The Case for Service Assurance in Carrier SDN
 Service assurance is the missing link in carrier SDN.
Service assurance is the missing link in carrier SDN.
SDN Lesson #2 – Introducing Faucet as an OpenFlow Controller
Welcome back to a new article about SDN - this time introducing an OpenFlow controller called Faucet, developed as a RYU application by New Zeeland's Research and Education (REANNZ). In this article, I am not going to write about Faucet's architecture and features since you can read about it on its github page or here or here>. Instead, I will describe the setup used for a demo presented at the Irish Network Operators Group 11th meetup (iNOG::B).
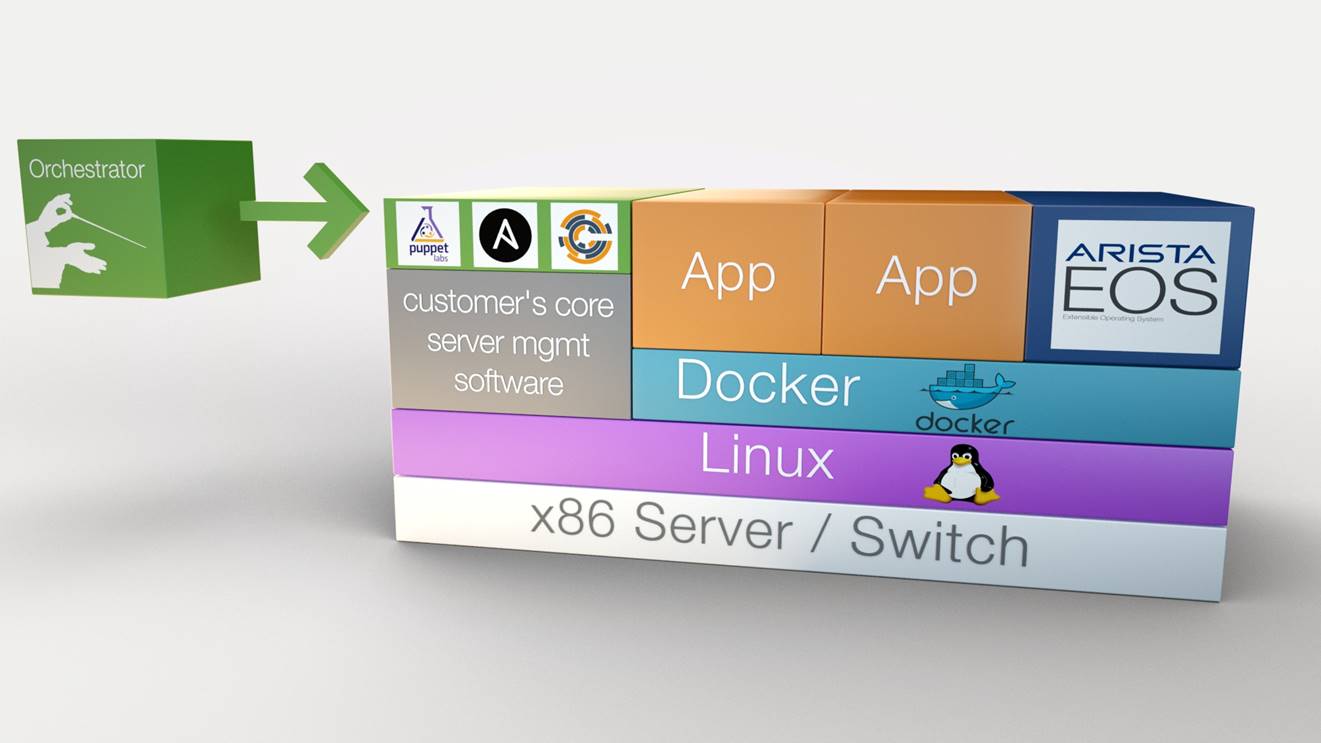
The Catalyst for Cloud Networking with Containerization
Today’s applications are connected both to users and other applications, increasing traffic and profoundly affecting performance. Recently, there has been much discussion around the Application Performance Management (APM) category. This got me thinking about new cloud migration versus legacy application tools. Is the industry being myopic and dealing with silos?