Tech Bytes: Using ZTNA for VPN Consolidation, Protecting Dev Access with SSE (Sponsored)
Zero Trust Network Access, or ZTNA, is a core element of a Security Service Edge because it enables secure remote access to on-prem and cloud-based applications. On today’s episode, sponsored by HPE Aruba Networking, we dig into ZTNA from HPE’s perspective and hear customer stories on how it’s being used for third-party access, VPN consolidation,... Read more »NB476: IBM Buys HashiCorp; Running Data Centers With Vegetable Oil?
Take a Network Break! We welcome guest commentator Kyler Middleton of Day Two Cloud to discuss the IBM/HashiCorp deal, then pivot to new Wi-Fi 7 APs from HPE Aruba Networking, and discuss why a data center builder in Ireland is constructing a power generation plant alongside the generator–and powering it partly with vegetable oil. Noncompete... Read more »Q1 2024 Internet disruption summary
This post is also available in 日本語, 한국어, Deutsch, Français, Español.
Cloudflare’s network spans more than 310 cities in over 120 countries, where we interconnect with over 13,000 network providers in order to provide a broad range of services to millions of customers. The breadth of both our network and our customer base provides us with a unique perspective on Internet resilience, enabling us to observe the impact of Internet disruptions. Thanks to recently released Cloudflare Radar functionality, this quarter we have started to explore the impact from a routing perspective, as well as a traffic perspective, at both a network and location level.
The first quarter of 2024 kicked off with quite a few Internet disruptions. Damage to both terrestrial and submarine cables caused problems in a number of locations, while military action related to ongoing geopolitical conflicts impacted connectivity in other areas. Governments in several African countries, as well as Pakistan, ordered Internet shutdowns, focusing heavily on mobile connectivity. Malicious actors known as Anonymous Sudan claimed responsibility for cyberattacks that disrupted Internet connectivity in Israel and Bahrain. Maintenance and power outages forced users offline, resulting in observed drops in traffic. And in Continue reading
netlab: Global and Node VRFs
When designing the netlab VRF configuration module, I tried to make it as flexible as possible while using the minimum number of awkward nerd knobs. As is often the case1, the results could be hard to grasp, so let’s walk through the various scenarios of using global and node VRFs.
netlab allows you to define a VRF in the lab topology vrfs dictionary (global VRF) or in a node vrfs dictionary (node VRF). In most cases, you’d define a few global VRFs and move on.
netlab: Global and Node VRFs
When designing the netlab VRF configuration module, I tried to make it as flexible as possible while using the minimum number of awkward nerd knobs. As is often the case1, the results could be hard to grasp, so let’s walk through the various scenarios of using global and node VRFs.
netlab allows you to define a VRF in the lab topology vrfs dictionary (global VRF) or in a node vrfs dictionary (node VRF). In most cases, you’d define a few global VRFs and move on.
Cisco vPC in VXLAN/EVPN Network – Part 1 – Anycast VTEP
Many vendors offer MLAG features, that is, the ability to form a PortChannel (some vendors call it trunk or bond) towards two separate devices. In this post, I will cover the following:
- Briefly describe vPC in a traditional network.
- Describe vPC in a VXLAN/EVPN network.
- Configure leaf switches to support vPC.
- Setup of Ubuntu Linux host to bond two interfaces and use LACP.
- Verification of the setup.
Traditional vPC
On Cisco Nexus switches, virtual Port Channel (vPC) has been a highly used feature for many years. It has been used towards other network devices such as firewalls, routers, and switches, but also towards hosts running hypervisors such as ESX.
As opposed to other technologies such as Virtual Switching System (VSS) or StackWise Virtual, it does not require the two switches to become one to provide the ability to do MLAG. Instead, the two devices appear as one in PDUs such as LACP, STP, and IGMP, by using a vPC system MAC address as the source MAC. With MLAG features, the two switches need to verify the other is alive and also synchronize state and perform consistency checking. This is done by connecting them with a vPC peer keepalive link, and Continue reading
Single-AS EVPN Fabric with OSPF Underlay: Underlay Network Multicast Routing: Any-Source Multicast – ASM
Underlay Network Multicast Routing: PIM-SM
In a traditional Layer 2 network, switches forward Intra-VLAN data traffic based on the destination MAC address of Ethernet frames. Therefore, hosts within the same VLAN must resolve each other's MAC-IP address bindings using Address Resolution Protocol (ARP). When a host wants to open a new IP connection with a device in the same subnet and the destination MAC address is unknown, the connection initiator generates an ARP Request message. In the message, the sender provides its own MAC-IP binding information and queries the MAC address of the owner of the target IP. The ARP Request messages are Layer 2 Broadcast messages with the destination MAC address FF:FF:FF:FF:FF:FF.
