Announcement: Cumulus recognized by both our employees & customers
It’s not every day you get recognized. But to get recognized TWICE in one day? Now that’s a rare experience. We’re thrilled to announce that Cumulus Networks has been recognized with both the FORTUNE 2018 50 Best Small and 100 Medium Size Companies to Work For award, as well as Gartner Customers’ Choice for Data Center Networking.
With recognition like this, we’re taking time to celebrate and appreciate the awesome and talented people we get to work with every day.
Cumulus awarded as a FORTUNE 2018 50 Best Small and 100 Medium Size Companies to Work For
The Fortune award is one of the most prestigious and for good reason — Their rigorous methodology focuses on more than just benefits and office snacks. According to their 2017 methodology statement:
All employees were invited to participate in the survey, which is designed to reveal whether the organization is consistently a great place to work for all its people. Meaning: Do employees trust the people they work for? Are they treated fairly and with respect? Are people proud of their work? Do they enjoy the folks they work with? Are great experiences available to everyone – or does it Continue reading
IPv6 Buzz 011: An IPv6 Address Planning Guide
Today's episode explores the ins and outs of IPv6 address planning, with IPv6 Buzz co-host Tom Coffeen in the guest chair. Tom discusses how to get away from "IPv4 thinking" when planning your v6 transition, and shares his real-world experiences of IPv6 adoption with CDNs and service providers.IPv6 Buzz 011: An IPv6 Address Planning Guide
Today's episode explores the ins and outs of IPv6 address planning, with IPv6 Buzz co-host Tom Coffeen in the guest chair. Tom discusses how to get away from "IPv4 thinking" when planning your v6 transition, and shares his real-world experiences of IPv6 adoption with CDNs and service providers.
The post IPv6 Buzz 011: An IPv6 Address Planning Guide appeared first on Packet Pushers.
DT, Intel, MobiledgeX Lead TIP’s Edge App Developer Project
 The group will produce vendor-neutral APIs and software tools focused on mobile functions running on edge infrastructure.
The group will produce vendor-neutral APIs and software tools focused on mobile functions running on edge infrastructure.
McAfee Uncovers New Security Threat Linked to China
 McAfee also added new products to its Mvision enterprise security portfolio including endpoint detection and response and an integrated data loss prevention policy engine across endpoints, networks, and the cloud.
McAfee also added new products to its Mvision enterprise security portfolio including endpoint detection and response and an integrated data loss prevention policy engine across endpoints, networks, and the cloud.
Encrypt that SNI: Firefox edition
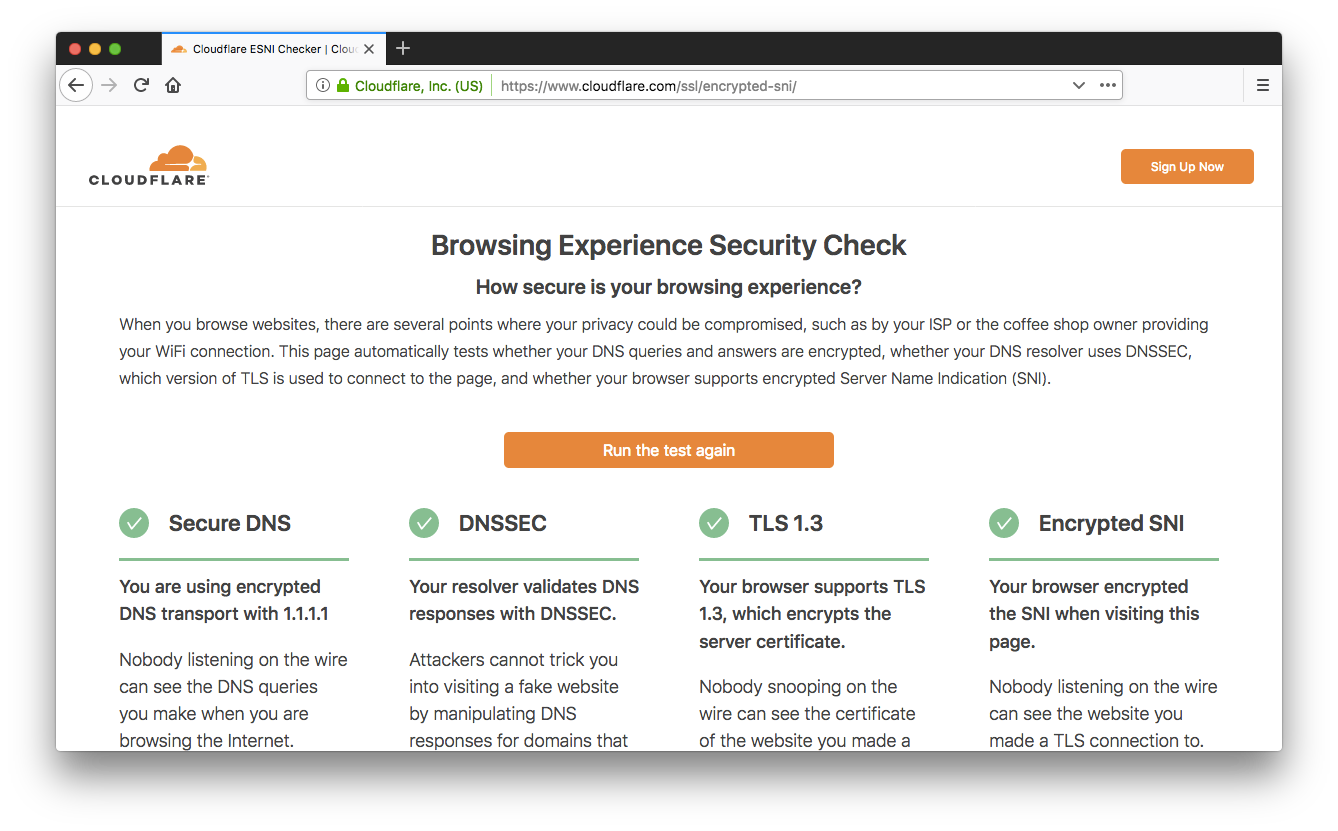
A couple of weeks ago we announced support for the encrypted Server Name Indication (SNI) TLS extension (ESNI for short). As promised, our friends at Mozilla landed support for ESNI in Firefox Nightly, so you can now browse Cloudflare websites without leaking the plaintext SNI TLS extension to on-path observers (ISPs, coffee-shop owners, firewalls, …). Today we'll show you how to enable it and how to get full marks on our Browsing Experience Security Check.

