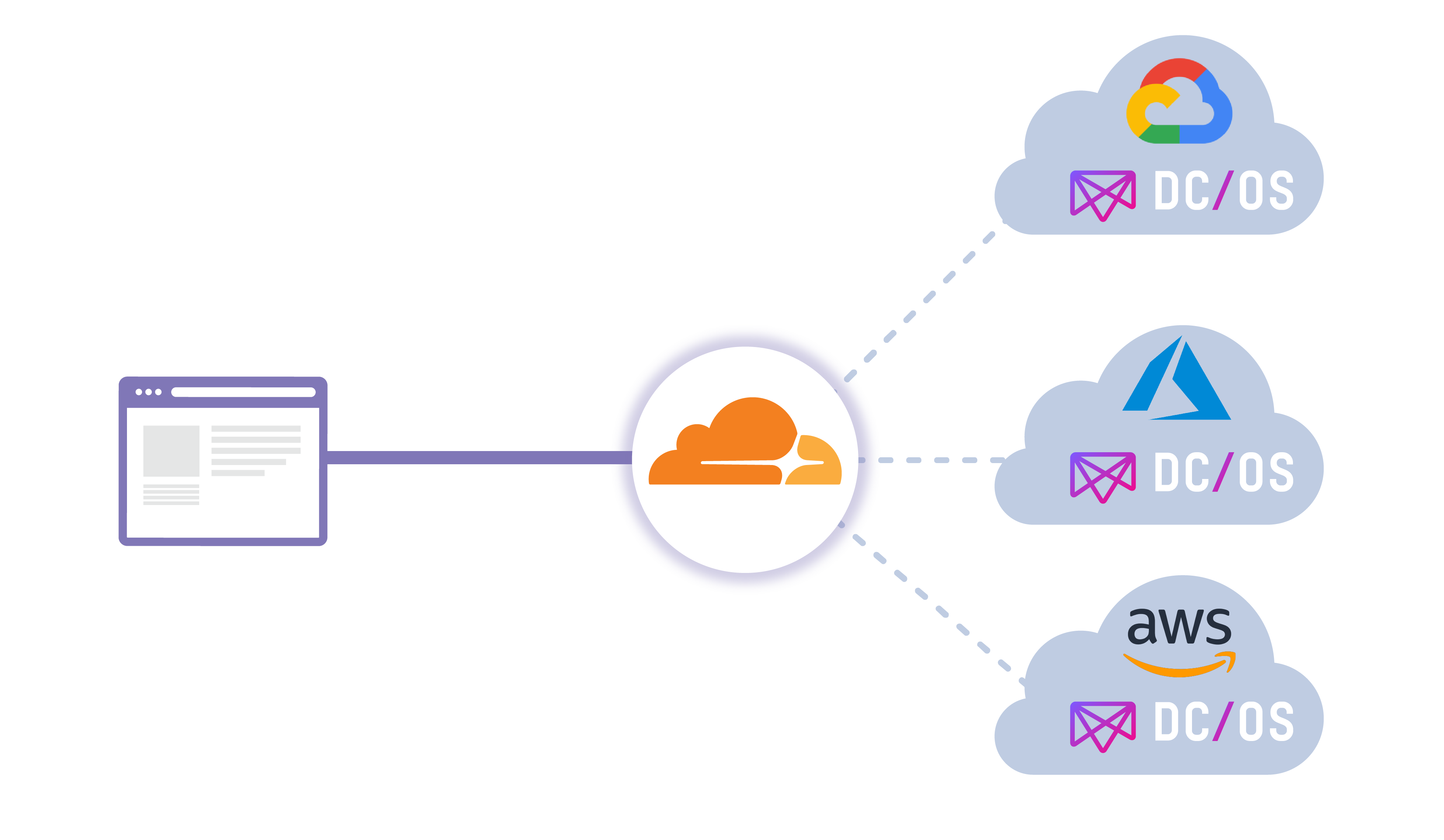
Quick Tunnel Refresh
Cloudflare Argo Tunnel is a private connection between your services and Cloudflare. Tunnel makes it such that only traffic that routes through the Continue reading
Exporting Flow to multiple servers (Flow Samplicators)
The post Exporting Flow to multiple servers (Flow Samplicators) appeared first on Noction.