EVPN Fabric is a routed network and requires a solution for Layer 2 Broadcast messages. We can select either BGP EVPN-based Ingress-Replication (IR) solution or enable Multicast routing in Underlay network. This chapter introduces the latter model. As in previous Unicast Routing section, we follow the Multicast deployment workflow of Nexus Dashboard Fabric Controller (NDFC) graphical user interface.
Figure 2-4 depicts the components needed to deploy Multicast service in the Underlay network. The default option for selecting “RP mode” is ASM (Any-Source Multicast). ASM is Continue reading
Hedge 223: The Political Side of Standards with Geoff Huston
Listen in as Geoff Huston, Tom, and Russ discuss how the IETF, governments, and political movements interact when creating standards and guiding the future of the Internet.
FreeIX – Remote
Introduction

Tier1 and aspiring Tier2 providers interconnect only in large metropolitan areas, due to commercial incentives and politics. They won’t often peer with smaller providers, because why peer with a potential customer? Due to this, it’s entirely likely that traffic between two parties in Thessaloniki is sent to Frankfurt or Milan and back.
One possible antidote to this is to connect to a local Internet Exchange point. Not all ISPs have access to large metropolitan datacenters where larger internet exchanges have a point of presence, and it doesn’t help that the datacenter operator is happy to charge a substantial amount of money each month, just for the privilege of having a passive fiber cross connect to the exchange. Many Internet Exchanges these days ask for per-month port costs and meter the traffic with policers and rate limiters, such that the total cost of peering starts to exceed what one might pay for transit, especially at low volumes, which further exacerbates the problem. Bah.
This is an unfortunate market effect (the race to the bottom), where transit providers are continuously lowering their prices to compete. And while transit providers can make up to some extent due to economies of scale, at Continue reading
Worth Reading: Comparing GNS3, containerlab, and netlab
You probably know I hate posting links to walled gardens or sites that try really hard to make you sign up. Sometimes, I have to make an exception: Roman Pomazanov wrote a great (and humorous) article comparing how easy it is to set up simple labs with GNS3, containerlab, and netlab.
Worth Reading: Comparing GNS3, containerlab, and netlab
You probably know I hate posting links to walled gardens or sites that try really hard to make you sign up. Sometimes, I have to make an exception: Roman Pomazanov wrote a great (and humorous) article comparing how easy it is to set up simple labs with GNS3, containerlab, and netlab.
Rust is faster than C, even before I added SIMD
I found some old C code of mine from around 2001 or so. I vaguely remember trying to make it as optimized as possible. Sure, I was still a teenager, so it’s not state of the art. But it’s not half bad. I vaguely suspect I could do better with better optimization for cache lines, but it’s pretty good.
On my current laptop it does about 12 million passwords per second, single threaded.
Because I’m learning Rust, I decided to port it, and see how fast rust is.
Imagine my surprise when even the first version in Rust was faster. (Yes, I rebuilt the old C code with a modern compiler and its optimizations)
The first Rust version was about 13 million passwords per second.
Why is that? It’s basically the same as the C code. Maybe Rust can take advantage of knowing there’s no pointer aliasing (the reason usually quoted for why Fortran can be faster than C)? Or maybe the memory layout just happened to become more cache friendly?
In any case, I think we can already say that Rust is at least as fast as C.
The code is on github.
SIMD (with Rust)
I realized, of Continue reading
On Open Source and Volunteering

I saw a recent post on LinkedIn from Alex Henthorn-Iwane that gave me pause. He was talking about how nearly 2/3rds of Github projects are maintained by one or two people. He also quoted some statistics around how projects are maintained by volunteers and unpaid members as opposed to more institutional support from people getting paid to do the work. It made me reflect on my own volunteering journey and how the parallels between open source and other organizations aren’t so different after all.
