NetQ is now a 2018 “New Product” Award Winner!

Cumulus NetQ is on FIRE!!
Just one year ago, Cumulus launched a new product that fundamentally changes the way organizations validate and troubleshoot not just their network, but the entire Linux ecosystem as a whole. The product was named NetQ (think Network Query). It provides deep insight on the connectivity of all network devices either now or in the past — including all switches, Linux hosts, inside Linux hosts (Containers, direct interaction with container orchestration tools like Kubernetes, VMs, Openstack environment) and any other devices running a Linux-based operating system connected to the network. No more manual box-by-box troubleshooting, no more wondering what happened last night, no more pulling cables to find where the issue was stemming from, no more finger pointing, no more human-led misconfigurations and no more frustration of not having sight past the edge of the network.
Instead, Cumulus NetQ, the agent-based technology that runs on anything Linux, changes all that. NetQ brings the efficiencies of web-scale to network operations with an algorithmic, preventive, centralized telemetry system built for the modern automated cloud network. NetQ aggregates and maintains data from across all Linux nodes in the data center in a time-series database, making the fabric-wide events, Continue reading
5 Serverless Ecosystem Players You Need to Know
 A recent survey from DigitalOcean found that half of developers said they did not have a strong understanding of serverless. Of those, a vast majority said they plan to research the topic within the next 12 months.
A recent survey from DigitalOcean found that half of developers said they did not have a strong understanding of serverless. Of those, a vast majority said they plan to research the topic within the next 12 months.
The Privacy Pickle

I recorded a fantastic episode of The Network Collective last night with some great friends from the industry. The topic was privacy. Originally I thought we were just going to discuss how NAT both was and wasn’t a form of privacy and how EUI-64 addressing wasn’t the end of days for people worried about being tracked. But as the show wore on, I realized a few things about privacy.
Booming In Peace
My mom is a Baby Boomer. We learn about them as a generation based on some of their characteristics, most notably their rejection of the values of their parents. One of things they hold most dear is their privacy. They grew up in a world where they could be private people. They weren’t living in a 1 or 2 room house with multiple siblings. They had the right of privacy. They could have a room all to themselves if they so chose.
Baby Boomers, like my mom, are intensely private adults. They marvel at the idea that targeted advertisements can work for them. When Amazon shows them an ad for something they just searched for they feel like it’s a form of dark magic. They also aren’t trusting Continue reading
Security Remains Top Public Cloud Concern, SDxCentral Report Says
 A new survey from SDxCentral found 71 percent or respondents use public clouds — up from just 43 percent three years ago.
A new survey from SDxCentral found 71 percent or respondents use public clouds — up from just 43 percent three years ago.
SDxCentral’s Weekly Roundup — July 6, 2018
 Apple snubs Intel's 5G modem for its next-gen iPhone; ZTE names a new CEO; Ericsson opens a 5G lab in Delhi, India; InterDigital shows a 5G control plane.
Apple snubs Intel's 5G modem for its next-gen iPhone; ZTE names a new CEO; Ericsson opens a 5G lab in Delhi, India; InterDigital shows a 5G control plane.
Short Take – Complexity Sells
In this Network Collective Short Take, Russ White examines why our industry continually introduces complexity even though most engineers recognize that simpler solutions are usually more robust and maintainable.
The post Short Take – Complexity Sells appeared first on Network Collective.
A Deeper Dive Into Public DNS Resolver Quad9
There are plenty of public DNS resolvers. The best known was Google Public DNS i.e. 8.8.8.8 and 8.8.4.4 for IPv4 and 2001:4860:4860::8888 and 2001:4860:4860::8844 for IPv6. But there are a few other options available now, each with different policies and technical features.
Two new Public DNS resolvers were recently launched. Quad9 (launched Nov 2017) and 1dot1dot1dot1 (launched Apr 2018). We have already covered 1.1.1.1 in detail in a recent blog. So let’s talk about Quad9 (9.9.9.9).
The Global Cyber Alliance (GCA), an organization founded by a partnership of law enforcement (New York County District Attorney and City of London Police) and research (Center for Internet Security – CIS) organizations focused on combating systemic cyber risk in real, measurable ways, partnered with IBM and Packet Clearing House (PCH) to launch a Global Public Recursive DNS Resolver Service. Quad9 protects users from accessing known malicious websites, leveraging threat intelligence from multiple industry leaders; it currently blocks up to two million threats per day.
