30 Days Left to Buy ipSpace.net Subscription
When I announced the lifetime ipSpace.net subscription in early September, I also mentioned that you won’t be able to purchase any ipSpace.net subscription after December 31st, 2023.
As of today, you have 30 days left to decide, and don’t wait till the last minute – I plan to turn off the purchasing process sometime during the business hours of December 31st as I hope to have more interesting things to do in the evening.
KU042: Kubernetes Long-Term Support With Kubernetes Co-Founder Brendan Burns
As Kubernetes becomes more mainstream and overall “stable,” organizations need a way to get both enterprise support and proper upgrade paths. Brendan Burns, co-founder of Kubernetes, joins the show to discuss Kubernetes LTS—long-term support.
The post KU042: Kubernetes Long-Term Support With Kubernetes Co-Founder Brendan Burns appeared first on Packet Pushers.
KU042: Kubernetes Long-Term Support With Kubernetes Co-Founder Brendan Burns
As Kubernetes becomes more mainstream and “stable,” organizations need a way to get enterprise support and proper upgrade paths. Brendan Burns, co-founder of Kubernetes, joins the show to discuss Kubernetes LTS—long-term support. Brendan shares how he and his team are bringing this to life at Microsoft with Azure Kubernetes Service (AKS), and what you can... Read more »The Growing Middle Mile Networks Funding Debate
Will the $1 billion in grants awarded to expand and upgrade these networks be enough to close the digital divide? Some say no.IPB140: IPv6 CLAT And IPv6-Only Networks
Ed, Scott, and Tom discuss the Customer-Side Translator (CLAT) function and its role in enabling client connectivity in IPv6-only networks.
The post IPB140: IPv6 CLAT And IPv6-Only Networks appeared first on Packet Pushers.
IPB140: IPv6 CLAT And IPv6-Only Networks
In this episode Ed, Scott, and Tom discuss the Customer-Side Translator (CLAT) function and its role in enabling client connectivity in IPv6-only networks. Topics discussed include: Traditional use of the CLAT and 464XLAT by mobile service providers How the CLAT may be used in enterprise IPv6-only networks Where DNS64/NAT64 doesn’t work and drives the need... Read more »The BGP Multi-Exit Discriminator (MED) Saga
Martijn Van Overbeek left this comment on my LinkedIn post announcing the BGP MED lab:
It might be fixed, but I can recall in the past that there was a lot of quirkiness in multi-vendor environments, especially in how different vendors use it and deal with the setting when the attribute does exist or does not have to exist.
TL&DR: He’s right. It has been fixed (mostly), but the nerd knobs never went away.
In case you’re wondering about the root cause, it was the vagueness of RFC 1771. Now for the full story ;)
The BGP Multi-Exit Discriminator (MED) Saga
Martijn Van Overbeek left this comment on my LinkedIn post announcing the BGP MED lab:
It might be fixed, but I can recall in the past that there was a lot of quirkiness in multi-vendor environments, especially in how different vendors use it and deal with the setting when the attribute does exist or does not have to exist.
TL&DR: He’s right. It has been fixed (mostly), but the nerd knobs never went away.
In case you’re wondering about the root cause, it was the vagueness of RFC 1771. Now for the full story ;)
Azure Key Vault Certificate Migration with Powershell
https://codingpackets.com/blog/azure-key-vault-certificate-migration-with-powershell
Unified SASE Maximizes the Potential of Observability
Unified SASE can amplify an organization’s observability capabilities, facilitating proactive threat detection, precise analysis, and better decision-making.Tigera has achieved AWS Security Competency status!
We’re happy to announce that Tigera recently achieved Amazon Web Services (AWS) Security Competency status. This designation recognizes the security capabilities of Tigera’s Calico Cloud platform in helping customers secure their AWS workloads and achieve their cloud security goals.
To receive the designation, AWS Partners must possess deep AWS expertise and deliver solutions seamlessly on AWS. After evaluating Calico Cloud’s security capabilities, including vulnerability management, container- and network-based threat detection, observability and security policy lifecycle, AWS found it surpassed the competency requirements.
This is the second AWS competency Tigera has achieved and we’re proud to add this new competency to our existing AWS Containers Software Competency. Our team is dedicated to helping companies achieve their Kubernetes and container security goals by combining our technology with the range of powerful security tools AWS provides.
Read the full press release for more details or visit us on the AWS Marketplace.
The post Tigera has achieved AWS Security Competency status! appeared first on Tigera.
D2C222: What’s New In Azure Networking (Sponsored)
Today's Day Two Cloud discusses how Azure's use of hollow core fiber will impact customers, building networks to support AI workloads, the general availability of Virtual Network Manager, routing improvements, a tech preview of IPAM in vNet Manager, updates around containers and security, and other network-related topics in Azure. Microsoft is the sponsor of this episode.
The post D2C222: What’s New In Azure Networking (Sponsored) appeared first on Packet Pushers.
D2C222: What’s New In Azure Networking (Sponsored)
From using hollow core fiber to building networks designed to support AI workloads and modern applications, there’s a lot happening in Azure networking. In this sponsored Day Two Cloud episode, recorded live at Microsoft Ignite this November, we have a wide-ranging discussion about new and forthcoming features and capabilities. My guest is Narayan Annamalai, who... Read more »BGP Labs: Set BGP Communities on Outgoing Updates
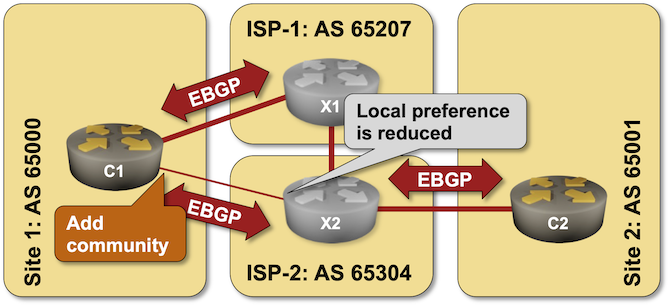
It’s hard to influence the behavior of someone with strong opinions (just ask any parent with a screaming toddler), and trying to persuade an upstream ISP not to send the traffic over a backup link is no exception – sometimes even AS path prepending is not a strong enough argument.
An easy solution to this problem was proposed in 1990s – what if we could attach some extra attributes (called communities just to confuse everyone) to BGP updates and use them to tell adjacent autonomous systems to lower their BGP local preference? You can practice doing that in the Attach BGP Communities to Outgoing BGP Updates lab exercise.
BGP Labs: Set BGP Communities on Outgoing Updates
It’s hard to influence the behavior of someone with strong opinions (just ask any parent with a screaming toddler), and trying to persuade an upstream ISP not to send the traffic over a backup link is no exception – sometimes even AS path prepending is not a strong enough argument.
An easy solution to this problem was proposed in 1990s – what if we could attach some extra attributes (called communities just to confuse everyone) to BGP updates and use them to tell adjacent autonomous systems to lower their BGP local preference? You can practice doing that in the Attach BGP Communities to Outgoing BGP Updates lab exercise.