Here comes the night
The first step is to download and install the very latest Firefox Nightly build, or, if you have Nightly already installed, make sure it’s up to date.
When we announced our support for ESNI we also created a test page you can point your browser to https://encryptedsni.com which checks whether your browser / DNS configuration is providing a more secure browsing experience by using secure DNS transport, DNSSEC validation, TLS 1.3 & ESNI itself when it connects to our test page. Before you make any changes to your Firefox configuration, you might well see a result something like this:
So, room for improvement! Next, head to the about:config page and look for the network.security.esni.enabled Continue reading
AIOps the next big thing for Enterprise IT?
 Out of everything I think will be big in 2019, AIOps is near the top of the list. My current prediction is Artificial Intelligence (AI) making big moves in the enterprise IT Infrastructure and Operations market. AI-based technology is a hot topic in the media these days, everyone is exploring its benefits in a wide range of markets. From self-driving cars and industrial automation to advertising and fraud prevention. It’s no surprise that 2018 was predicted to be a dominating year for AI in IT. While I believe 2018 was a key year for AI getting it’s foot in the door of IT Ops, the reality is lagging behind the hype. In IT we hear a lot about machine learning, and big data, but with the reality of how this data is organized in most enterprises, the onus is still on us to get that data laid out in an organized structure to extract the potential that AI promises.
Out of everything I think will be big in 2019, AIOps is near the top of the list. My current prediction is Artificial Intelligence (AI) making big moves in the enterprise IT Infrastructure and Operations market. AI-based technology is a hot topic in the media these days, everyone is exploring its benefits in a wide range of markets. From self-driving cars and industrial automation to advertising and fraud prevention. It’s no surprise that 2018 was predicted to be a dominating year for AI in IT. While I believe 2018 was a key year for AI getting it’s foot in the door of IT Ops, the reality is lagging behind the hype. In IT we hear a lot about machine learning, and big data, but with the reality of how this data is organized in most enterprises, the onus is still on us to get that data laid out in an organized structure to extract the potential that AI promises.
But how does all of this relate to IT Infrastructure and Operations? AIOps is the combination of AI and IT Operations. And while the IT community hears the AI related buzzwords, not many of us know where or how it can Continue reading
Human Connection Frames Success of 2018 Indigenous Connectivity Summit

The Internet is an incredible tool that can help amplify voices that may not otherwise be heard. But when it comes to making sure everyone can have access to this tool, we can’t downplay the power of human connections to overcome connectivity challenges.
One of the things that stood out for me most at the 2018 Indigenous Connectivity Summit (ICS) last week in Inuvik, NT was getting a first-hand view of what happens when Indigenous voices are at the forefront of Internet solutions.
Nearly 140 people joined us in the Arctic Circle for a two-day series of panels and presentations focused on finding solutions to improve connectivity in rural and remote Indigenous communities, with a special focus on northern connectivity challenges. The livestream was viewed over 850 times.
It was inspiring to hear speakers shed light on the ways they innovated to bring Internet to underserved Indigenous communities on their own terms through Community Networks throughout North America and abroad.
I think some of the most important successes, however, came when ICS participants were able to interact during breaks, round-table discussions, on the bus trip to Tuktoyaktuk, at the community feast, and even on the flights to and from the Continue reading
Ciena Inflates Software Control to Reduce Network Complexity
 The company is expanding the reach of its SOAS software to boost IP capabilities and integrating Layer 3 expertise from its Packet Design acquisition.
The company is expanding the reach of its SOAS software to boost IP capabilities and integrating Layer 3 expertise from its Packet Design acquisition.
Splintering the Internet: The Unintended Consequence of Regulation

