HN736: Understanding VMware by Broadcom (Sponsored)
Today on Heavy Networking, sponsored by Broadcom, we talk about VMware’s transition under Broadcom’s ownership. The acquisition has led to big changes that rolled out very quickly, including how VMware sells products and services – subscription only licensing, bundles of products, a hard stop on sales of existing licenses, overhaul of license issuance, and more.... Read more »Hedge 228: Five Execs Misunderstandings about Tech
Miscommunication between techies and business leaders are often caused by misunderstanding. Listen in as Eyvonne, Tom, and Russ discuss these misunderstandings and how we can address them.
Extending local traffic management load balancing to Layer 4 with Spectrum

In 2023, Cloudflare introduced a new load balancing solution, supporting Local Traffic Management (LTM). This gives organizations a way to balance HTTP(S) traffic between private or internal servers within a region-specific data center. Today, we are thrilled to be able to extend those same LTM capabilities to non-HTTP(S) traffic. This new feature is enabled by the integration of Cloudflare Spectrum, Cloudflare Tunnels, and Cloudflare load balancers and is available to enterprise customers. Our customers can now use Cloudflare load balancers for all TCP and UDP traffic destined for private IP addresses, eliminating the need for expensive on-premise load balancers.

A quick primer
In this blog post, we will be referring to load balancers at either layer 4 or layer 7. This is, of course, referring to layers of the OSI model but more specifically, the ingress path that is being used to reach the load balancer. Layer 7, also known as the Application Layer, is where the HTTP(S) protocol exists. Cloudflare is well known for our layer 7 capabilities, which are built around speeding up and protecting websites which run over HTTP(S). When we refer to layer 7 load balancers, we are referring to HTTP(S)-based services. Our layer Continue reading
Worth Reading: ChatGPT Does Not Summarize
I mostly gave up on LLMs being any help (apart from generating copious amounts of bullshit), but I still thought that generating summaries might be an interesting use case. I was wrong.
As Gerben Wierda explains in his recent “When ChatGPT summarises, it actually does nothing of the kind” blog post, you have to understand a text if you want to generate a useful summary, and that’s not what LLMs do. They can generate a shorter version of the text, which might not focus on the significant bits.
Worth Reading: ChatGPT Does Not Summarize
I mostly gave up on LLMs being any help (apart from generating copious amounts of bullshit), but I still thought that generating summaries might be an interesting use case. I was wrong.
As Gerben Wierda explains in his recent “When ChatGPT summarises, it actually does nothing of the kind” blog post, you have to understand a text if you want to generate a useful summary, and that’s not what LLMs do. They can generate a shorter version of the text, which might not focus on the significant bits.
NAN064: Get to Know NAF Co-Founder: Scott Robohn
Scott Robohn is responsible for so much of the current buzz and awareness of network automation. Today, we sit down with the co-founder of Network Automation Forum to learn about his own journey. We chat about his education and the question of if college degrees are necessary. We also talk about his experience at big... Read more »Disrupting FlyingYeti’s campaign targeting Ukraine

