How to Mitigate Shadow AI Security Risks by Implementing the Right Policies
Security has become even more paramount in every organization with growing popularity in AI created by a new phenomenon of ‘Shadow AI’ applications that need to be vetted against security policies.Adding TS’s IP Address to MAC-VRF (L2RIB) and IP-VRF (L3RIB)
In the previous chapter, we discussed how a VTEP learns the local TS's MAC address and the process through which the MAC address is programmed into BGP tables. An example VTEP device was configured with a Layer 2 VLAN and an EVPN Instance without deploying a VRF Context or VLAN routing interface. This chapter introduces, at a theoretical level, how the VTEP device, besides the TS's MAC address, learns the TS's IP address information after we have configured the VRF Context and routing interface for our example VLAN.
Figure 1-3: MAC-VRF Tenant System’s IP Address Propagation.
I have divided Figure 1-3 into three sections. The section on the top left, Integrated Routing and Bridging - IRB illustrates the components required for intra-tenant routing and their interdependencies. By configuring a Virtual Routing and Forwarding Context (VRF Context), we create a closed routing environment with a per-tenant IP-VRF L3 Routing Information Base (L3RIB). Within the VRF Context, we define the Layer 3 Virtual Network Identifier (L3VNI) along with the Route Distinguisher (RD) and Route Target (RT) values. The RD of the VRF Context enables the use of overlapping IP addresses across different tenants. Based on the RT value of the VRF Context, Continue reading
10 Steps to Choosing the Best SD-WAN Provider for Your Company
When evaluating SD-WAN providers, proceed with caution.OSPF Summarization and Split Areas
In the Do We Still Need OSPF Areas and Summarization? I wrote this somewhat cryptic remark:
The routers advertising a summarized prefix should be connected by a path going exclusively through the part of the network with more specific prefixes. GRE tunnel also satisfies that criteria; the proof is left as an exercise for the reader.
One of my readers asked for a lengthier explanation, so here we go. Imagine a network with two areas doing inter-area summarization on /24 boundary:
OSPF Summarization and Split Areas
In the Do We Still Need OSPF Areas and Summarization? I wrote this somewhat cryptic remark:
The routers advertising a summarized prefix should be connected by a path going exclusively through the part of the network with more specific prefixes. GRE tunnel also satisfies that criteria; the proof is left as an exercise for the reader.
One of my readers asked for a lengthier explanation, so here we go. Imagine a network with two areas doing inter-area summarization on /24 boundary:
Tech Bytes: Cisco ThousandEyes Deepens Visibility for Remote Workforce Management (Sponsored)
SecOps, NetOps, and help desks need integrated data, increased context, and the ability to quickly understand interdependencies in order to take on the complex tasks facing them. That’s why ThousandEyes is now integrated with Cisco Secure Access, Cisco’s SSE solution. Tune in to learn about ThousandEyes’ deeper visibility, system process metrics, streamlined test setup, and... Read more »User Discomfort As A Security Function

If you grew up in the 80s watching movies like me, you’ll remember Wargames. I could spend hours lauding this movie but for the purpose of this post I want to call out the sequence at the beginning when the two airmen are trying to operate the nuclear missile launch computer. It requires the use of two keys, one each in the possession of one of the airmen. They must be inserted into two different locks located more than ten feet from each other. The reason is that launching the missile requires two people to agree to do something at the same time. The two key scene appears in a number of movies as a way to show that so much power needs to have controls.
However, one thing I wanted to talk about in this post is the notion that those controls need to be visible to be effective. The two key solution is pretty visible. You carry a key with you but you can also see the locks that are situated apart from each other. There is a bit of challenge in getting the keys into the locks and turning them simultaneously. That not only shows that the Continue reading
NB 469: Arista Debuts Network Observability Service; Startups Aim To Break Nvidia’s AI Chip Grip
This week we discuss a new network observability offering from Arista that integrates network telemetry with application data, why startups such as Groq and Taalas think they can break Nvidia’s grip on the AI chip market, and how Microsoft is hedging its LLM bets. Amazon goes nuclear with the purchase of a reactor-powered data center... Read more »What is Network-as-a-Service (NaaS)? A Complete Guide
Network-as-a-Service (NaaS) offers a flexible, cost-effective, and efficient way for businesses to manage their networking needs. Here is an overview to guide your selection and use of NaaS.Security Week 2024 wrap up

The next 12 months have the potential to reshape the global political landscape with elections occurring in more than 80 nations, in 2024, while new technologies, such as AI, capture our imagination and pose new security challenges.
