The Renaissance of Quechua Language in Cyberspace
Half of the world’s languages are expected to disappear by the end of the century. This is a huge cultural loss to humanity. When we think about endangered languages, we usually consider them as part of traditions that link us to the past. From a forward-looking perspective, they mean more than cultural heritage. When a language dies, a unique vision of the world is gone forever.
Does the language we speak online matter? Studies show that it deeply affects people’s experience of the Internet. It determines how much information we can access, who we choose to connect with and how we behave in our community. Keeping languages alive is essential to shape our future. The Internet offers the greatest chance to have a public voice in response to cultural globalization, a languages renaissance.
UNESCO is convinced that multilingualism on the Internet has a key role to play in fostering pluralistic, open and inclusive knowledge societies.
A project called Siminchikkunarayku, supported by The Internet Society Peru Chapter and the Beyond the Net Funding Programme, aims to build the linguistic corpus of the southern Quechua language by collecting and digitizing 10,000 hours of speeches. The Quechua is a family Continue reading
Announcing Cumulus NetQ 1.3 — now with Kubernetes!
Today, we are thrilled to announce the availability of Cumulus NetQ 1.3. With this release, Cumulus extends its leadership in container networking insight by integrating NetQ with Kubernetes, along with our previously supported integration with Docker Swarm.
This announcement aligns perfectly with Cumulus’ mission of driving web-scale networks for the digital age with automation and agility by implementing networking with S.O.U.L. Simple. Open. Untethered. Linux. NetQ is woven deep into that S.O.U.L. strategy, which we’ll get to later in a separate blog post. For now, there is a lot to dig into here with this Kubernetes integration with NetQ, so let’s begin.
The growth & challenges with containers
Container technology is all the rage in the CD/DevOps world. Nearly 70% of the companies queried in a Portworx 2017 container adoption survey invested financially in containers at some level in 2017, leaping from 52% in 2016. 451 Research predicts containers will grow to become a $2.7BN market by 2020. That’s 3.5 times greater than the $762 million container market in 2016, with a CAGR of 40%.
The popularity of these Linux-based containers stems from their ability to dramatically improve flexibility when running Continue reading
Cisco Networking Basics: IP Addressing
In this excerpt from "Implementing Cisco Networking Solutions" from Packt, learn IP addressing fundamentals.
Pragmatic Data Center Fabrics
I always love to read the practical advice by Andrew Lerner. Here’s another gem that matches what Brad Hedlund, Dinesh Dutt and myself (plus numerous others) have been saying for ages:
One specific recommendation we make in the research is to “Build a rightsized physical infrastructure by using a leaf/spine design with fixed-form factor switches and 25/100G capable interfaces (that are reverse-compatible with 10G).”
There’s a slight gotcha in that advice: it trades implicit complexity of chassis switches with explicit complexity of fixed-form switches.
Read more ...No More Meltdowns: Cisco and Microsoft Will Use Intel’s Silicon-Level Security
![]() An integration with Cisco Tetration will combine platform telemetry with machine learning algorithms to improve threat detection.
An integration with Cisco Tetration will combine platform telemetry with machine learning algorithms to improve threat detection.
Google Kaniko Tool Wrenches on Container Privilege Concern
 The open source tool allows for the building of a container image without providing privileged root access.
The open source tool allows for the building of a container image without providing privileged root access.
Winners and Losers After ZTE Is Banned From Buying U.S. Components
 Ciena stands to be a winner because it competes with ZTE. Infinera and Nokia might benefit as well.
Ciena stands to be a winner because it competes with ZTE. Infinera and Nokia might benefit as well.
mmproxy – Creative Linux routing to preserve client IP addresses in L7 proxies
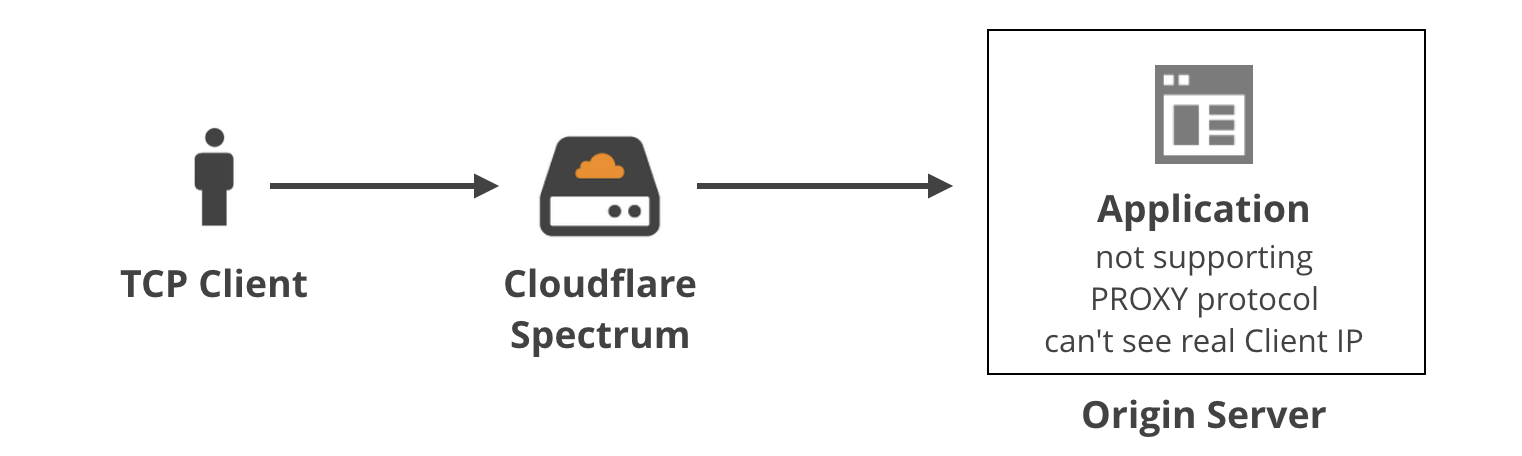
In previous blog post we discussed how we use the TPROXY iptables module to power Cloudflare Spectrum. With TPROXY we solved a major technical issue on the server side, and we thought we might find another use for it on the client side of our product.