A Hour A Week
Most of my readers know that one of my passion projects outside of Tech Field Day and this humble blog is the involvement of my children in Scouting. I spend a lot of my free time volunteering as a leader and organizer for various groups. I get to touch grass quite often. At least I do when I’m not stuck in meetings or approving paperwork.
One of the things that struck me in Alex’s post was how he talked about the lack of incoming talent to help with projects as older maintainers are aging out. We face a similar problem in scouting. Rather than our volunteers getting too old to do the Continue reading
HN731: GraphQL: Open Source Query Language for APIs
What if instead of sending multiple queries out to APIs and getting disparate data back, you could just send a single query and receive a single answer. That’s exactly what GraphQL does for you. Rick Donato joins the show today to teach us about GraphQL and how it can help us on the path to... Read more »Enhancing Kubernetes network security with microsegmentation: A strategic approach
Microsegmentation represents a transformative approach to enhancing network security within Kubernetes environments. This technique divides networks into smaller, isolated segments, allowing for granular control over traffic flow and significantly bolstering security posture. At its core, microsegmentation leverages Kubernetes network policies to isolate workloads, applications, namespaces, and entire clusters, tailoring security measures to specific organizational needs and compliance requirements.
The essence of microsegmentation strategies
Scalability and flexibility
The fundamental advantage of microsegmentation through network policies lies in its scalability and flexibility. Kubernetes’ dynamic, label-based selection process facilitates the addition of new segments without compromising existing network infrastructure, enabling organizations to adapt to evolving security landscapes seamlessly.
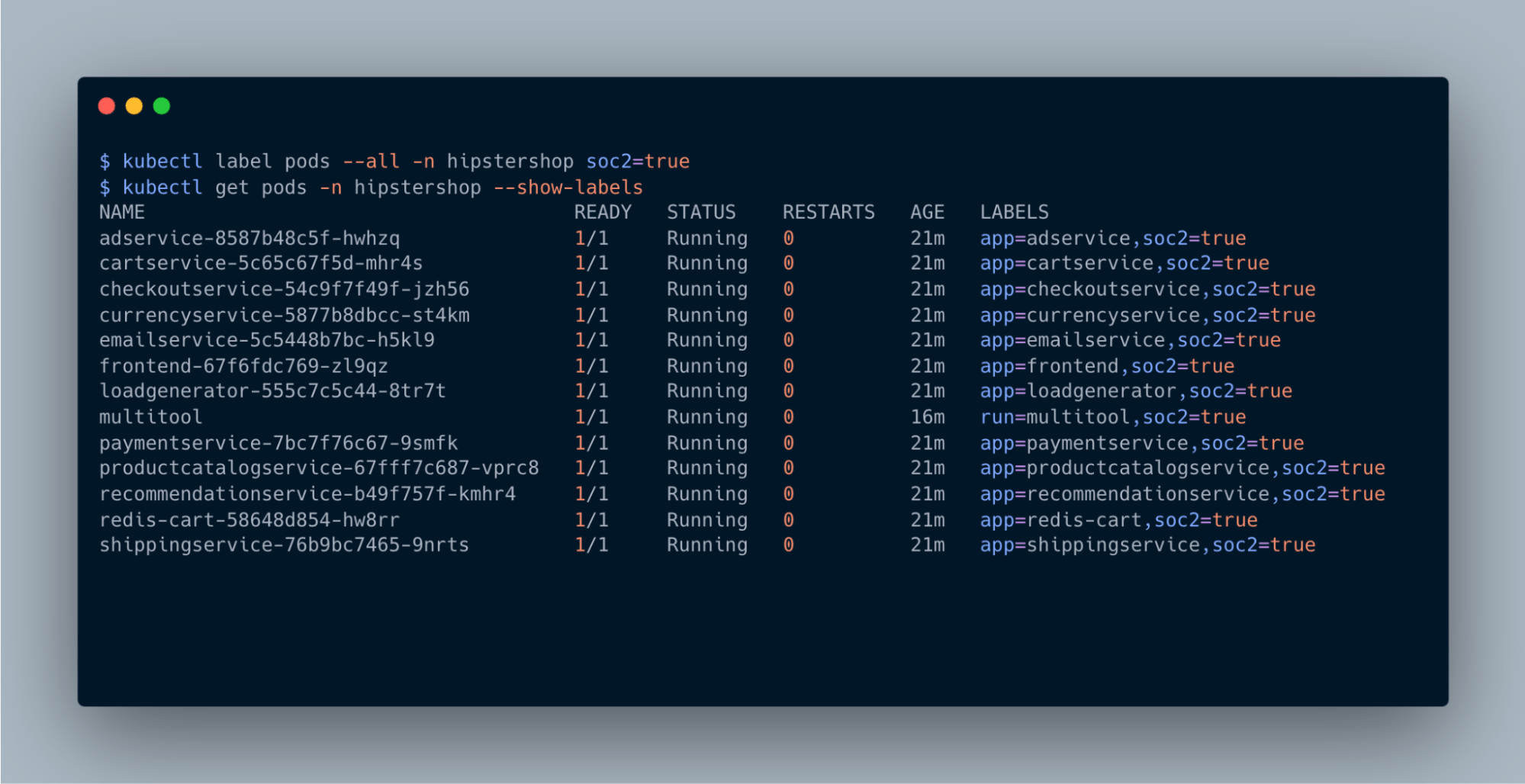
Prevent lateral movement of threats
Workload isolation, a critical component of microsegmentation, emphasizes the importance of securing individual microservices within a namespace or tenant by allowing only required and approved communication. This minimizes the attack surface and prevents unauthorized lateral movement.
Namespace and tenant isolation
Namespace isolation further enhances security by segregating applications into unique namespaces, ensuring operational independence and reducing the impact of potential security breaches. Similarly, tenant isolation addresses the needs of multi-tenant environments by securing shared Kubernetes infrastructure, thus protecting tenants from each other Continue reading
