BGP Labs: Simple Routing Policy Tools
The first set of BGP labs covered the basics, the next four will help you master simple routing policy tools (BGP weights, AS-path filters, prefix filters) using real-life examples:
- Use BGP weights to prefer one of the upstream providers
- Prevent route leaking between upstream providers with an AS-path filter
- Filter prefixes advertised by your autonomous system with a prefix list
- Minimize the size of your BGP table with inbound filters
The labs are best used with netlab (it supports BGP on almost 20 different devices), but you could use any system you like (including GNS3 and CML/VIRL). If you’re stubborn enough it’s possible to make them work with the physical gear, but don’t ask me for help. For more details, read the Installation and Setup documentation.
BGP Labs: Simple Routing Policy Tools
The first set of BGP labs covered the basics; the next four will help you master simple routing policy tools (BGP weights, AS-path filters, prefix filters) using real-life examples:
- Use BGP weights to prefer one of the upstream providers
- Prevent route leaking between upstream providers with an AS-path filter
- Filter prefixes advertised by your autonomous system with a prefix list
- Minimize the size of your BGP table with inbound filters
The labs are best used with netlab (it supports BGP on almost 20 different devices), but you could use any system you like (including GNS3 and CML/VIRL). For more details, read the Installation and Setup documentation.
Valley-free Routing in Leaf and Spine Topology
Valley-free routing is a concept that may not be well known but that is relevant to datacenter design. In this post, we’ll valley-free routing based on a leaf and spine topology.
There are many posts about leaf and spine topology and the benefits. To summarize, some of the most prominent advantages are:
- Predictable number of hops between any two nodes.
- All links are available for usage providing high amount of bisection bandwidth (ECMP).
- The architecture is easy to scale out.
- Redundant and resilient.
Now, what does this have to do with valley-free routing? To understand what valley-free routing is, first let’s take a look at the expected traffic flow in a leaf and spine topology:
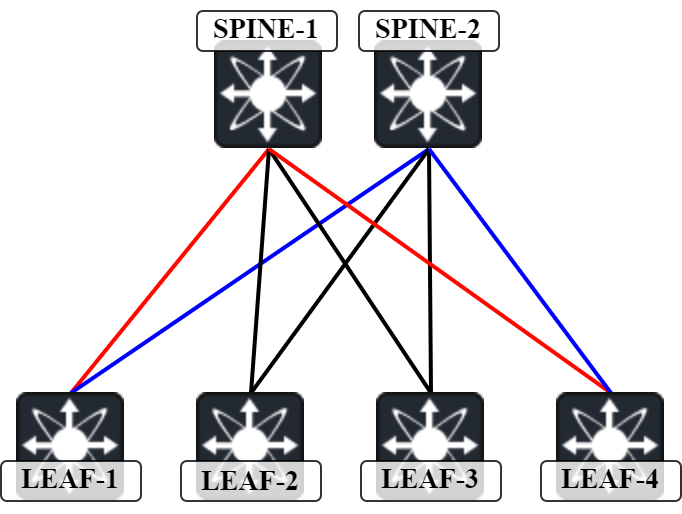
For traffic between Leaf1 and Leaf4, the two expected paths are:
- Red path – Leaf-1 to Spine-1 to Leaf-4.
- Blue path – Leaf-1 to Spine-2 to Leaf-4.
This means that there is only one intermediate hop between Leaf1 and Leaf4. Let’s confirm with a traceroute:
Leaf1# traceroute 203.0.113.4 traceroute to 203.0.113.4 (203.0.113.4), 30 hops max, 48 byte packets 1 Spine2 (192.0.2.2) 1.831 ms 1.234 ms 1.12 ms 2 Leaf4 (203. Continue reading
Linux Networking – Source IP address selection
Any network device, be it a transit router or a host, usually has multiple IP addresses assigned to its interfaces. One of the first things we learn as network engineers is how to determine which IP address is used for the locally-sourced traffic. However, the default scenario can be changed in a couple of different ways and this post is a brief documentation of the available options.
