Ultra Etherent: Discovery
Creating the fi_info Structure
Before the application can discover what communication services are available, it first needs a way to describe what it is looking for. This description is built using a structure called fi_info. The fi_info structure acts like a container that holds the application’s initial requirements, such as desired endpoint type or capabilities.
The first step is to reserve memory for this structure in the system’s main memory. The fi_allocinfo() helper function does this for the application. When called, fi_allocinfo() allocates space for a new fi_info structure, which this book refers to as the pre-fi_info, that will later be passed to the libfabric core for matching against available providers.
At this stage, most of the fields inside the pre-fi_info structure are left at their default values. The application typically sets only the most relevant parameters that express what it needs, such as the desired endpoint type or provider name, and leaves the rest for the provider to fill in later.
In addition to the main fi_info structure, the helper function also allocates memory for a set of sub-structures. These describe different parts of the communication stack, including the fabric, domain, and endpoints. The fixed sub-structures Continue reading
Working for a Vendor with David Gee
When I first met David Gee, he worked for a large system integrator. A few years later, he moved to a networking vendor, worked for a few of them, then for a software vendor, and finally decided to start his own system integration business.
Obviously, I wanted to know what drove him to make those changes, what lessons he learned working in various parts of the networking industry, and what (looking back with perfect hindsight) he would have changed.
NB546: Meta Mulls GPU Startup Purchase; Indirect Prompt Injection Exacerbates AI Risks
Take a Network Break! We start with a two-part listener follow-up and sound alarms about a serious flaw in Termix and tens of thousands of still-vulnerable Cisco security devices. Alkira debuts an MCP server and AI copilot for its multi-cloud networking platform; Cato Networks releases a Chrome-based browser extension to help secure contractor and personal... Read more »Tech Bytes: Building a UEC-Supported AI Data Center Fabric With Nokia (Sponsored)
The network plays a key role in AI model and inference training. On today’s Tech Bytes podcast, sponsored by Nokia, we talk about why you need a high-performance network for AI training workloads, essential technologies such as RoCE v2 and others that make Ethernet suitable for scale-out networking, the role of the Ultra Ethernet Consortium... Read more »Spaghetti Pasta Networking
Here’s an interesting data point in case you ever wondered why things are getting slower, even though the CPU performance is supposedly increasing. Albert Siersema sent me a link to a confusing implementation of spaghetti networking.
It looks like they’re trying to solve the how do I connect two containers (network namespaces) without having the privilege to create a vEth pair challenge with plenty of chewing gum and duct tape tap interfaces 🤦♂️
How to Take Packet Captures in ContainerLab/Netlab?

If you follow my blog, you probably know that I’m a big advocate for using Containerlab and Netlab to spin up network labs. I’ve already covered both tools in detail, so I won’t go over the basics again here. You can check the links below if you’re new to them or want a quick refresher. In this post, we’ll look at how to take packet captures in Containerlab labs. So, let’s get started.
How do I run Containerlab?
I know everyone has their own way of running Containerlab, so I thought I’d share how I set up and run my labs. My daily driver is a MacBook, but I run Containerlab on a server that’s set up as Continue reading
SUSE and Tigera: Empowering Secure, Scalable Kubernetes with Calico Enterprise
Modern Workloads Demand Modern Kubernetes Infrastructure
As organizations expand Kubernetes adoption—modernizing legacy applications on VMs and bare metal, running next-generation AI workloads, and deploying intelligence at the edge—the demand for infrastructure that is scalable, flexible, resilient, secure, and performant has never been greater. At the same time, compliance, consistent visibility, and efficient management without overburdening teams remain critical.
The combination of Calico Enterprise from Tigera and SUSE Rancher Prime delivers a resilient and scalable platform that combines high-performance networking, robust network security, and operational simplicity in one stack.
Comprehensive Security Without Compromise
Calico Enterprise provides a unified platform for Kubernetes networking, security, and observability:
- eBPF-powered networking for high performance without sidecar overhead
- One platform for all Kubernetes traffic: ingress, egress, in-cluster, and multi-cluster
- Security for every workload type: containers, VMs, and bare metal
- Seamless scaling with built-in multi-cluster networking and security
- Zero-trust security with identity-aware policies and workload-based microsegmentation
- Integrated observability for policy enforcement and troubleshooting
- Compliance features that simplify audits (PCI-DSS, HIPAA, SOC 2, FedRAMP)
Deployed with Rancher Prime, these capabilities extend directly into every cluster, enabling security-conscious industries such as finance, healthcare, and government to confidently run Kubernetes for any use case—from application modernization to AI and edge Continue reading
TNO044: Inside a Global Enterprise Data Center Network Migration (Sponsored)
Today we get an inside look at a major data center migration that Nokia is undertaking. Nokia is our sponsor for today’s episode. The company is moving legacy sets of data center networking equipment to its own Event Driven Automation (EDA) solution. We go behind the scenes of Nokia’s own IT department, which is supporting... Read more »How to Connect Nested KubeVirt Clusters with Calico and BGP Peering
Running Kubernetes inside Kubernetes isn’t just a fun experiment anymore – it’s becoming a key pattern for delivering multi-environment platforms at scale. With KubeVirt, a virtualization add-on for Kubernetes that uses QEMU (an open-source machine emulator and virtualizer), you can run full-featured Kubernetes clusters as virtual machines (VMs) inside a parent Kubernetes cluster. This nested architecture makes it possible to unify containerized and virtualized workloads, and opens the door to new platform engineering use cases.