Against this backdrop, the role of CISOs has never been more important. Grant Bourzikas, Cloudflare’s Chief Security Officer, shared his views on what the biggest challenges currently facing the security industry are in the Security Week opening blog.
Over the past week, we announced a number of new products and features that align with what we believe are the most crucial challenges for CISOs around the globe. We released features that span Cloudflare’s product portfolio, ranging from application security to securing employees and cloud infrastructure. We have also published a few stories on how we take a Customer Zero approach to using Cloudflare services to manage security at Cloudflare.
We hope you find these stories interesting and are excited by the new Cloudflare products. In case you missed any of these announcements, here is a recap of Security Week:
Responding to opportunity and risk from AI
| Title | Excerpt |
|---|---|
| Cloudflare announces Firewall for AI | Cloudflare announced the development of Firewall for AI, Continue reading |
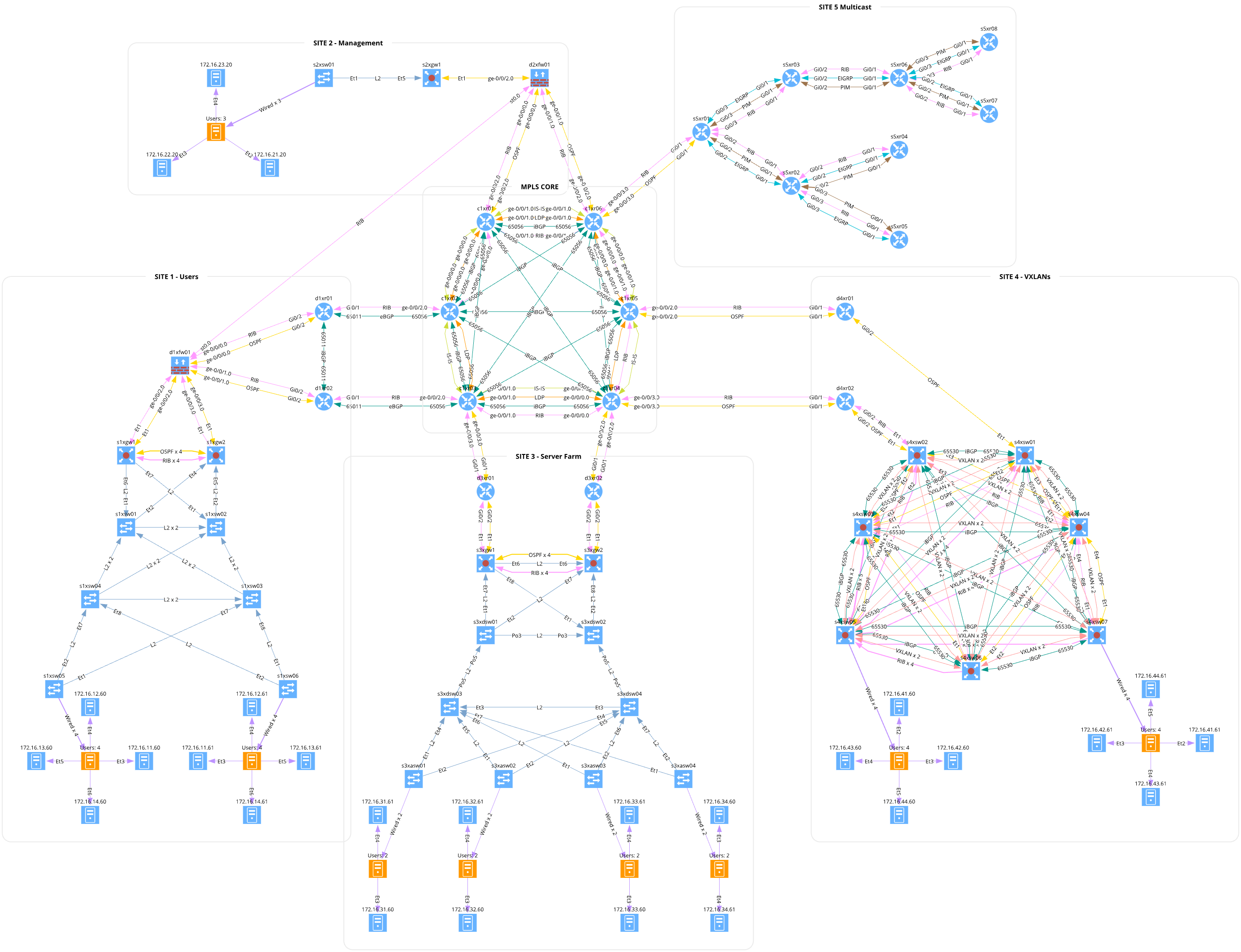
Cyber Crane Mesh Topology Built with netlab
Milan Zapletal submitted the source code for a huge lab topology they built with netlab. It has almost 50 routers and over 50 Linux nodes to emulate end-users and servers.
