Introducing notifications for HTTP Traffic Anomalies

When it comes to managing Internet properties, the difference between a small technical hiccup and major incident is often a matter of speed. Proactive alerting plays a crucial role, which is why we were excited when we released HTTP Error Rate notifications — giving administrators visibility into when end users are experiencing errors.
But what if there are issues that don't show up as errors, like a sudden drop in traffic, or a spike?
Today, we're excited to announce Traffic Anomalies notifications, available to enterprise customers. These notifications trigger when Cloudflare detects unexpected changes in traffic, giving another valuable perspective into the health of your systems.
Unexpected changes in traffic could be indicative of many things. If you run an ecommerce site and see a spike in traffic that could be great news — maybe customers are flocking to your sale, or you just had an ad run on a popular TV show. However, it could also mean that something is going wrong: maybe someone accidentally turned off a firewall rule, and now you’re seeing more malicious traffic. Either way, you might want to know that something has changed.
Similarly, a sudden drop in traffic could mean many things. Perhaps Continue reading
Forwarding BUM Frames in VXLAN Network With Static Ingress Replication
In the last post we used multicast to forward BUM frames. In this post, static ingress replication is used which removes the requirement for multicast in the underlay. Before setting this up, let’s do a comparison of multicast vs ingress replication. To make this interesting, let’s use a larger topology consisting of 2 Spines and 32 Leafs:
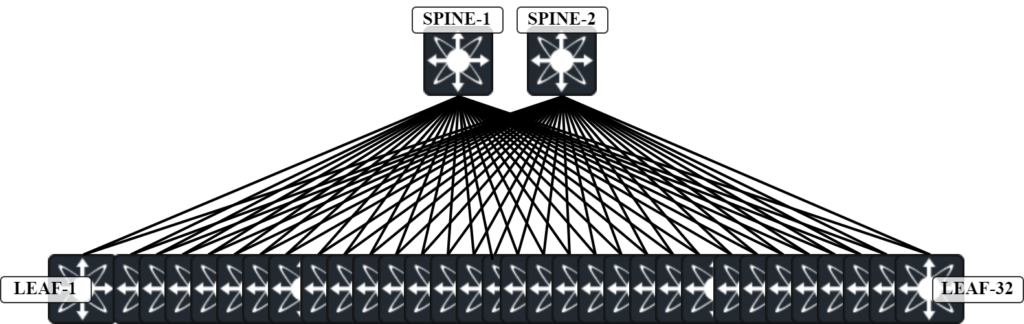
Assume that all Leafs have the same VNIs. In a scenario with multicast, Leaf-1 sends for example an ARP request encapsulated in multicast towards Spine-1. This is a single frame. Spine-1 then replicates this frame and sends it on all its links towards the Leafs:
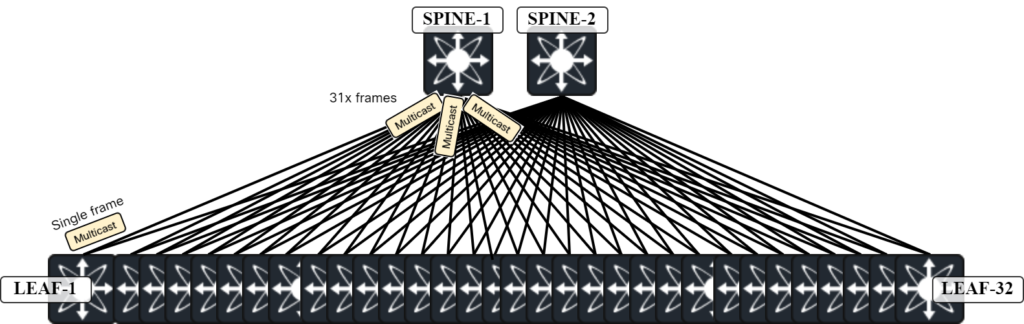
This is very efficient as a single frame is sent by Leaf-1 and then 31 copies are sent on the other links to the Leafs. If the ARP request is 110 bytes, then a total of 32 x 110 = 3520 bytes have been consumed to send this ARP request. This is optimal forwarding from a resource consumption perspective and one of the strengths of multicast. Now let’s compare that to ingress replication. With ingress replication, Leaf-1 sends 31x copies of the frame (with different destination IP) towards Spine-1. Spine-1 then forwards those frames on each link towards Continue reading
Tech Bytes: Nokia’s ChatGPT App Lets Engineers Query The Network (Sponsored)
AI is making its way into network operations, and on today’s episode, sponsored by Nokia, we talk about how Nokia has developed a ChatGPT-based application that runs on its SR Linux network OS. Network engineers can use this app to query about network state, ask troubleshooting questions, check configurations, search logs, and quickly sort through reams of documentation.
The post Tech Bytes: Nokia’s ChatGPT App Lets Engineers Query The Network (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Nokia’s ChatGPT App Lets Engineers Query The Network (Sponsored)
AI is making its way into network operations, and on today’s episode, sponsored by Nokia, we talk about how Nokia has developed a ChatGPT-based application that runs on its SR Linux network OS. Network engineers can use this app to query about network state, ask troubleshooting questions, check configurations, search logs, and quickly sort through reams of documentation.Network Break 453: Cisco Invests In Quantum Networking; SmartNIC Sales Surge; Intel Unplugs Another Business
Today's episode includes Cisco patching a critical vulnerability affecting IOS-XE gear, startup Prosimo releasing a cost calculator to help network engineers track their public cloud networking costs, and Juniper integrating its SD-WAN to the AWS cloud WAN. We also cover Cisco's investment in a quantum networking startup, growing DPU sales, and Intel divesting from pluggable optical modules.
