Nokia Strikes 5G Test Deal With China Social Media Giant Tencent
 The vendor has seen around 20 percent growth per quarter over the past two quarters across its enterprise, webscale, and cable TV markets.
The vendor has seen around 20 percent growth per quarter over the past two quarters across its enterprise, webscale, and cable TV markets.
ThetaRay Scores $30 Million Series B for AI-Powered Security
 The startup’s customers include banks and industrial firms. Its latest funding round brings its total to $60.5 million.
The startup’s customers include banks and industrial firms. Its latest funding round brings its total to $60.5 million.
Telecom Services 23% of US IT Market
The drive for SD-WAN and mobile phones degrades this position.
Debugging Serverless Apps
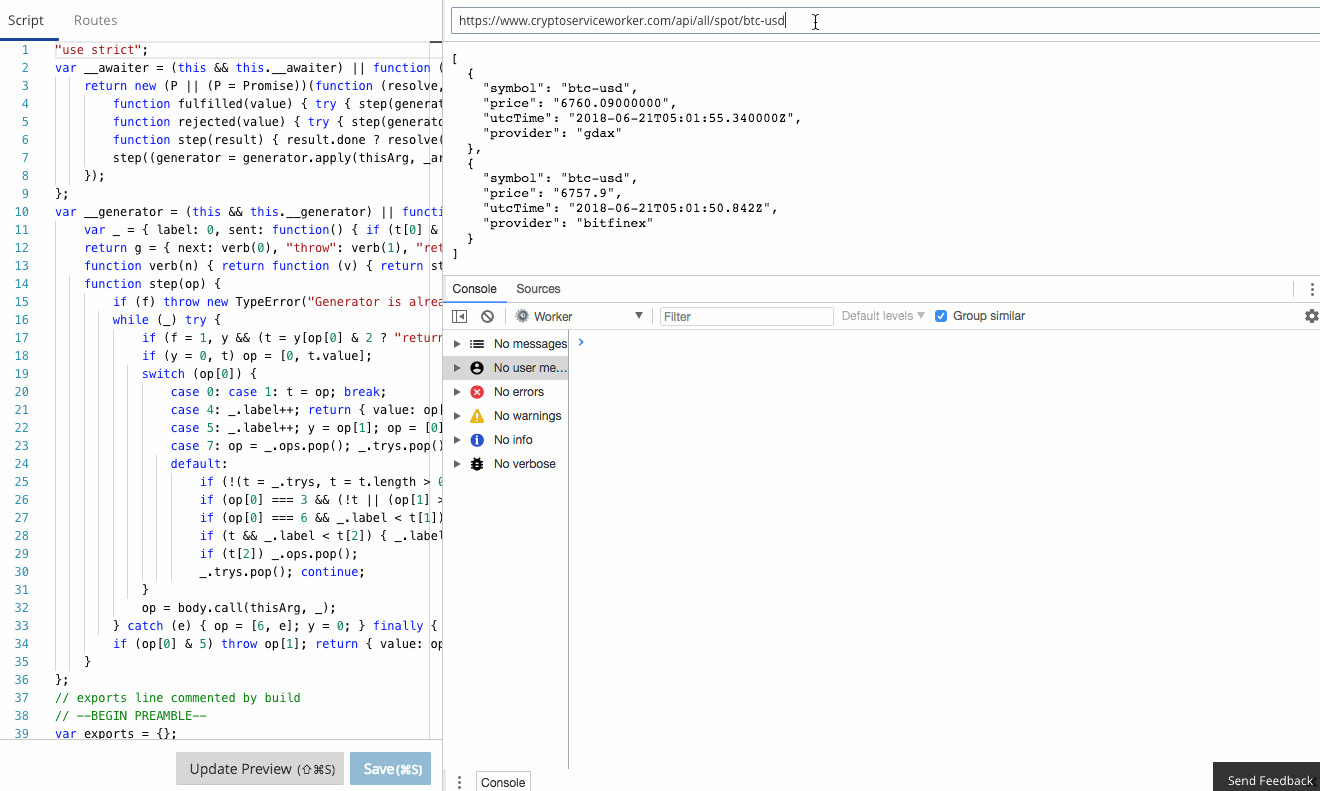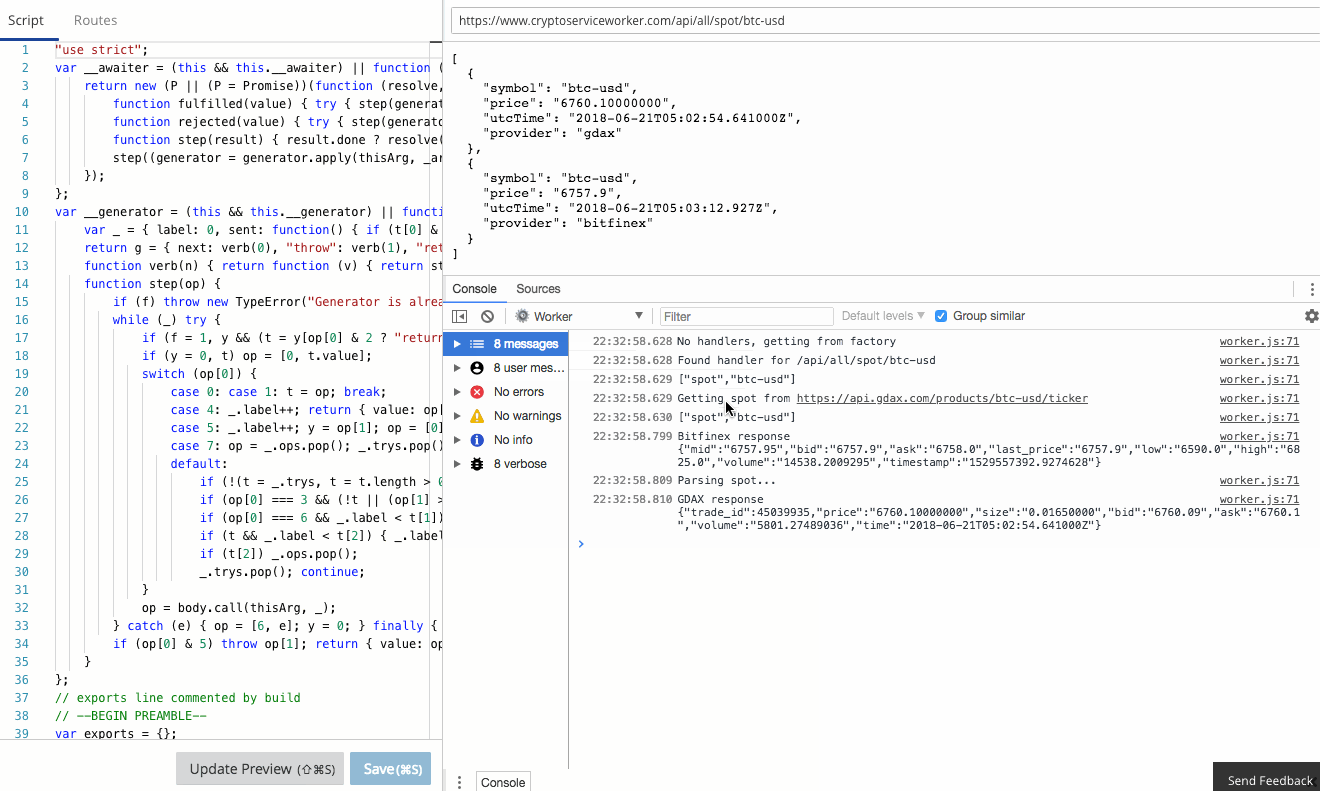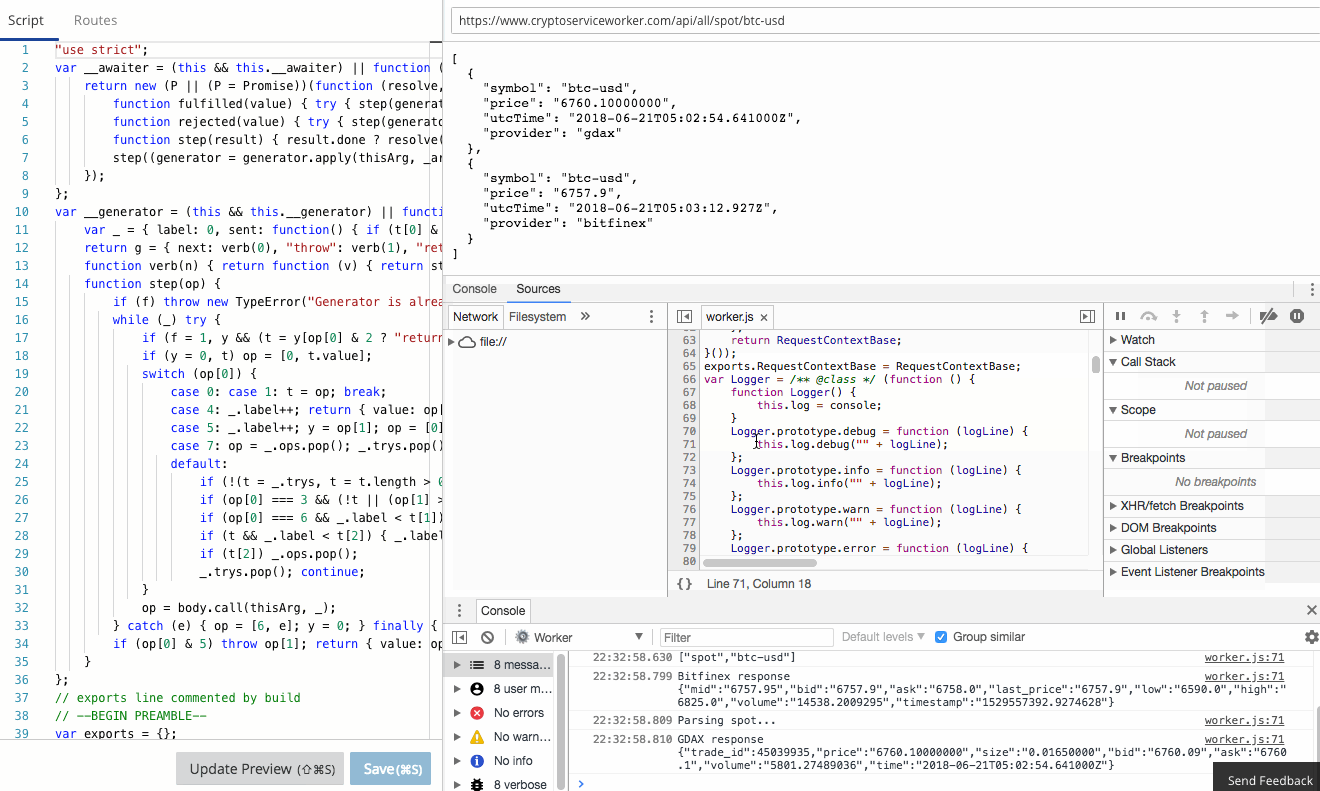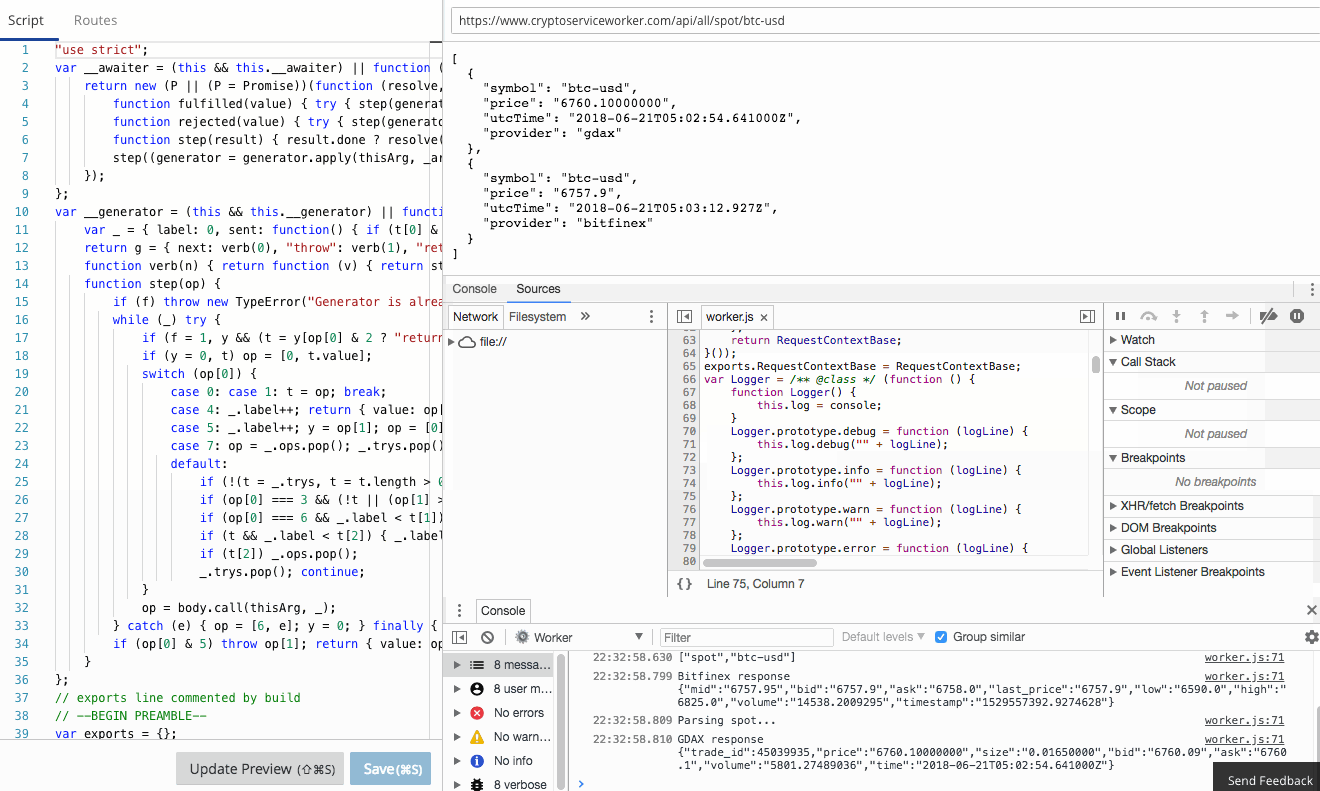
The Workers team have already done an amazing job of creating a functional, familiar edit and debug tooling experience in the Workers IDE. It's Chrome Developer Tools fully integrated to Workers.
