Large drop in traffic from the Democratic Republic of Congo
It is not uncommon for countries around the world to interrupt Internet access for political reasons or because of social unrest. We've seen this many times in the past (e.g. Gabon, Syria, Togo).
Today, it appears that Internet access in the Democratic Republic of Congo has been greatly curtailed. The BBC reports that Internet access in the capital, Kinshasa was cut on Saturday and iAfrikan reports that the cut is because of anti-Kabila protests.
Our monitoring of traffic from the Democratic Republic of Congo shows a distinct drop off starting around midnight UTC on January 21, 2018. Traffic is down to about 1/3 of its usual level.
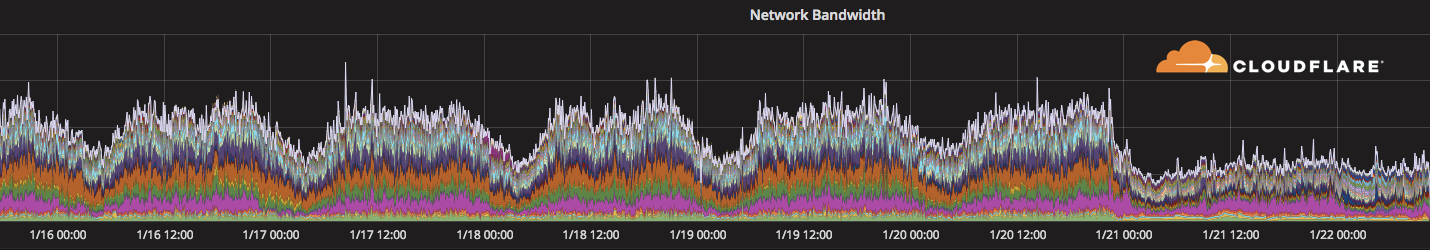
We'll update this blog once we have more information about traffic levels.
CCDE Training in Istanbul on November 2017 – Feedbacks
CCDE Training in Istanbul on November 2017. It was 5 days , almost 50 hours training. It was very intense and the attendees got tried but enjoyed too, as you will see their feedbacks in the below video. None of these guys attended CCDE Practical exam on November, some of them will attempt on February 2018 […]
The post CCDE Training in Istanbul on November 2017 – Feedbacks appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
CCDE Training in Istanbul on November 2017 – Feedbacks
CCDE Training in Istanbul on November 2017. It was 5 days , almost 50 hours training. It was very intense and the attendees got tried but enjoyed too, as you will see their feedbacks in the below video. None of these guys attended CCDE Practical exam on November, some of them will attempt on February 2018 …
Continue reading "CCDE Training in Istanbul on November 2017 – Feedbacks"
The post CCDE Training in Istanbul on November 2017 – Feedbacks appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
CCDE Training in Istanbul on November 2017 – Feedbacks
CCDE Training in Istanbul on November 2017. It was 5 days , almost 50 hours training. It was very intense and the attendees got tried but enjoyed too, as you will see their feedbacks in the below video. None of these guys attended CCDE Practical exam on November, some of them will attempt on February 2018 …
Continue reading "CCDE Training in Istanbul on November 2017 – Feedbacks"
The post CCDE Training in Istanbul on November 2017 – Feedbacks appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
BGP RR (Route Reflector) in EBGP
Is BGP RR used in EBGP ? You might think I mean IBGP , not EBGP or I mean BGP Route Server, not BGP Route Reflector but no I really mean BGP RR (Route Reflector). If you are reading this post, for sure you know what is BGP Route Reflector and it is used for […]
The post BGP RR (Route Reflector) in EBGP appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
BGP RR (Route Reflector) in EBGP
Is BGP RR used in EBGP ? You might think I mean IBGP , not EBGP or I mean BGP Route Server, not BGP Route Reflector but no I really mean BGP RR (Route Reflector). If you are reading this post, for sure you know what is BGP Route Reflector and it is used for …
Continue reading "BGP RR (Route Reflector) in EBGP"
The post BGP RR (Route Reflector) in EBGP appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
BGP RR (Route Reflector) in EBGP
Is BGP RR used in EBGP ? You might think I mean IBGP , not EBGP or I mean BGP Route Server, not BGP Route Reflector but no I really mean BGP RR (Route Reflector). If you are reading this post, for sure you know what is BGP Route Reflector and it is used for …
Continue reading "BGP RR (Route Reflector) in EBGP"
The post BGP RR (Route Reflector) in EBGP appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Synchronize Network Management Parameters across Network Devices
While I have stock homework assignments prepared for every module of the Building Network Automation Solutions online course I always encourage the students to pick a challenge from their production network and solve it during the course.