Can a Hybrid Cloud Strategy Boost IT Transformation Adoption?
Breaking out of old perceptions about the role of IT departments be the key to being part of companies' overall digital transformation strategies.
QNA: How could an EIGRP Stuck In Active event ever happen in real life?

War stories on EIGRP Stuck In Active.
The post QNA: How could an EIGRP Stuck In Active event ever happen in real life? appeared first on EtherealMind.
Continuous Integration in Network Automation
In the first part of his interview with Christoph Jaggi Kristian Larsson talked about the basics of CI testing. Now let’s see how you can use these concepts in network automation (and you’ll learn way more in Kristian’s talk on April 9th… if you register for our network automation course).
How does CI testing fit into an overall testing environment?
Traditionally, in particular in the networking industry, it's been rather common to have proof of concepts (POC) delivered by vendors for various networking technologies and then people have sat down and manually tested that the POC meets some set of requirements.
Read more ...New Year, New Home
We have left the Bay Area, and headed North. We have moved to the Greater Seattle area - specifically the Eastside, between Bellevue and Redmond. We’ve given up the old apartment in San Francisco for a larger, nicer house…for a lot less in rent. A lot fewer bars & restaurants, a lot more trees, parks and lakes.
But Why?
The typical Bay Areas response is: “But why??? It rains all the time in the Pacific Northwest!!!!”
A few things:
1. Yes, it rains more here than San Francisco, but not as much as people think. It’s not even in the top 10 cities in the US for annual rainfall. Boston, New York, Washington DC all receive more.
2. Rain is OK. In fact rain is good. You don’t get lush forests through irrigation. You also don’t get clean streets just from street sweepers.
The main attractions for us are:
-
Much better lifestyle for us. It’s easy to go mountain biking, running, hiking, skiing here.
-
Much lower rent. Yes, rents have gone up a lot here, but it’s still much better value than San Francisco. I pay much less rent here, but I get a nice place, and the Continue reading
New Year, New Home
We have left the Bay Area, and headed North. We have moved to the Greater Seattle area - specifically the Eastside, between Bellevue and Redmond. We’ve given up the old apartment in San Francisco for a larger, nicer house…for a lot less in rent. A lot fewer bars & restaurants, a lot more trees, parks and lakes.
But Why?
The typical Bay Areas response is: “But why??? It rains all the time in the Pacific Northwest!!!!”
A few things:
1. Yes, it rains more here than San Francisco, but not as much as people think. It’s not even in the top 10 cities in the US for annual rainfall. Boston, New York, Washington DC all receive more.
2. Rain is OK. In fact rain is good. You don’t get lush forests through irrigation. You also don’t get clean streets just from street sweepers.
The main attractions for us are:
-
Much better lifestyle for us. It’s easy to go mountain biking, running, hiking, skiing here.
-
Much lower rent. Yes, rents have gone up a lot here, but it’s still much better value than San Francisco. I pay much less rent here, but I get a nice place, and the Continue reading
New Year, New Home
We have left the Bay Area, and headed North. We have moved to the Greater Seattle area - specifically the Eastside, between Bellevue and Redmond. We’ve given up the old apartment in San Francisco for a larger, nicer house…for a lot less in rent. A lot fewer bars & restaurants, a lot more trees, parks and lakes.
But Why?
The typical Bay Areas response is: “But why??? It rains all the time in the Pacific Northwest!!!!”
A few things:
1. Yes, it rains more here than San Francisco, but not as much as people think. It’s not even in the top 10 cities in the US for annual rainfall. Boston, New York, Washington DC all receive more.
2. Rain is OK. In fact rain is good. You don’t get lush forests through irrigation. You also don’t get clean streets just from street sweepers.
The main attractions for us are:
-
Much better lifestyle for us. It’s easy to go mountain biking, running, hiking, skiing here.
-
Much lower rent. Yes, rents have gone up a lot here, but it’s still much better value than San Francisco. I pay much less rent here, but I get a nice place, and the Continue reading