console.log in your Worker goes straight to the console, just as if you were debugging locally! Furthermore, errors and even log lines come complete with call-site info, so you click and navigate straight to the relevant line.
In this blog post I’m going to show a small and powerful technique I use to make debugging serverless apps simple and quick.
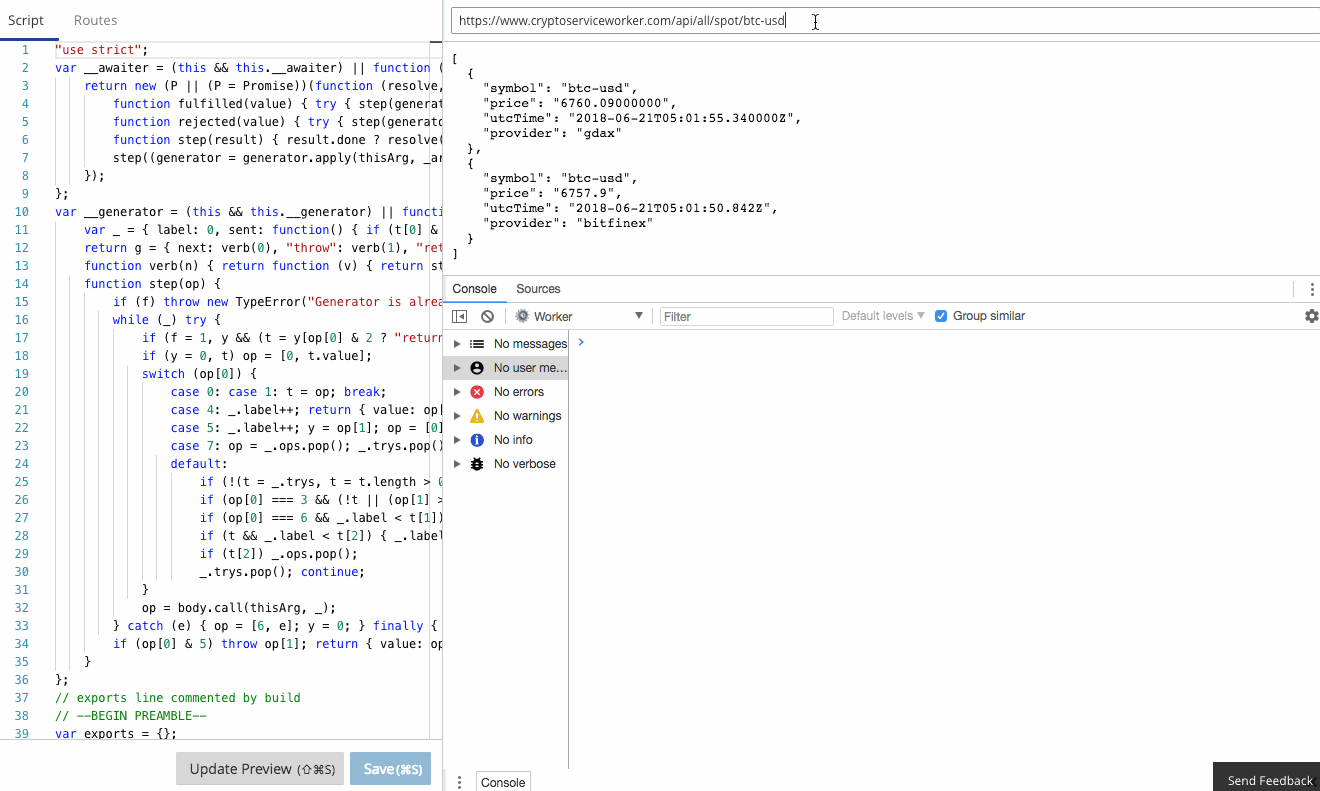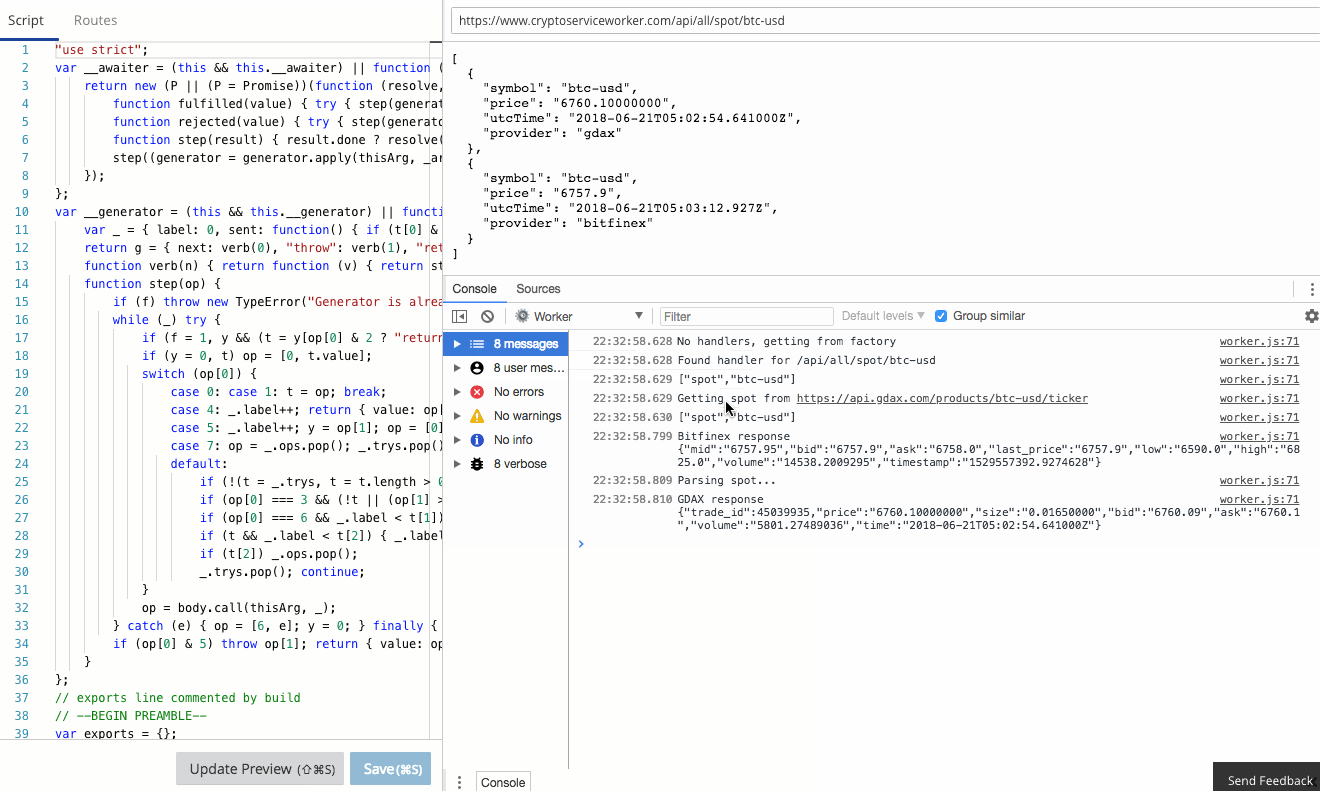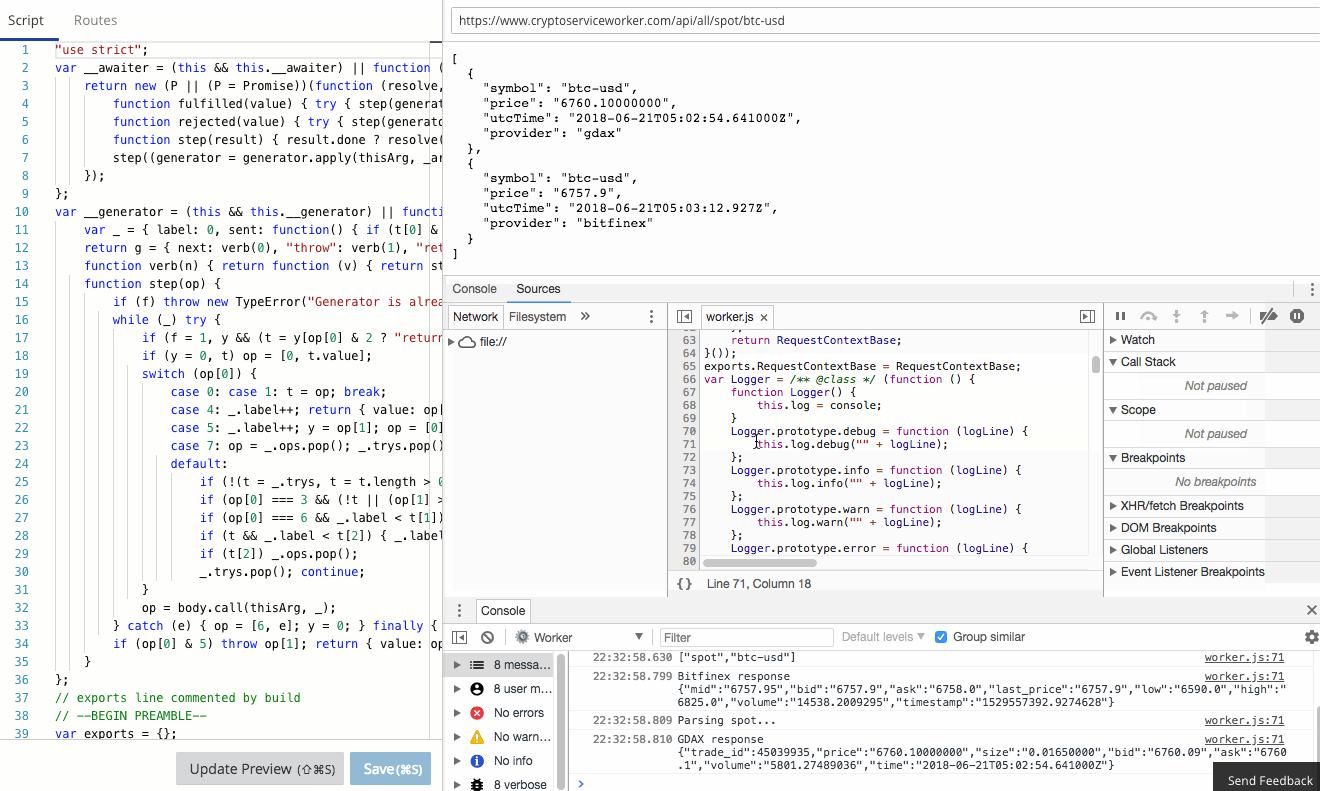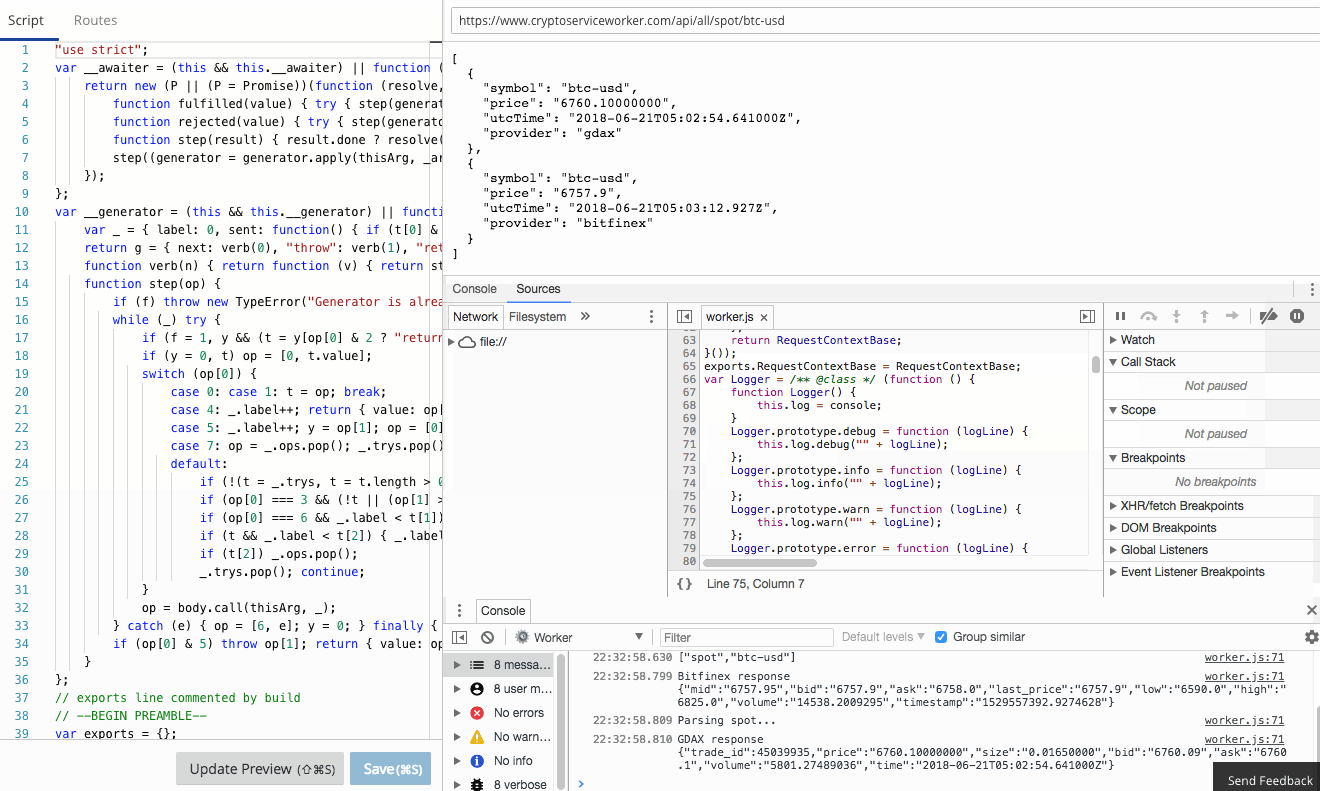