They used netlab to configure VLANs, VRFs, IS-IS, OSPF, EIGRP, BGP, MPLS, VXLAN, and EVPN. Imagine how long it would take to configure all that by hand using a more traditional labbing tool.
Cyber Crane Mesh Topology Built with netlab
Milan Zapletal submitted the source code for a huge lab topology they built with netlab. It has almost 50 routers and over 50 Linux nodes to emulate end-users and servers.
They used netlab to configure VLANs, VRFs, IS-IS, OSPF, EIGRP, BGP, MPLS, VXLAN, and EVPN. Imagine how long it would take to configure all that by hand using a more traditional labbing tool.
KeyTrap!
Yet another DNS vulnerability has been exposed. The language of the press release revealing the vulnerabil;ity is certainly dramatic, with "devasting consequences" and the threat to "completely disable large parts of the worldwide Internet."" If this is really so devastating then perhaps we should look at this in a little more detail to see what’s going on, how this vulnerability works, and what the response has been.KeyTrap!
Yet another DNS vulnerability has been exposed. The language of the press release revealing the vulnerabil;ity is certainly dramatic, with "devasting consequences" and the threat to "completely disable large parts of the worldwide Internet."" If this is really so devastating then perhaps we should look at this in a little more detail to see what’s going on, how this vulnerability works, and what the response has been.The Future of Network Engineering in the AI/ML era

It seems like yesterday when I saw my first network automation presentation at a conference. I remember it very well; it was in 2015 at the Cisco Network Innovation Summit in Prague. Mr. Tim Szigeti was presenting the first version of the Cisco APIC-EM, the future Cisco Digital Network Architecture (DNA) controller. I talked already about it in a previous article, written in 2018, about my journey toward network programmability and automation. After its presentation, and for many years afterward, the question was on everyone’s lips: Is this the end…
The post The Future of Network Engineering in the AI/ML era appeared first on AboutNetworks.net.
Slurp’it – Network Inventory & Discovery Tool

I recently came across a neat tool called 'Slurp'it', a Network Inventory and Discovery solution. If you've been following my blog for a while, you know I just had to give it a try and share my findings with you. So, in this post, I'm going to quickly go over how to get it up and running, along with a few ways you might find it useful. Let's dive in.
What We Will Cover?
- What is Slurp'it?
- Licenses
- Installation and Setup
- Data Collection
- Custom Planning
- Some Use Cases
What is Slurp'it?
The official definition is "Slurp’it is a powerful and easy-to-use network discovery solution that offers 100% accurate network inventory. No coding required." Out of the box, the tool supports almost all the vendors (117 as of writing this)
In a nutshell, Slurp'it simplifies the whole process of understanding your network's inventory. All you need to do is provide the IP address or hostname of your devices, along with the login credentials. Slurp'it takes it from there. It executes various 'show' commands on your devices, usesTextFSM to parse the outputs, and finally presents you with a tidy table detailing everything it has discovered. It's straightforward yet effective, Continue reading
Understanding BGP Communities
The post Understanding BGP Communities appeared first on Noction.
Worth Reading: Talent Gap in IT
If you need a good rant about Thought Leaders, Talent Gap, and Certification-Based-Hiring, look no further than I see a different gap from here!. Here’s a choice tidbit:
Every single job description that requires some sort of certification must be treated with suspicion. Demanding a certification usually means that you don’t know what you want, and you’re just outsourcing your thinking to someone else.
Have fun!