But here’s the challenge: how can you ensure that these nested clusters, and the workloads within, can reach, and be reached by, your physical network and are treated the same way as any other cluster?
That’s where Calico’s Advanced BGP (Border Gateway Protocol) peering with workloads comes into play. By enabling BGP route exchange between the parent cluster and nested KubeVirt VMs, Calico extends dynamic routing directly to virtualized workloads. This allows nested clusters to participate in the broader network topology and advertise their pod and service IPs just like any other node. Thus eliminating the need for tunnels or overlays to achieve true layer 3 connectivity.
In this blog, we’ll walk through the big picture, prerequisites, and step-by-step configuration for setting up BGP Continue reading
HN799: Multi-Homing IPv6 to Your Home Lab
If you’ve got an Autonomous System Number (ASN) and an IPv6 block, you too can multi-home IPv6 to your home lab! Sounds easy, right? Well, maybe…but today we’re going to discuss why you’d want to and how you can do that with guest Anton Lönnerbro. Anton is a solutions architect at a managed service provider... Read more »Hedge 282: Future of Operations
On this episode of the Hedge, Anil Varanasi joins Russ to talk about the complexities of network operations and what Meter is doing in this space.
note: even though this is a more product-heavy episode of the Hedge than usual, it is not sponsored
download
Using BIRD BGP Daemon as a BGP Route Reflector
In this challenge lab, you’ll configure a BIRD daemon running in a container as a BGP route reflector in a transit autonomous system. You should be familiar with the configuration concepts if you completed the IBGP lab exercises, but will probably struggle with BIRD configuration if you’re not familiar with it.
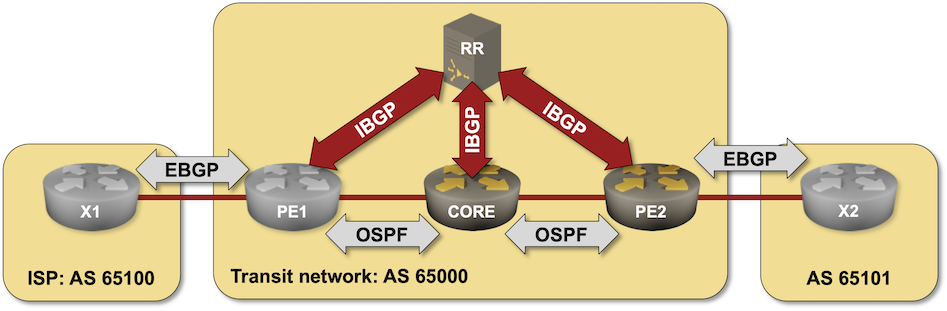
Click here to start the lab in your browser using GitHub Codespaces (or set up your own lab infrastructure). After starting the lab environment, change the directory to challenge/01-bird-rr, build the BIRD container with netlab clab build bird if needed, and execute netlab up.
Containerlab – The Anti-Pattern
An intellectual is a man who says a simple thing in a difficult way; an artist is a man who says a difficult thing in a simple way. Charles Bukowski - Notes of a Dirty Old Man, 1969 In a world where technology seems to be working against us and seemingly simple things require far READ MORE
The post Containerlab – The Anti-Pattern appeared first on The Gratuitous Arp.
LIU001: Growing Pains
Starting any new endeavor is hard. That’s particularly true for a career in tech. And that’s the reason Alexis Bertholf and Kevin Nanns are launching the Life In Uptime podcast. In each episode they’ll sit down with engineers, leaders, and builders in tech to uncover the stories behind their careers to help you see how... Read more »netlab: Applying Simple Configuration Changes
For years, netlab has had custom configuration templates that can be used to deploy custom configurations onto lab devices. The custom configuration templates can be Jinja2 templates, and you can create different templates (for the same functionality) for different platforms. However, using that functionality if you need an extra command or two makes approximately as much sense as using a Kubernetes cluster to deploy a BusyBox container.
netlab release 25.09 solves that problem with the files plugin and the inline config functionality.
Ultra Ethernet: Address Vector (AV)
Address Vector (AV)
The Address Vector (AV) is a provider-managed mapping that connects remote fabric addresses to compact integer handles (fi_addr_t) used in communication operations. Unlike a routing table, the AV does not store IP (device mappings). Instead, it converts an opaque Fabric Address (FA)—which may contain IP, port, and transport-specific identifiers—into a simple handle that endpoints can use for sending and receiving messages. The application never needs to reference the raw IP addresses directly.
Phase 1: Application – Request & Definition
The application begins by requesting an Address Vector (AV) through the fi_av_open() call. To do this, it first defines the desired AV properties in a fi_av_attr structure:
int fi_av_open(struct fid_domain *domain, struct fi_av_attr *attr, struct fid_av **av, void *context);
struct fi_av_attr av_attr = {
.type = FI_AV_TABLE,
.count = 16,
.rx_ctx_bits = 0,
.ep_per_node = 1,
.name = "my_av",
.map_addr = NULL,
.flags = 0
};
Example 4-1: structure Continue reading
From Classroom to Community 2 – ROT13 and Math Quizzer
I am so happy the first post about sharing my Python scripts got such a […]
The post From Classroom to Community 2 - ROT13 and Math Quizzer first appeared on Brezular's Blog.