Pavel Rovnov decided to focus on consistency of network management parameters (NTP, SNMP, SSH and syslog configuration) across Extreme and Cumulus switches, Fortinet firewalls and several distributions of Linux.
Read more ...CCDE Practical/Lab Exam Result Policy
Many of my students have been asking whether CCDE Practical/Lab Exam Result policy is still the same. As you might know after CCDE 2017 May exam cancellation , practical exam results can be learned after 8 to 12 weeks. This mean, if you attend CCDE Practical exam, you cannot learn the result (Pass or fail) […]
The post CCDE Practical/Lab Exam Result Policy appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
CCDE Practical/Lab Exam Result Policy
Many of my students have been asking whether CCDE Practical/Lab Exam Result policy is still the same. As you might know after CCDE 2017 May exam cancellation , practical exam results can be learned after 8 to 12 weeks. This mean, if you attend CCDE Practical exam, you cannot learn the result (Pass or fail) …
Continue reading "CCDE Practical/Lab Exam Result Policy"
The post CCDE Practical/Lab Exam Result Policy appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
CCDE Practical/Lab Exam Result Policy
Many of my students have been asking whether CCDE Practical/Lab Exam Result policy is still the same. As you might know after CCDE 2017 May exam cancellation , practical exam results can be learned after 8 to 12 weeks. This mean, if you attend CCDE Practical exam, you cannot learn the result (Pass or fail) …
Continue reading "CCDE Practical/Lab Exam Result Policy"
The post CCDE Practical/Lab Exam Result Policy appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Telecom Operator Network Design Training
I missed writing , missed writing a post lot on the website specifically !. Because I know you are reading right now and wonder where I have been. I just checked and seen that my last post was on October 26. More than 2 months , I didn’t share anything on the website. I […]
The post Telecom Operator Network Design Training appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Telecom Operator Network Design Training
I missed writing , missed writing a post lot on the website specifically !. Because I know you are reading right now and wonder where I have been. I just checked and seen that my last post was on October 26. More than 2 months , I didn’t share anything on the website. I …
Continue reading "Telecom Operator Network Design Training"
The post Telecom Operator Network Design Training appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Telecom Operator Network Design Training
I missed writing , missed writing a post lot on the website specifically !. Because I know you are reading right now and wonder where I have been. I just checked and seen that my last post was on October 26. More than 2 months , I didn’t share anything on the website. I …
Continue reading "Telecom Operator Network Design Training"
The post Telecom Operator Network Design Training appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Network Command Reference
This page serves as a command reference and comparison of how to get information from the CLI across multiple networking vendors. ARP Show ARP Table Cisco show ip arp Arista show ip arp Juniper show arp Cumulus ip...continue reading
CCIE SP Written and Lab Content Updates v4.1
For those who may not have heard, Cisco recently updated their blueprint for the CCIE Service Provider Written and Lab Exams. According to Cisco, only about 10% of the overall blueprint has changed and topics on 4.1 will be similar to those on 4.0. Read on to learn more.
Domain Changes:
4.1 domain topics are almost exactly the same as 4.0 topics. The main difference in domains is that domains 1 and 3 (service provider architecture and evolution and service provider base services) have been merged into one domain. While other domain topics did not change, slight shifts were made to domain weights.
Weighting of Domains:
Topic changes within the Domains:
- Domain 1 (Core Routing): No topics were added or removed within this domain, but some items were moved, rephrased, or merged into one single item.
- Domain 2 (Service Provider Architecture and Services) now holds tasks of the original domain 1 and 3. Other items that were part of domain 1, such as software architecture, mobility node functions, and virtualization concepts, were rephrased to better define their scope.
- Domain 3 (Access and Aggregation) had a few topics items removed.
- Domain 4 (High Availability and Continue reading
Show 373: Cisco’s Model-Driven Telemetry (Sponsored)
On today's sponsored Weekly Show, the Packet Pushers talk with Cisco about using model-driven telemetry for improved operations and troubleshooting. The post Show 373: Cisco’s Model-Driven Telemetry (Sponsored) appeared first on Packet Pushers.Weekend Reads 011918: IoT, Cyberthreat Thinking, and Techlash
Deputy Attorney General Rosenstein has given talks where he proposes that tech companies decrease their communications and device security for the benefit of the FBI. In a recent talk, his idea is that tech companies just save a copy of the Continue reading
Nokia Scores 5G Equipment Deal with NTT DoCoMo
 It’s the first 3GPP-standards compliant 5G NR equipment deal that’s been announced.
It’s the first 3GPP-standards compliant 5G NR equipment deal that’s been announced.
Project Falco joins SONiC Community (Software for Open Networking in the Cloud) | LinkedIn Engineering
 Linked chooses SONIC for hardware abstraction
Linked chooses SONIC for hardware abstraction

