Short Take – Cisco Disaggregation Announcement
In this Network Collective short take, Jordan Martin shares his thoughts on the recent announcement from Cisco that they will be offering disaggregated solutions. Has Cisco seen the light? Will Cisco abandon hardware completely? Or are the doing all of this for other reasons?
Related Episodes:
The post Short Take – Cisco Disaggregation Announcement appeared first on Network Collective.
Power Failure Leaves Brazilian Internet In The Dark

On Wednesday, March 21, a massive power failure impacted large parts of northern Brazil, leaving tens of millions of people without electricity. Beginning at about 3:40pm local time (18:40 UTC), the outage was reportedly due to the failure of a transmission line near the Belo Monte hydroelectric station.
As occurred in a major power outage in Brazil in 2009, this power failure had a measureable impact on the country’s Internet. This is illustrated below through graphs from Oracle Dyn’s Internet Intelligence team based on BGP and traceroute data, as well as graphs from Akamai’s mPulse service, based on end user Web traffic.
The graphic below depicts the counts of available networks (lower graph) and unstable networks (upper graph) for Brazil in the latter half of March 21. The number of unstable networks spikes around 18:40 UTC as routers of ISPs in Brazil began re-routing traffic away from disabled connections, while the lower graph shows that the corresponding drop in available networks (i.e. routed prefixes) was minor when compared to the total number routes that define the Internet of Brazil.
In addition to aggregating BGP routing information from around the globe, the Internet Intelligence team also performs millions of Continue reading
Data Center Routing with RIFT on Software Gone Wild
Years ago Petr Lapukhov decided that it’s a waste of time to try to make OSPF or IS-IS work in large-scale data center leaf-and-spine fabrics and figured out how to use BGP as a better IGP.
In the meantime, old-time routing gurus started designing routing protocols targeting a specific environment: highly meshed leaf-and-spine fabrics. First in the list: Routing in Fat Trees (RIFT).
Read more ...Mininet weathermap
Mininet dashboard is a real-time dashboard displaying traffic information from Mininet virtual networks. The screen capture demonstrates the real-time network weather map capability that was recently added to the dashboard. The torus topology is displayed and link widths are updated every second to reflect traffic. In this example a large flow between switches s1x1 and s3x3 is routed via s1x3.The network was created using the following Mininet command:
sudo mn --custom=sflow-rt/extras/sflow.py --link tc,bw=10 \In the screen capture above you can clearly see the large flow traversing switches, s4, s3, s2, s1, s9, s13, and s15 in a tree topology. The network was created using the following command:
--topo torus,3,3 --switch ovsbr,stp=1 --test iperf
sudo mn --custom sflow-rt/extras/sflow.py --link tc,bw=10 \The screen capture above shows a large flow traversing switches s1, s2, s3, and s4 in a linear topology. The network was created using the following command:
--topo tree,depth=4,fanout=2 --test iperf
sudo mn --custom sflow-rt/extras/sflow.py --link tc,bw=10 \It's also easy to create Custom Topologies. The following command creates the example custom topology, topo-2sw-2host.py, that ships with Mininet:
--topo linear,4 --test iperf
sudo mn --custom ~/mininet/custom/topo-2sw-2host.py,sflow-rt/extras/sflow.py Continue reading
Service Providers Get a Little Testy With Vendors Regarding SDN
 Unfortunately for vendors, they don’t have the luxury of sitting on stage and defending their point of view. But vendors aren’t going to provide products based on open source unless there’s money to be made.
Unfortunately for vendors, they don’t have the luxury of sitting on stage and defending their point of view. But vendors aren’t going to provide products based on open source unless there’s money to be made.
Meet the APRICOT 2018 Fellows
The Asia Pacific Regional Internet Conference on Operational Technologies (APRICOT) is an annual event that brings together Internet engineers and networking experts, government representatives, Internet business leaders, and other interested parties from around the world to learn from training workshops and tutorials, attend technical presentations, discuss policies, and extend social and professional networks with like-minded peers. This year’s event was held in Kathmandu, Nepal from 19-28 February.
The Internet Society Asia-Pacific Bureau has a long-term partnership with APRICOT and proudly sponsors its fellowship program, providing financial support for individuals from developing economies to attend the event, and to contribute to discussions about Internet operations, technologies and development. This year the Internet Society sponsored a total of 13 fellows to APRICOT 2018, split between the technical workshops and the conference week, depending on their areas of interest. 75% of these fellows were females, endorsing our focus to inspire and facilitate the participation of women in the technology sector and to #ShineTheLight!
We had an opportunity to meet some of these fellows, to know more about them and their experience as a fellow.