A handy little infographic on the Quad9 website helps show how it works. Essentially, you set up Quad 9 as your Continue reading
Show 397: The Future Of Networking With Peter Wohlers
Our next installment of the Future Of Networking series brings Peter Wohlers to the podcast.
Way back in the early history of Packet Pushers, we received a presentation from Peter when he worked at Force10 as part of a Tech Field Day event. It was blunt, knowledgeable, cynical and nerd-funny.
Today Peter is VP of Engineering at a large CDN. I invited him to come on talk about the current and future state of the industry.
We discuss the effect of cloud computing on the networking industry and its impact on skills and careers, the early hype around SDN and where it stands today, how much skill you really need in coding, the rise of APIs in networking, and a passionate debate about whether different networks are actually all that unique.
Show Links:
TFD Bonus 3 Peter Wohlers of Force10 Presents to Tech Field Day San Jose 09/16/2010 – Packet Pushers
The post Show 397: The Future Of Networking With Peter Wohlers appeared first on Packet Pushers.
EdgeConnex Expands Denver Data Center Footprint, Strikes Megaport, Colt Deals
 The expansion is in the form of a new 115,000-square foot building that can support up to 21 megawatts of capacity.
The expansion is in the form of a new 115,000-square foot building that can support up to 21 megawatts of capacity.
Leading Uruguayan Students to Thrive in the Future Economy
Current researches show that children are exposed to both increased risks and increased opportunities when accessing the Internet and using apps and social media. The UNICEF’s “Children in a Digital World” 2017 report takes a comprehensive look at the different ways digital technology affects children. It is critical that children have necessary training in digital literacy to acquire the skills to minimize risks and to confidently navigate the web to maximize their opportunities. Evidence suggests that technology has benefits where positive human forces for learning are already in place.
