Measurement and Analysis of Protocols at IETF 118
>At IETF 118 in November 2023 I attended the meeting of the Measurement and Analysis of Protocols Research Group, and here are my impressions from that meeting.Life is Life
The initial idea behind this blog was to have a medium to store and share notes on the different technologies I worked on in an searchable manner. I have decided to step back from work and take a year out so this new life tab of the blog will be for all things non-IT related. I still plan to write technology based blogs over this time (got a few automation projects and Azure tips to share), however this is unlikely to start happening until later into next year.
The Benefits of Comprehensive Observability and Potent Analytics for Enterprise Networks
A real-time, dynamic, and high-definition network map can often provide information about whether the network is functioning properly or whether there are problems with any particular device.What is an IPU (Infrastructure Processing Unit) and How Does it Work?
IPUs (Infrastructure Processing Units) are hardware accelerators designed to offload compute-intensive infrastructure tasks like packet processing, traffic shaping, and virtual switching from CPUs.ML Ops Platform at Cloudflare
We've been relying on ML and AI for our core services like Web Application Firewall (WAF) since the early days of Cloudflare. Through this journey, we've learned many lessons about running AI deployments at scale, and all the tooling and processes necessary. We recently launched Workers AI to help abstract a lot of that away for inference, giving developers an easy way to leverage powerful models with just a few lines of code. In this post, we’re going to explore some of the lessons we’ve learned on the other side of the ML equation: training.
Cloudflare has extensive experience training models and using them to improve our products. A constantly-evolving ML model drives the WAF attack score that helps protect our customers from malicious payloads. Another evolving model power bot management product to catch and prevent bot attacks on our customers. Our customer support is augmented by data science. We build machine learning to identify threats with our global network. To top it all off, Cloudflare is delivering machine learning at unprecedented scale across our network.
Each of these products, along with many others, has elevated ML models — including experimentation, training, and deployment — to a crucial position within Continue reading
AMS-IX Outage: Layer-2 Strikes Again
On November 22nd, 2023, AMS-IX, one of the largest Internet exchanges in Europe, experienced a significant performance drop lasting more than four hours. While its peak performance is around 10 Tbps, it dropped to about 2.1 Tbps during the outage.
AMS-IX published a very sanitized and diplomatic post-mortem incident summary in which they explained the outage was caused by LACP leakage. That phrase should be a red flag, but let’s dig deeper into the details.
AMS-IX Outage: Layer-2 Strikes Again
On November 22nd, 2023, AMS-IX, one of the largest Internet exchanges in Europe, experienced a significant performance drop lasting more than four hours. While its peak performance is around 10 Tbps, it dropped to about 2.1 Tbps during the outage.
AMS-IX published a very sanitized and diplomatic post-mortem incident summary in which they explained the outage was caused by LACP leakage. That phrase should be a red flag, but let’s dig deeper into the details.
D2C223: Accelerating VM Performance With Azure Boost
Azure Boost is a hardware offload of Azure virtual machines designed to improve VM performance. On today's Day Two Cloud we dig into how it works. We also talk about how to implement security in Virtual Network Manager, as well as how to optimize your Azure observability--meaning, how not to blow up your budget with unnecessary logging.
The post D2C223: Accelerating VM Performance With Azure Boost appeared first on Packet Pushers.
D2C223: Accelerating VM Performance With Azure Boost
Welcome to Day Two Cloud! In this episode with Microsoft, it’s November 2023, and I’m in Seattle for the Microsoft Ignite conference. If you think you heard this intro before and you’re wondering if you’re hearing the same episode again, you’re not. This is the second episode from Microsoft Ignite 2023. Today, I’m talking with... Read more »How the AI Gold Rush Has the Potential to Take the Ceiling off The Network’s Potential
Leveraging AI, network providers can more easily evolve their networks to be faster, smarter, and governed by data-driven business policies.How we used OpenBMC to support AI inference on GPUs around the world
Cloudflare recently announced Workers AI, giving developers the ability to run serverless GPU-powered AI inference on Cloudflare’s global network. One key area of focus in enabling this across our network was updating our Baseboard Management Controllers (BMCs). The BMC is an embedded microprocessor that sits on most servers and is responsible for remote power management, sensors, serial console, and other features such as virtual media.