Athirah Rosli is a Doctoral Researcher at Universiti Utara Malaysia, and also a committee member of the ISOC Malaysia Continue reading
Three more US data centers! Jacksonville, Memphis and Tallahassee


Good things come in threes! Following the launch of three data centers each in the Baltics (Riga, Tallinn, Vilnius) and in the Canadian Prairies (Calgary, Saskatoon, Winnipeg), we're thrilled to announce three new data centers in the Southern United States!
Located in Jacksonville (Florida), Memphis (Tennessee), and Tallahassee (Florida), they represent the 146th, 147th and 148th cities across our growing global network, and our 40th, 41st and 42nd cities just in North America. They join existing Cloudflare facilities in the US, including other Florida / Tennessee deployments such as Miami, Tampa and Nashville. Just in March, we've added deployments in 28 new cities worldwide, which help reduce latency to millions of Internet properties using Cloudflare, while expanding our capacity to withstand new and familiar attacks.
 Photo of Jacksonville Beach by Lance Asper / Unsplash
Photo of Jacksonville Beach by Lance Asper / Unsplash
Whether you're doing the Memphis Main Street Crawl, experiencing history through a visit to Tallahassee's Mission San Luis de Apalachee, or just relaxing by the stunning beaches of Jacksonville, you'll be close to the nearest Cloudflare data center.
The Cloudflare Global Anycast Network
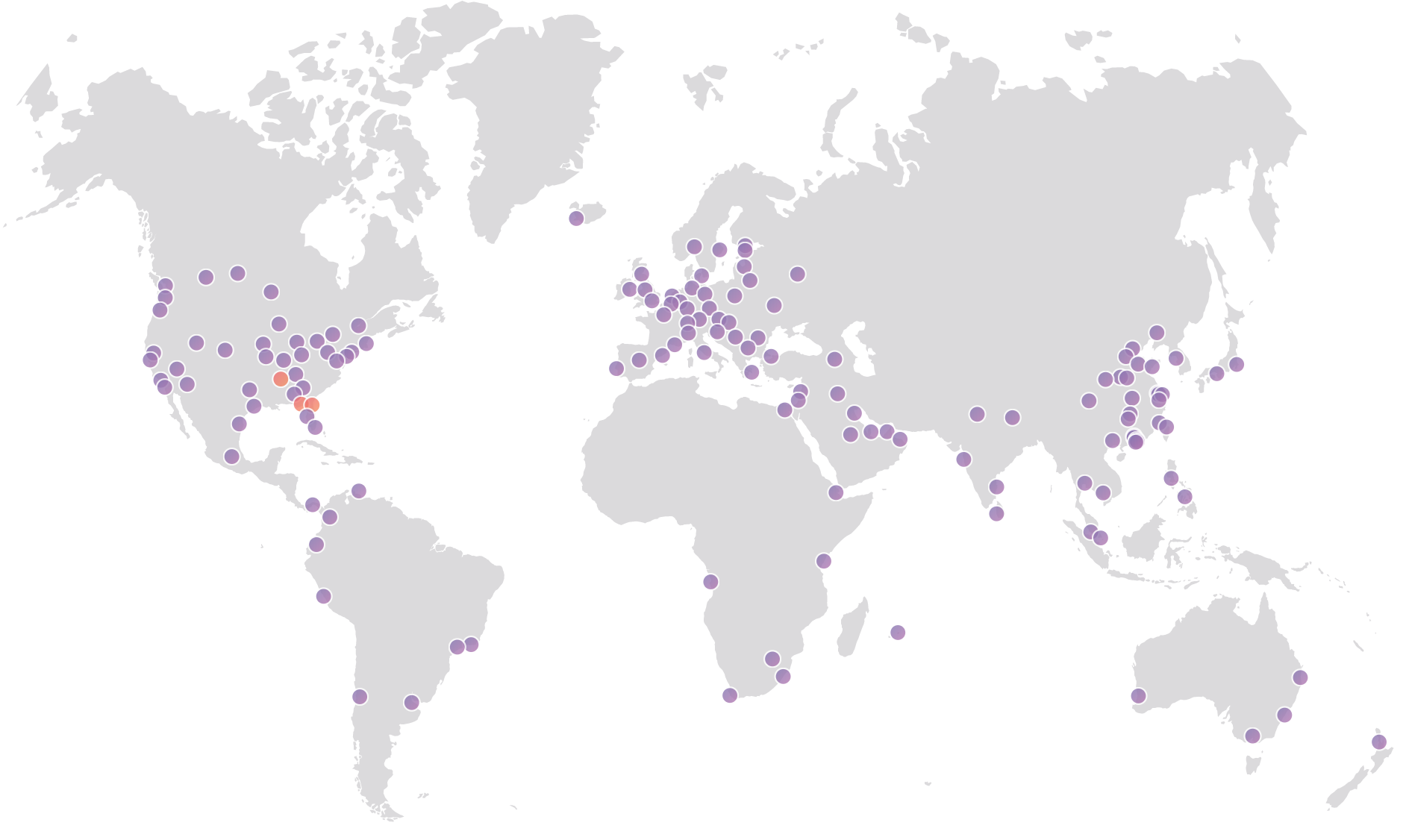
This map reflects the network as of the publish date of this blog post. For the most up to date directory Continue reading
SPIFFE, SPIRE Join Cloud Native Computing Foundation Sandbox
 The open source workload identity framework projects are modeled after similar systems at Google, Netflix, and Twitter.