The University of the Republic in partnership with the Internet Society Uruguay Chapter and the financial support of the Beyond the Net Funding Programme has taken significant steps to help children and teenagers to develop digital skills in a creative and innovative way in three of the nineteen segments in which Uruguay is politically divided, Paysandú, Rivera, and Salto. Their project Flor de Ceibo Conecta2 aims to train young people from disadvantaged communities using digital resources in creative and challenging learning classes to help them improve their everyday lives and expand their chances for a better future.
 María Julia Morales González, project manager and professor at the Department of Sociology and Continue reading
María Julia Morales González, project manager and professor at the Department of Sociology and Continue reading
How to drop 10 million packets per second
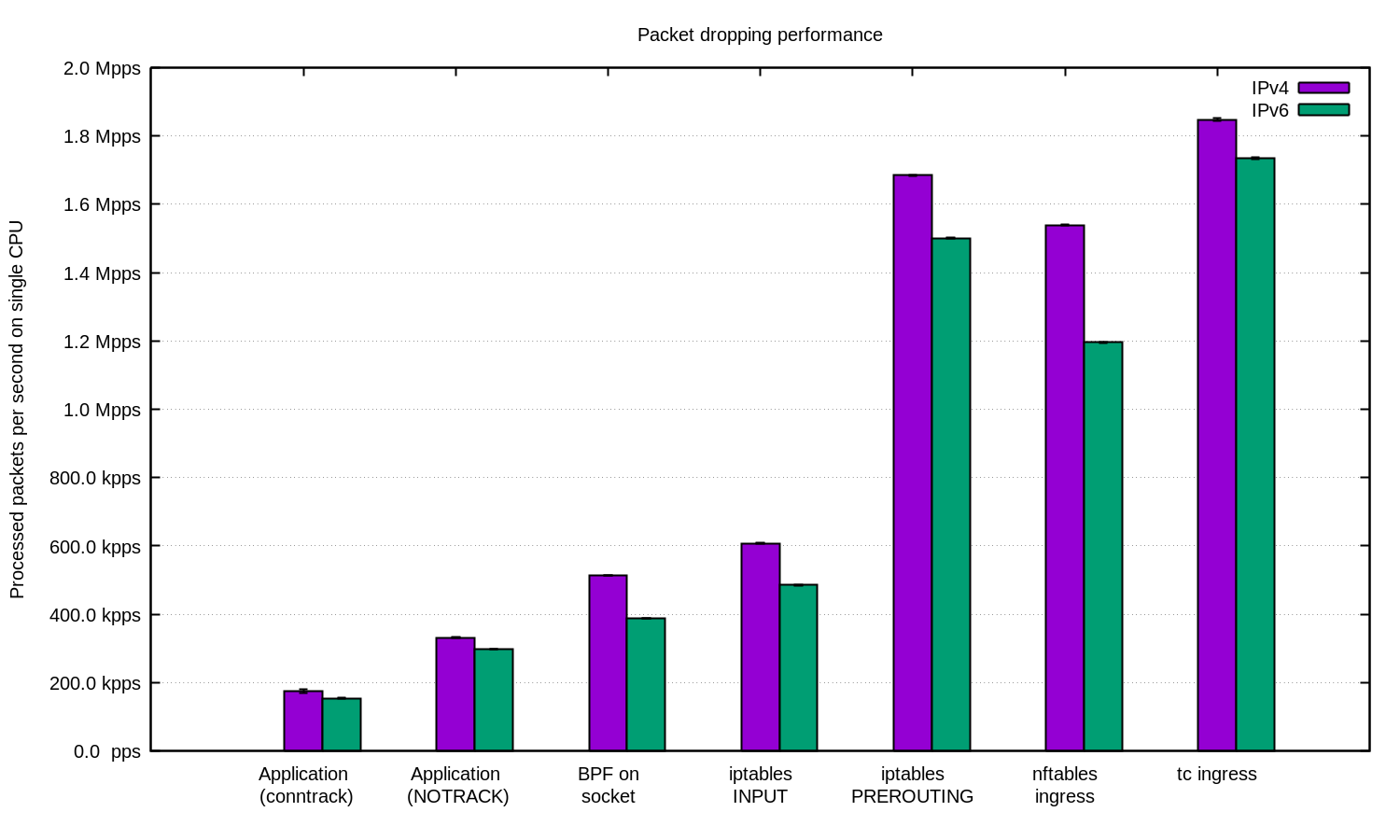
Internally our DDoS mitigation team is sometimes called "the packet droppers". When other teams build exciting products to do smart things with the traffic that passes through our network, we take joy in discovering novel ways of discarding it.

CC BY-SA 2.0 image by Brian Evans
Being able to quickly discard packets is very important to withstand DDoS attacks.
Dropping packets hitting our servers, as simple as it sounds, can be done on multiple layers. Each technique has its advantages and limitations. In this blog post we'll review all the techniques we tried thus far.
Test bench
To illustrate the relative performance of the methods we'll show some numbers. The benchmarks are synthetic, so take the numbers with a grain of salt. We'll use one of our Intel servers, with a 10Gbps network card. The hardware details aren't too important, since the tests are prepared to show the operating system, not hardware, limitations.
Our testing setup is prepared as follows:
-
We transmit a large number of tiny UDP packets, reaching 14Mpps (millions packets per second).
-
This traffic is directed towards a single CPU on a target server.
