Verizon and AT&T Exit From Cloud Business Applauded by Analysts
 Enterprises want carrier-agnostic solutions.
Enterprises want carrier-agnostic solutions.
Show 338: Tales From The Trenches With Connection (Sponsored)
Todays Weekly Show brings you tales from the trenches with our sponsor Connection. As a national solutions provider, Connection sees all sorts of things at all sorts of sites, and thus has interesting stories to tell. The post Show 338: Tales From The Trenches With Connection (Sponsored) appeared first on Packet Pushers.
Google’s RailTel Project Uses Cloud-Native NFV to Deliver WiFi to Millions
 "When you transform the control plane architecture, you alter the capex structure."
"When you transform the control plane architecture, you alter the capex structure."
User-guided caching in Docker for Mac
Recent Docker releases (17.04 CE Edge onwards) bring significant performance improvements to bind-mounted directories on macOS. (Docker users on the stable channel will see the improvements in the forthcoming 17.06 release.) Commands for bind-mounting directories have new options to selectively enable caching.
Containers that perform large numbers of read operations in mounted directories are the main beneficiaries. Here’s an illustration of the improvements in a few tools and applications in common use among Docker for Mac users: go list is 2.5× faster; symfony is 2.7× faster, and rake is 3.5× faster, as illustrated by the following graphs:
go list (2.5× speedup)

go list ./... in the moby/moby repository
symfony (2.7× speedup)

curl of the main page of the Symfony demo app
rake (3.5× speedup)

rake -T in @hirowatari’s benchmark
For more details about how and when to enable caching, and what’s going on under the hood, read on.
Basics of bind-mounting
A defining characteristic of containers is isolation: by default, many parts of the execution environment of a container are isolated both from other containers and from the host system. In the filesystem, isolation shows up as layering: the filesystem Continue reading
Keeping Up with Storage Demands by Pairing vNAS and vSAN
 This combined approach will give enterprises the flexibility and scalability they need.
This combined approach will give enterprises the flexibility and scalability they need.
Meet The Brand New DNS Analytics Dashboard

Have you noticed something new in your Cloudflare analytics dashboard this morning? You can now see detailed DNS analytics for your domains on Cloudflare.
If you want to skip to the punch and start exploring, go check it out here. Otherwise, hop on the DNS magic school bus - and let us show you all the neat stats in your now-available DNS analytics.
DNS analytics dashboard: What does it know? Does it know things? Let’s find out.
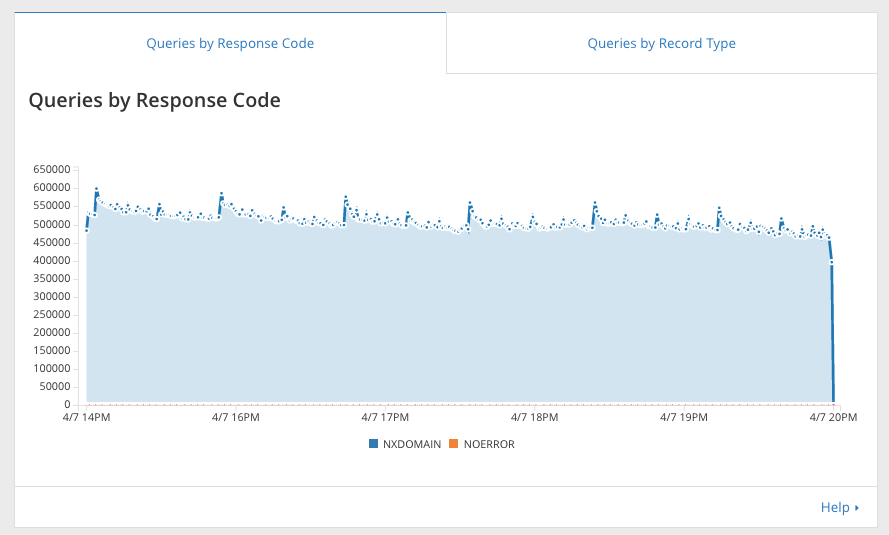
At the top of the DNS analytics dashboard you can see your DNS traffic health. This “Queries by Response Codes” graph breaks down queries by what response code Cloudflare DNS answered to the visitor. Like HTTP response codes, DNS response codes give an indication of what is happening behind the scenes. Mostly you will just see NOERROR, the HTTP 200 of DNS response codes, and NXDOMAIN, the HTTP 404 of DNS response codes. NXDOMAIN is particularly interesting - what are people querying for that doesn’t exist?
If you are an enterprise customer and you want to know what all the NXDOMAIN queries are, just scroll down a little bit where we show you the top queries for your domain and top queries for Continue reading
BGP over GRE Tunnel
The post BGP over GRE Tunnel appeared first on Noction.
What IPv6 Transition Mechanisms Are Actually Being Used?
An engineer watching my IPv6 Transition Mechanisms webinar sent me this question:
We would appreciate any insight you might have as to which transitional mechanisms the ISPs are actually deploying.
All of them ;)
Read more ...