Cloudforce One is publishing the results of our investigation and real-time effort to detect, deny, degrade, disrupt, and delay threat activity by the Russia-aligned threat actor FlyingYeti during their latest phishing campaign targeting Ukraine. At the onset of Russia’s invasion of Ukraine on February 24, 2022, Ukraine introduced a moratorium on evictions and termination of utility services for unpaid debt. The moratorium ended in January 2024, resulting in significant debt liability and increased financial stress for Ukrainian citizens. The FlyingYeti campaign capitalized on anxiety over the potential loss of access to housing and utilities by enticing targets to open malicious files via debt-themed lures. If opened, the files would result in infection with the PowerShell malware known as COOKBOX, allowing FlyingYeti to support follow-on objectives, such as installation of additional payloads and control over the victim’s system.
Since April 26, 2024, Cloudforce One has taken measures to prevent FlyingYeti from launching their phishing campaign – a campaign involving the use of Cloudflare Workers and GitHub, as well as exploitation of the WinRAR vulnerability CVE-2023-38831. Our countermeasures included internal actions, such as detections and code takedowns, as well as external collaboration with third parties to remove the actor’s cloud-hosted malware. Continue reading
Cloudflare acquires BastionZero to extend Zero Trust access to IT infrastructure
We’re excited to announce that BastionZero, a Zero Trust infrastructure access platform, has joined Cloudflare. This acquisition extends our Zero Trust Network Access (ZTNA) flows with native access management for infrastructure like servers, Kubernetes clusters, and databases.
Security teams often prioritize application and Internet access because these are the primary vectors through which users interact with corporate resources and external threats infiltrate networks. Applications are typically the most visible and accessible part of an organization's digital footprint, making them frequent targets for cyberattacks. Securing application access through methods like Single Sign-On (SSO) and Multi-Factor Authentication (MFA) can yield immediate and tangible improvements in user security.
However, infrastructure access is equally critical and many teams still rely on castle-and-moat style network controls and local resource permissions to protect infrastructure like servers, databases, Kubernetes clusters, and more. This is difficult and fraught with risk because the security controls are fragmented across hundreds or thousands of targets. Bad actors are increasingly focusing on targeting infrastructure resources as a way to take down huge swaths of applications at once or steal sensitive data. We are excited to extend Cloudflare One’s Zero Trust Network Access to natively protect infrastructure with user- and device-based policies Continue reading
IPB152: IPv6 and Windows Active Directory
If you’re an Active Directory administrator or part of an enterprise network team working with one, this episode is for you. Ed literally wrote the book “Practical IPv6 for Windows Administrators” so Scott has fun interviewing him as today’s guest. Ed goes over how to diagram out your IPv6 deployment, including address allocation and making... Read more »BGP Labs: Graceful Shutdown
Using the typical default router configurations, it can take minutes between a failure of an inter-AS link and the convergence of BGP routes. You can fine-tune that behavior with BGP timers and BFD (and still get pwned by Graceful Restart). While you can’t influence link failures, you could drain the traffic from a link before starting maintenance operations on it, and it would be a shame not to do that considering there’s a standard way to do that – the GRACEFUL_SHUTDOWN BGP community defined in RFC 8326. That’s what you’ll practice in the next BGP lab exercise.
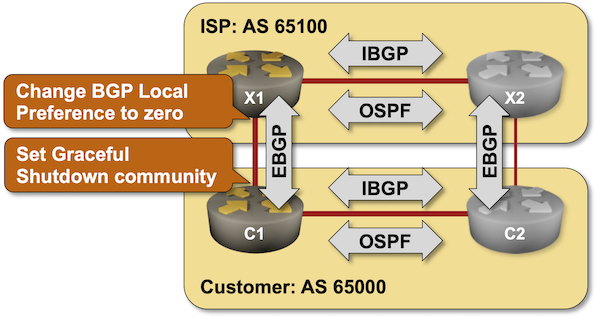
BGP Labs: Graceful Shutdown
Using the typical default router configurations, it can take minutes between a failure of an inter-AS link and the convergence of BGP routes. You can fine-tune that behavior with BGP timers and BFD (and still get pwned by Graceful Restart). While you can’t influence link failures, you could drain the traffic from a link before starting maintenance operations on it, and it would be a shame not to do that considering there’s a standard way to do that – the GRACEFUL_SHUTDOWN BGP community defined in RFC 8326. That’s what you’ll practice in the next BGP lab exercise.

On the ‘net: Modeling Tunnels
One reason the OSI model isnメt all that useful anymore is because it assumes things about networks that are no longer true, such as the existence of a clear set of protocols neatly layered one atop another. We just donメt build networks this way any longer.
The New Era of AI Centers
In 1984, Sun was famous for declaring, “The Network is the Computer.” Forty years later we are seeing this cycle come true again with the advent of AI. The collective nature of AI training models relies on a lossless, highly-available network to seamlessly connect every GPU in the cluster to one another and enable peak performance. Networks also connect trained AI models to end users and other systems in the data center such as storage, allowing the system to become more than the sum of its parts. As a result, data centers are evolving into new AI Centers where the networks become the epicenter of AI management.
Must Read: Make Two Trips
Tom Limoncelli wrote another must-read masterpiece: sometimes you’ll save time if you make two trips instead of one.
The same lesson applies to network design: cramming too many features into a single device will inevitably result in complex, hard-to-understand configurations and weird bugs. Sometimes, it’s cheaper to split the required functionality across multiple devices.
Must Read: Make Two Trips
Tom Limoncelli wrote another must-read masterpiece: sometimes you’ll save time if you make two trips instead of one.
The same lesson applies to network design: cramming too many features into a single device will inevitably result in complex, hard-to-understand configurations and weird bugs. Sometimes, it’s cheaper to split the required functionality across multiple devices.
Container Security: Protect your data with Calico Egress Access Controls
23andMe is a popular genetics testing company, which was valued at $6B in 2021. Unfortunately, there was a massive data breach in December 2023, which caused a steep decline in the company’s value and trust, plummeting the company to a penny stock. While this breach was not directly related to Kubernetes, the same risks apply to containers running in your Kubernetes environments. If your containerized applications do not have the right egress access controls defined, chances of data exfiltration are much higher.
The basics
A typical modus operandi for threat actors is to look for vulnerabilities or misconfiguration in the environment and workloads, install malicious pods through privilege escalation techniques, and then exploit this unsecured pod to exfiltrate data.

An easy reconnaissance technique by just scanning the cluster network for public-facing workloads will be a first starting point for most attackers. Privilege escalation occurs mostly due to inconsistent or incorrect RBAC policies in Kubernetes through which unauthorized users can gain root privileges. Vulnerabilities in container images as part of the supply chain are also another attack path. All of these techniques will ultimately land on an exposed pod with a remote code Continue reading

