Nutanix HCI Simplifies, Shrinks University’s Data Center Footprint
 It doesn't makes IT totally fun, "but at least mildly interesting."
It doesn't makes IT totally fun, "but at least mildly interesting."
RIPE 75: IoT & Routing Security

RIPE 75 was held on 22-26 October 2017 in Dubai, United Arab Emirates, and was the second time the meeting has come to the Middle East. 483 participants from 54 countries including 175 newcomers came together to discuss operational issues and share expertise about the Internet, with a particular focus on the RIPE region that covers Europe, the Middle East and Central Asia.
Jan Žorž and Kevin Meynell from the Deploy360 team, along with Salam Yamout from the Middle East Bureau were also actively involved in the launch of a new Internet-of-Things Working Group, hosting a Routing Security BoF, and raising awareness of IRTF work on Human Rights Protocol Considerations.
The BoF session on ‘Internet Routing Health’ was organised by the Internet Society, and chaired by Jan and Benno Overreinder (NLnet Labs). The BoF attracted 20 participants variously drawn from commercial network operators and cloud providers, Regional Internet Registries (RIRs), and academia, with the aim of discussing ideas for measuring the health of the Internet routing system in order to obtain empirical data to strengthen the case for collaborative routing security.
The IoT session aimed to build on the RIPE IoT Roundtable meeting that was held on 21 September 2017 in Leeds, UK, and Continue reading
Juniper Optical Networking Platform Separates Hardware from Software
 The move targets service providers looking for "cloudification" of their network resources.
The move targets service providers looking for "cloudification" of their network resources.
How to Get Your IT ‘Dream Job’
Interop ITX infrastructure track chair Keith Townsend talks about working his way up from the help desk.
How to Get Your IT ‘Dream Job’
Interop ITX infrastructure track chair Keith Townsend talks about working his way up from the help desk.
Quick Facts on EIGRP
There are lot of interesting facts around the EIGRP protocol, Some says it is Link state routing protocol and some says it is distance vector routing protocol. Well it is a Hybrid routing protocol. I am expecting you guys know about the fact of Distance Vector routing protocol and also know about the features and working of the Link State routing protocols.
ROCA: Encryption vulnerability and what to do about it
Researchers recently discovered a dangerous vulnerability – called ROCA – in cryptographic smartcards, security tokens, and other secure hardware chips manufactured by Infineon Technologies. These articles on Ars Technica and The Register give a good background.
Is this a serious problem?
Yes. It’s serious in practice and in principle. Infineon used a flawed key generation routine, which means those keys are easier to crack, and the routine is used in chips embedded in a wide variety of devices. It’s reckoned that the flawed routine has been in use since 2012 and has probably been used to generate tens of millions of keys. Naturally, many of those keys will have been generated precisely because someone had data or resources that they particularly wanted to secure.
It’s serious because a flawed implementation managed to get through all the development and standardisation processes without being spotted, and has been widely deployed on mass-market devices.
What’s the flaw, and why does it cause a problem?
The flaw affects keys generated for the RSA and OpenPGP algorithms, both of which are public key crypto systems. Public key cryptography is based on pairs of keys, one of which is made public and the other kept private:
Enterprise Network on GNS3 – Part 3 – Distribution and Core Layers
This is the third from the series of the articles that discuss configuration of the entire enterprise network. The article focuses on the configuration of the distribution and core switches. The distribution layer consists of two multilayer switches vEOS-DIS-I and vEOS-DIS-II. The switches are Arista vEOS version 4.17.2F Qemu appliances installed on VMware disks. Each appliance has assigned 1536 MB RAM.
The distribution switches route traffic between end user VLANs and they connect the lower layer network to a Core layer. The layer 3 (routed) interfaces connect both distribution switches to each other and to the Core switches. The interfaces toward the Access layer are layer 2 (switchports). The OSPF routing protocol is running on the distribution switches so there is only l3 connectivity between distribution and core layer.