This is Addressograph. Source Wikipedia
When building an application level proxy, the first consideration is always about retaining real client source IP addresses. Some protocols make it easy, e.g. HTTP has a defined X-Forwarded-For header[1], but there isn't a similar thing for generic TCP tunnels.
Others have faced this problem before us, and have devised three general solutions:
(1) Ignore the client IP
For certain applications it may be okay to ignore the real client IP address. For example, sometimes the client needs to identify itself with a username and password anyway, so the source IP doesn't really matter. In general, it's not a good practice because...
(2) Nonstandard TCP header
A second method was developed by Akamai: the client IP is saved inside a custom option in the TCP header in the SYN packet. Early implementations of this method weren't conforming to any standards, e.g. using option field 28 Continue reading
Two-Factor Authentication with VMware NSX-T
In a previous post, I covered how to integrate NSX-T with VMware Identity Manager (vIDM) to achieve remote user authentication and role-based access control (RBAC) for users registered with a corporate Active Directory (AD) http://blogs.vmware.com/networkvirtualization/2017/11/remote-user-auth…-rbac-with-nsx-t.html/
On this post, I’m showing how add two-factor authentication (2FA) for NSX-T administrators/operators on top of that existing integration. Two-factor authentication is a mechanism that checks username and password as usual, but adds an additional security control before users are authenticated. It is a particular deployment of a more generic approach known as Multi-Factor Authentication (MFA).
Throughout this post, I’m providing step-by-step guidance on how to use VMware Verify as that second authentication. I will also highlight what would be different if using third party mechanisms. At the end of the post, you will find a demo showing how to do the configuration and how users authenticate once 2FA is enabled.
What is VMware Verify? Let me quote what my colleague Vikas Jain wrote on this post: “VMware Verify uses modern mobile push tokens, where users get a push notification on their mobile device that they can simply accept or deny. When the user’s device does not have cellular reception, Continue reading
Microsoft’s Smith Calls for Digital Geneva Convention, Launches Cybersecurity Tech Accord
 War and the battlefield themes dominated the opening keynotes at the annual RSA Conference 2018, just a day after a joint U.S. and U.K. alert warned that Russians are targeting American and British organizations’ network infrastructure devices, such as routers.
War and the battlefield themes dominated the opening keynotes at the annual RSA Conference 2018, just a day after a joint U.S. and U.K. alert warned that Russians are targeting American and British organizations’ network infrastructure devices, such as routers.
Do We Need Regulations For IoT Security?
Security regulations for IoT probably won't make much difference--until people start getting hurt.Mirantis Launches Moonshot Based on Netflix-Developed Spinnaker
 The new platform allows the company to get into the application space and diversify operations away from the increasingly competitive infrastructure space around OpenStack and Kubernetes.
The new platform allows the company to get into the application space and diversify operations away from the increasingly competitive infrastructure space around OpenStack and Kubernetes.
OSPF Topology Transparent Zones
Anyone who has worked with OSPF for any length of time has at least heard of areas—but perhaps before diving into Topology Transparent Zones (TTZs), a short review is in order.

In this diagram, routers A and B are in area 0, routers C and D are Area Border Routers (ABRs), and routers E, F, G, H, and K are all in area 1. The ABRs, C and D, do not advertise the existence of E, F, G, H, or K to the routers in area 0, nor the links to or between any of those routers. Any reachable destinations in area 1 are advertised using a em>summary LSA, or a type 3 LSA, towards A and B. From the perspective of A and B, 100::/64 and 101::/64 would be advertised by C and D as directly connected destinations, using the cost from C and D to each of these two destinations, based on a summary LSA.
What if you wanted to place H and K in their own area, with G as an ABR, behind the existing area 1? You cannot do this in OSPF using any form of a standard flooding domain, or area. There is no way Continue reading
The Russians Are Targeting Internet Routers for Cyberattacks, Says Joint U.S., U.K. Alert
 Cisco, itself, recently issued a warning about its Smart Install client, saying it was vulnerable to cyber attacks by nation-state actors.
Cisco, itself, recently issued a warning about its Smart Install client, saying it was vulnerable to cyber attacks by nation-state actors.
Cisco Extends Its Intent-based Networking to IoT
 Cisco expects the ratio of IT people to devices to increase from 1 to 1,000 to 1 to 100,000 in just a couple of years.
Cisco expects the ratio of IT people to devices to increase from 1 to 1,000 to 1 to 100,000 in just a couple of years.