To efficiently manage our BMCs, Cloudflare leverages OpenBMC, an open-source firmware stack from the Open Compute Project (OCP). For Cloudflare, OpenBMC provides transparent, auditable firmware. Below describes some of what Cloudflare has been able to do so far with OpenBMC with respect to our GPU-equipped servers.
Ouch! That’s HOT!
For this project, we needed a way to adjust our BMC firmware to accommodate new GPUs, while maintaining the operational efficiency with respect to thermals and power consumption. OpenBMC was a powerful tool in meeting this objective.
OpenBMC allows us to change the hardware of our existing servers without the dependency of our Original Design Manufacturers (ODMs), consequently allowing our product teams to get started on products quickly. To physically support this effort, our servers need to be able to supply enough power and keep Continue reading
How to Interview a Network Engineer Using a Single Scenario
Most organizations are terribly bad at interviewing people. They overcomplicate things by holding too many interviews (more than 2-3) and often focus their interview on trivia and memorization rather than walking through a scenario. Every interview should have some form of a scenario and a whiteboard if you are hiring a Network Engineer. Rather than overcomplicating things, here’s how you can interview someone using a single scenario that you can expand on and go to different depths at different stages depending on the focus of the role.
Scenario:
You are an employee working in a large campus network. Your computer has just started up and has not previously communicated with anything before you open your browser and type in microsoft.com.
Before any communication can take place, you need an IP address. What IP protocols are there? What are the main differences between the two?
Things to look for: IPv4 vs IPv6. ARP vs ND. DHCP vs RA. Broadcast vs multicast.
What methods are there of configuring an IP address?
Things to look for: Static IP vs DHCP vs RA.
When I need to communicate to something external, traffic goes through a gateway. What type of device would Continue reading
BGP Labs: Use BGP Route Reflectors
In the previous BGP labs, we built a network with two adjacent BGP routers and a larger transit network using IBGP. Now let’s make our transit network scalable with BGP route reflectors, this time using a slightly larger network:
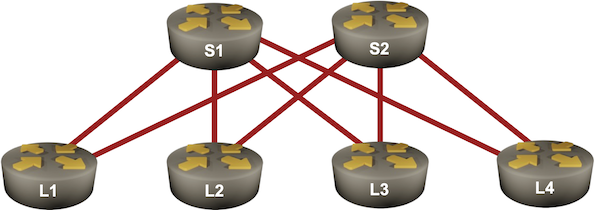
BGP Labs: Use BGP Route Reflectors
In the previous BGP labs, we built a network with two adjacent BGP routers and a larger transit network using IBGP. Now let’s make our transit network scalable with BGP route reflectors, this time using a slightly larger network:

HN712: FortiGuard Security Services: Invisible Operations, Tangible Results (Sponsored)
Fortinet turns its on-prem and cloud security devices into a sensor network that collects threat intelligence across the globe. That intelligence then feeds those devices and services with new updates and the latest protections. In today's sponsored Heavy Networking, we talk with Fortinet about its Fortiguard Security Services, how they work, and how customers can take advantage of them.
The post HN712: FortiGuard Security Services: Invisible Operations, Tangible Results (Sponsored) appeared first on Packet Pushers.
HN712: FortiGuard Security Services: Invisible Operations, Tangible Results (Sponsored)
Today we’re talking security, but security you don’t always see. Fortinet, today’s sponsor, has millions of devices in the field. These are real-world devices seeing real-world traffic, all day, everyday. While those devices have a primary protection role, they can also serve as sensors that collect threat signals and feed threat intelligence services that can,... Read more »Overspending on SaaS? 6 Ways to Cost Optimization
Here are 6-step quick tips to optimize your SaaS spending. Applying these tactics in your organization can reduce your SaaS expenses without adversely impacting your bottom line.HS060 Power Micro-Generation for Data Center
Powering data centres is big deal in current decade. Massive increases in consumption and scaling of off-prem clouds has exceeded the capacity of civilian power grids while cloud operators are reluctant to sign thirty year supply agreements so that more power plants can be built. Enter power micro-generation where large DCs needs too small power supply.
The post HS060 Power Micro-Generation for Data Center appeared first on Packet Pushers.