-
We measure the number of packets handled by the kernel on that Continue reading
초당 천만개의 패킷을 버리는 방법
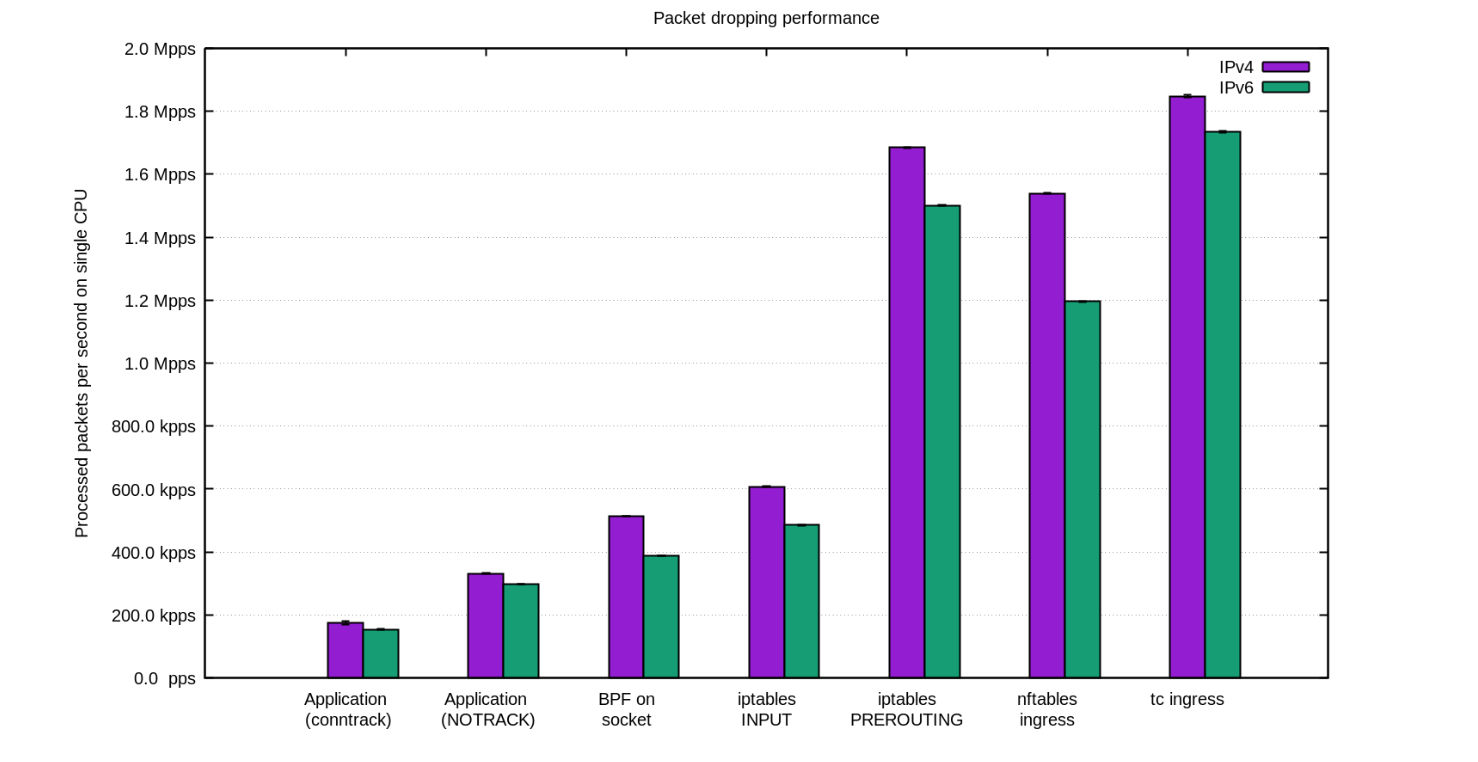
This is a Korean translation of a prior post by Marek Majkowski.
사내에서 DDoS 대응팀은 종종 "패킷 버리는 사람들"이라 불립니다. 다른 팀이 우리 네트워크를 통해 지나가는 트래픽으로 스마트한 일을 하며 신나할 때 우리는 그걸 버리는 여러가지 방법을 찾아가며 즐거워 합니다.

CC BY-SA 2.0 image by Brian Evans
DDoS 공격을 견뎌내기 위해서는 빠르게 패킷을 버릴 수 있는 능력이 매우 중요합니다.
쉽게 들리겠지만 서버에 도달한 패킷을 버리는 것은 여러 단계에서 가능합니다. 각 기법은 장점과 한계점이 있습니다. 이 블로그 글에서는 지금까지 시도해 본 기법들을 모두 정리해 보도록 하겠습니다.
테스트 벤치마크
각 기법의 상대적인 성능을 시각화하기 위해서 먼저 숫자를 볼 것입니다. 벤치마크는 합성 테스트이므로 실제 숫자와는 일부 차이가 있을 수 있습니다. 테스트를 위해서는 10Gbps 네트워크 카드가 달린 인텔 서버를 사용할 것입니다. 하드웨어가 아니라 운영체제의 한계를 보여주기 위한 테스트이므로 하드웨어의 상세 사항은 적지 않겠습니다.
테스트 설정은 다음과 같습니다:
- 작은 크기의 UDP 패킷을 14Mpps (Mpps = 초당 백만 패킷) 에 도달하도록 대량으로 전송
- 이 트래픽은 테스트 서버의 단일 CPU에 전달되도록 함
- 단일 CPU에서 커널에 의해 처리되는 패킷의 개수를 측정
테스트는 사용자 공간 어플리케이션의 속도나 패킷 처리 속도를 최대화하려는 것이 아니라 커널의 병목 지점을 알고자 하는 것입니다.
