Famous Last Words: I’m Too Stupid for That
Some networking vendors realized that one way to gain mindshare is to make their network operating systems available as free-to-download containers or virtual machines. That’s the right way to go; I love their efforts and point out who went down that path whenever possible1 (as well as others like Cisco who try to make our lives miserable).
However, those virtual machines better work out of the box, or you’ll get frustrated engineers who will give up and never touch your warez again, or as someone said in a LinkedIn comment to my blog post describing how Junos vPTX consistently rejects its DHCP-assigned IP address: “If I had encountered an issue like this before seeing Ivan’s post, I would have definitely concluded that I am doing it wrong.”2
Famous Last Words: I’m Too Stupid for That
Some networking vendors realized that one way to gain mindshare is to make their network operating systems available as free-to-download containers or virtual machines. That’s the right way to go; I love their efforts and point out who went down that path whenever possible1 (as well as others like Cisco who try to make our lives miserable).
However, those virtual machines better work out of the box, or you’ll get frustrated engineers who will give up and never touch your warez again, or as someone said in a LinkedIn comment to my blog post describing how Junos vPTX consistently rejects its DHCP-assigned IP address: “If I had encountered an issue like this before seeing Ivan’s post, I would have definitely concluded that I am doing it wrong.”2
Worth Reading: Cisco vPC in VXLAN/EVPN Networks
Daniel Dib started writing a series of blog posts describing Cisco vPC in VXLAN/EVPN Networks. The first one covers the anycast gateway, the second one the vPC configuration.
Let’s hope he will keep them coming and link them together so it will be easy to find the whole series after stumbling on one of the posts ;)
Worth Reading: Cisco vPC in VXLAN/EVPN Networks
Daniel Dib started writing a series of blog posts describing Cisco vPC in VXLAN/EVPN Networks. The first one covers the anycast VTEP, the second one the vPC configuration.
Let’s hope he will keep them coming and link them together so it will be easy to find the whole series after stumbling on one of the posts ;)
HN732: Juniper’s PTX Platforms: 800GE and Double-Density 400GE for DC and WAN (Sponsored)
The future has arrived: 800 gig Ethernet is here. Amit Bhardwaj and Dmitry Shokarev from today’s sponsor, Juniper Networks, join the show to tell us all about Juniper’s 800 gig Ethernet and what we need to know as engineers: use cases, transition plans, fiber and power needs (a lot less than you’d think). We also... Read more »Public Videos: Network Connectivity and Graph Theory

When I decided to sunset the ipSpace.net subscription, I asked Rachel Traylor whether I could make the content of her webinars public. She graciously agreed, and the first results are already here: you can download approximately half of the videos from the Network Connectivity and Graph Theory without a valid ipSpace.net account. Enjoy!
IPB150: IPv6 Basics: ICMPv6
As part of our ongoing series on IPv6 basics, today we cover the differences you should be aware of between ICMPv4 and ICMPv6. Internet Control Message Protocol (ICMP) is the protocol that lets you test reachability: Pings, echoes, TCP connections, etc. We explain what you need to know and why you need to know it,... Read more »Hedge 224: Is Open Source a Market Failure?

Is Open Source Software (OSS) a market failure? What does OSS add to the market that cannot be accomplished in other ways? What happened to the F (Free)? Join us for this roundtable episode of the Hedge.
Configuration of BGP afi/safi L2VPN EVPN and NVE Tunnel Interface
Overlay Network Routing: MP-BGP L2VPN/EVPN
EVPN Fabric Data Plane – MP-BGP
Instead of being a protocol, EVPN is a solution that utilizes the Multi-Protocol Border Gateway Protocol (MP-BGP) for its control plane in an overlay network. Besides, EVPN employs Virtual eXtensible Local Area Network (VXLAN) encapsulation for the data plane of the overlay network.
