Simplifying ipSpace.net Products
When I started my ipSpace.net project life was simple: I had a few webinars, and you could register for the live sessions. After a while I started adding recordings, subscriptions, bundles, roadmaps (and tracks), books… and a few years later workshops and online courses.
As you can imagine, the whole thing became a hard-to-navigate mess. Right now you can buy almost 70 different products on ipSpace.net. Time for a cleanup.
Read more ...Network Neutrality – Again
It strikes me as odd to see a developed and, by any reasonable standard, a prosperous economy getting into so much trouble with its public communications policy framework.Technology with Purpose: Vashkar Bhattacharjee’s Story
In honor of today’s International Day of Persons with Disabilities, we are sharing part one of Vashkar Bhattacharjee’s story. He is the National Consultant, Accessibility, A2i, Prime Minister’s Office of Bangladesh, and the Program Manager, Young Power in Social Action (YPSA).
I am Vashkar Bhattacharjee, a visually impaired person from Bangladesh. And this is the story of how I have excelled in life and career, not through sympathy and charity, but through inspiration and assistance.
In Bangladesh, every 1 in 10 persons experience at least one kind of disability. I am one of approximately 4 million Bangladeshis who are visually impaired.
In 1979, like most of the villages in Bangladesh, my village in the district of Chittagong did not have doctors or hospital facilities. On July 1st in the same year, in a small remote village called Bagdondi, I was born in my parental home without any medical supervision. Right after my birth, I was bleeding through my nose and mouth. My parents and relatives could not figure out what was wrong. After a while, the bleeding stopped and everything seemed to be normal. By the time I was two years old, my parents realized the heartbreaking truth that Continue reading
Worth Reading: The Basic Math behind Reliability
Diptanshu Singh wrote a nice explanation of the math behind reliability calculations. Definitely worth reading even if you hated statistics.
A Dummy Light for My Network
I’ve always heard the red lights in car dashboard referred to as Dummy Lights. One example might be the use of a light to indicate high temperature in lieu of a temperature gauge. Over the past few weeks, I’ve spent more time doing unique things with hardware and software. Yesterday I challenged myself to build an indicator light to show health issues with my Meraki MX.
Before I get into this, the cool factor here is not what I have built. The cool factor is that someone with very little experience, driven by curiosity, can build this in a very short period of time. I’m neither a professional developer nor someone with deep knowledge around hardware hacking. So before I get too deep into this, I want to solicit thoughts, feedback, and recommendations.
The Trigger
After a little research, I found that the Meraki Dashboard provides a “Load Monitor” that is returned via a perfScore value. This feature is in beta and there’s not a lot of information on it. Therefore, consider your own data source that you would like to use as a trigger value. The following python code will store a numeric value (score) between 1 and 100 (with a Continue reading
A Dummy Light for My Network
I’ve always heard the red lights in car dashboard referred to as Dummy Lights. One example might be the use of a light to indicate high temperature in lieu of a temperature gauge. Over the past few weeks, I’ve spent more time doing unique things with hardware and software. Yesterday I challenged myself to build an indicator light to show health issues with my Meraki MX.
Before I get into this, the cool factor here is not what I have built. The cool factor is that someone with very little experience, driven by curiosity, can build this in a very short period of time. I’m neither a professional developer nor someone with deep knowledge around hardware hacking. So I want to solicit thoughts, feedback, and recommendations.
The Trigger
After a little research, I found that the Meraki Dashboard provides a “Load Monitor” that is returned via a perfScore value. This feature is in beta and there’s not a lot of information on it. Therefore, consider your own data source that you would like to use as a trigger value. The following python code will store a numeric value (score) between 1 and 100 (with a lower number being a better score).
import Continue reading
A Dummy Light for My Network
I’ve always heard the red lights in car dashboard referred to as Dummy Lights. One example might be the use of a light to indicate high temperature in lieu of a temperature gauge. Over the past few weeks, I’ve spent more time doing unique things with hardware and software. Yesterday I challenged myself to build an indicator light to show health issues with my Meraki MX.