In early 2000, two Paris-based, anti-racism groups sued Yahoo on the basis that its auction’s site was exposing French people to more than 1,000 objects of Nazi memorabilia. In May of that year, a French court confirmed the illegal nature of the sale under French law, claiming that the company had offended France’s “collective memory.” More importantly, the judge also ordered Yahoo to identify ways to block French users from its Nazi auction site or other Yahoo sites with content deemed to be racist.
The case attracted significant attention, due to the legal precedent it could set on the right of one country to reach across borders and impose its own laws on online material stored in other countries. At the time, Yahoo’s lawyer expressed his hope that “other countries [wouldn’t] take the same route.”
Fast forward 18 years and today’s Internet is going through an intense phase of regulation with similar effects to those of the Yahoo case. Almost every country in the world is currently in the business of “regulating the Internet.” A clarification is important at this stage. “Internet regulation” is a somewhat loaded and misguided phrase. In reality, what most state actors seek Continue reading
PQ 157: How Cisco Built A Carrier-Grade Network OS (Sponsored)
On today's sponsored Priority Queue podcast we take a deep dive into Cisco's IOS-XR network OS to learn what it takes to build a carrier-grade NOS, including its microservices architecture, multiple levels of abstraction, and how it captures and shares state data.
The post PQ 157: How Cisco Built A Carrier-Grade Network OS (Sponsored) appeared first on Packet Pushers.
Juniper Nxtwork – Hackathon 2018
This year while at Juniper Nxtwork 2018 I had the privilege of attending the pre-event Hackathon on Tuesday, October 9th, 2018. …
The post Juniper Nxtwork – Hackathon 2018 appeared first on Fryguy's Blog.
Warum ich Cloudflare helfe in Deutschland, Österreich und der Schweiz zu wachsen


Warum Cloudflare ?
Ich übernehme bei Cloudflare die Verantwortung für die DACH Region (Deutschland, Austria & Switzerland-CH), um das Geschäft von Cloudflare in Deutschland, Österreich und der Schweiz zu erweitern. Die einzigartige Mission von Cloudflare ein besseres Internet zu gestalten, ist der Grund, warum ich diese Verantwortung übernommen habe. Heute kann ich es kaum erwarten dieses Ziel zu erreichen.
Cloudflare trägt dazu bei 10 Millionen Domains schneller und sicherer zu machen indem die Kunden gegen eine große Anzahl von Online-Angriffen geschützt werden und gleichzeitig die Verfügbarkeit garantiert wird. Dies ist die Grundlage für jedes erfolgreiche Geschäft.
Sicherheit, Datenschutz und Geschwindigkeit sind Schlüsselfunktionen für fast jedes Unternehmen: von sehr großen traditionellen bis hin zu reinen Online-Unternehmen oder Einzelpersonen, die ihre eigene persönliche Marke aufbauen. Dazu könnte ich endlos weitere Beispiele nennen und je mehr ich über Cloudflare’s Mission erfahre desto mehr bin ich begeistert.
Eine von Cloudflare’s größten Stärken ist das globale Netzwerk.
Cloudflare verfügt bereits über Rechenzentren in sieben Städten der DACH Region (weitere folgen), um sicherzustellen, dass das Internet für die Nutzer in der Region schnell, sicher und zuverlässig ist.
Ich bin stolz, das erste Büro in Deutschland eröffnen zu dürfen. Gleichzeitig habe ich Continue reading
Why I’m helping Cloudflare grow in Germany, Austria, and Switzerland


Why Cloudflare?
I am incredibly excited to announce that I’m joining Cloudflare as the Head of DACH to help to expand Cloudflare’s demand in Germany, Austria, and Switzerland. Having been in the technology industry for many years, Cloudflare’s mission to help build a better Internet was frankly the reason I joined, and I’m now very eager to start working towards this.
I quickly learned how Cloudflare helps to speed up and secure over 10 million Internet properties by protecting these customers from a wide range of online attacks and providing the reliability needed to run strong businesses. Security, privacy, and performance are key drivers for almost every business: from large traditional enterprises to purely online businesses and even individuals building their own personal brand. I could go on and on. The more I learned, the more excited I became.
One of Cloudflare’s major strengths is its global network. Cloudflare already has data centers in seven cities in the DACH region (with more to come) helping to ensure the Internet is fast, safe, and reliable for users online in the region. So while I get the honor of opening our first office in Germany (in Munich), I loved that Cloudflare had Continue reading
What to Look for in a Network Monitoring Application
Keeping tabs on network operations and performance is a 24x7 job. The right monitoring application makes the task easier.
Leaf-and-Spine Fabric Myths (Part 3)
Evil CCIE concluded his long list of leaf-and-spine fabric myths (more in part 1 and part 2) with a layer-2 fabric myth:
Layer 2 Fabrics can't be extended beyond 2 Spine switches. I had a long argument with a $vendor guys on this. They don't even count SPB as Layer 2 fabric and so forth.
The root cause of this myth is the lack of understanding of what layer-2, layer-3, bridging and routing means. You might want to revisit a few of my very old blog posts before moving on: part 1, part 2, what is switching, layer-3 switches and routers.
Read more ...