SDxCentral’s Weekly Roundup — February 23, 2018
 Qualcomm increases NXP offer, making Broadcom change its offer; Google pushes cloud IoT to general availability.
Qualcomm increases NXP offer, making Broadcom change its offer; Google pushes cloud IoT to general availability.
Juniper Names its First Contrail SD-WAN Service Provider Customer
 Contrail SD-WAN includes hardware and software.
Contrail SD-WAN includes hardware and software.
What’s Your #TechConfession?

Think back to the first moment you fell in love with technology. Was it love at first deployment? What about developing code to trick your school’s bell system into letting your class out early? If you love all things technology, or you’re a technologist, then you should definitely put #TechConfessions, the podcast and YouTube playlist, on your radar.
#TechConfessions is a weekly podcast and web series that uncovers the deep, dark tech secrets of some of high tech’s finest minds. The series looks to expose the inner thoughts and forgotten stories of tech professionals. Hear from top tech pros as they divulge the early beginnings of their tech careers and proclaim their favorite software-defined moments. Get insights into what makes these tech leaders tick, and discover their long-burning passion for all things tech.
Director of Influence Marketing at VMware, Amy Lewis, one of the hosts of #TechConfessions, gives a voice to the professionals witnessing industry changes. Going from a hardware to a software state of mind happens differently for everyone. As the host of #TechConfessions, Amy digs deep to get the real backstory behind each individual’s transition into the world of software.
So far, season one Continue reading
2018 NFV Report Series Survey: Love NFV or Hate NFV? Share Your Thoughts with Us.
 Take the 2018 NFV Report Series Survey and enter to win one of two $300 Gift Cards redeemable at various retailers including Amazon, Target, Visa Virtual Card, etc.
Take the 2018 NFV Report Series Survey and enter to win one of two $300 Gift Cards redeemable at various retailers including Amazon, Target, Visa Virtual Card, etc.
Creating a single pane of glass for your multi-cloud Kubernetes workloads with Cloudflare
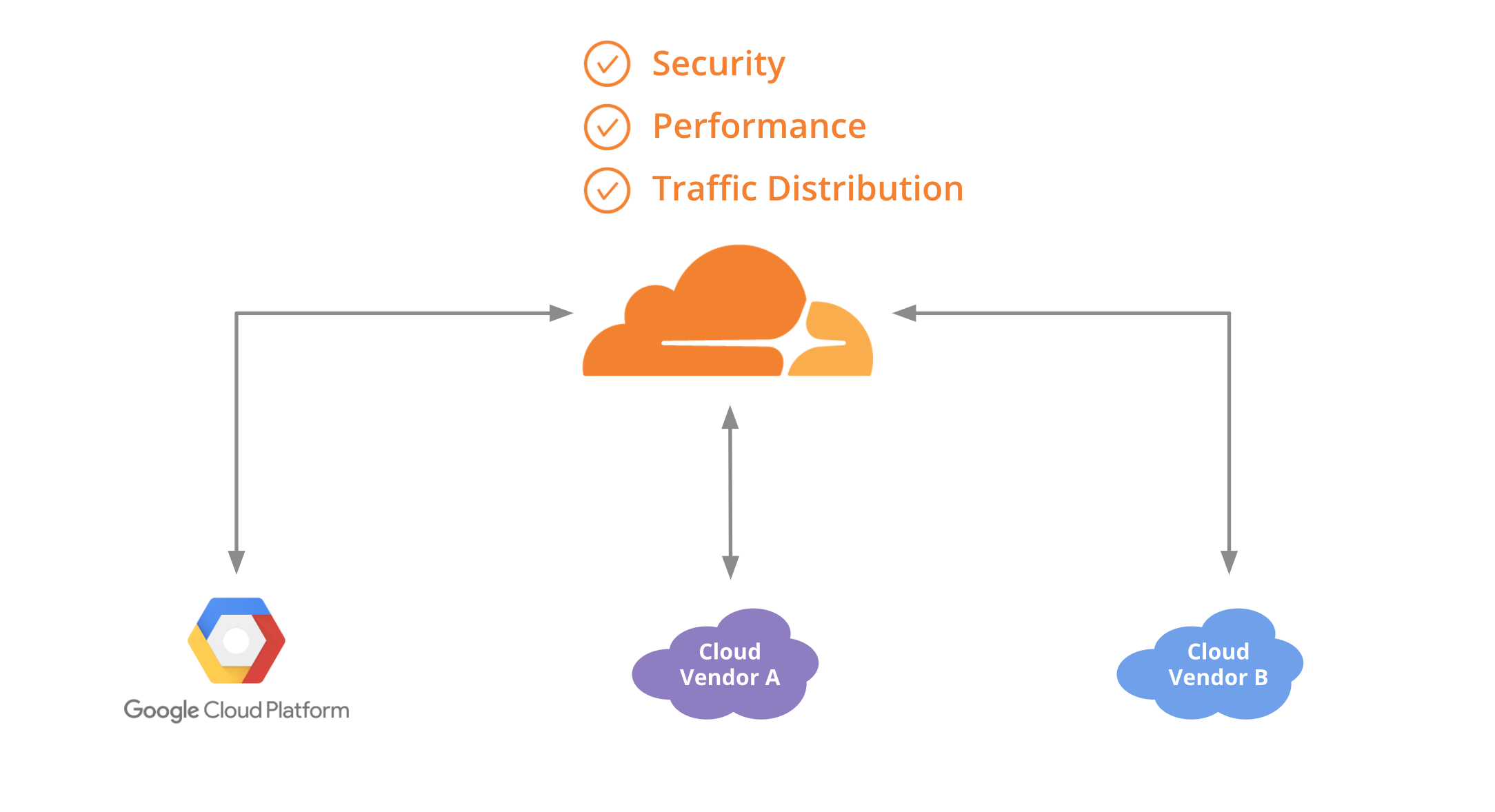
(This is a crosspost of a blog post originally published on Google Cloud blog)
One of the great things about container technology is that it delivers the same experience and functionality across different platforms. This frees you as a developer from having to rewrite or update your application to deploy it on a new cloud provider—or lets you run it across multiple cloud providers. With a containerized application running on multiple clouds, you can avoid lock-in, run your application on the cloud for which it’s best suited, and lower your overall costs.
If you’re using Kubernetes, you probably manage traffic to clusters and services across multiple nodes using internal load-balancing services, which is the most common and practical approach. But if you’re running an application on multiple clouds, it can be hard to distribute traffic intelligently among them. In this blog post, we show you how to use Cloudflare Load Balancer in conjunction with Kubernetes so you can start to achieve the benefits of a multi-cloud configuration.