Multi-Protocol BGP (MP-BGP) is an extension of BGP-4 that allows BGP speakers to encode Network Layer Reachability Information (NLRI) of various address types, including IPv4/6, VPNv4, and MAC addresses, into BGP Update messages. The MP_REACH_NLRI path attribute (PA) carried within MP-BGP update messages includes Address Family Identifier (AFI) and Subsequent Address Family Identifier (SAFI) attributes. The combination of AFI and SAFI determines the semantics of the carried Network Layer Reachability Information (NLRI). For example, AFI-25 (L2VPN) with SAFI-70 (EVPN) defines an MP-BGP-based L2VPN solution, which extends a broadcast domain in a multipoint manner over a routed IPv4 infrastructure using an Ethernet VPN (EVPN) solution.
BGP EVPN Route Types (BGP RT) carried in BGP update messages describe the advertised EVPN NLRIs (Network Layer Reachability Information) type. Besides publishing IP Prefix information with IP Prefix Route (EVPN RT 5), BGP EVPN uses MAC Advertisement Route (EVPN RT 2) Continue reading
BGP Labs: EBGP Sessions over IPv6 LLA Interfaces
If you insist on building your network with EBGP as a better IGP, make sure your implementation supports running IPv4 and IPv6 address families over EBGP sessions established between IPv6 link-local addresses (the functionality lovingly called unnumbered EBGP sessions).
Want to practice that neat trick? Check out the EBGP Sessions over IPv6 LLA Interfaces lab exercise.
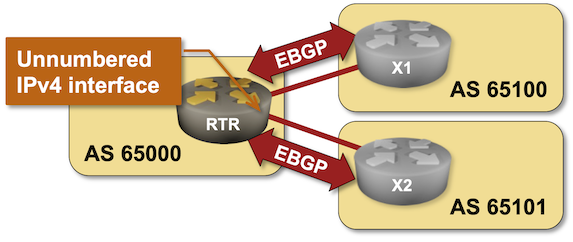
BGP Labs: EBGP Sessions over IPv6 LLA Interfaces
If you insist on building your network with EBGP as a better IGP, make sure your implementation supports running IPv4 and IPv6 address families over EBGP sessions established between IPv6 link-local addresses (the functionality lovingly called unnumbered EBGP sessions).
Want to practice that neat trick? Check out the EBGP Sessions over IPv6 LLA Interfaces lab exercise.

NAN062: The Team Behind Nautobot (Part 1)
Today we chat with the maintainers of Nautobot, the open source network source of truth and network automation platform. Jason Edelman, Ken Celenza, John Anderson explain how their day jobs at professional services company, Network to Code, informs their work on Nautobot. They walk us through Nautobot’s core, out-of-the-box capabilities as well as the extensibility... Read more »Fat Pipe Transition Notification – May 2024
Hey, everyone. Ethan here with a behind-the-scenes administrative request. Several thousand of you subscribe to the Packet Pushers’ Fat Pipe. In the Fat Pipe, we’ve been stuffing every single podcast we produce. The problem is that we produce way too many shows–one almost every weekday–for the average podcast client to absorb them all. We can... Read more »3 observability best practices for improved security in cloud-native applications
Why is observability important for better security?
Observability, especially in the context of cloud-native applications, is important for several reasons. First and foremost is security. By design, cloud-native applications rely on multiple, dynamic, distributed, and highly ephemeral components or microservices, with each microservice operating and scaling independently to deliver the application functionality. In this type of microservices-based architecture, observability and metrics provide security insights that enable teams to identify and mitigate zero-day threats through the detection of anomalies in microservices metrics, such as traffic flow, process calls, syscalls, and more. Using machine learning (ML) and heuristic analysis, security teams can identify abnormal behavior and issue alerts.
Observability also enables security teams to visualize the blast radius in the event of a breach. Using this information, teams can apply mitigating controls, such as security policy updates, to isolate the breached microservice and thereby limit exposure.
And finally, observability helps DevOps teams maintain the quality of service by identifying service failure and performance hotspots, and conducting a detailed investigation with capabilities such as packet capture and distributed tracing.
Observability challenges
DevOps and SRE teams today are being overwhelmed by an enormous amount of data from multiple, disparate systems that monitor infrastructure and Continue reading
Managing Multiple Python Versions with pyenv

In my Python journey, I've always stuck to just one version of Python at a time. I happily used Python 3.9 for quite a while, then switched to Python 3.10 without any issues. Everything was perfect until recently when I tried installing a Python application using pip, but no matter what I did, the installation kept failing. I couldn't fix the issue even after hours of Googling.
