Datanauts 136: ChatOps Using PoshBot With Brandon Olin
On this episode of Datanauts, we chat with Brandon Olin, the creator of PoshBot, a PowerShell based chatbot for ops teams. What does PoshBot do? How was PoshBot built? How do chatbots impact Brandon’s delivery model?
ChatBots?
Bots have been around for a long time. They re really handy, too, often being able to answer simple questions by submitting a special command that has some sort of prefix or identifier associated with them. Especially if you re on Twitch and want to know how long your favorite streamer has been online.
Maybe that isn t the most helpful thing in the world, but what if we changed the narrative to be all about operations and how talking to a bot (with your peers watching) could actually up-level your day-to-day enjoyment of IT?
That’s our conversation today.
What is PoshBot?
PoshBot is a chat bot written in PowerShell. It makes extensive use of classes introduced in PowerShell 5.0. PowerShell modules are loaded into PoshBot and instantly become available as bot commands. PoshBot currently supports connecting to Slack to provide you with awesome ChatOps goodness.
For More Information About PoshBot
- PoshBot on GitHub, Home of the PoshBot Project
https://github.com/poshbotio - PoshBot Continue reading
AT&T’s Mixed Messages on 5G Fixed Wireless
 AT&T executives tout the company’s 5G fixed wireless trial results but cast doubt on the cost effectiveness of deploying the technology. Is the company just protecting its DirecTV business?
AT&T executives tout the company’s 5G fixed wireless trial results but cast doubt on the cost effectiveness of deploying the technology. Is the company just protecting its DirecTV business?
Kubernetes Driving Broader, Deeper Container Usage, Study Finds
 Organizations are packing 50 percent more running containers per host, with a vast majority running less than one hour.
Organizations are packing 50 percent more running containers per host, with a vast majority running less than one hour.
IBM’s New Cloud Data Service Targets Enterprise AI, Could Capture Microsoft’s Attention
 Recent updates ahead of its official launch included a product to help organizations deal with the EU's recently implemented GDPR rules.
Recent updates ahead of its official launch included a product to help organizations deal with the EU's recently implemented GDPR rules.
Cisco’s Cloud Team Contends With Old-School Cisco Sales Team
 Compton’s job will be to orchestrate across a hodge podge of clouds and internal business units. And he’ll need to inspire the sales force to sell cloud technology, too.
Compton’s job will be to orchestrate across a hodge podge of clouds and internal business units. And he’ll need to inspire the sales force to sell cloud technology, too.
French Hosting Provider Fends Off DDoS Attacks With NetScout vAPS
 As a hosting provider, Jaguar Networks has a higher risk of DDoS attacks because it aggregates its customers' risks in a shared infrastructure.
As a hosting provider, Jaguar Networks has a higher risk of DDoS attacks because it aggregates its customers' risks in a shared infrastructure.
Extending the Power of NSX to Bare-metal Workloads
Authors – Sridhar Subramanian and Geoff Wilmington
VMware NSX Data Center was built with the goal of consistent networking and security services independent of changing application frameworks or physical infrastructure. In the last couple of years, NSX Data Center has focused on delivering network and security abstractions for applications on any compute platform. In our journey, we have handled VM’s, containers, cloud, and now we are also looking to help our customers with scenarios where they need a unified experience for bare-metal workloads. The goal being to maintain a consistent security experience regardless of location or platform the workload is running on.
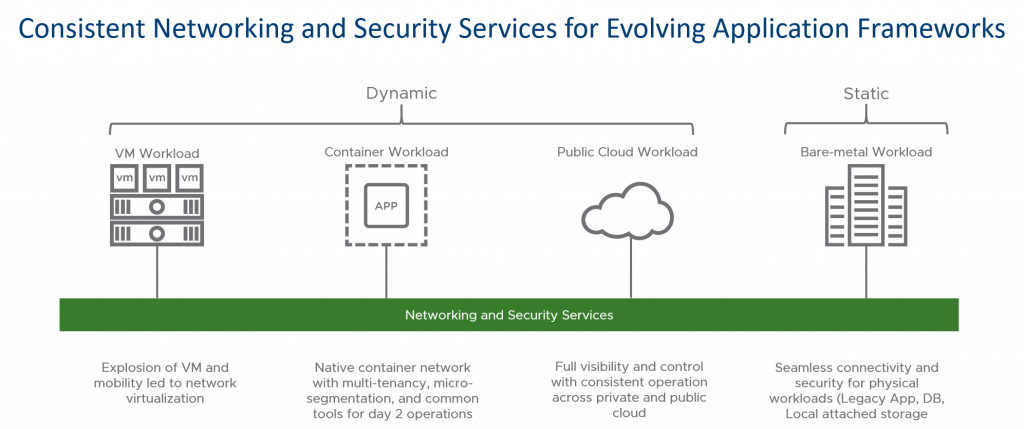
This experience means being able to take any workload, add it to an NSX Data Center Security Group and through the NSX Data Center Distributed Firewall have a consistent policy applied regardless of location and workload type. This consistent approach leverages the NSX DFW capabilities with stateful firewalling for the workloads. This is accomplished outside of using native OS capabilities like IP Tables or Windows Firewall so security admins only need to understand how to apply security through NSX DFW, and not have to understand the myriad of native OS approaches and complexity. By centralizing Continue reading
To Tackle the VPNFilter Botnet, It’s Going to Take Help from You and Me
If you’ve been reading the news lately, you might have seen headlines like “FBI to America: Reboot Your Routers, Right Now” or “F.B.I.’s Urgent Request: Reboot Your Router to Stop Russia-Linked Malware”. These headlines can be pretty alarming, and you may find yourself thinking, “things must be pretty bad if the FBI is putting out such an urgent warning.”