Azure Application Gateway Log Analytics
https://codingpackets.com/blog/azure-application-gateway-log-analytics
Azure Firewall Log Analytics
https://codingpackets.com/blog/azure-firewall-log-analytics
Recap: KubeCon + CloudNativeCon NA 2023
Thanks to everyone who joined us in Chicago this month at KubeCon + CloudNativeCon NA 2023. We had a chance to have many meaningful conversations about Kubernetes and container security, the latest in the open source ecosystem, and of course—Calico! Here are some highlights from the conference.
Calico at KubeCon
We had a ton of visitors at our booth this year and were happy to catch up with old friends as well as meet new ones. Tech problems for business needs, such as how to provide fixed IPs to workloads for communication outside of the Kubernetes cluster instead of architectural debates about the underlying dataplane, was a popular topic of discussion. Another was runtime security at the workload level (default-deny/zero trust). The issue of visibility into workload communication at scale overlaid with effective security policies also came up often. We were all too happy to show how Calico can help!

Cruise Party
Those who joined us for our private cruise party enjoyed a guided architecture tour of the spectacular Chicago lakefront. The evening went swimmingly and offered our guests a chance to unwind and network while enjoying great food and an open bar, against a backdrop of glittering skyscrapers.


2023 Continue reading
Cyber Week: Analyzing Internet traffic and e-commerce trends

Throughout the year, special events lead to changes in Internet traffic. We observed this with Thanksgiving in the US last week, where traffic dipped, and during periods like Black Friday (November 24, 2023) and Cyber Monday (November 27, 2023), where traffic spiked.
But how significant are these Cyber Week days on the Internet? Is it a global phenomenon? Does e-commerce interest peak on Black Friday or Cyber Monday, and are attacks increasing during this time? These questions are important to retailers and stakeholders around the world. At Cloudflare, we manage substantial traffic for our customers, which gives us a unique vantage from which to analyze traffic and attack patterns across large swaths of the Internet.
As we'll explore next, we observed varying trends. From a global perspective, there was a clear Internet traffic winner: Cyber Monday was the highest overall traffic day of 2023 (as it was for 2022), followed by Black Friday, and then Monday, November 21 from the same week. But zooming in, this pattern didn’t hold in some countries.
For this analysis, we examined anonymized samples of HTTP requests crossing our network, as well as DNS queries. Cloudflare's global data shows that peak request traffic occurred on Continue reading