To continue reading follow the Google Cloud blog here or if you are ready to get started we created a guide on how to deploy an application using Kubernetes on GCP and AWS Continue reading
The Cost of Cybercrime
Most people paying attention would expect that the cost of cybercrime has gone up in recent years. But a new report has put a number on it: Worldwide cybercrime costs an estimated $600 billion USD a year.
That’s up from $500 billion USD in 2014, the last time security vendor McAfee and think tank the Center for Strategic and International Studies released a similar study. The new estimate amounts to 0.8 percent of global GDP, up from 0.7 percent in 2014.
“Cybercrime is relentless, undiminished, and unlikely to stop,” writes report author James Lewis, senior vice president at CSIS. “It is just too easy and too rewarding, and the chances of being caught and punished are perceived as being too low.”
Lewis points to poorly-protected IoT devices as a particular problem. Insecure IoT devices “provide new, easy approaches to steal personal information or gain access to valuable data or networks,” he writes. They also power botnets that can create massive denial-of-service attacks.
Among the other reasons for the growth in the cost of cybercrime:
- Cybercriminals are embracing new attack technologies.
- Many new Internet users come from countries with weak cybersecurity.
- Online crime is becoming easier through cybercrime-as-a-service Continue reading
Short Take – Breaking Things
Should you be breaking things intentionally on your network? The idea might sound preposterous to some, but in this short take Russ White explains how intentional failures can make your network more resilient.
The post Short Take – Breaking Things appeared first on Network Collective.
Cisco and Rackspace Team Up on Multi-Cloud Security
 The managed cloud provider deploys more than 22,000 Cisco firewalls.
The managed cloud provider deploys more than 22,000 Cisco firewalls.
Networking Career: Taking the Road Less Traveled
The traditional certification route for NetOps is giving way to automation and coding skills.
Why Is Container Security So Difficult?
 IT departments want containers to make their lives easier, not harder.
IT departments want containers to make their lives easier, not harder.
EVPN with MPLS Data Plane in Data Centers
Mr. Anonymous (my most loyal reader and commentator) sent me this question as a comment to one of my blog posts:
Is there any use case of running EVPN (or PBB EVPN) in DC with MPLS Data Plane, most vendors seems to be only implementing NVO to my understanding.
Sure there is: you already have MPLS control plane and want to leverage the investment.
Read more ...Kathmandu, Nepal is data center 123
We said that we would head to the mountains for Cloudflare’s 123rd data center, and mountains feature prominently as we talk about Kathmandu, Nepal, home of our newest deployment and our 42nd data center in Asia!
Five and three quarter key facts to get started:
- Nepal is home to the highest mountain in the world.
- Kathmandu has more UNESCO heritage sites in its immediate area than any other capital!
- The Nepalese flag isn’t a rectangle. It’s not even close!
