SoftWatch Releases SaaS to Help Enterprises Migrate to Cloud
 Determine which apps are most suitable to run on the cloud.
Determine which apps are most suitable to run on the cloud.
Data Deduplication: 7 Factors To Consider
Deduplication has become a standard feature in storage arrays. Here are some issues to weigh with the technology.
This Is Why I’m Not Doing SD-WAN Webinars
One of my long-time regular readers sent me this question:
I was wondering if you have had any interest in putting together an SD-WAN overview/update similar to what you do with data center fabrics where you cover the different product offerings, differentiators, solution scorecard…
That would be a good idea. Unfortunately the SD-WAN vendors aren’t exactly helping.
Read more ...Industry First Micro-segmentation Cybersecurity Benchmark Released
 The VMware NSX Micro-segmentation Cybersecurity Benchmark report has been released! As previewed in part six of the Micro-segmentation Defined – NSX Securing Anywhere blog series , independent cyber risk management advisor and assessor Coalfire was sponsored by VMware to create an industry first Micro-segmentation Cybersecurity Benchmark report. Coalfire conducted an audit of the VMware NSX micro-segmentation capabilities to develop this benchmark report detailing the efficacy of NSX as a security platform through a detailed “micro-audit” process, testing NSX against simulated zero-day threats.
The VMware NSX Micro-segmentation Cybersecurity Benchmark report has been released! As previewed in part six of the Micro-segmentation Defined – NSX Securing Anywhere blog series , independent cyber risk management advisor and assessor Coalfire was sponsored by VMware to create an industry first Micro-segmentation Cybersecurity Benchmark report. Coalfire conducted an audit of the VMware NSX micro-segmentation capabilities to develop this benchmark report detailing the efficacy of NSX as a security platform through a detailed “micro-audit” process, testing NSX against simulated zero-day threats.
Testing included five different network design patterns, and demonstrated how NSX micro-segmentation can provide stateful, distributed, policy-based protection in environments regardless of network topology. Topologies included –
- Flat L2 network segments
- L2 and L3 networks with centralized virtual or physical routers, representative of typical data center rack implementations built on hybrid physical and network virtualization platform / distributed virtual switch (dVS)
- Networks with connection to other physical servers
- Overlay-based networks using the Distributed Firewalls (DFW) and Distributed Logical Routers (DLR)
- Physical VLAN and overlay-based networks using service insertion technologies running on dedicated VMs (in our case, Palo Alto Networks NextGen FW with Panorama)
Coalfire’s examination and testing of VMware NSX technology utilized simulated exploits that depict likely malware and Continue reading
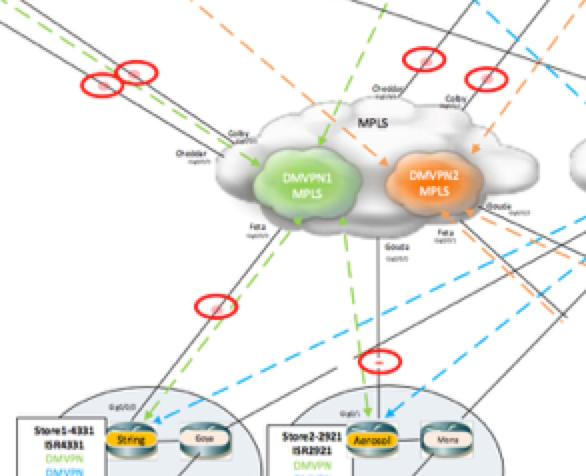
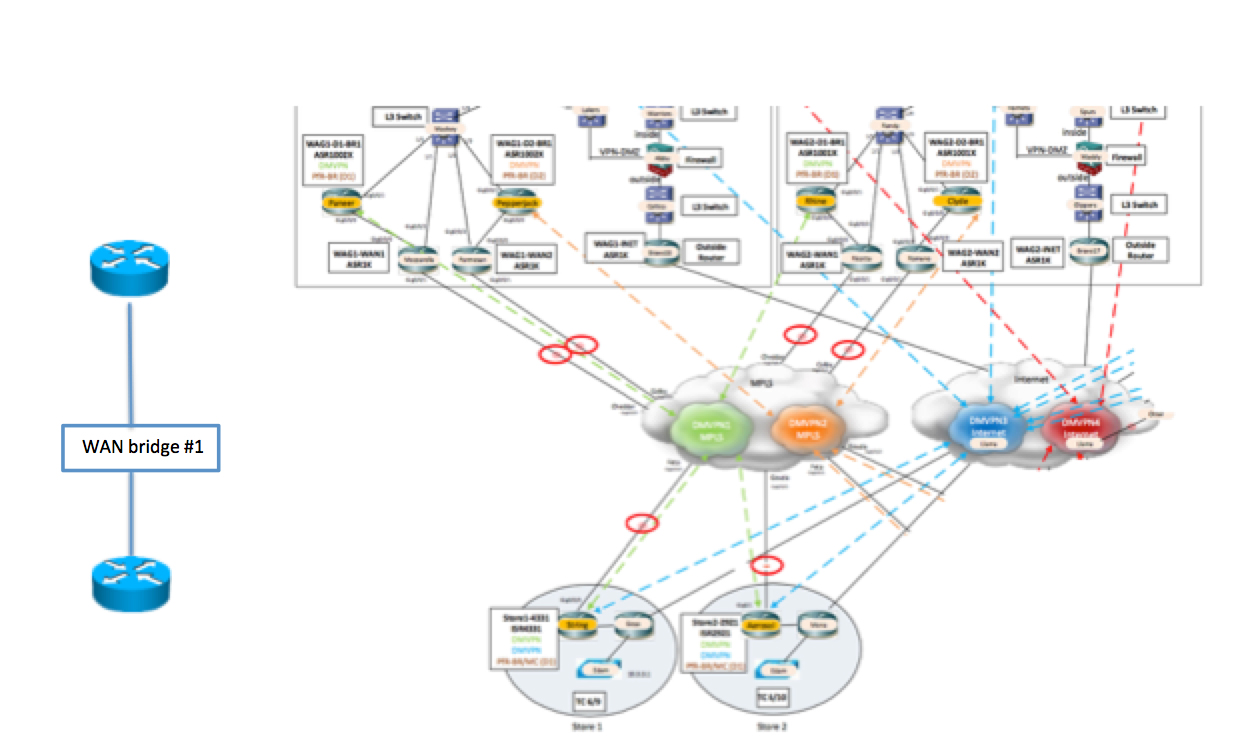
WAN Impairment/WAN Emulator with WAN Bridge
Playing in the lab and want to impair a link with delay or loss?  I use WAN Bridge – its simple and free.
I use WAN Bridge – its simple and free.
So say I’m testing an SD-WAN brownout/impairment avoidance solution in my lab. For example, Cisco’s IWAN. I’m going to need something to impair links with delay or loss. I like WAN Bridge. Why? Because its simple, easy, and free.
There has been one thing I’ve struggled with in the past year about. Every time I needed an impairment point this burned up 2 NICs on my UCS equipment. Why? Cause I couldn’t seem to figure out how to load one NIC on a UCS as a trunk port with multiple VLANs on it and have multiple WAN bridges with just 1 trunk on a switch.
So that meant, for a recent CPOC that I was doing, if I really wanted 6 impairment points (red circles in diagram below) I was going to need to eat up 12 NICs on my UCS.
There had to be a better way…..
My friend, David Prall, was convinced it “should” work. I was equally convinced that I had tried it before and Continue reading
Worth Reading: laptop killing USB stick
The post Worth Reading: laptop killing USB stick appeared first on 'net work.