Cache Rules go GA: precision control over every part of your cache
One year ago we introduced Cache Rules, a new way to customize cache settings on Cloudflare. Cache Rules provide greater flexibility for how users cache content, offering precise controls, a user-friendly API, and seamless Terraform integrations. Since it was released in late September 2022, over 100,000 websites have used Cache Rules to fine-tune their cache settings.
Today, we're thrilled to announce that Cache Rules, along with several other Rules products, are generally available (GA). But that’s not all — we're also introducing new configuration options for Cache Rules that provide even more options to customize how you cache on Cloudflare. These include functionality to define what resources are eligible for Cache Reserve, what timeout values should be respected when receiving data from your origin server, which custom ports we should use when we cache content, and whether we should bypass Cloudflare’s cache in the absence of a cache-control header.
Cache Rules give users full control and the ability to tailor their content delivery strategy for almost any use case, without needing to write code. As Cache Rules go GA, we are incredibly excited to see how fast customers can achieve their perfect cache strategy.
History of Customizing Cache Continue reading
netlab 1.6.4: Support for Multi-Lab Projects; More BGP Goodies
Features in netlab release 1.6.4 were driven primarily by the needs of my BGP labs project:
- bgp.session plugin (formerly known as ebgp.utils plugin) got support for BFD, passive BGP peers and remove-private-as option.
- bgp.policy plugin implements basic BGP routing policy tools, including per-neighbor weights, local preference and MED.
- You can enable external tools in user defaults and use default groups to create user- or project-wide groups in the defaults files.
- Version-specific lab topology files allow netlab to select a lab topology that is a best fit for the netlab release you’re running.
Numerous platforms already support the new BGP nerd knobs:
netlab 1.6.4: Support for Multi-Lab Projects; More BGP Goodies
Features in netlab release 1.6.4 were driven primarily by the needs of my BGP labs project:
- bgp.session plugin (formerly known as ebgp.utils plugin) got support for BFD, passive BGP peers and remove-private-as option.
- bgp.policy plugin implements basic BGP routing policy tools, including per-neighbor weights, local preference and MED.
- You can enable external tools in user defaults and use default groups to create user- or project-wide groups in the defaults files.
- Version-specific lab topology files allow netlab to select a lab topology that is a best fit for the netlab release you’re running.
Numerous platforms already support the new BGP nerd knobs:
Setting up secure wifi
If you don’t set a password on your wifi, then not only can anyone connect, but it’s not even encrypted. This means that even when an open network gives you a captive portal, that could actually be an attacker giving you a fake portal. Even if the portal is HTTPS, because you may be connected to https://evil-fake-portal.com.
That is solved in WPA3, where even open networks become encrypted.
Of course, the attacker can just set up a fake access point, and you’ll connect, none the wiser. Even if the network has a password, the attacker only needs to know that password in order to fake it.
Before WPA3, passwords can easily be brute forced offline. A few years ago I calculated that it would cost about $70 to crack the default generated 8 character random passwords used by a popular ISP here in London, using some GPUs in Google Cloud. I’m sure it’s cheaper now.
That’s potentially years of free use of your neighbours wifi, for just the cost of a couple of months of paying for your own.
But that’s illegal, of course. This post is about protecting you against these attacks, not performing them.
If you Continue reading
Tech Bytes: Addressing New Service Provider Routing Applications With Nokia’s FPcx Silicon (Sponsored)
Today's Tech Bytes podcast explores custom silicon with sponsor Nokia. Nokia has recently launched its new FPcx chip for Nokia routers. We’ll talk about the features and capabilities in the new silicon, and the value to service providers and enterprises that custom silicon can bring.
The post Tech Bytes: Addressing New Service Provider Routing Applications With Nokia’s FPcx Silicon (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Addressing New Service Provider Routing Applications With Nokia’s FPcx Silicon (Sponsored)
Today's Tech Bytes podcast explores custom silicon with sponsor Nokia. Nokia has recently launched its new FPcx chip for Nokia routers. We’ll talk about the features and capabilities in the new silicon, and the value to service providers and enterprises that custom silicon can bring.The Evolving Threat Landscape: What’s Next for Security?
