ParkMyCloud Automates Multi-Cloud Cost Control
 The platform works with AWS, Azure, and Google, and plans to support Alibaba Cloud later this year.
The platform works with AWS, Azure, and Google, and plans to support Alibaba Cloud later this year.
NSX-T: Routing where you need it (Part 2, North-South Routing)
In the first part of this blog series, NSX-T: Routing where you need it (Part 1), I discussed how East-West (E-W) routing is completely distributed on NSX-T and how routing is done by the Distributed Router (DR) running as a kernel module in each hypervisor.
In this post, I will explain how North-South (N-S) routing is done in NSX-T and we will also look at the ECMP topologies. This N-S routing is provided by the centralized component of logical router, also known as Service Router. Before we get into the N-S routing or packet walk, let’s define Service Router.
Service Router (SR)
Whenever a service which cannot be distributed is enabled on a Logical Router, a Service Router (SR) is instantiated. There are some services today on NSX-T which are not distributed such as:
1) Connectivity to physical infrastructure
2) NAT
3) DHCP server
4) MetaData Proxy
5) Edge Firewall
6) Load Balancer
Let’s take a look at one of these services (connectivity to physical devices) and see why a centralized routing component makes sense for running this service. Connectivity to physical topology is intended to exchange routing information from NSX domain to external networks (DC, Campus or Continue reading
Domain Name System Security Extensions (DNSSEC) Cheat Sheet Released

Here is the Cheat Sheet for DNSSEC. Recently vulnerabilities in the DNS were discovered that allow an attacker to hijack this process of looking some one up or looking a site up on the Internet using their name. The purpose of the attack is to take control of the session to, for example, send the user to the hijacker's own deceptive web site for account and password collection.
These vulnerabilities have increased interest in introducing a technology called DNS Security Extensions (DNSSEC) to secure this part of the Internet's infrastructure.
If you found a bug or want new content to be added, email me!
New developments in the net neutrality debate
Democrats in the USA haven’t given up on net neutrality since the FCC voted to repeal the 2015 Open Internet Order in December.
Senator Markey, a Democrat from Massachusetts, has put forward a bill that would use the Congressional Review Act (CRA) to reverse the Federal Communications Commission’s (FCC) decision. The CRA allows lawmakers 60 legislative days after the FCC submits its regulations to Congress to take action.
That bill now has the support of more than 40 Senators, including Senator Susan Collins (R-Maine), its first Republican supporter.
Senator Markey needs 52 votes to get the bill passed in the Senate, which is unlikely given that Republicans remain in control of both chambers of Congress. Nevertheless, Democrats see value in forcing a vote on the bill ahead of the 2018 midterm elections. Polls indicate that 83 per cent of Americans support keeping the FCC’s net neutrality rules.
If the bill fails to move forward, Congress may pursue a legislative solution – a bill that would codify net neutrality rules into law, rather than a reversal of the FCC’s decision. In fact, the Republicans are possibly signaling an appetite to come to a legislative solution to this issue. Regardless of Continue reading
Telefónica and Huawei Provide Optical Clarity with Transport SDN Lab Test
 The T-SDN technology targets greater control over optical transport networks.
The T-SDN technology targets greater control over optical transport networks.
Pivotal Commware Touts Holographic Beamforming as 5G Coverage Tool
 Bill Gates is an investor in this Kirkland, Washington-based startup.
Bill Gates is an investor in this Kirkland, Washington-based startup.
IBM ‘Redeploys’ CFO, Reportedly Plans to Reassign 30% of Workforce
 The cuts will come from the Global Technology Services division.
The cuts will come from the Global Technology Services division.
Show 372: Kentik & Network Traffic Intelligence (Sponsored)
Today's Weekly Show is all about network traffic intelligence. Our sponsor is Kentik and we talk with CEO Avi Freedman about getting deep visibility for performance, DDoS detection & more. The post Show 372: Kentik & Network Traffic Intelligence (Sponsored) appeared first on Packet Pushers.SDxCentral’s Weekly Roundup — January 11, 2018
 Huawei persists despite failures in U.S.; T-Mobile launches NB-IoT plan; Verizon acquires threat hunter.
Huawei persists despite failures in U.S.; T-Mobile launches NB-IoT plan; Verizon acquires threat hunter.
DNSFS. Store your files in others DNS resolver caches
DNSFS. Store your files in others DNS resolver caches
A while ago I did a blog post about how long DNS resolvers hold results in cache for, using RIPE Atlas probes testing against their default resolvers (in a lot of cases, the DNS cache on their m
Welcome Salt Lake City and Get Ready for a Massive Expansion


We just turned up Salt Lake City, Utah — Cloudflare's 120th data center. Salt Lake holds a special place in Cloudflare's history. I grew up in the region and still have family there. Back in 2004, Lee Holloway and I lived just up into the mountains in Park City when we built Project Honey Pot, the open source project that inspired the original idea for Cloudflare.
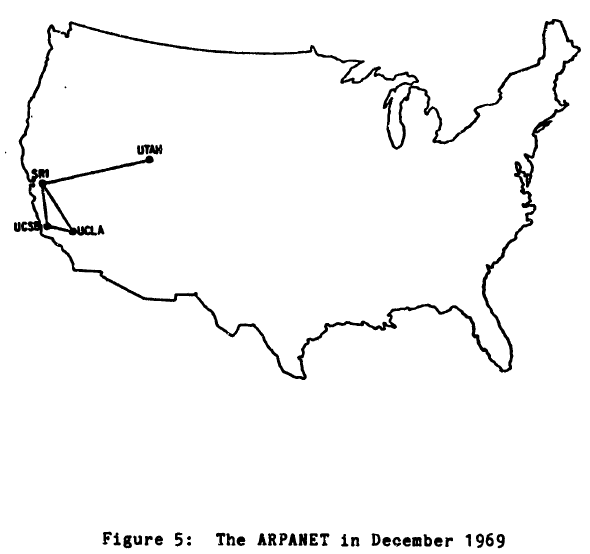
Salt Lake also holds a special place in the history of the Internet. The University of Utah, based there, was one of the original four Arpanet locations (along with UCLA, UC Santa Barbara, and the Stanford Research Institute). The school also educated the founders of great technology companies like Silicon Graphics, Adobe, Atari, Netscape, and Pixar. Many were graduates of the computer graphics department lead by Professors Ivan Sutherland and David Evans.

In 1980, when I was seven years old, my grandmother, who lived a few blocks from the University, gave me an Apple II+ for Christmas. I took to it like a duck to water. My mom enrolled in a continuing education computer course at the University of Utah teaching BASIC programming. I went with her to the classes. Unbeknownst to the Continue reading
