Enhancing Kubernetes network security with microsegmentation: A strategic approach
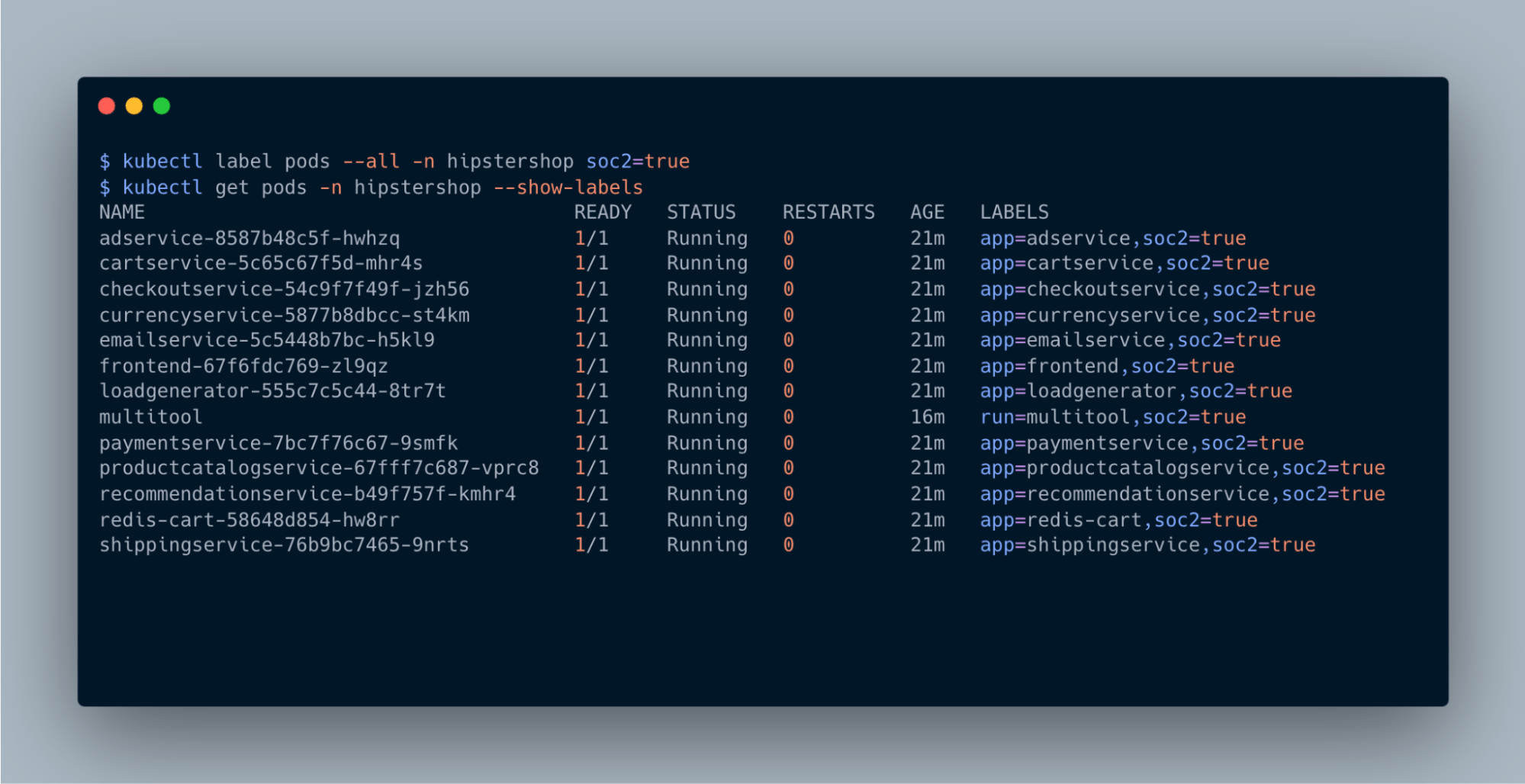
Microsegmentation represents a transformative approach to enhancing network security within Kubernetes environments. This technique divides networks into smaller, isolated segments, allowing for granular control over traffic flow and significantly bolstering security posture. At its core, microsegmentation leverages Kubernetes network policies to isolate workloads, applications, namespaces, and entire clusters, tailoring security measures to specific organizational needs and compliance requirements.