The post Network Break 453: Cisco Invests In Quantum Networking; SmartNIC Sales Surge; Intel Unplugs Another Business appeared first on Packet Pushers.
NB453: Cisco Invests In Quantum Networking; SmartNIC Sales Surge; Intel Unplugs Another Business
Today's episode includes Cisco patching a critical vulnerability affecting IOS-XE gear, startup Prosimo releasing a cost calculator to help network engineers track their public cloud networking costs, and Juniper integrating its SD-WAN to the AWS cloud WAN. We also cover Cisco's investment in a quantum networking startup, growing DPU sales, and Intel divesting from pluggable optical modules.Weird: vJunos Evolved 23.2R1.5 Declines DHCP Address
It’s time for a Halloween story: imagine the scary scenario in which a DHCP client asks for an address, gets it, and then immediately declines it. That’s what I’ve been experiencing with vJunos Evolved release 23.2R1.15.
Before someone gets the wrong message: I’m not criticizing Juniper or vJunos.
- Juniper did a great job releasing a no-hassles-to-download virtual appliance.
- DHCP assignment of management IPv4 address worked with vJunos Evolved release 23.1R1.8
- There were reports that the DHCP assignment process in vJunos Evolved 23.1R1.8 was not reliable, but it worked for me so far, so I’m good to go as long as I can run the older release.
- I might get to love vJunos Evolved. Boot- and configuration times are very reasonable.
However, it looks like something broke in vJunos release 23.2, and it would be nice to figure out what the workaround might be.
Weird: vJunos Evolved 23.2R1.5 Declines DHCP Address
It’s time for a Halloween story: imagine the scary scenario in which a DHCP client asks for an address, gets it, and then immediately declines it. That’s what I’ve been experiencing with vJunos Evolved release 23.2R1.15.
Before someone gets the wrong message: I’m not criticizing Juniper or vJunos.
- Juniper did a great job releasing a no-hassles-to-download virtual appliance.
- DHCP assignment of management IPv4 address worked with vJunos Evolved release 23.1R1.8
- There were reports that the DHCP assignment process in vJunos Evolved 23.1R1.8 was not reliable, but it worked for me so far, so I’m good to go as long as I can run the older release.
- I might get to love vJunos Evolved. Boot- and configuration times are very reasonable.
However, it looks like something broke in vJunos release 23.2, and it would be nice to figure out what the workaround might be.
Top Tips for a Strong Zero Trust Architecture
A zero trust architecture reduces a network's attack surface and lowers the risk of a data breach. Here are some tips when implementing such an architecture.Worth Exploring: BGP from Theory to Practice
My good friend Tiziano Tofoni finally created an English version of his evergreen classic BGP from theory to practice with co-authors Antonio Prado and Flavio Luciani.
I had the Italian version of the book since the days I was running SDN workshops with Tiziano in Rome, and it’s really nice to see they finally decided to address a wider market.
Also, you know what would go well with that book? Free open-source BGP configuration labs of course 😉
Worth Exploring: BGP from Theory to Practice
My good friend Tiziano Tofoni finally created an English version of his evergreen classic BGP from theory to practice with co-authors Antonio Prado and Flavio Luciani.
I had the Italian version of the book since the days I was running SDN workshops with Tiziano in Rome, and it’s really nice to see they finally decided to address a wider market.
Also, you know what would go well with that book? Free open-source BGP configuration labs of course 😉
Forwarding BUM Frames in VXLAN Network With Multicast in Underlay
There are two main methods that can be used to forward broadcast, unknown unicast, and multicast (BUM) frames in a VXLAN network:
- Ingress replication.
- Multicast in underlay.
In this post, we take a detailed look at how multicast can be used to forward BUM frames by running multicast in the underlay. We are using the topology from my Building a VXLAN Lab Using Nexus9000v post. The Spine switches are configured using the Nexus feature Anycast RP. That is, no MSDP is used between the RPs. To be able to forward broadcast frames such as ARP in our topology, the following is required:
- The VTEPs must signal that they want to join the shared tree for 239.0.0.1 (to receive multicast) using a PIM Join.
- The VTEPs must signal that they intend to send multicast for 239.0.0.1 on the source tree using a PIM Register.
- The RPs must share information about the sources that they know of by forwarding PIM Register messages.
- The VTEP must encapsulate ARP packets in VXLAN and forward in the underlay using multicast.
The Leaf switches have the following configuration to enable multicast:
ip pim rp-address 192.0.2.255 group-list 224. Continue reading
Hedge 200: Automation with Ethan Banks
We’ve been on a long streak of discussions about automation, why it works, why it isn’t working, and what the networking industry can do about it. For this episode, we’re joined by the indubitable Ethan Banks. If you don’t think there’s anything left to say, you’ve not yet listened to Ethan!
Heavy Networking 707: Getting Real With Selector’s AIOps (Sponsored)
AI and machine learning are finally being applied to networking in meaningful ways. On today's sponsored show we talk with Selector about its AIOps platform, which ingests networking logs, flows, configurations, SNMP, and other telemetry to detect patterns, spot problems, and provide contextual insights to help network engineers do their jobs better. We speak with Selector about what it is, how it works, and concrete use cases.
The post Heavy Networking 707: Getting Real With Selector’s AIOps (Sponsored) appeared first on Packet Pushers.