Before I get into this, the cool factor here is not what I have built. The cool factor is that someone with very little experience, driven by curiosity, can build this in a very short period of time. I’m neither a professional developer nor someone with deep knowledge around hardware hacking. So I want to solicit thoughts, feedback, and recommendations.
The Trigger
After a little research, I found that the Meraki Dashboard provides a “Load Monitor” that is returned via a perfScore value. This feature is in beta and there’s not a lot of information on it. Therefore, consider your own data source that you would like to use as a trigger value. The following python code will store a numeric value (score) between 1 and 100 (with a lower number being a better score).
import Continue reading
Juniper vSRX Vagrant Libvirt Box Install
Build a Juniper vSRX box for use with the libvirt provider.Juniper vSRX Vagrant Libvirt Box Install
In this post I will install a Juniper vSRX for use with the vagrant-libvirt provider. Prior to installing the vSRX there are some required steps to get the KVM host prepped which I will not cover. These steps are covered in the Juniper documentation here. For reference the following...Tool-of-the-day: Isochronous Round-Trip-Tester
Dave Taht sent me a link to IRTT after I published a blog post on measuring end-to-end latency with an Ansible playbook. Definitely looks like a tool worth having in your toolbox.
Interoperability between Dell and Cisco: Rapid-PVST+
Before I start with the PVST+ ,I would like to tell you guys that we have our own youtube channel for various network videos that can further help you guys to study further. I will going to add many more videos soon on the channel, Please subscribe to the channel for the study network related videos
 |
| Fig 1.1- LAN network STP topology |
Upcoming Seminar: Brighttalk on the future of networking
On Tuesday the 5th, I’m participating in a webcast discussion about the future of networking over at Brighttalk. The details and registration linked below. I’ll be in a hotel room; I’m hoping the audio and lighting will work out correctly.
Re-Engineering Enterprise IT: A Blueprint for the Modern Infrastructure

The Largest Rounds of Funding in 2017, So Far
 Investors put money into IoT, cybersecurity, the cloud, containers, and more.
Investors put money into IoT, cybersecurity, the cloud, containers, and more.
Hyperconverged Infrastructure Eases IT Transformation to the Hybrid Cloud
 Organizational readiness is a big factor in HCI integration.
Organizational readiness is a big factor in HCI integration.
Weekend Reads 120117
There’s an “automation meteor” headed right at us, according to financial adviser and Reformed Broker blogger Josh Brown, who used this troubling “chart o’ the day” from Wharton to show just “how quickly things have changed” over the past decade. And how they’re going to keep on changing. —Shawn Langlois @ MarketWatchThere’s an “automation meteor” headed right at us, according to financial adviser and Reformed Broker blogger Josh Brown, who used this troubling “chart o’ the day” from Wharton to show just “how quickly things have changed” over the past decade. And how they’re going to keep on changing. —Shawn Langlois @ MarketWatch
Many historians believe that one of the main reasons why the U.S. won the Cold War was its decisive lead over the Soviet Union in computer and telecommunications technology, which, by the 1980s, made it virtually impossible for the Soviets to compete, either economically or militarily. Continue reading
Show 368: Radical Change, DevOps & Automation
On today's Weekly Show, Greg and Ethan discuss why it's hard to bring radical products to market, DevOps as a communications issue, and whether automation tooling is just a provisional step in network evolution. The post Show 368: Radical Change, DevOps & Automation appeared first on Packet Pushers.Enterprise Network on GNS3 – Part 4 – Cisco ASAv-I
This is the fourth from the series of the articles that discuss configuration of the enterprise network. The article explains configuration of the device ASAv-I. The device is a Cisco Adaptive Security Virtual Appliance (ASAv) version 9.6(1) installed on qcow2 Qemu disk. The ASAv-I provides traffic filtering and inspection services for the campus network and Data Center (DC). It also connects the campus network and DC to the vIOS-EDGE-I edge router.