The Default Scenario
Whenever a local application decides to connect to a remote network endpoint, it creates a network socket, providing a minimal amount of details required to build and send a network packet. Most often, this information includes a destination IP and port number as you can see from the following abbreviated output:
$ strace -e trace=network curl http://example.com
socket(AF_INET, SOCK_STREAM, IPPROTO_TCP) = 6
setsockopt(6, SOL_TCP, TCP_NODELAY, [1], 4) = 0
setsockopt(6, SOL_SOCKET, SO_KEEPALIVE, [1], 4) = 0
setsockopt(6, SOL_TCP, TCP_KEEPIDLE, [60], 4) = 0
setsockopt(6, SOL_TCP, TCP_KEEPINTVL, [60], 4) = 0
connect(6, {sa_family=AF_INET, sin_port=htons(80), sin_addr=inet_addr("93.184.216.34")}, 16)
While this output does not show the DNS resolution part (due to getaddrinfo() not being a syscall), we can see that the only user-specific input information provided by an application ( Continue reading
Hedge 193: Network Automation with the Network Automation Forum
Year after year network engineering media, vendors, and influencers talk about the importance of network automation—and yet according to surveys, most network operators still have not automated their network operations. In this episode of the Hedge, part 1 of 2, Chris Grundemann and Scott Robohn join the Hedge to give their ideas on why network automation isn’t happening, and how we can resolve the many blockers to automation.
Calico monthly roundup: August 2023
Welcome to the Calico monthly roundup: August edition! From open source news to live events, we have exciting updates to share—let’s get into it!

*NEW* The State of Calico Open Source: Usage & Adoption Report 2023 Get insights into Calico’s adoption across container and Kubernetes environments, in terms of platforms, data planes, and policies. |

Customer case study: HanseMerkur Using Calico, HanseMerkur was able to reduce infrastructure overhead and achieve organizational compliance. Read our new case study to find out how. |
Open source news
- Calico Live – Join the Calico community every Wednesday at 2:00 pm ET for a live discussion about learning how to leverage Calico and Kubernetes for networking and security. We will explore Kubernetes security and policy design, network flow logs and more. Join us live on LinkedIn or YouTube.
- CNCF webinar – Watch the recording of our CNCF live webinar, where we talk about eBPF advantages and troubleshooting. Watch now.
- Calico for Microsoft Azure – Learn technical differences between different Azure networking options for Microsoft AKS environments and tradeoff analysis. Read blog post.
- Podcast – Listen to this joint podcast with Calico Big Cat, Parth Goswami, where they answer the Continue reading
Heavy Networking 697: Getting Operational Visibility Into The Networks That Matter (Sponsored)
In today's sponsored Heavy Networking we explore new features in Cisco Thousand Eyes, an operational tool based on visibility and observability of public and private network. Thousand Eyes has continued to grow into complex operational areas such AWS Network Path, Webex performance, and integrations with Meraki to help you identify and fix network and application performance problems.
The post Heavy Networking 697: Getting Operational Visibility Into The Networks That Matter (Sponsored) appeared first on Packet Pushers.
Heavy Networking 697: Getting Operational Visibility Into The Networks That Matter (Sponsored)
In today's sponsored Heavy Networking we explore new features in Cisco Thousand Eyes, an operational tool based on visibility and observability of public and private network. Thousand Eyes has continued to grow into complex operational areas such AWS Network Path, Webex performance, and integrations with Meraki to help you identify and fix network and application performance problems.Overcoming the Wall
I was watching a Youtube video this week that had a great quote. The creator was talking about sanding a woodworking project and said something about how much it needed to be sanded.
Whenever you think you’re done, that’s when you’ve just started.
