Encryption Is Key to Safety of Journalists
At a time when we notice increasing and alarming threats to media freedom around the world, World Press Freedom Day (WPFD) is more pertinent today than ever before. We therefore can’t afford to celebrate this important day without both considering the damage done to the free press over the past year and intensifying our efforts to protect journalists and the future of journalism around the world.
To ensure that we can continue to celebrate the media’s vital role in democracies in the future, we must tackle the increasing number of Internet shutdowns around the world and find better ways to secure the safety of journalists.
Let’s start with the latter. The surveillance of journalists, in particular, has profound implications for democratic institutions, including freedom of the press. It threatens journalists’ ability to confidently and confidentially work with sources and to unlock information about controversial issues. It therefore hinders their ability to play their roles as watchdogs in democratic or undemocratic, developed or developing societies alike. But reports indicate that more and more journalists are at risk of facing state or societal surveillance.
Encryption offers a vital and relatively simple defense for such intrusions. Building on last year’s Continue reading
Google Secures 5 Partners for Its Cloud Security Command Center
 The five container-focused partners include Aqua Security, Capsule8, Stackrox, Sysdig Secure, and Twistlock.
The five container-focused partners include Aqua Security, Capsule8, Stackrox, Sysdig Secure, and Twistlock.
Equinix Interconnection Revenues Jump 16% in First Quarter 2018
 The data center giant also added private, direct connections to Microsoft Azure cloud services in Miami and Paris.
The data center giant also added private, direct connections to Microsoft Azure cloud services in Miami and Paris.
BiB 41: VMware NSX SD-WAN By VeloCloud
VMware's networking and cloud ambitions come into sharper focus with the introduction of NSX SD-WAN by VeloCloud.
The post BiB 41: VMware NSX SD-WAN By VeloCloud appeared first on Packet Pushers.
Cloud Provider RapidScale Offers Citrix NetScaler SD-WAN
 The partnership between a cloud provider and an SD-WAN vendor allows Citrix’s technology to run on a RapidScale’s global backbone.
The partnership between a cloud provider and an SD-WAN vendor allows Citrix’s technology to run on a RapidScale’s global backbone.
Call for Contributions to Northern Public Affairs: Internet Connectivity in Indigenous and Northern Communities
Northern Public Affairs, in collaboration with the Internet Society, is pleased to release a call for contributions to the Fall 2018 special issue of NPA Magazine focusing on emerging developments in community networks among Indigenous peoples in North America.
Internet connectivity for Indigenous Peoples in Canada and the United States has long been difficult to implement due to many environmental and socioeconomic factors such as remoteness of communities, difficulty gaining first mile access, reliable networks, slow speeds, expensive equipment, and high data costs. Community networks are communications infrastructure deployed and operated by local people, offering Indigenous communities a way to access the Internet to meet their own needs. For many, affordable, high-quality Internet access means community sustainability. Community networks encourage policymakers and regulators to examine new ways and means to fill local digital divides, like supporting local content in the appropriate language(s).