In light of the evolving threat of credential abuse, a radical shift in how we view identity is a good step toward stopping attackers and solving cybersecurity challenges.Network Break 452: Cisco Makes You Feel Vulnerable; Broadcom 25.6Tbps Routing ASIC Targets Custom Silicon; China Mandates IPv6
This week's IT news podcast covers a serious Cisco exploit against IOS XE, new firewalls from Juniper, Broadcom's hopes to capture the routing market with merchant silicon, more movement on restoring net neutrality in the US, and more.
The post Network Break 452: Cisco Makes You Feel Vulnerable; Broadcom 25.6Tbps Routing ASIC Targets Custom Silicon; China Mandates IPv6 appeared first on Packet Pushers.
NB452: Cisco Makes You Feel Vulnerable; Broadcom 25.6Tbps Routing ASIC Targets Custom Silicon; China Mandates IPv6
This week's IT news podcast covers a serious Cisco exploit against IOS XE, new firewalls from Juniper, Broadcom's hopes to capture the routing market with merchant silicon, more movement on restoring net neutrality in the US, and more.Cyber attacks in the Israel-Hamas war

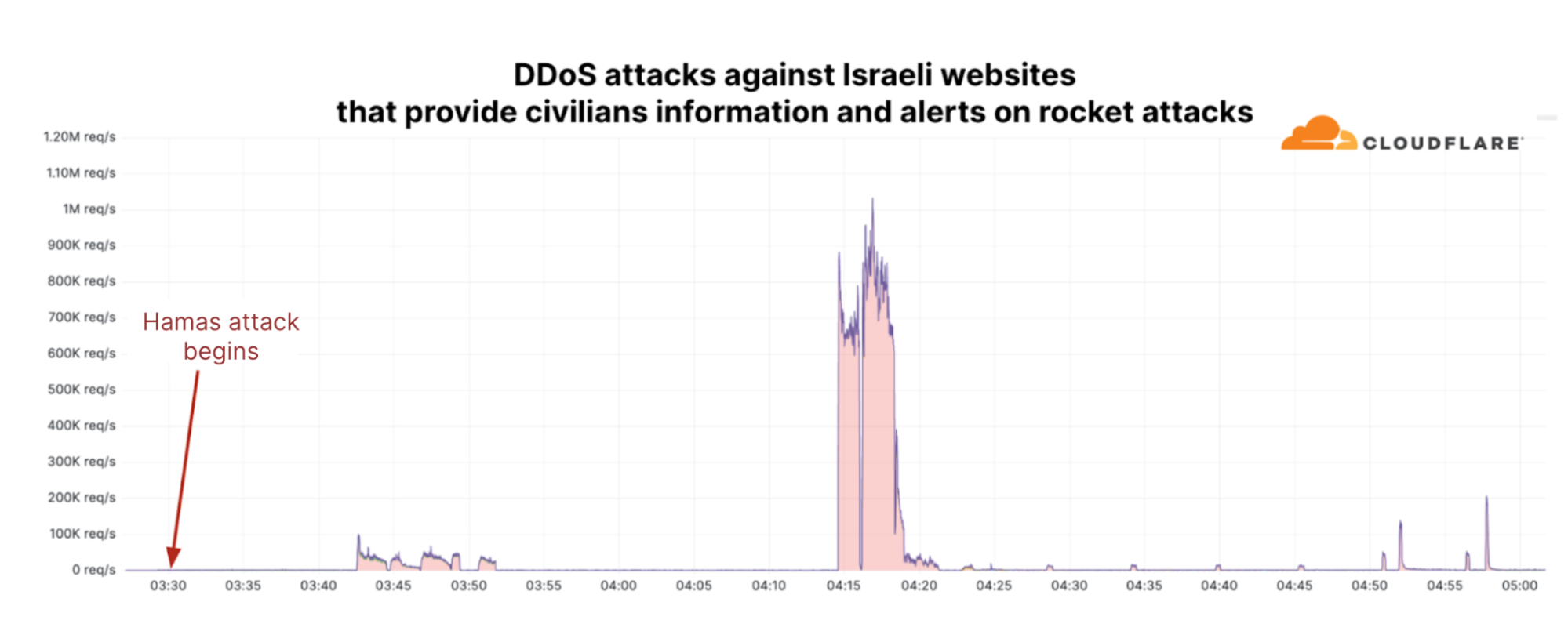
On October 7, 2023, at 03:30 GMT (06:30 AM local time), Hamas attacked Israeli cities and fired thousands of rockets toward populous locations in southern and central Israel, including Tel Aviv and Jerusalem. Air raid sirens began sounding, instructing civilians to take cover.