That statement really resonated with me. I’ve found that it’s far too easy to think you’re finished with something right about the time you really need to hunker down and put in extra effort. In running they call it “hitting the wall” and it usually marks the point when your body is out of energy. There’s often another wall you hit mentally before you get there, though, and that’s the one that needs to be overcome with some tenacity.
The Looming Rise
If your brain is like mine you don’t like belaboring something. The mind craves completion and resolution. Once you’ve solved a problem it’s done and finished. No need to continue on with it once you’ve reached a point where it’s good enough. Time to move on to something else that’s new and exciting and a source of dopamine.
However, that feeling of being done with something early on is often a false sense of completion. Continue reading
Improving Worker Tail scalability


Being able to get real-time information from applications in production is extremely important. Many times software passes local testing and automation, but then users report that something isn’t working correctly. Being able to quickly see what is happening, and how often, is critical to debugging.
This is why we originally developed the Workers Tail feature - to allow developers the ability to view requests, exceptions, and information for their Workers and to provide a window into what’s happening in real time. When we developed it, we also took the opportunity to build it on top of our own Workers technology using products like Trace Workers and Durable Objects. Over the last couple of years, we’ve continued to iterate on this feature - allowing users to quickly access logs from the Dashboard and via Wrangler CLI.
Today, we’re excited to announce that tail can now be enabled for Workers at any size and scale! In addition to telling you about the new and improved scalability, we wanted to share how we built it, and the changes we made to enable it to scale better.
Why Tail was limited
Tail leverages Durable Objects to handle coordination between the Worker producing messages and Continue reading
Patching vs. Uptime: What You Need to Know About Securing Industrial IoT Networks
Misconfiguration, ransomware, and alert fatigue could lead to downtime on industrial IoT networks in industries such as manufacturing and energy.Nexus9000v and “Missing” Routes
I have built my lab for VXLAN on the Nexus9300v platform. Since I have a leaf and spine topology, there are ECMP routes towards the spines for the other leafs’ loopbacks. When performing labs though, I noticed that I didn’t have any ECMP routes in the forwarding table (FIB). They are in the RIB, though:
Leaf1# show ip route 203.0.113.4
IP Route Table for VRF "default"
'*' denotes best ucast next-hop
'**' denotes best mcast next-hop
'[x/y]' denotes [preference/metric]
'%<string>' in via output denotes VRF <string>
203.0.113.4/32, ubest/mbest: 2/0
*via 192.0.2.1, Eth1/1, [110/81], 1w0d, ospf-UNDERLAY, intra
*via 192.0.2.2, Eth1/2, [110/81], 1w0d, ospf-UNDERLAY, intra
There is only one entry in the FIB, though:
Leaf1# show forwarding route 203.0.113.4? A.B.C.D Display single longest match route A.B.C.D/LEN Display single exact match route Leaf1# show forwarding route 203.0.113.4/32 slot 1 ======= IPv4 routes for table default/base ------------------+-----------------------------------------+----------------------+-----------------+----------------- Prefix | Next-hop | Interface | Labels | Partial Install ------------------+-----------------------------------------+----------------------+-----------------+----------------- 203.0.113.4/32 192.0.2.1 Ethernet1/1
This seemed strange to me and I was concerned that maybe something was Continue reading
Lifetime ipSpace.net Subscription
More than thirteen years after I started creating vendor-neutral webinars, it’s time for another change1: the ipSpace.net subscriptions became perpetual. If you have an active ipSpace.net subscription, it will stay valid indefinitely2 (and I’ll stop nagging you with renewal notices).
Wow, Free Lunch?
Sadly, that’s not the case.
Lifetime ipSpace.net Subscription
More than thirteen years after I started creating vendor-neutral webinars, it’s time for another change1: the ipSpace.net subscriptions became perpetual. If you have an active ipSpace.net subscription, it will stay valid indefinitely2 (and I’ll stop nagging you with renewal notices).
Wow, Free Lunch?
Sadly, that’s not the case.