In this special edition issue of NPA Magazine the goal is to assemble diverse voices to explore the impact of access in the areas of education, healthcare, digital literacy, cultural/language promotion and preservation, as well as any negative impacts. We will seek existing Indigenous Community Networks and developing ones, highlighting successful and promising initiatives bringing Internet connectivity Continue reading
Against metrics: how measuring performance by numbers backfires | Aeon Ideas

Metrics lead to gaming the system
Custom Page Selection for Cloudflare Apps
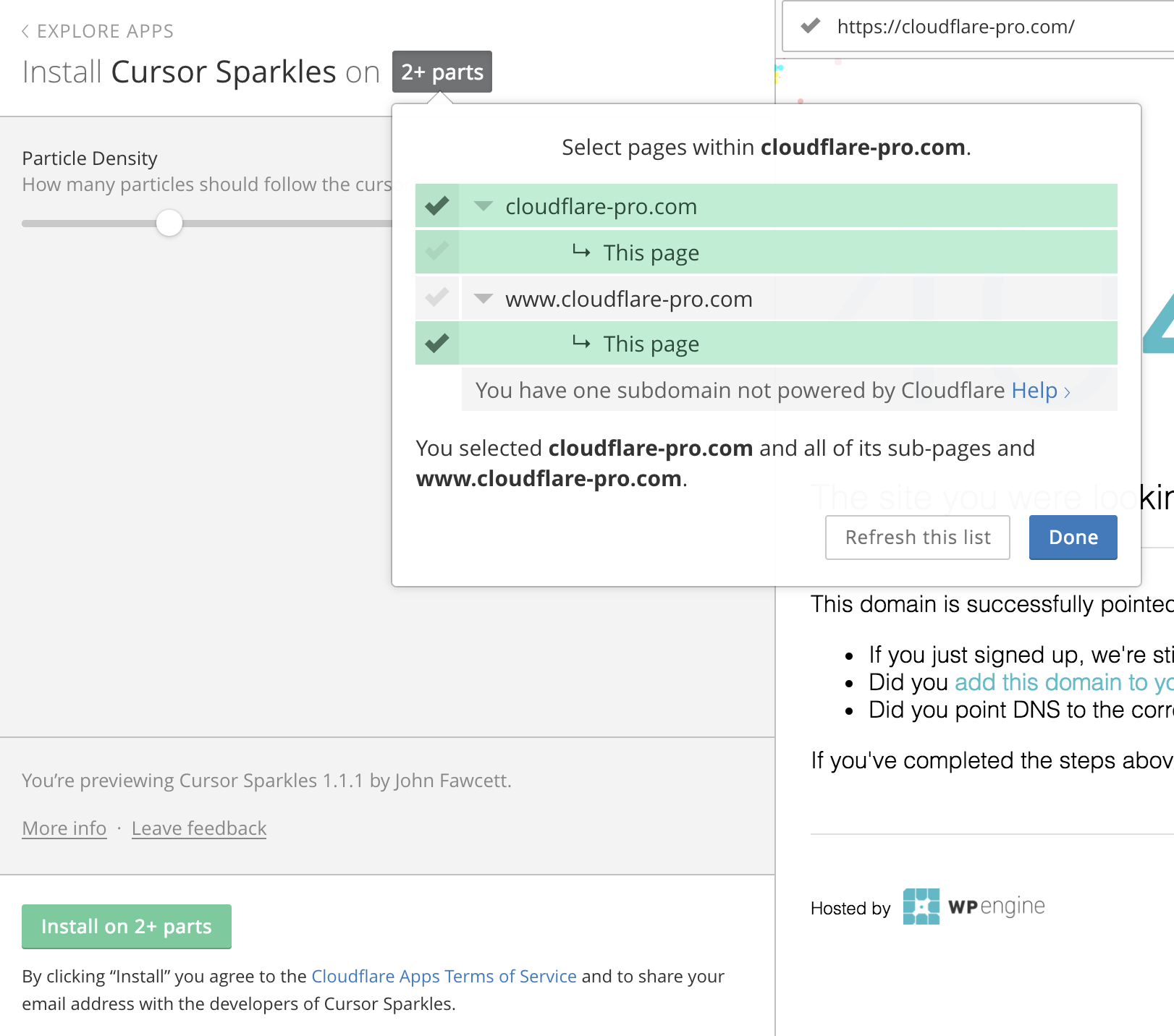
In July 2016, Cloudflare integrated with Eager - an apps platform. During this integration, several decisions were made to ensure an optimal experience installing apps. We wanted to make sure site owners on Cloudflare could customize and install an app with the minimal number of clicks possible. Customizability often adds complexity and clicks for the user. We’ve been tinkering to find the right balance of user control and simplicity since.
When installing an app, a site owner must select where - what URLs on their site - they want what apps installed. Our original plan for selecting the URLs an app would be installed on took a few twists and turns. Our end decision was to utilize our Always Online crawler to pre-populate a tree of the user’s site. Always Online is a feature that crawls Cloudflare sites and serves pages from our cache if the site goes down.
The benefits to this original setup are:
1. Only valid pages appear
An app only allows installations on html pages. For example, since injecting Javascript into a JPEG image isn’t possible, we would prevent the installer from trying it by not showing that path. Preventing the user from that type of Continue reading
Networking Pros: Get Out of Your Comfort Zone
Surviving tumultuous times in enterprise IT means networking pros need to focus on learning new skills and participating in the community, panelists at Interop ITX said.
Cisco to MikroTik – MPLS
About the Cisco to MikroTik series
One of the hardest things to do quickly in network engineering, is learn a new syntax for a NOS. Especially if you have a tight deadline and need to stand up equipment you’ve never worked with before. The command structure for RouterOS can be cumbersome if you are used to the Cisco CLI.
If you’ve been in networking for a while, you probably started with learning the Cisco CLI. Therefore, it is helpful to compare the commands if you want to implement a network with a MikroTik and Cisco routers.
This is the third post in a series that creates a Rosetta stone between IOS and RouterOS. We plan to tackle other command comparisons like VLANs, QoS and basic operations to make it easier for network engineers trained in Cisco IOS to successfully implement Mikrotik / RouterOS devices.