- Nepal has never been conquered or ruled by another country.
- Kathmandu, Nepal is where Cloudflare has placed its 123rd data center.
- Nepal’s timezone is 5 hours 45 minutes ahead of GMT.
Mountains
The mountainous nation of Nepal is home to Mount Everest, the highest mountain in the world, known in Nepali as Sagarmāthā. Most of us learn that at school; however there’s plenty of other mountains located in Nepal. Here’s the ones above 8,000 meters (extracted from the full list) to get you started:
- Mount Everest at 8,848 meters
- Kanchenjunga at 8,586 meters
- Lhotse at 8,516 meters
- Makalu at 8,463 meters
- Cho Oyu at 8,201 meters
- Dhaulagiri I at 8,167 meters
- Manaslu at 8,156 meters
- Annapurna I at 8,091 meters
Viewing Cisco Proximity with SpectrumView
I wanted to share a quick trick for troubleshooting Cisco Proximity. For those that haven’t stumbled onto this particular technology, Proximity is a feature in Spark Connected and Traditional Cisco Video Endpoints that provides a pairing channel for screen sharing. Specifically, the codec announces its presence and connection information via 22khz audio stream. The client device then uses that connection information to make a connection over the network and share the screen with the codec. Since 22khz is beyond what the human ear can hear, there is a need for some other tool to check for its presence.
The tool I use to check for the pairing channel presence is SpectrumView and is available in the Apple App Store.
There are a couple options that need to be manually configured before the tool displays the higher frequency used for the pairing process:
- Recording – Audio Sampling Rate 48000
- Display – This may be necessary to adjust if you don’t see anything. I typically set mine to about 15dB

With the proper settings and within range of a proximity enable device, some output should be visible just above 20kHz.

Disclaimer: This article includes the independent thoughts, opinions, commentary or technical Continue reading
Viewing Cisco Proximity with SpectrumView
I wanted to share a quick trick for troubleshooting Cisco Proximity. For those that haven’t stumbled onto this particular technology, Proximity is a feature in Spark Connected and Traditional Cisco Video Endpoints that provides a pairing channel for screen sharing. Specifically, the codec announces its presence and connection information via 22khz audio stream. The client device then uses that connection information to make a connection over the network and share the screen with the codec. Since 22khz is beyond what the human ear can hear, there is a need for some other tool to check for its presence.
The tool I use to check for the pairing channel presence is SpectrumView and is available in the Apple App Store.
There are a couple options that need to be manually configured before the tool displays the higher frequency used for the pairing process:
- Recording – Audio Sampling Rate 48000
- Display – This may be necessary to adjust if you don’t see anything. I typically set mine to about 15dB

With the proper settings and within range of a proximity enable device, some output should be visible just above 20kHz.

Disclaimer: This article includes the independent thoughts, opinions, commentary or technical Continue reading