Approximately twelve minutes later, Cloudflare systems automatically detected and mitigated DDoS attacks that targeted websites that provide critical information and alerts to civilians on rocket attacks. The initial attack peaked at 100k requests per second (rps) and lasted ten minutes. Forty-five minutes later, a second much larger attack struck and peaked at 1M rps. It lasted six minutes. Additional smaller DDoS attacks continued hitting the websites in the next hours.
Not just DDoS attacks
Multiple Israeli websites and mobile apps have become targets of various pro-Palestinian hacktivist groups. According to Cybernews, one of those groups, AnonGhost, exploited a vulnerability in a mobile app that alerts Israeli civilians of incoming rockets, “Red Alert: Israel”. The exploit allowed them to intercept requests, expose servers and APIs, and send fake alerts to some app users, including a message that a “nuclear bomb is coming Continue reading
Video: History of BGP Route Leaks
I’ll be talking about Internet routing security at the Deep conference in a few days, and just in case you won’t be able to make it1 ;) here’s the first bit of my talk: a very brief history of BGP route leaks2.
Note: you’ll find more Network Security Fallacies videos in the How Networks Really Work webinar.
Video: History of BGP Route Leaks
I’ll be talking about Internet routing security at the Deep conference in a few days, and just in case you won’t be able to make it1 ;) here’s the first bit of my talk: a very brief history of BGP route leaks2.
Note: you’ll find more Network Security Fallacies videos in the How Networks Really Work webinar.
VPP IXP Gateway – Part 1
About this series
Ever since I first saw VPP - the Vector Packet Processor - I have been deeply impressed with its performance and versatility. For those of us who have used Cisco IOS/XR devices, like the classic ASR (aggregation service router), VPP will look and feel quite familiar as many of the approaches are shared between the two.
There’s some really fantastic features in VPP, some of which are lesser well known, and not always very well documented. In this article, I will describe a unique usecase in which I think VPP will excel, notably acting as a gateway for Internet Exchange Points.
In this first article, I’ll take a closer look at three things that would make such a gateway possible: bridge domains, MAC address filtering and traffic shaping.
Introduction
Internet Exchanges are typically L2 (ethernet) switch platforms that allow their connected members to exchange traffic amongst themselves. Not all members share physical locations with the Internet Exchange itself, for example the IXP may be at NTT Zurich, but the member may be present in Interxion Zurich. For smaller clubs, like IPng Networks, it’s not always financially feasible (or desirable) to order a dark fiber between two adjacent Continue reading
How Cloudflare mitigated yet another Okta compromise
On Wednesday, October 18, 2023, we discovered attacks on our system that we were able to trace back to Okta – threat actors were able to leverage an authentication token compromised at Okta to pivot into Cloudflare’s Okta instance. While this was a troubling security incident, our Security Incident Response Team’s (SIRT) real-time detection and prompt response enabled containment and minimized the impact to Cloudflare systems and data. We have verified that no Cloudflare customer information or systems were impacted by this event because of our rapid response. Okta has now released a public statement about this incident.
This is the second time Cloudflare has been impacted by a breach of Okta’s systems. In March 2022, we blogged about our investigation on how a breach of Okta affected Cloudflare. In that incident, we concluded that there was no access from the threat actor to any of our systems or data – Cloudflare’s use of hard keys for multi-factor authentication stopped this attack.
The key to mitigating this week’s incident was our team’s early detection and immediate response. In fact, we contacted Okta about the breach of their systems before they had notified us. The attacker used an open Continue reading