Cyber threats are not uncommon, but the good news is that the security community is working around the clock to tackle these threats as early and quickly as possible. Most of the time we do not see all this hard work, nor are we often asked to play a large part in taking down a botnet. But this time, by rebooting our routers, we can help the law enforcement and information security communities to identify infected routers so they can be cleaned up, moving us closer to a permanent fix for a particular kind of malware – VPNFilter.
Here is what happened …
From Discovery to Takedown
On 23 May, 2018, researchers at Cisco’s Talos publicly shared their findings about a large botnet of infected networking devices (home routers) they called “VPNFilter” because of concerns that the Continue reading
Connecting the Unconnected: The Land of Zero Connect
As we move to a more digitally-connected world, the need for Internet access has never been greater. In many parts of the world, the Internet has firmly established itself as a core part of everyday life – and this holds true for everyone from kids to adults to senior citizens. Yet, there remain communities and places around the world that are still offline. In some instances, these are probably the hardest locations to connect. And there are many reasons for this – geography and terrain could be one reason, commercial viability of service provision is another, as is affordability – the capacity of the community to pay for devices and Internet connectivity.
In 2010, the Internet Society Asia-Pacific Bureau launched the award-winning Wireless for Communities Programme. This was a pioneering effort that placed the local community front and centre, with its catchphrase – “for the community, with the community, by the community”.
The focus of the programme is to provide Internet access and connectivity to underserved and unserved rural areas in a holistic manner that leads to socioeconomic empowerment. A key component involves developing communities’ capacity to build and operate the wireless network, and at the same time, empowering them Continue reading
Episode 28 – For the Love of NAT
When it comes to NAT, network engineers love it, they hate it, or the love to hate it. In this episode, Tom Hollingsworth and Nick Buraglio join us to talk about NAT, why it exists, and its continued role in networking.
 We would like to thank Core BTS for sponsoring this episode of Network Collective. Core BTS focuses on partnering with your company to deliver technical solutions that enhance and drive your business. If you’re looking for a partner to help your technology teams take the next step, you can reach out to Core BTS by emailing them here.
We would like to thank Core BTS for sponsoring this episode of Network Collective. Core BTS focuses on partnering with your company to deliver technical solutions that enhance and drive your business. If you’re looking for a partner to help your technology teams take the next step, you can reach out to Core BTS by emailing them here.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post Episode 28 – For the Love of NAT appeared first on Network Collective.
Don’t Miss Keith Bogart’s Live Webinar! Deciphering Spanning-Tree Technologies
Tune in Tomorrow, May 31st, at 10 am PDT/ 1 pm EDT for a FREE live webinar with expert instructor Keith Bogart (CCIE #4923).
About This Webinar:
Understanding the logic of 802.1d and how it builds a loop-free “tree” is critical to passing any Cisco certification exam. Presented by INE instructor Keith Bogart (CCIE #4923), this session will take you through that logic so that, given any bridged/switched layer-2 network, you can predict what tree will be formed. Ask questions live with an experienced industry expert!
Business-Driven Network Transformation
Understand business requirements before jumping into a network design in order to ensure they're aligned, networking expert says.
Typical EVPN BGP Routing Designs
As discussed in a previous blog post, IETF designed EVPN to be next-generation BGP-based VPN technology providing scalable layer-2 and layer-3 VPN functionality. EVPN was initially designed to be used with MPLS data plane and was later extended to use numerous data plane encapsulations, VXLAN being the most common one.
Design Requirements
Like any other BGP-based solution, EVPN uses BGP to transport endpoint reachability information (customer MAC and IP addresses and prefixes, flooding trees, and multi-attached segments), and relies on an underlying routing protocol to provide BGP next-hop reachability information.
Read more ...