The open source workload identity framework projects are modeled after similar systems at Google, Netflix, and Twitter.
Vint Cerf Envies the Modern ‘Internet Adventure’ with Open Routing, Switching
 The disaggregation of the control plane and data plane with open interfaces feels a bit like the free-wheeling days of the early internet.
The disaggregation of the control plane and data plane with open interfaces feels a bit like the free-wheeling days of the early internet.
Cloudflare Arrives in the Canadian Prairies! Welcome Calgary, Saskatoon and Winnipeg


We just turned up Calgary, Saskatoon and Winnipeg - Cloudflare’s 143rd, 144th, and 145th data centers. This brings our Canadian presence to six cities, joining Toronto, Montreal and Vancouver. I grew up just outside of Saskatoon, so I couldn’t be happier that Cloudflare’s network has expanded to the Canadian Prairies. My parents still live there and I just booked flights to go and visit them this summer. When I tell people that I grew up in Saskatchewan, most people don’t know a lot about the region, so I wanted to share some of my favorite things about the region, starting from west to east:
- Calgary was home to the 1988 Winter Olympics and is a 90 minute drive from Banff, an incredible National Park that is absolutely worth visiting. Calgary has grown quickly over the last twenty years because of all the natural resources, including oil and gas. They host a famous rodeo, Calgary Stampede, for 10 days every summer. Definitely something to add to your bucket list. With Cloudflare’s new deployment in Calgary, we’ll make the Internet even faster for visitors. Hello Calgary!
-
About 1 million people live in the province of Saskatchewan. Saskatoon is the Continue reading
Rewind & recap: OCP Summit 2018
As you probably know, Cumulus Networks is an active contributor and enthusiastic member of the OCP community. So naturally, we couldn’t bear to miss OCP Summit 2018! The summit was held in San Jose from March 20th – 21st, and believe us, if you’re into open source anything, it was THE place to be. From BoF sessions to engineering workshops and everything in-between, there’s so much to talk about — but we’ll spare you an essay-length article and keep this short blog limited to our absolute favorite Cumulus OCP Summit highlights from the event. So whether you’re an OCP fan that couldn’t make it or you’re an attendee that wants to reminisce, check out these stellar moments from OCP Summit 2018.
Cumulus’ OCP projects
It was great to hear Omar Baldonado from Facebook give Backpack a shoutout during his keynote address. With the support of OCP, we’ve teamed up our OS with Celestica’s hardware to bring this project to fruition, and what better place to highlight this venture than at OCP Summit? As Baldonado points out, “Cumulus also has been a very long standing partner and contributor and driver within the OCP community,” and we intend to continue those efforts. Continue reading
Kathy Brown’s Op-Ed in the Hill Times: Canada’s Unique Opportunity to Lead the Future of the Internet
Kathy Brown, CEO of the Internet Society, recently penned an Op-Ed for Canada’s the Hill Times calling for a multistakeholder approach to Internet governance: “an approach that is collaborative, one that engages the entire Internet community.” According to Brown, “The time has come to expand this inclusive model of governance to more places around the world.”
“No one party, government, corporation, or non-profit controls the Internet and we are all better for it. Nor does any one party have the knowledge or the ability to identify the solutions to these complex policy challenges. It has been this approach—what we call the multistakeholder model—that has allowed humankind’s most advanced and powerful communications tool to spread so far and so fast.”
She cites the partnership between the Internet Society, Innovation, Science and Economic Development, the Canadian Internet Registration Authority, CANARIE, and CIPPIC as an example of the multistakeholder approach working successfully. “[Canada] is addressing cybersecurity head-on by working with the Internet Society to engage the Canadian Internet community in a process to develop recommendations to secure the Internet of Things.”
Read the entire Op-Ed, then learn how you can participate in the Collaborative Governance Project, Continue reading