Click here for the first article in this series – “Cisco to MikroTik BGP command translation”
Click here for the second article in this series – “Cisco to MikroTik OSPF command translation”
While many commands have almost the exact same information, others are as close as possible. Since there isn’t always an exact match, sometimes you may have to run Continue reading
Cisco to MikroTik – MPLS
About the Cisco to MikroTik series
One of the hardest things to do quickly in network engineering, is learn a new syntax for a NOS. Especially if you have a tight deadline and need to stand up equipment you’ve never worked with before. The command structure for RouterOS can be cumbersome if you are used to the Cisco CLI.
If you’ve been in networking for a while, you probably started with learning the Cisco CLI. Therefore, it is helpful to compare the commands if you want to implement a network with a MikroTik and Cisco routers.
This is the third post in a series that creates a Rosetta stone between IOS and RouterOS. We plan to tackle other command comparisons like VLANs, QoS and basic operations to make it easier for network engineers trained in Cisco IOS to successfully implement Mikrotik / RouterOS devices.
Click here for the first article in this series – “Cisco to MikroTik BGP command translation”
Click here for the second article in this series – “Cisco to MikroTik OSPF command translation”
While many commands have almost the exact same information, others are as close as possible. Since there isn’t always an exact match, sometimes you may have to run Continue reading
PQ 148: How To Monitor Cryptojacking With Paessler PRTG (Sponsored)
Today on Priority Queue, the Packet Pushers peer into the darker corners of network monitoring.
Monitoring gets you visibility. But when you can see what’s happening, you might not like what you find. That s the topic of today s sponsored show with Paessler AG, maker of PRTG network monitoring software.
Our guests are Greg Ross, Presales Systems Engineer at Paessler; and Troy Mursch, a security researcher who blogs at Bad Packets Report.
Troy discovered that cryptojacking malware called Coinhive had infected a popular Website. We’ll talk about how he used Paessler sensors to monitor the malware on the site, and to track down other infected systems.
We talk with Troy and Greg about how to use Paessler to monitor key metrics that could indicate malware. We also dig into Paessler’s capabilities for more typical network monitoring use cases.
And here’s a special offer for Packet Pushers listeners: Paessler is offering a free network security eBook. You can get it at go.paessler.com/packetpushers.
You can also get a free trail of PRTG here.
Show Links:
Free Network Security eBook – Paessler
2018 NFV Report Series Part 2: Rising roles of MANO, LSO and Assurance Available Now
 Download now to learn the latest on the MANO, LSO and Assurance market.
Download now to learn the latest on the MANO, LSO and Assurance market.
Rancher Labs Ties Future to Building a Car Around Kubernetes
 The company launched general availability of its Kubernetes-based platform that breaks from its past reliance on Docker.
The company launched general availability of its Kubernetes-based platform that breaks from its past reliance on Docker.
Sprint Shuffles Top Management Ahead of T-Mobile Acquisition
 CEO Marcelo Claure will become executive chairman of Sprint. He expects to spend a lot of time in Washington, D.C., getting regulators to approve the T-Mobile merger.
CEO Marcelo Claure will become executive chairman of Sprint. He expects to spend a lot of time in Washington, D.C., getting regulators to approve the T-Mobile merger.
Internet Society, LACNIC, and LAC-IX Partner to Strengthen IXPs in Latin America
Wednesday, 2 May 2018, the Internet Society signed a Memorandum of Understanding with the Association of Internet Exchange Points (LAC-IX) and the Latin American Registry for Internet Numbers (LACNIC) to create and strengthen Internet Exchange Points (IXPs) for a stable, secure, and open Internet and to maximise the impact of our activities across Latin America and the Caribbean.
Internet Society’s work on interconnection, traffic exchange, and IXPs not only improves local Internet service in developed regions, but also engages with the local communities that are instrumental in advancing the Internet Society’s mission. The IXP program helps develop Internet technical communities and network operators across the globe.
The Internet Society cooperates with regional organisations that lead IXP work in the field, supporting their work, promoting new IXPs where needed, and helping spread Internet Society work that is valuable to their communities.
LAC-IX and LACNIC have a unique role in promoting new IXPs, supporting existing communities, and, through them, providing the messages that contribute to a stable and scalable Internet.
This Memorandum of Understanding establishes a reference framework for cooperation mechanisms between the Parties. Plans include supporting capacity-building events, disseminating common initiatives and projects, and promoting good routing practices at traffic exchange Continue reading