Automation Leveraging NSX REST API Guide
Check-out the new Automation Leveraging NSX REST API Guide.
Authors: VMware NSX Technical Product Management Team
Thanks to all the contributors and reviewers of this document. A brief overview of the guide is provided below. Continue reading
Simplify Simplify Simplify In Sales
It’s super important to understand and know your audience. Even when you think you’re not being technical, there are levels of un-technical you can drop to that make you cringe, but if your audience needs it, then it’s a great skill to learn.
As the network and software world hurtles along at super ridiculous speed (that’s the perception at least), it’s important to acknowledge that a lot of the enterprises and organisations out there are dealing with much the sameness of the last decade or so. Not everyone is riding the hype of Cloud, SDN or DevOps (shock horror?), so when your area of speciality in their world is the disruptive technology, be sure to have a card in your back pocket that helps you step it down a level. Many preconceived ideas exist in every world so do not be afraid to help them understand. You will get met with resistance but remember, you are threatening the way they do things today, therefore show them and help them see the value. It’s always critical to remember, someone else has been in at some point and convinced them to do what they’re doing today. Fair fight? Never is.
Ultimately Continue reading
10 Ways To Get The Most Out Of Ethernet
Find out how to squeeze more performance out of your Ethernet LAN.
Networking Education: Leave Your Comfort Zone
Breadth makes more sense than depth in today's IT environment.
On the Lossiness of TCP
When someone tells you that “TCP is a lossy protocol” during a job interview, don’t throw him out immediately – he was just trusting the Internet a bit too much (click to enlarge).
Everyone has a bad hair day, and it really doesn’t matter who published that text… but if you’re publishing technical information, at least try to do no harm.
Read more ...A post-mortem on this morning’s incident
We would like to share more details with our customers and readers on the internet outages that occurred this morning and earlier in the week, and what we are doing to prevent these from happening again.
June 17 incident
On June 17, at 08:32 UTC, our systems detected a significant packet loss between multiple destinations on one of our major transit provider backbone networks, Telia Carrier.
In the timeframe where the incident was being analysed by our engineers, the loss became intermittent and finally disappeared.
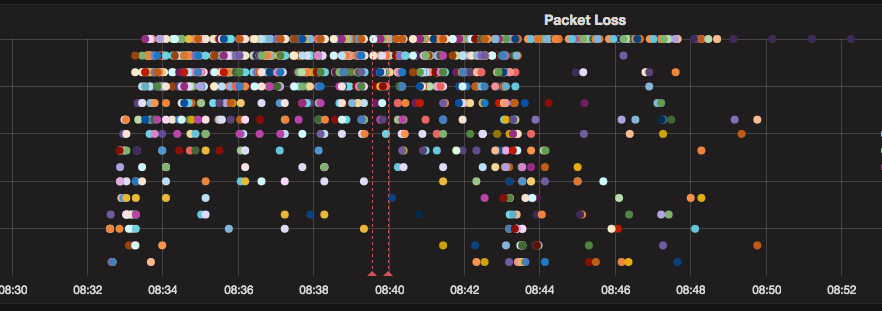
Today’s incident
Today, Jun 20, at 12:10 UTC, our systems again detected massive packet loss on one of our major transit provider backbone networks: Telia Carrier.
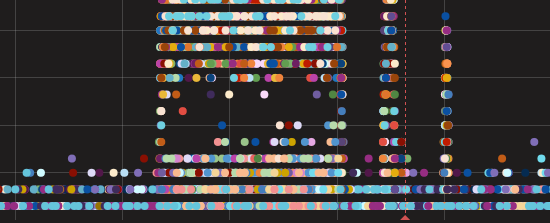
Typically, transit providers are very reliable and transport all of our packets from one point of the globe to the other without loss - that’s what we pay them for. In this case, our packets (and that of other Telia customers), were being dropped.
While Internet users usually take it for granted that they can reach any destination in the world from their homes and businesses, the reality is harsher than that. Our planet is big, and Continue reading