합성 트래픽은 conntrack에 최대한의 부하를 주도록 준비되었습니다 - 임의의 소스 IP와 포트 필드를 사용합니다. tcpdump는 다음과 같이 Continue reading
Redefining Automation in a Multi-Cloud World
Enterprises will need to break down traditional silos in order to achieve the agility benefits of a multi-cloud environment.
Openswitch OPX Installation on Linux

We have recently covered installation of Openswitch OPS on Linux. Since the version 2.0, Openswitch OPS has transformed into to a completely new project, called Openswitch OPX Base. Similar to its predecessor, OpenSwitch OPX Base system also provides an abstraction of hardware devices of network switch platforms in a Linux OS environment. However, original Yocto OS has been replaced by an unmodified Linux kernel based on Debian Jessie distribution.
We can install OPX Base on a virtual machine, similar to installing OpenSwitch on hardware platforms. A virtual machine (VM) uses the same software binaries as those executed on S6000-ON devices. The main difference is that the low-level device drivers for the SAI and SDI libraries are replaced with the packages that support hardware simulation, and interact with the hardware simulation infrastructure.
A host machine running Openswitch OPX VM might be Windows, or Mac OS X with at least 8GB of RAM and 100GB available disk space, and Virtual Box installed. The virtual machine needs to have one network interface configured for the Management interface (eth0). The network adapter eth0 corresponds to the first adapter attached to the VM, e101-001-0 to the second adapter and so on, and e101-00N-1 to Continue reading
Openswitch OPX Installation on Linux

We have recently covered installation of Openswitch OPS on Linux. Since the version 2.0, Openswitch OPS has transformed into to a completely new project, called Openswitch OPX Base. Similar to its predecessor, OpenSwitch OPX Base system also provides an abstraction of hardware devices of network switch platforms in a Linux OS environment. However, original Yocto OS has been replaced by an unmodified Linux kernel based on Debian Jessie distribution.
We can install OPX Base on a virtual machine, similar to installing OpenSwitch on hardware platforms. A virtual machine (VM) uses the same software binaries as those executed on S6000-ON devices. The main difference is that the low-level device drivers for the SAI and SDI libraries are replaced with the packages that support hardware simulation, and interact with the hardware simulation infrastructure.
A host machine running Openswitch OPX VM might be Windows, or Mac OS X with at least 8GB of RAM and 100GB available disk space, and Virtual Box installed. The virtual machine needs to have one network interface configured for the Management interface (eth0). The network adapter eth0 corresponds to the first adapter attached to the VM, e101-001-0 to the second adapter and so on, and e101-00N-1 to Continue reading
Openswitch OPX Appliances
OpenSwitch OPX Base is an innovative operating system for network systems. It uses an unmodified Linux kernel and standard distribution to take advantage of rich ecosystem, and also provide flexibility in customizing your system according to your network needs.
Note: Openswitch OPX images are customized with my after install script and they are ready for use in GNS3.
Openswitch OPX 2.3.2
https://drive.google.com/file/d/1Vdpjoz53R7Rx1HYi8KcEuRuNvQnMMn0f/view?usp=sharing
https://sourceforge.net/projects/gns-3/files/VirtualBox%20Appliances/OpenswitchOPX-2.3.2.zip
https://www.4shared.com/s/fQu2DUd9dca
Openswitch OPX Appliances
OpenSwitch OPX Base is an innovative operating system for network systems. It uses an unmodified Linux kernel and standard distribution to take advantage of rich ecosystem, and also provide flexibility in customizing your system according to your network needs.
Note: Openswitch OPX images are customized with my after install script and they are ready for use in GNS3.
Openswitch OPX 2.3.2
https://drive.google.com/file/d/1Vdpjoz53R7Rx1HYi8KcEuRuNvQnMMn0f/view?usp=sharing
https://sourceforge.net/projects/gns-3/files/VirtualBox%20Appliances/OpenswitchOPX-2.3.2.zip
https://www.4shared.com/s/fQu2DUd9dca