The essence of microsegmentation strategies
Scalability and flexibility
The fundamental advantage of microsegmentation through network policies lies in its scalability and flexibility. Kubernetes’ dynamic, label-based selection process facilitates the addition of new segments without compromising existing network infrastructure, enabling organizations to adapt to evolving security landscapes seamlessly.
Prevent lateral movement of threats
Workload isolation, a critical component of microsegmentation, emphasizes the importance of securing individual microservices within a namespace or tenant by allowing only required and approved communication. This minimizes the attack surface and prevents unauthorized lateral movement.
Namespace and tenant isolation
Namespace isolation further enhances security by segregating applications into unique namespaces, ensuring operational independence and reducing the impact of potential security breaches. Similarly, tenant isolation addresses the needs of multi-tenant environments by securing shared Kubernetes infrastructure, thus protecting tenants from each other Continue reading
KU054: OpenTelemetry: Open Source Observability
Observability is foundational to application and infrastructure performance. That’s why it’s fitting that OpenTelemetry is the second most active project in the CNCF after Kubernetes. Today CNCF ambassador Dotan Horovits tells us about the project: OpenTelemetry is a uniform, vendor-agnostic observability framework for generating and collecting telemetry data across both infrastructure and application, across different... Read more »Understand Enterprise Connectivity by Going Directly to the Source
Discover the benefits of scalable backbone and network services for application and cloud providers.Single-AS EVPN Fabric with OSPF Underlay: Underlay Network Unicast Routing
Introduction
Image 2-1 illustrates the components essential for designing a Single-AS, Multicast-enabled OSPF Underlay EVPN Fabric. These components need to be established before constructing the EVPN fabric. I've grouped them into five categories based on their function.
- General: Defines the IP addressing scheme for Spine-Leaf Inter-Switch links, set the BGP AS number and number of BGP Route-Reflectors, and set the MAC address for the Anycast gateway for client-side VLAN routing interfaces.
- Replication: Specifies the replication mode for Broadcast, Unknown Unicast, and Multicast (BUM) traffic generated by Tenant Systems. The options are Ingress-Replication and Multicast (ASM or BiDir options).
- vPC: Describes vPC multihoming settings such as vPC Peer Link VLAN ID and Port-Channel ID, vPC Auto-recovery and Delay Restore timers, and define vPC Peer Keepalive interface.
- Protocol: Defines the numbering schema for Loopback interfaces, set the OSPF Area identifier, and OSPF process name.
- Resources: Reserves IP address ranges for Loopback interfaces defined in the Protocols category and for the Rendezvous Point specified in the Replication category. Besides, in this section, we reserve Layer 2 and Layer 3 VXLAN and VLAN ranges for overlay network segments.
The model presented in Figure 2-1 outlines the steps for configuring an EVPN fabric using the Continue reading
Repost: Think About the 99% of the Users
Daniel left a very relevant comment on my Data Center Fabric Designs: Size Matters blog post, describing how everyone rushes to sell the newest gizmos and technologies to the unsuspecting (and sometimes too-awed) users1:
Absolutely right. I’m working at an MSP, and we do a lot of project work for enterprises with between 500 and 2000 people. That means the IT department is not that big; it’s usually just a cost center for them.
Repost: Think About the 99% of the Users
Daniel left a very relevant comment on my Data Center Fabric Designs: Size Matters blog post, describing how everyone rushes to sell the newest gizmos and technologies to the unsuspecting (and sometimes too-awed) users1:
Absolutely right. I’m working at an MSP, and we do a lot of project work for enterprises with between 500 and 2000 people. That means the IT department is not that big; it’s usually just a cost center for them.