There is a comprehensive guide to common debugging approaches and I'm going to focus on returning debug information in a header. This is a great tip and one that I use to capture debug information when I'm using curl or Postman, or integration tests. It was a little finicky to get right the first time, so let me save you some trouble.
If you've followed part 1 or part 2 of my Workers series, you'll know I'm using Typescript, but the approach would equally apply to Javascript. In the rest of this example, I’ll be using the routing framework I created in part 2.
Requesting Debug Info
Feedback: Data Center Infrastructure for Networking Engineers
When I created the Data Center Infrastructure for Networking Engineers webinar, I wanted to reach these goals:
- Understand the data center acronym soup;
- Build a conceptual framework of the data center technologies and solutions.
Every now and then I get feedback from a happy attendee telling me how the webinar helped them. Here’s what I got earlier this month:
Read more ...Why you should not use Google Cloud – Punch a Server
Google shutoff their ‘data centre’. No one to contact to get it back.
When Firepower Management Center Goes Offline
A typical Firepower deployment consists of a management component and a managed device. The management component is known as Firepower Management Center (FMC). The managed device is the NGIPS or NGFW itself and would be leveraging the Firepower or the Firepower Threat Defense (FTD) operating system. Both layers of the topology include provisions for redundant deployments. Firepower Management Center is available in a two-node HA configuration. Firepower Threat Defense, the NGFW managed device, can be either HA or clustered.
One question that often comes up is, “What happens when FMC goes offline?” The general response is traffic continues to flow but the managed device cannot be managed. While this is not a good position to be in, it does provide an opportunity to assess the impact of waiting for a maintenance window (or a replacement).
