Is It The End, Or Can You Do Something in 2024?
David Bombal invited me for another annual chat last December, focusing on (what else) networking careers in 2024. The results were published a few days ago, and I was amazed at how good it turned out. I always love chatting with David; this time, his editing team did a masterful job.
KU045: How Yellowbrick Is Redefining Data Warehousing with Kubernetes (Sponsored)
Mark Cusack from Yellowbrick joins us to talk about all things database and data warehouse on Kubernetes. Yellowbrick is a data warehousing solution that runs 100% on Kubernetes. Mark details the company’s history, the transition from hardware to a software-only model, and the adoption of Kubernetes to improve scalability and flexibility. He addresses misconceptions about... Read more »Hedge 208: The Internet of Things

The Internet of Things (IoT) has been brewing for many years–but how do all these new devices impact your network? Are there new concepts and architectures you need to learn to get a handle on IoT? Jasbir Singh, author of a new book on IoT architecture, joins Tom and Russ for this episode of the Hedge.
IPv6 Buzz 142: IPv6 Basics – Why We Need IPv6 And How It’s Different From IPv4
We kick off 2024 with a new limited series called “IPv6 Basics” for those listeners who might be new to this protocol or would like a refresher. Ed and Scott start with why IPv6 was needed and how it is different (and the same) as IPv4. Topics discussed include: Early drivers for IPv6 development IPv6... Read more »Painless Progress with My Ubiquiti Upgrade

I’m not a wireless engineer by trade. I don’t have a lab of access points that I’m using to test the latest and greatest solutions. I leave that to my friends. I fall more in the camp of having a working wireless network that meets my needs and keeps my family from yelling at me when the network is down.
Ubiquitous Usage
For the last five years my house has been running on Ubiquiti gear. You may recall I did a review back in 2018 after having it up and running for a few months. Since then I’ve had no issues. In fact, the only problem I had was not with the gear but with the machine I installed the controller software on. Turns out hard disk drives do eventually go bad and I needed to replace it and get everything up and running again. Which was my intention when it went down sometime in 2021. Of course, life being what it is I deprioritized the recovery of the system. I realized after more than a year that my wireless network hadn’t hiccuped once. Sure, I couldn’t make any changes to it but the joy of having a stable environment Continue reading
HS062: Questions On Being Service-Oriented
Johna and Greg discuss service-oriented networking and the challenges of defining and delivering network services. They explore the negative impact of siloed organizational structures on service delivery and the importance of continuous adaptation in infrastructure management. They debate the perception of services by users, using metaphors like sidewalks and electricity, and the importance of defining... Read more »Navigating 2024: Transformative Trends Shaping the Tech Landscape
The 2024 tech landscape may best be described with three words: adapt, collaborate, and secure. Specifically, businesses will shift how they approach technology via the adoption of NaaS, the prioritization of cloud security, and the implementation of a collective defense against cyber threats.netlab 1.7.1: Eye Candy

What do you get when you write code next to a Christmas tree? You can expect to get tons of eye candy, and that’s what netlab release 1.7.1 is all about.
It all started with a cleanup idea: I could replace the internal ASCII table-drawing code with the prettytable library. Stefan was quick to point out that I should be looking at the rich library, and the rest is history:
netlab 1.7.1: Eye Candy