KU054: OpenTelemetry: Open Source Observability
Observability is foundational to application and infrastructure performance. That’s why it’s fitting that OpenTelemetry is the second most active project in the CNCF after Kubernetes. Today CNCF ambassador Dotan Horovits tells us about the project: OpenTelemetry is a uniform, vendor-agnostic observability framework for generating and collecting telemetry data across both infrastructure and application, across different... Read more »Understand Enterprise Connectivity by Going Directly to the Source
Discover the benefits of scalable backbone and network services for application and cloud providers.Single-AS EVPN Fabric with OSPF Underlay: Underlay Network Unicast Routing
Introduction
Image 2-1 illustrates the components essential for designing a Single-AS, Multicast-enabled OSPF Underlay EVPN Fabric. These components need to be established before constructing the EVPN fabric. I've grouped them into five categories based on their function.
- General: Defines the IP addressing scheme for Spine-Leaf Inter-Switch links, set the BGP AS number and number of BGP Route-Reflectors, and set the MAC address for the Anycast gateway for client-side VLAN routing interfaces.
- Replication: Specifies the replication mode for Broadcast, Unknown Unicast, and Multicast (BUM) traffic generated by Tenant Systems. The options are Ingress-Replication and Multicast (ASM or BiDir options).
- vPC: Describes vPC multihoming settings such as vPC Peer Link VLAN ID and Port-Channel ID, vPC Auto-recovery and Delay Restore timers, and define vPC Peer Keepalive interface.
- Protocol: Defines the numbering schema for Loopback interfaces, set the OSPF Area identifier, and OSPF process name.
- Resources: Reserves IP address ranges for Loopback interfaces defined in the Protocols category and for the Rendezvous Point specified in the Replication category. Besides, in this section, we reserve Layer 2 and Layer 3 VXLAN and VLAN ranges for overlay network segments.
The model presented in Figure 2-1 outlines the steps for configuring an EVPN fabric using the Continue reading
Repost: Think About the 99% of the Users
Daniel left a very relevant comment on my Data Center Fabric Designs: Size Matters blog post, describing how everyone rushes to sell the newest gizmos and technologies to the unsuspecting (and sometimes too-awed) users1:
Absolutely right. I’m working at an MSP, and we do a lot of project work for enterprises with between 500 and 2000 people. That means the IT department is not that big; it’s usually just a cost center for them.