Fortinet Next Generation Firewalls : Fortinet 5000 Series Firewalls
Now I am going to talk about the Fortinet Next Generation Firewalls.
Fortinet Next Generation Firewalls
 |
| Fig 1.1- Fortigate Next Generation Firewalls |
Reaction: Enabling Privacy is not Harmful
The argument for end-to-end encryption is apparently heating up with the work moving forward on TLSv1.3 currently in progress in the IETF. The naysayers, however, are also out in force, arguing that end-to-end encryption is a net negative. What is the line of argument? According to a recent article in CircleID, it seems to be something like this:
- Governments have a right to asymmetrical encryption capabilities in order to maintain order. In other words, governments have the right to ensure that all private communication is ultimately readable by the government for any lawful purpose.
- Standards bodies that enable end-to-end encryption that will prevent this absolute governmental good endanger society. The leaders of such standards bodies may, in fact, be prosecuted for their role in subverting government power.
The idea of end-to-end encryption is recast as a form of extremism, a radical idea that should not be supported by the network engineering community. Is end-to-end encryption really extremist? Is it really a threat to the social order?
Let me begin here: this is not just a technical issue. There are two opposing worldviews in play. Engineers don’t often study worldviews, or philosophy, so these questions tend to get buried in Continue reading
VMware Snaps Up SD-WAN Vendor VeloCloud
 The deal gives VMware more networking clout to better compete with Cisco.
The deal gives VMware more networking clout to better compete with Cisco.
3 must-attend events at OpenStack Summit Sydney
OpenStack Summit Sydney is just around the corner, and Cumulus Networks wouldn’t miss it for the world! We’ll be there at our booth, doing daily contests and raffles, so make sure to stop by. If you’re lucky, you might walk away with a 6 pack of Linux Lager. But of course, you don’t need beer to have fun at OpenStack — there’s so much to keep you busy and fired up! With so many amazing panels and presentations, it’s hard to pick and choose which events to attend. Fortunately, we’ve done the research and picked out the top 3 must-attend activities. If you’re going to be at OpenStack in Sydney next week, make sure to check these out:
- 1-on-1 OpenStack demo: Eager to get hands-on with everything OpenStack has to offer? Then you should sign up for a live demo with Cumulus Networks! We will first be doing a theater session at 4:00 PM on Monday at the Marketplace Demo Theater Level 2, where CTO JR Rivers will give insight as to how production deployments are leveraging IP fabrics and OpenStack networking to simplify operations and deliver services at scale. But of course, nothing beats seeing the tech up-close and Continue reading
Berlin Becomes Hotbed for 5G, SDN, NFV, and MEC Events
 Open Baton adds Docker container support to its MANO code.
Open Baton adds Docker container support to its MANO code.
FRRouting Software with EIGRP Support
In September 2016 I wrote the article about EIGRP support in Quagga network routing suite. More than one year later, I am going to check the progress of development EIGRP in Linux again. To do so, I have installed a fork of Quagga - FRRouting (FRR) with EIGRP support on Linux Core. EIGRP routing daemon included inside FRR benefits from active development brought by Cumulus employees. For the purpose of FRR testing, I have created a minimalistic Linux Core Pure64 virtual machine with FRR suite compiled as frr extension. Meanwhile, I have submitted FRR extension so it will be available in the next few days in Tinycore repository.
Content of Disk - CorePure64-frr_3-1.vmdk:
- Linux Core Pure 64 version 8.2,kernel 4.8.17
- FRRouting 3.1dev
- OpenSSL 1.0.2l 25 May 2017
- OpenSSH_7.2p2
- GNU bash, 4.4.0(1)
- iproute2-ss140411
- iptables v1.4.21
- tcpdump 4.7.4
- Nmap 7.12
- mtr 0.86
- hping 3.0.0-alpha-1
- iperf 3.1b3
- D-ITG 2.8.1 (r1023)
Software:
- Host OS - Ubuntu 16.04.3 LTS x64
- GNS3 2.0.3
- QEMU x64 emulator version 2.8.0
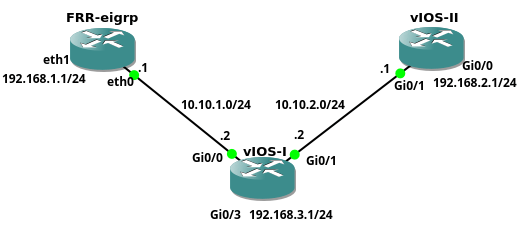 Picture 1 - Network Topology
Picture 1 - Network Topology
The FRR EIGRP instance with attached CorePure64-frr_3-1.vmdk Continue reading
PQ 134: Meet ZeroTier – Open Source Networking
Today's Priority Queue dives into ZeroTier, an open source project for building virtual networks including VPNs, SDN, and SD-WAN. Our guest is founder Adam Ierymenko. The post PQ 134: Meet ZeroTier – Open Source Networking appeared first on Packet Pushers.Abstract, Automate & Secure — From Data Center to Cloud to Edge
By Milin Desai, Vice President of Products, NSBU
It feels like only yesterday when we started our journey into networking at VMware. Even from the early beginnings in 2011, it became clear to some of us that the abstraction and operations model of virtualization for compute and memory, which completely transformed the modern data center, was something we needed to extend to networking. We understood that that a network based on software and abstraction in the long run would extend beyond our customers’ data centers to public clouds and ultimately to the Edge.
We’ve been executing on this vision for almost eight years; reinventing data center networking and enabling our customers to be smarter about how they secure, manage and connect their applications and users.
Starting with the Data Center
The Nicira acquisition, alongside our internal innovations, resulted in the release of VMware NSX in 2013. VMware NSX made network virtualization a mainstream possibility for the data center. The goal was simple — abstract the application from the physical network and deliver the networking attributes in software at machine speeds. After four years, multiple thousands of customers and the creation of a billion-dollar run rate business, we have transformed the Continue reading
Network Optimization for Cloud Access
With the growth of cloud services, enterprises need to ensure users don't run into network bottlenecks.
Network Optimization for Cloud Access
With the growth of cloud services, enterprises need to ensure users don't run into network bottlenecks.