Evolved Packet Core – Welcome to Long Term Evolution!
As an end user, I am always welcoming the “4G” Signal indicator on my mobile because basically for me this maps to a better Download Speed, good quality VoIP calls (skype, Hangout, Whatsapp, etc) , better Streaming, and HD Videos. This article is all about the “4G” indicator. I am discussing the Evolved Packet Core together with […]
The post Evolved Packet Core – Welcome to Long Term Evolution! appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
IS-IS level 1, IS-IS Routing Protocol Levels
What is IS-IS Level 1 ? Why IS-IS level 1 is used ? What are the IS-IS levels ? What is the corresponding Area type in OSPF ? IS-IS Level 1 is also called as IS-IS Level 1 sub domain. IS-IS is a link state routing protocol, similar to OSPF. You can read detail comparison […]
The post IS-IS level 1, IS-IS Routing Protocol Levels appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Jinja2 and… Powershell? Automation(ish) Microsoft DHCP
Most of us have home labs, right?
I’m in the middle of doing some zero touch provisioning testing, and I had the need to create a bunch of DHCP scopes and reservations, some with scope specific options, and some with client specific options. As often as I’ve had to create a Microsoft DHCP server in the lab and set up some custom scopes, I decided I was going to figure out how to automate this as much as I could with a little effort as possible.
After taking a quick look around for a python library to help me out, python being my weapon of choice, I realized that I was going to have to get into some Powershell scripting. I’ve dabbled before, but I’ve never really take the time to learn much about Powershell control structures ( loops, conditionals, pipes, etc…). I really didn’t want to spend the time getting up to speed on a new language, so I instead decided I was going to use the python skills I had to auto generate the scripts using a little jinja2 and some google-technician skills.
Figuring out the Powershell Syntax
This was the easy part actually, Microsoft has some pretty Continue reading
Forensics Challenge for CSIRT Team – Part 1 Assignment
I have created a virtual machine that you can use to test your forensics analysis skills. Please, download the VM, solve an assignment below and share solutions with us.
1. Assignment
Your are a member of elite CSIRT team which is responsible for dealing with computer security incidents in your jurisdiction. You are asked to investigate a server that was previously administered by disgruntled administrator Mr. Abdullah Khan who was fired up. Although login credentials for server were changed after Khan's sacking from the company, it is believed he might insert malicious software into server before change of credentials. Your task is to ensure that a sever does not contain any malicious software and user data stored on the server are not compromised. You also need to prove your professional forensic skills and analyze a suspicious file in case you find it on the server. Based on your investigation you should find out how malware work and create detailed report for your boss.
The server is running Ubuntu 16.04.1 and it is primary used as a file server with configured SSH access. Unfortunately the backup of user files is damaged and cannot be used in case of data are lost during your investigation. The login/password is Continue reading
On the ‘Net: Big thinkers leave Cisco
The post On the ‘Net: Big thinkers leave Cisco appeared first on 'net work.
On the ‘Net: You keep using that SDN word…
The post On the ‘Net: You keep using that SDN word… appeared first on 'net work.
What is MPLS tunnel label and why it is used ?
In networking we use many times different terms to define the same thing. MPLS tunnel label or transport label are just two of those. Not only transport and tunnel labels but also other terms are used to define the same thing which these labels provide. Let me explain first why and where MPLS tunnel label is […]
The post What is MPLS tunnel label and why it is used ? appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
SDxCentral Weekly News Roundup — July 22, 2016
 FatPipe Networks and Avaya combined data center SDN and SD-WAN into a single system.
FatPipe Networks and Avaya combined data center SDN and SD-WAN into a single system.
NSX-V: Multi-site Options and Cross-VC NSX Design Guide
Check-out the new NSX-V Multi-site Options and Cross-VC NSX Design Guide
The goal of this design guide is to outline several NSX solutions available for multi-site data center connectivity before digging deeper into the details of the Cross-VC NSX multi-site solution. Learn how Cross-VC NSX enables logical networking and security across multiple vCenter domains/sites and how it provides enhanced solutions for specific use cases. No longer is logical networking and security constrained to a single vCenter domain. Cross-VC NSX use cases, architecture, functionality, design, and failure/recovery scenarios are discussed in detail.
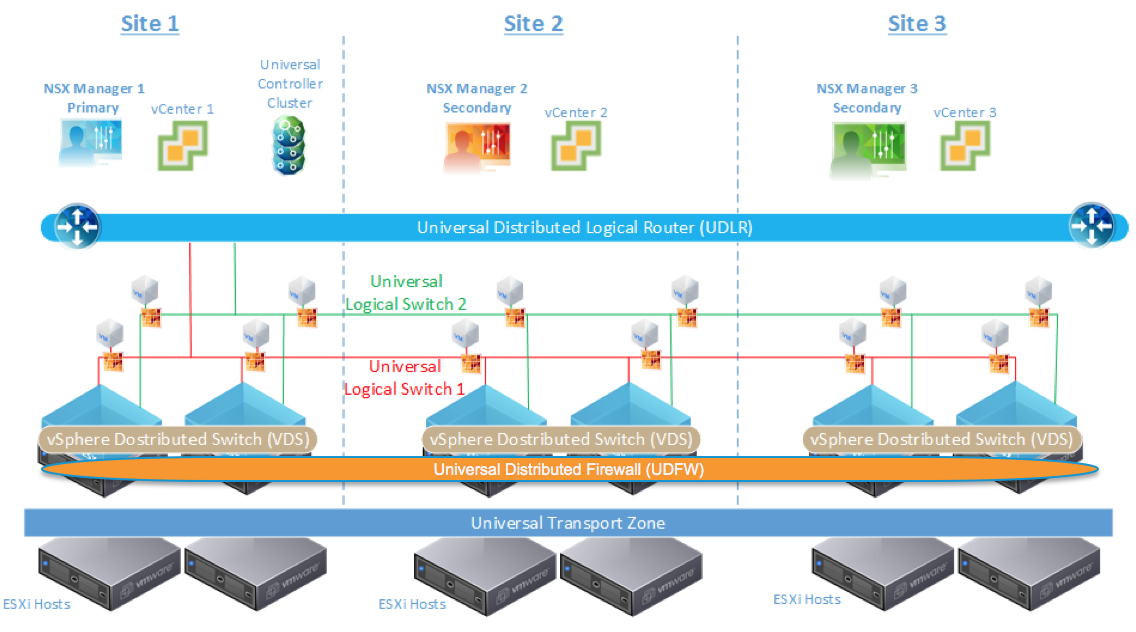
Cross-VC NSX: Logical Networking and Security Across vCenter Domains and Sites
Outlined briefly below are several important use cases that Cross-VC NSX enables in regards to Application Continuity. For additional details on Cross-VC NSX and multi-site data center solutions see the NSX-V Multi-site Options and Cross-VC NSX Design Guide.
Use Case 1: Workload Mobility
Since logical networking and security can span multiple vCenter domains and multiple sites, Cross-VC NSX allows for enhanced workload mobility which can not only span multiple sites but also multiple vCenter domains across Active-Active data centers. Workloads can now move between vCenter domains/sites on demand for tasks such as data center migration, data center Continue reading
Worth Reading: Protecting your assets
The post Worth Reading: Protecting your assets appeared first on 'net work.