TL;DR
- Firepower continues to pass traffic when FMC is offline
- Events captured on the Firepower device will be passed to the FMC when it is available
- Event Storage on the managed device is finite, events may be lost during an extended outage
- Malware Cloud Lookups/Block functionality depends on FMC, plan HA and File Policy accordingly
- Firepower managed device cannot be managed until FMC is available
When Firepower Management Center Goes Offline
A typical Firepower deployment consists of a management component and a managed device. The management component is known as Firepower Management Center (FMC). The managed device is the NGIPS or NGFW itself and would be leveraging the Firepower or the Firepower Threat Defense (FTD) operating system. Both layers of the topology include provisions for redundant deployments. Firepower Management Center is available in a two-node HA configuration. Firepower Threat Defense, the NGFW managed device, can be either HA or clustered.
One question that often comes up is, “What happens when FMC goes offline?” The general response is traffic continues to flow but the managed device cannot be managed. While this is not a good position to be in, it does provide an opportunity to assess the impact of waiting for a maintenance window (or a replacement).
TL;DR
- Firepower continues to pass traffic when FMC is offline
- Events captured on the Firepower device will be passed to the FMC when it is available
- Event Storage on the managed device is finite, events may be lost during an extended outage
- Malware Cloud Lookups/Block functionality depends on FMC, plan HA and File Policy accordingly
- Firepower managed device cannot be managed until FMC is available
Tracking DNSSEC: See the Deployment Maps
Did you know the Internet Society Deploy360 Programme provides a weekly view into global DNSSEC deployment? Each Monday, we generate new maps and send them to a public DNSSEC-Maps mailing list. We also update the DNSSEC Deployment Maps page periodically, usually in advance of ICANN meetings.
DNS Security Extensions — commonly known as DNSSEC — allow us to have more confidence in our online activities at work, home, and school. DNSSEC acts like tamper-proof packaging for domain name data, helping to ensure that you are communicating with the correct website or service. However, DNSSEC must be deployed at each step in the lookup from the root zone to the final domain name. Signing the root zone, generic Top Level Domains (gTLDs) and country code Top Level Domains (ccTLDs) is vital to this overall process. These maps help show what progress the Internet technical community is making toward the overall goal of full DNSSEC deployment.
These maps are a bit different from other DNSSEC statistics sites in that they contain both factual, observed information and also information based on news reports, presentations, and other collected data. For more information about how we track the deployment status of TLDs, please read our page Continue reading
Network Address Translation (NAT) and BGP Explained
The post Network Address Translation (NAT) and BGP Explained appeared first on Noction.
Cisco Live 2018 – Yes, I Went Too
It’s been a very busy month or so. June is always like that, it seems. There’s ARRL Field Day, which is always the last rainy weekend in June. This year, Cisco Live was in June, and that typically includes Tech Field Day activities. Right before that, we had the whole family in town for a family reunion. There was all sorts of stuff going on. Now that most of that has blown over, I’ve collected my thoughts and wanted to talk about Cisco Live this year.
Those who are of any importance in the networking world (LOL!) converged on Orlando this to attend the conference. Orlando brings back all sorts of memories — from Taverna Opa to Sizzler to LISP explained with plates — and we’re all familiar with the Orange County Convention Center. It’s a great facility with enough room to handle the largest of gatherings. I don’t think I saw the attendance numbers, but I would guess there were 30,000 attendees at Cisco Live this year. A typical crowd for the event, and the venue was more than adequate.
This year, I went on the Imagine Pass instead of the full conference pass. This pass included Continue reading
Too Old To Rocket Load, Too Young To Die

Rocket Loader is in the news again. One of Cloudflare's earliest web performance products has been re-engineered for contemporary browsers and Web standards.
No longer a beta product, Rocket Loader controls the load and execution of your page JavaScript, ensuring useful and meaningful page content is unblocked and displayed sooner.
For a high-level discussion of Rocket Loader aims, please refer to our sister post, We have lift off - Rocket Loader GA is mobile!
Below, we offer a lower-level outline of how Rocket Loader actually achieves its goals.
Prehistory
Early humans looked upon Netscape 2.0, with its new ability to script HTML using LiveScript, and <BLINK>ed to ensure themselves they weren’t dreaming. They decided to use this technology, soon to be re-christened JavaScript (a story told often and elsewhere), for everything they didn’t know they needed: form input validation, image substitution, frameset manipulation, popup windows, and more. The sole requirement was a few interpreted commands enclosed in a <script> tag. The possibilities were endless.

Soon, the introduction of the src attribute allowed them to import a file full of JS into their pages. Little need to fiddle with the markup, when all the requisite JS for the page Continue reading