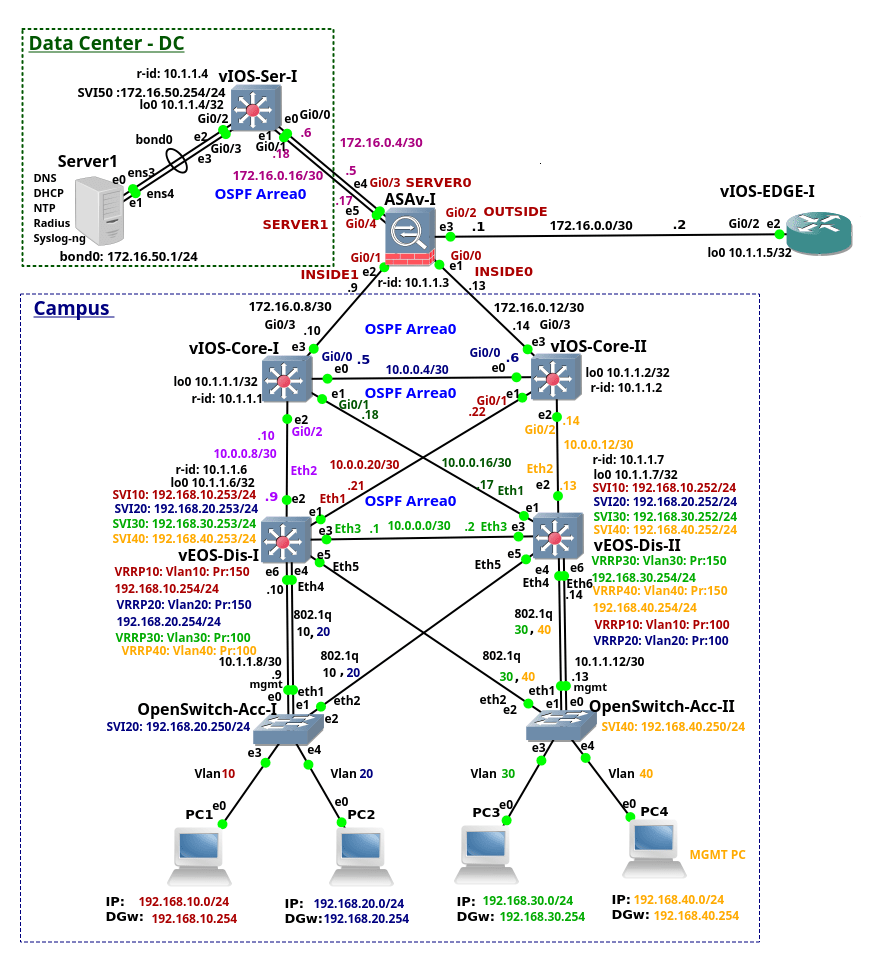
Picture 1 - ASAv-I, Campus, DC and Edge Connection
Note: The recommended RAM size for ASAv instance is 2048 MB. In order to lower memory consumption, GNS3 is configured to assign 1536 MB to the ASAv.
Note: The interface eth0 on the ASAv-I is referred as the interface Management0/0 in ASAv configuration. The interface eth0 is not connected as we use the inside interfaces for management instead. The first connected interface is then the interface eth1 that is referred as the interface GigabitEthernet0/0 in ASAv CLI. Similarly, the second connected interface eth2 is referred as the GigabitEthernet0/1 and so on.
Note: Here is the configuration file of vASA-I.
ASAv-I Configuration
Once we start ASAv, the Qemu window is launched. However we want to use GNS3 Continue reading
SDxCentral’s Weekly Roundup — December 1, 2017
 Hyperledger reaches 183 members; Azure adds location services; and AWS debuts new VR, IoT, and more at re:Invent.
Hyperledger reaches 183 members; Azure adds location services; and AWS debuts new VR, IoT, and more at re:Invent.