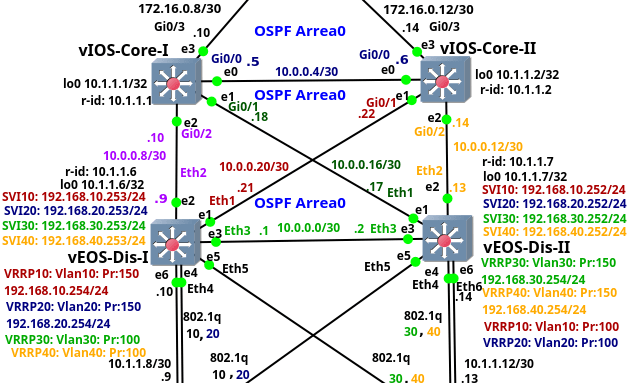
Picture 1 - Distribution and Core Layers of Enterprise Campus Network
Note: The configuration files of the distribution switches are: vEOS-DIS-I and vEOS-DIS-II.
The core layer consists of the switches vIOS-Core-I and vIOS-Core-II. These are the Cisco vIOS-l2 Qemu appliances on qcow2 disks, version 15.2. Each switch has assigned 768 MB RAM by GNS3. The core layer is completely layer3. It si connected to the lower Continue reading
All Of Ethan’s Podcasts And Articles For October 2017
Here’s a catalog of all the media I produced (or helped produce) in October 2017. I’ve decided to add some content summaries so that you have good incentive to give some of the podcasts a listen if they tickle your fancy.
PACKET PUSHERS WEEKLY PODCAST
- Episode 360 – All About Optics With InterOptic (Sponsored) A show that got a lot of positive feedback from listeners. We covered the benefits & tradeoffs of using third party optics in switching equipment. InterOptic is an optics vendor.
- Episode 361 – The Future Of Networking With Brighten Godfrey Brighten is a PhD who founded Veriflow, a startup making a strong showing in mathematical verification of network intent.
- Episode 362 – Advanced Network Programmability With Cisco (Sponsored) Cisco’s service provider business unit sponsored this show to have a technical discussion about YANG and IOS-XR service level APIs.
- Episode 363 – How Networking Has Changed In 2017 Greg Ferro and I have a chinwag about what we think are the most interesting networking trends for this year. Topics include intent based networking, SD-WAN, and the marked rise of visibility and analytics platforms.
PRIORITY QUEUE PODCAST
All Of Ethan’s Podcasts And Articles For October 2017
Here’s a catalog of all the media I produced (or helped produce) in October 2017. I’ve decided to add some content summaries so that you have good incentive to give some of the podcasts a listen if they tickle your fancy.
PACKET PUSHERS WEEKLY PODCAST
- Episode 360 – All About Optics With InterOptic (Sponsored) A show that got a lot of positive feedback from listeners. We covered the benefits & tradeoffs of using third party optics in switching equipment. InterOptic is an optics vendor.
- Episode 361 – The Future Of Networking With Brighten Godfrey Brighten is a PhD who founded Veriflow, a startup making a strong showing in mathematical verification of network intent.
- Episode 362 – Advanced Network Programmability With Cisco (Sponsored) Cisco’s service provider business unit sponsored this show to have a technical discussion about YANG and IOS-XR service level APIs.
- Episode 363 – How Networking Has Changed In 2017 Greg Ferro and I have a chinwag about what we think are the most interesting networking trends for this year. Topics include intent based networking, SD-WAN, and the marked rise of visibility and analytics platforms.
PRIORITY QUEUE PODCAST
10 5G Terms You Should Know
 5G will soon be a reality. Are you prepared?
5G will soon be a reality. Are you prepared?
IBM’s Considine on the Future of Cloud: Solutions are ‘Where It’s At’
 Pooling resources in the cloud and disaggregation is a future trend.
Pooling resources in the cloud and disaggregation is a future trend.
AT&T Tackles Artificial Intelligence with Open Source Acumos Project
 ONAP is viewed as the open source framework for the new AI project.
ONAP is viewed as the open source framework for the new AI project.
AT&T, Nokia, Qualcomm, and Ford Will Test C-V2X Tech in San Diego
 MEC will be a key technology to help cars communicate.
MEC will be a key technology to help cars communicate.
Google Supports Hybrid Cloud with Cloud Dedicated Interconnect
 Google can now better compete against AWS and Azure.
Google can now better compete against AWS and Azure.
Charter Expects to Launch SD-WAN ‘In the Coming Months’
 The company would be the second major cable operator to offer SD-WAN.
The company would be the second major cable operator to offer SD-WAN.