Hedge 213: Batfish with Ratul Mahajan
Network configuration analysis has always been the domain of commercial-grade software. Batfish changes all that with an open source, community-supported tool that can find errors and guarantees the correctness of planned or current network configurations. Ratul Mahajan joins Tom Ammon and Russ White to talk about this new tool, its capabilities, and the importance of network configuration analysis.
download
You can find out more about Batfish at the project home page, and in this paper by Ratul.
HN721: Goodbye Network Cowboys, Hello Total Network Operations
The days of network cowboy heroism are over… or at least they need to be. It’s time for network engineering to grow up and standardize how networks are built. Not only will this make life easier for all of us as we inherit networks when we move from company to company, but it’s the only... Read more »Public Videos: 400 Gigabit Ethernet

The 400 Gigabit Ethernet videos with Mark Nowell and Lukas Krattiger are now public. Enjoy!
Monitoring machine learning models for bot detection

Cloudflare’s Bot Management is used by organizations around the world to proactively detect and mitigate automated bot traffic. To do this, Cloudflare leverages machine learning models that help predict whether a particular HTTP request is coming from a bot or not, and further distinguishes between benign and malicious bots. Cloudflare serves over 55 million HTTP requests per second — so our machine learning models need to run at Cloudflare scale.
We are constantly making improvements to the models that power Bot Management to ensure they are incorporating the latest threat intelligence. This process of iteration is an important part of ensuring our customers stay a step ahead of malicious actors, and it requires a rigorous process for experimentation, deployment, and ongoing observation.
We recently shared an introduction to Cloudflare’s approach to MLOps, which provides a holistic overview of model training and deployment processes at Cloudflare. In this post, we will dig deeper into monitoring, and how we continuously evaluate the models that power Bot Management.
Why monitoring matters
Before bot detection models are released, we undergo an extensive model testing/validation process to ensure our detections perform as expected. Model performance is validated across a wide number of web traffic Continue reading
Satellite Operators Team to Pursue Direct-to-Device Opportunity
New mobile association seeks help developing integrated terrestrial and non-terrestrial network (NTN) services for smartphones and IoT devices worldwide.KU048: Platforms in the Clouds
What are we talking about when we are all talking about private clouds? On-prem? Hybrid? Virtualization? Where does hardware fit into it all– and would younger engineers even know what to do with a physical piece of hardware? Driven by Broadcom’s acquisition of VMare and the anticipated rising costs of VMare licenses, enterprises are exploring... Read more »Safeguarding your brand identity: Logo Matching for Brand Protection
In an era dominated by digital landscapes, protecting your brand’s identity has become more challenging than ever. Malicious actors regularly build lookalike websites, complete with official logos and spoofed domains, to try to dupe customers and employees. These kinds of phishing attacks can damage your reputation, erode customer trust, or even result in data breaches.
In March 2023 we introduced Cloudflare’s Brand and Phishing Protection suite, beginning with Brand Domain Name Alerts. This tool recognizes so-called “confusable” domains (which can be nearly indistinguishable from their authentic counterparts) by sifting through the trillions of DNS requests passing through Cloudflare’s DNS resolver, 1.1.1.1. This helps brands and organizations stay ahead of malicious actors by spotting suspicious domains as soon as they appear in the wild.
Today we are excited to expand our Brand Protection toolkit with the addition of Logo Matching. Logo Matching is a powerful tool that allows brands to detect unauthorized logo usage: if Cloudflare detects your logo on an unauthorized site, you receive an immediate notification.
The new Logo Matching feature is a direct result of a frequent request from our users. Phishing websites often use official brand logos as part of their facade. In Continue reading
D2C233: Pinning Down Private Clouds
What are we talking about when we are all talking about private clouds? On-prem? Hybrid? Virtualization? Where does hardware fit into it all– and would younger engineers even know what to do with a physical piece of hardware? Driven by Broadcom’s acquisition of VMare and the anticipated rising costs of VMare licenses, enterprises are exploring... Read more »Maui Teaches Us Why We Need to Change Our Data Protection Strategies
Needing to protect all data from disasters while bringing costs down means a one-size-fits-all DR strategy no longer works.Welcome to Network Automation Nerds
Hi, I’m Eric Chou, and welcome to the Network Automation Nerds podcast, the newest addition to the Packet Pushers family. This is your audio destination for network engineers and infrastructure professionals who are on a mission to build stronger, more resilient systems through the art of network automation. Join us as we connect with a... Read more »Shaping the future: Cloudflare’s service partner strategy