IPv6 Prefix Lengths
These days its up to IPv6 Service providers to determine what IPv6 address prefix length they assign to each customer. This leads to the question: What lengths are commonly used for customer assignments? Let's see if we can answer it.Fixed Wireless Access Benefits Extend to Enterprises
Pending 6GHz spectrum availability, faster speeds, and private wireless access use drive FWA forward.NAN061: Transforming Network Telemetry Into Operational Insights With Kentik (Sponsored)
The expectations for application delivery are higher than ever before, the networks that support those applications are increasingly distributed, and visibility is essential for network operations and troubleshooting. On today’s sponsored episode, Kentik’s Phil Gervasi joins us to discuss how Kentik collects essential performance data to help you monitor and manage all the networks your... Read more »How to Get the Maximum Value Out of Network Automation
Network automation is gaining momentum. Here's how you can drive this powerful technology to its full potential.D2C241: Choose Your Own Adventure: Manager, Director, or IC
What makes for a good manager, director, and independent contributor (IC), and how do you figure out which is the best fit for you? Hazel Weakly has had a whirlwind tour of all three and is ready to share her insight into each. We talk about the skill set needed for each, and figuring out... Read more »Aruba Networking Unveils Wi-Fi 7 Access Points
The new HPE Aruba 730 series Wi-Fi 7 access points tout high performance, enhanced security, location tracking capabilities, and more.Stop the Network-Based Application Recognition Nonsense
One of my readers sent me an interesting update on the post-QUIC round of NBAR whack-a-mole (TL&DR: everything is better with Bluetooth AI):
So far, so good. However, whenever there’s a change, there’s an opportunity for marketing FUD, coming from the usual direction.
Stop the Network-Based Application Recognition Nonsense
One of my readers sent me an interesting update on the post-QUIC round of NBAR whack-a-mole (TL&DR: everything is better with Bluetooth AI):
So far, so good. However, whenever there’s a change, there’s an opportunity for marketing FUD, coming from the usual direction.
PP011: IoT Protocols: Detection and Protection
IoT devices are often like the tiny aliens in the locker in Men in Black: They’ve created a whole little world on your network without almost any humans knowing they exist. Today Troy Martin joins the show to teach us the basics of how to find and secure IoT devices on your network, specifically focusing... Read more »Good Things Happen when Network Engineers Internalize Spider-Man’s Mantra
NetOps teams, like Spider Man, have great powers and great responsibilities. Increasingly, they are adopting a Zero Trust approach to network operations to help fight their battles.HS070: Living on the Edge: The Present Future of Edge Architecture
Right now we’re in the first generation of edge architecture. We won’t even really know how to define it until we’re past it. Greg and Johna discuss the operational milieu in which the edge is forming: Vast numbers of IoT devices, increased remote computing capabilities, questions around cloud operational costs and efficiency, and vendors jostling... Read more »Lessons from building an automated SDK pipeline
In case you missed the announcement from Developer Week 2024, Cloudflare is now offering software development kits (SDKs) for Typescript, Go and Python. As a reminder, you can get started by installing the packages.
// Typescript
npm install cloudflare
// Go
go get -u github.com/cloudflare/cloudflare-go/v2
// Python
pip install --pre cloudflare
Instead of using a tool like curl or Postman to create a new zone in your account, you can use one of the SDKs in a language that you’re already comfortable with or that integrates directly into your existing codebase.
import Cloudflare from 'cloudflare';
const cloudflare = new Cloudflare({
apiToken: process.env['CLOUDFLARE_API_TOKEN']
});
const newZone = await cloudflare.zones.create({
account: { id: '023e105f4ecef8ad9ca31a8372d0c353' },
name: 'example.com',
type: 'full',
});
Since their inception, our SDKs have been manually maintained by one or more dedicated individuals. For every product addition or improvement, we needed to orchestrate a series of manually created pull requests to get those changes into customer hands. This, unfortunately, created an imbalance in the frequency and quality of changes that made it into the SDKs. Even though the product teams would drive some of these changes, not all languages were covered and the SDKs Continue reading
Wi-Fi 7: The Future of High Speed Wireless Networking is Here
Enterprises are under pressure to meet and exceed the challenges of rapidly increasing bandwidth requirements, including AR/VR (augmented reality/virtual reality) applications, streaming multimedia, IoT proliferation, video applications and high density deployments.