That's when I finally decided to check the documentation (which I should have done from the start), and there it was, this application requires a minimum Python version of 3.8 and was only tested on versions 3.8 and 3.9. That made me think, maybe I should have installed it using Python 3.9, but how? I'm no expert in Linux or Unix systems, and I worried that reinstalling Python 3.9 could mess up other projects I'd built on 3.10.
So, I started exploring how to manage multiple Python versions on the same machine, and that's when I stumbled upon a tool called 'pyenv'. This seemed like the perfect solution to my problem, so I decided to learn more about it.
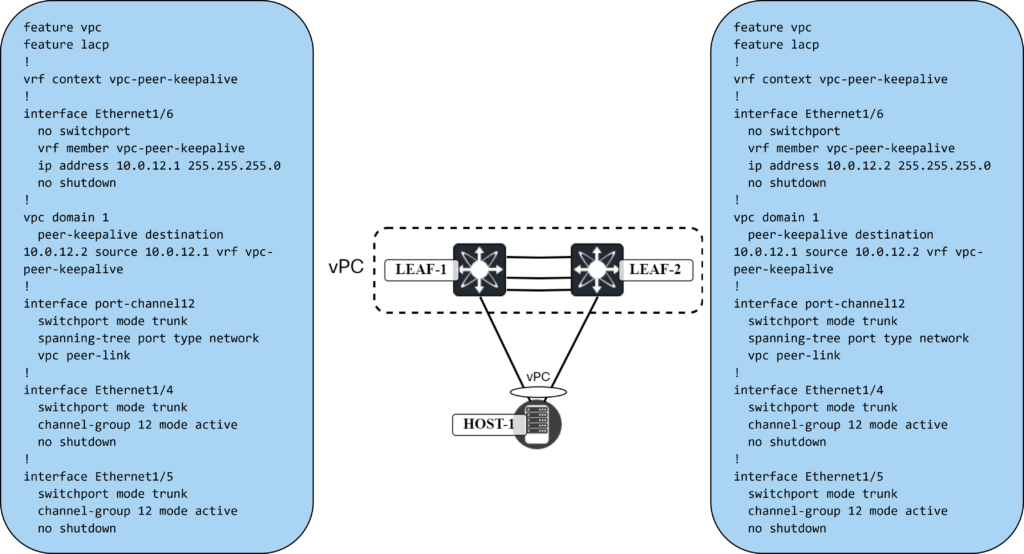
Cisco vPC in VXLAN/EVPN Network – Part 2 – Configuring vPC
When building leaf and spine networks, leafs connect to spines, but leafs don’t connect to leafs, and spines don’t connect to spines. There are exceptions to this and vPC is one of those exceptions. The leafs that are going to be part of the same vPC need to connect to each other. There are two ways of achieving this:
- Physical interfaces.
- Fabric peering.
We will first use physical interfaces and then later remove that and use fabric peering. Now, my lab is virtual so take physical with a grain of salt, but they will be dedicated interfaces. The following will be required to configure vPC:
- Enable vPC.
- Enable LACP.
- Create vPC domain.
- Create a VRF for the vPC peer keepalive.
- Configure the interface for vPC peer keepalive.
- Configure the vPC peer keepalive.
- Configure the vPC peer link interfaces.
- Configure the vPC peer link.
This is shown below:
The vPC is now up:
Leaf1# show vpc
Legend:
(*) - local vPC is down, forwarding via vPC peer-link
vPC domain id : 1
Peer status : peer adjacency formed ok
vPC keep-alive status : peer is alive
Configuration consistency status : success
Per-vlan consistency status : success
Type-2 consistency status : success
Continue reading
Testing Pi-hole Development Version 6
Pi-hole, the network-wide ad-blocking solution, has recently undergone significant updates, introducing a range of new […]
The post Testing Pi-hole Development Version 6 first appeared on Brezular's Blog.