Introduction and partner landscape
Cloudflare’s global network spans over 310 cities in more than 120 countries, and interconnects with 13,000 networks globally, including major ISPs, cloud services, and enterprises. This network serves as a globally distributed foundation from which Cloudflare offers a broad product portfolio spanning everything from core Internet services like security, performance, and reliability — to web development, AI, corporate access management, creative products, and more.
The diversity of our products is reflected in our millions of customers, who span a dizzying array of industries and institutions in nearly every country around the world. This incredible diversity has meant a lot of specialisation, as Cloudflare’s adaptable product suite is fitted for each use case. Many customers are keen to have a partner to help them ensure they are getting everything they can out of Cloudflare. And they’d like to do it in the language of their choice, with partners who are familiar with the industries and regions they operate in.
This is why Cloudflare has for many years invested in our Partner Services programs, and has made a concerted effort to scout and partner with the world’s leading service providers who can deliver Cloudflare solutions to the Continue reading
BGP Labs: Session Templates
Configuring an IBGP session on a route reflector takes a half-dozen parameters, starting with the remote BGP AS number (equal to the local one), remote IP address, and the source IP address or interface. You might have to specify the propagation of BGP communities and an MD5 password, and you will definitely have to specify that the BGP neighbor is a route reflector client.
Wouldn’t it be nice if you could group those parameters into a template and apply the template to a neighbor? Most BGP implementations have something along those lines. That feature could be called a session template or a peer group, and you can practice it in the next BGP lab exercise.
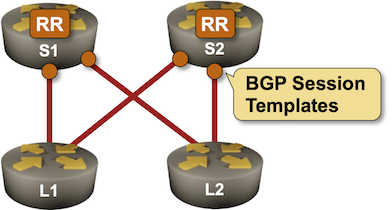
BGP Labs: Session Templates
Configuring an IBGP session on a route reflector takes a half-dozen parameters, starting with the remote BGP AS number (equal to the local one), remote IP address, and the source IP address or interface. You might have to specify the propagation of BGP communities and an MD5 password, and you will definitely have to specify that the BGP neighbor is a route reflector client.
Wouldn’t it be nice if you could group those parameters into a template and apply the template to a neighbor? Most BGP implementations have something along those lines. That feature could be called a session template or a peer group, and you can practice it in the next BGP lab exercise.

Proxmox Cloud-Init with Terraform and SaltStack
https://codingpackets.com/blog/proxmox-cloud-init-with-terraform-and-saltstack
PP001: WPA3: Everything You Wanted To Know But Were Afraid To Ask
It’s time to make the switch from WPA2 to WPA3. We cover how to do it and what migration challenges to be prepared for no matter what WLAN you are dealing with (open, passphrase, or 802.1x) . We also discuss what features make WPA3 an improvement over WPA2, particularly the replacement of PSK with SAE.... Read more »HS065: Calculating the Value of Telco AIOps (Sponsored)
AI and automation are hot topics in telco, but not all projects are created equal in terms of the bottom-line value. We dive into how to calculate total value, and discuss why the area of assurance looks set to generate the most value. We provide key questions to ask when considering what AIOps to add... Read more »How Cisco Sees Silicon One Easing Network Convergence and Helping with AI
With the rise of AI and its massive impact on networking, Cisco has pivoted swiftly to enable customers to utilize its converged networks to run taxing AI apps.Enhancing Zaraz support: introducing certified developers
Setting up Cloudflare Zaraz on your website is a great way to load third-party tools and scripts, like analytics or conversion pixels, while keeping things secure and performant. The process can be a breeze if all you need is just to add a few tools to your website, but If your setup is complex and requires using click listeners, advanced triggers and variables, or, if you’re migrating a substantial container from Google Tag Manager, it can be quite an undertaking. We want to make sure customers going through this process receive all the support they need.
Historically, we've provided hands-on support and maintenance for Zaraz customers, helping them navigate the intricacies of this powerful tool. However, as Zaraz's popularity continues to surge, providing one-on-one support has become increasingly impractical.
Companies usually rely on agencies to manage their tags and marketing campaigns. These agencies often have specialized knowledge, can handle diverse client needs efficiently, scale resources as required, and may offer cost advantages compared to maintaining an in-house team. That's why we're thrilled to announce the launch of the first round of certified Zaraz developers, aligning with the way other Tag Management software works. Our certified developers have undergone an intensive Continue reading