What do you get when you write code next to a Christmas tree? You can expect to get tons of eye candy, and that’s what netlab release 1.7.1 is all about.
It all started with a cleanup idea: I could replace the internal ASCII table-drawing code with the prettytable library. Stefan was quick to point out that I should be looking at the rich library, and the rest is history:
D2C228: Building Local Tech Communities
While it’s easy to find technical content and make professional connections online, in-person interactions are still valuable for learning, forging business and personal connections, and career development. On today’s Day Two Cloud we discuss how and why to build local tech communities. Guest Laura Santamaria is a developer, developer advocate, and longtime community builder. We... Read more »Wi-Fi Alliance Wi-Fi Certified 7 Program to Drive Deployment
Performance improvements make Wi-Fi 7 ideal for streaming applications and for reducing congestion in crowded environments.Registration No Longer Needed to Download Free PDFs
I published dozens of free-to-download slide decks on ipSpace.net. Downloading them required the free ipSpace.net subscription which is no longer available because I refuse to play a whack-a-mole game with spammers.
You might like the workaround I had to implement to keep those PDFs accessible: they are no longer behind a regwall.
You can find the list of all the free content ipSpace.net content here. The Conferences and Presentations page is another source of links to public presentations.
Registration No Longer Needed to Download Free PDFs
I published dozens of free-to-download slide decks on ipSpace.net. Downloading them required the free ipSpace.net subscription which is no longer available because I refuse to play a whack-a-mole game with spammers.
You might like the workaround I had to implement to keep those PDFs accessible: they are no longer behind a regwall.
You can find the list of all the free content ipSpace.net content here. The Conferences and Presentations page is another source of links to public presentations.
AI Data Centers Need High-performance Networks: HPE to Acquire Juniper Networks
AI has forced many enterprises to re-evaluate their network infrastructure. HPE’s acquisition of Juniper Networks seeks to focus on meeting the performance needs of AI data centers.HW018: Building a Successful Wi-Fi Consulting Business
Wi-Fi consultant Rowell Dionicio shares his experiences and insights on building a successful consulting practice. He discusses the importance of niche specialization, creating educational content, and using his podcast and blog as marketing tools. Rowell highlights the need for continuous learning, effective communication, and networking. He also addresses the business side of consulting, including handling... Read more »Making Networking Cool Again? (1)
Is network engineering still cool?
It certainly doesn’t seem like it, does it? College admissions seem to be down in the network engineering programs I know of, and networking certifications seem to be down, too. Maybe we’ve just passed the top of the curve, and computer networking skills are just going the way of coopering. Let’s see if we can sort out the nature of this malaise and possible solutions. Fair warning—this is going to take more than one post.
Let’s start here: It could be that computer networking is a solved problem, and we just don’t need network engineers any longer.
I’ve certainly heard people say these kinds of things—for instance, one rather well-known network engineer said, just a few years back, that network engineers would no longer be needed in five years. According to this view, the entire network should be like a car. You get in, turn the key, and it “just works.” There shouldn’t be any excitement or concern about a commodity like transporting packets. Another illustration I’ve heard used is “network bandwidth should just be like computer memory—if you need more, add it.”
Does this really hold, though? Even if we accept the Continue reading
Top 10 Reasons to Consider Replacing Your Existing SD-WAN
If your goal is to evolve to a converged networking and security infrastructure, follow these guidelines and consider upgrading your SD-WAN.Raspberry Pi 5 real-time network analytics
 |
| CanaKit Raspberry Pi 5 Starter Kit - Aluminum |
ssh [email protected]Use ssh to log into Raspberry Pi (having installled the micro SD card).
sudo apt-get update && sudo apt-get -y upgradeUpdate packages and OS to latest version.
curl Continue reading
VXLAN/EVPN – Host mobility
In the previous post VXLAN/EVPN – Host ARP, I talked about how knowing the MAC/IP of endpoints allows for ARP suppression. In this post we’ll take a look at host mobility. The topology used is the same as in the previous post:
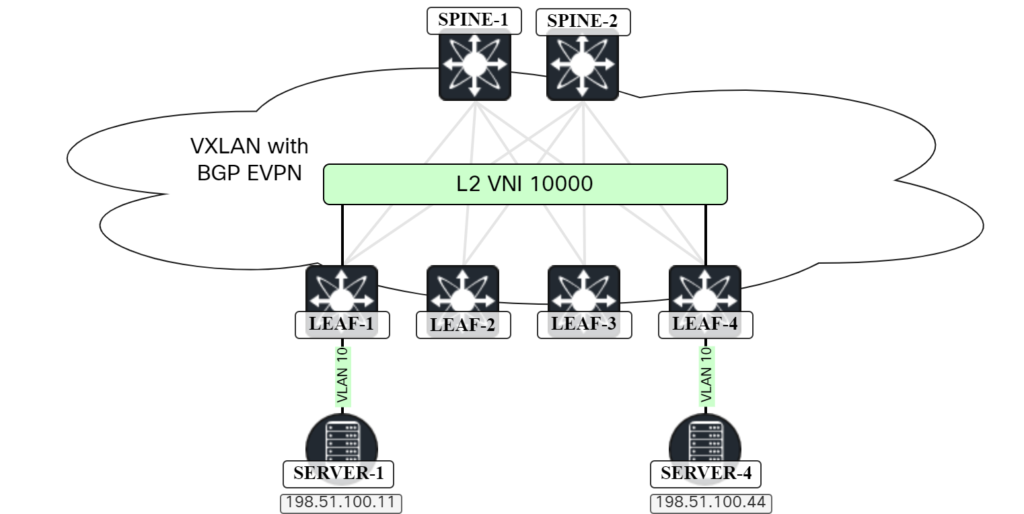
Currently SERVER-1 is connected to LEAF-1. What happens if SERVER-1 moves to LEAF-2? This would be a common scenario for a virtual infrastructure. First let’s take a look at LEAF-4 on what routes we have for SERVER-1:
Leaf4# show bgp l2vpn evpn 0050.56ad.8506
BGP routing table information for VRF default, address family L2VPN EVPN
Route Distinguisher: 192.0.2.3:32777
BGP routing table entry for [2]:[0]:[0]:[48]:[0050.56ad.8506]:[0]:[0.0.0.0]/216, version 662
Paths: (2 available, best #2)
Flags: (0x000202) (high32 00000000) on xmit-list, is not in l2rib/evpn, is not in HW
Path type: internal, path is valid, not best reason: Neighbor Address, no labeled nexthop
AS-Path: NONE, path sourced internal to AS
203.0.113.1 (metric 81) from 192.0.2.12 (192.0.2.2)
Origin IGP, MED not set, localpref 100, weight 0
Received label 10000
Extcommunity: RT:65000:10000 ENCAP:8
Originator: 192.0.2.3 Cluster list: 192.0.2.2
Advertised Continue reading