KU041: Running Kubernetes On Nomad
In this episode, Michael, Kristina, and Adriana Villela discuss the challenges and benefits of running Kubernetes on Nomad. Adriana shares her experience of using Nomad in a data center, highlighting its simplicity and ease of deployment compared to Kubernetes. The speakers also discuss the differences between the two platforms, the concept of vendor lock-in, and... Read more »SC23 Data Transfer Node TCP Metrics
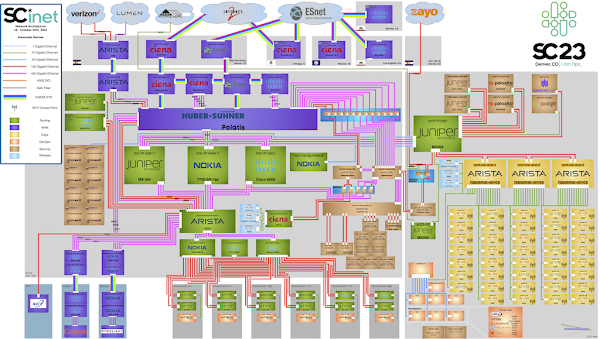
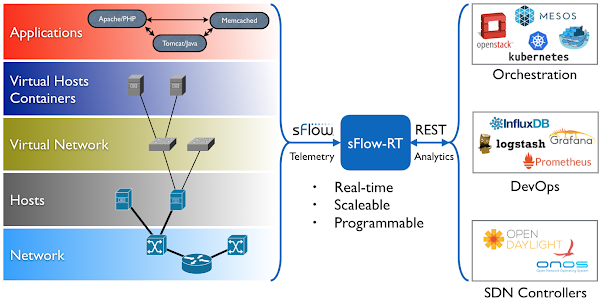
The dashboard shown above is based on the open source sflow-rt/dtn project. The dashboard shows data captured from The International Conference for High Performance Computing, Networking, Storage, and Analysis (SC23) being held this week in Denver.The dashboard displays data gathered from open source Host sFlow agents installed on Data Transfer Nodes (DTNs) run by the Caltech High Energy Physics Department and used for handling transfer of large scientific data sets (for example, accessing experiment data from the CERN particle accelerator). Network performance monitoring describes how the Host sFlow agents augment standard sFlow telemetry with measurements that the Linux kernel maintains as part of the normal operation of the TCP protocol stack.
The dashboard shows 5 large flows (greater than 50 Gigabits per Second). For each large flow being tracked, additional TCP performance metrics are displayed:
- RTT The round trip time observed between DTNs
- RTT Wait The amount of time that data waits on sender before it can be sent.
- RTT Sdev The standard deviation on observed RTT. This variation is a measure of jitter.
- Avg. Packet Size The average packet size used to send data.
- Packets in Flight The number of unacknowledged packets.
See Defining Flows for full range of Continue reading
Hedge 203: Terry Slattery on Network Automation

Terry Slattery joins Tom and Russ to continue the conversation on network automation—and why networks are not as automated as they should be. This is part one of a two-part series; the second part will be published in two weeks as Hedge episode 204.
Spider-Man, the Multiverse, and IPv6
As IPv6 usage continues its inevitable rise, now’s the time to admit you have or soon will have some IPv6 on the network and to engage with the IPv6 plane to incorporate it into your management strategy.Week in Review: Big Happenings on Multiple Wireless Fronts
A newly announced National Spectrum Strategy seeks to expand access to advanced wireless broadband networks and technologies.Introducing advanced session audit capabilities in Cloudflare One

The basis of Zero Trust is defining granular controls and authorization policies per application, user, and device. Having a system with a sufficient level of granularity to do this is crucial to meet both regulatory and security requirements. But there is a potential downside to so many controls: in order to troubleshoot user issues, an administrator has to consider a complex combination of variables across applications, user identity, and device information, which may require painstakingly sifting through logs.
We think there’s a better way — which is why, starting today, administrators can easily audit all active user sessions and associated data used by their Cloudflare One policies. This enables the best of both worlds: extremely granular controls, while maintaining an improved ability to troubleshoot and diagnose Zero Trust deployments in a single, simple control panel. Information that previously lived in a user’s browser or changed dynamically is now available to administrators without the need to bother an end user or dig into logs.

A quick primer on application authentication and authorization
Authentication and Authorization are the two components that a Zero Trust policy evaluates before allowing a user access to a resource.
Authentication is the process of verifying the identity Continue reading
IPB139: Avoiding Typical IPv6 Pitfalls
Network engineers and architects considering IPv6 can benefit from the experiences of those who have gone before them by avoiding the problems that have bedeviled other deployments. On today's show, your hosts discuss three typical pitfalls and how to get over or around them without falling in.
The post IPB139: Avoiding Typical IPv6 Pitfalls appeared first on Packet Pushers.
IPB139: Avoiding Typical IPv6 Pitfalls
Network engineers and architects considering IPv6 can benefit from the experiences of those who have gone before them by avoiding the problems that have bedeviled other deployments. On today’s show, your hosts discuss three typical pitfalls and how to get over or around them without falling in. Those IPv6 pitfalls include: IPv4 thinking Deploying ULA... Read more »The First Ever Network Automation Conference – AutoCon0
First let me just say that you have got to love a zero indexed conference! If you are a network engineer and you don’t know what that means we need to chat..and that situation was a key topic of the conference. In my mind the goal of the conference was to assess the state of READ MORE
The post The First Ever Network Automation Conference – AutoCon0 appeared first on The Gratuitous Arp.
Worth Reading: Cloudflare Control Plane Outage
Cloudflare experienced a significant outage in early November 2023 and published a detailed post-mortem report. You should read the whole report; here are my CliffsNotes:
- Regardless of how much redundancy you have, sometimes all systems will fail at once. Having redundant systems decreases the probability of total failure but does not reduce it to zero.
- As your systems grow, they gather hidden- and circular dependencies.
- You won’t uncover those dependencies unless you run a full-blown disaster recovery test (not a fake one)
- If you don’t test your disaster recovery plan, it probably won’t work when needed.
Also (unrelated to Cloudflare outage):
Worth Reading: Cloudflare Control Plane Outage
Cloudflare experienced a significant outage in early November 2023 and published a detailed post-mortem report. You should read the whole report; here are my CliffsNotes:
- Regardless of how much redundancy you have, sometimes all systems will fail at once. Having redundant systems decreases the probability of total failure but does not reduce it to zero.
- As your systems grow, they gather hidden- and circular dependencies.
- You won’t uncover those dependencies unless you run a full-blown disaster recovery test (not a fake one)
- If you don’t test your disaster recovery plan, it probably won’t work when needed.
Also (unrelated to Cloudflare outage):
IPv6, the DNS and Happy Eyeballs
If we are going to update RFC 3901, "DNS IPv6 Transport Guidelines," and offer a revised set of guidelines that are more positive guidelines about the use of IPv6 in the DNS, then what should such updated guidelines say?SC23 WiFi Traffic Heatmap
Additional use cases being demonstrated this week include, SC23 Dropped packet visibility demonstration and SC23 SCinet traffic.
D2C219: KubeConversations Part 1 – Platform Engineering
Welcome to a special edition of Day Two Cloud. Host Ned Bellavance traveled to KubeCon NA 2023 and spoke to vendors and open source maintainers about what's going on in the cloud-native ecosystem. This episode features conversations on platform engineering.
The post D2C219: KubeConversations Part 1 – Platform Engineering appeared first on Packet Pushers.