Tools: Conn-check
conn-check – A deployment utility to check connectivity between services conn-check is a small utility, written in Python using the Twisted network library, that verifies outgoing connections from your application servers to services it depends on, e.g. databases, caches, web service APIs, etc.conn-check is used not only to verify network dependency changes at deploy time, […]
The post Tools: Conn-check appeared first on EtherealMind.
Optimizing TLS over TCP to reduce latency
The layered nature of the Internet (HTTP on top of some reliable transport (e.g. TCP), TCP on top of some datagram layer (e.g. IP), IP on top of some link (e.g. Ethernet)) has been very important in its development. Different link layers have come and gone over time (any readers still using 802.5?) and this flexibility also means that a connection from your web browser might traverse your home network over WiFi, then down a DSL line, across fiber and finally be delivered over Ethernet to the web server. Each layer is blissfully unaware of the implementation of the layer below it.

But there are some disadvantages to this model. In the case of TLS (the most common standard used for sending encrypted data across in the Internet and the protocol your browser uses with visiting an https:// web site) the layering of TLS on top of TCP can cause delays to the delivery of a web page.
That’s because TLS divides the data being transmitted into records of a fixed (maximum) size and then hands those records to TCP for transmission. TCP promptly divides those records up into segments which are then transmitted. Ultimately, Continue reading
Establishing a confidential Service Boundary with Avaya’s SDN Fx

Security is a global requirement. It is also global in the fashion in which it needs to be addressed. But the truth is, regardless of the vertical, the basic components of a security infrastructure do not change. There are firewalls, intrusion detection systems, encryption, networking policies and session border controllers for real time communications. These components also plug together in rather standard fashions or service chains that look largely the same regardless of the vertical or vendor in question. Yes, there are some differences but by and large these modifications are minor.
So the questions begs, why is security so difficult? As it turns out, it is not really the complexities of the technology components themselves, although they certainly have that. It turns out that the real challenge is deciding exactly what to protect and here each vertical will be drastically different. Fortunately, the methods for identifying confidential data or critical control systems are also rather consistent even though the data and applications being protected may vary greatly.
In order for micro-segmentation as a security strategy to succeed, you have to know where the data you need to protect resides. You also need to know how it flows through Continue reading
Gain Deep Insight Into Your NSX Network While Simplifying Management and Operations
We’re excited to announce that VMware NSX, version 6.2.3, is now available for all customers with active support. As we evolve the NSX platform, we continue to place a high degree of emphasis on helping customers operationalize NSX, speed-up deployment, and integrate with more systems from our NSX ecosystem partners. This latest release introduces enhanced network monitoring and troubleshooting tools with expanded hardware partner integration.
Some of the top highlights include:
Native Visibility and Reporting
Resolve problems faster, visualize event trends, trigger alerts, and more, all in real-time with VMware vRealize Log Insight for NSX, now included with NSX Standard, Advanced and Enterprise licenses. This new capability introduces:
- Centralized big data log management built for NSX
- Monitoring and dashboards for network virtualization and security
To learn more about vRealize Log Insight for NSX refer to the FAQ or visit the Log Insight product page here.
Improvements to NSX Management and Operations
Reduce Mean Time to Recovery with improved troubleshooting and operational capabilities. Key enhancements include:
- Dashboards for health status of components and built-in monitoring of all critical systems communication channels
- Simplified filtering of firewall rules
- Enhancements to central CLI
- New partner services to enable packet capture and Continue reading
DevOps: The Real Impact On IT Pros
In this episode of Network Matters with Ethan Banks, learn why the topic of DevOps has become so pervasive in IT media. Ethan explains what DevOps really means for most IT organizations, and how Infrastructure professionals can use concepts from DevOps to improve their own efficiency.
Your Internet Really Is Down
While internet connectivity as a whole is resilient, the fabric that our users and applications traverse is susceptible to outages.
SDN as an Abstraction Layer
During the Introduction to SDN webinar I covered numerous potential definitions:
- It’s the separation of control and data plane;
- It’s software-based packet forwarding;
- It’s open networking and whitebox switching;
- It’s network programmability and device APIs.
I find all of these definitions too narrow or even misleading. However, the “SDN is a layer of abstraction” one is not too bad (see also RFC 1925 section 2.6a).
Perth, Australia: 80th Data Center
 CloudFlare is excited to announce the launch of our newest data center in Perth, Australia. This expands the breadth of our global network to span 80 unique cities across 41 countries, and is our fourth data center in the Oceania region, joining existing data centers in Sydney, Melbourne and Auckland.
CloudFlare is excited to announce the launch of our newest data center in Perth, Australia. This expands the breadth of our global network to span 80 unique cities across 41 countries, and is our fourth data center in the Oceania region, joining existing data centers in Sydney, Melbourne and Auckland.
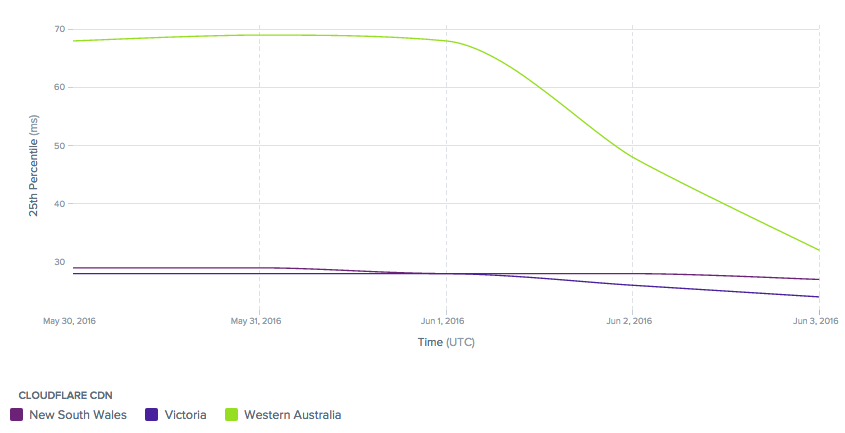
Western Australia
Perth is in a fascinating location. Home to sunny beaches and the highest number of self-made millionaires in the world, it is actually geographically closer to Singapore than to Sydney (though closer to Sydney in a “networking” sense, as determined by BGP routing).
Visitors to millions of websites across Western Australia served locally can now experience a faster and safer Internet - and ISPs can reach us at the Western Australia Internet Exchange (WA-IX), one of 119 internet exchanges that we openly peer at.
Missing letters?
Helping build CloudFlare’s network provides our team members with the opportunity to not just speed up the Internet, but also improve our sense of geography. Visitors to our offices in San Francisco, London and Singapore can get a sneak peek at our fast-changing map (with live and upcoming dots). Perth Continue reading
Security Startup Infocyte Widens Its Threat Hunting Scope
 Former Air Force officers now hunt for malware.
Former Air Force officers now hunt for malware.
CoreOS Attacks the Problem of Container Storage
 Torus almost rhymes with CoreOS...
Torus almost rhymes with CoreOS...