HPE & GE Form an IoT Partnership
 IoT partnerships between hardware and software companies are growing.
IoT partnerships between hardware and software companies are growing.
Worth Reading: The age of the GPU
The post Worth Reading: The age of the GPU appeared first on 'net work.
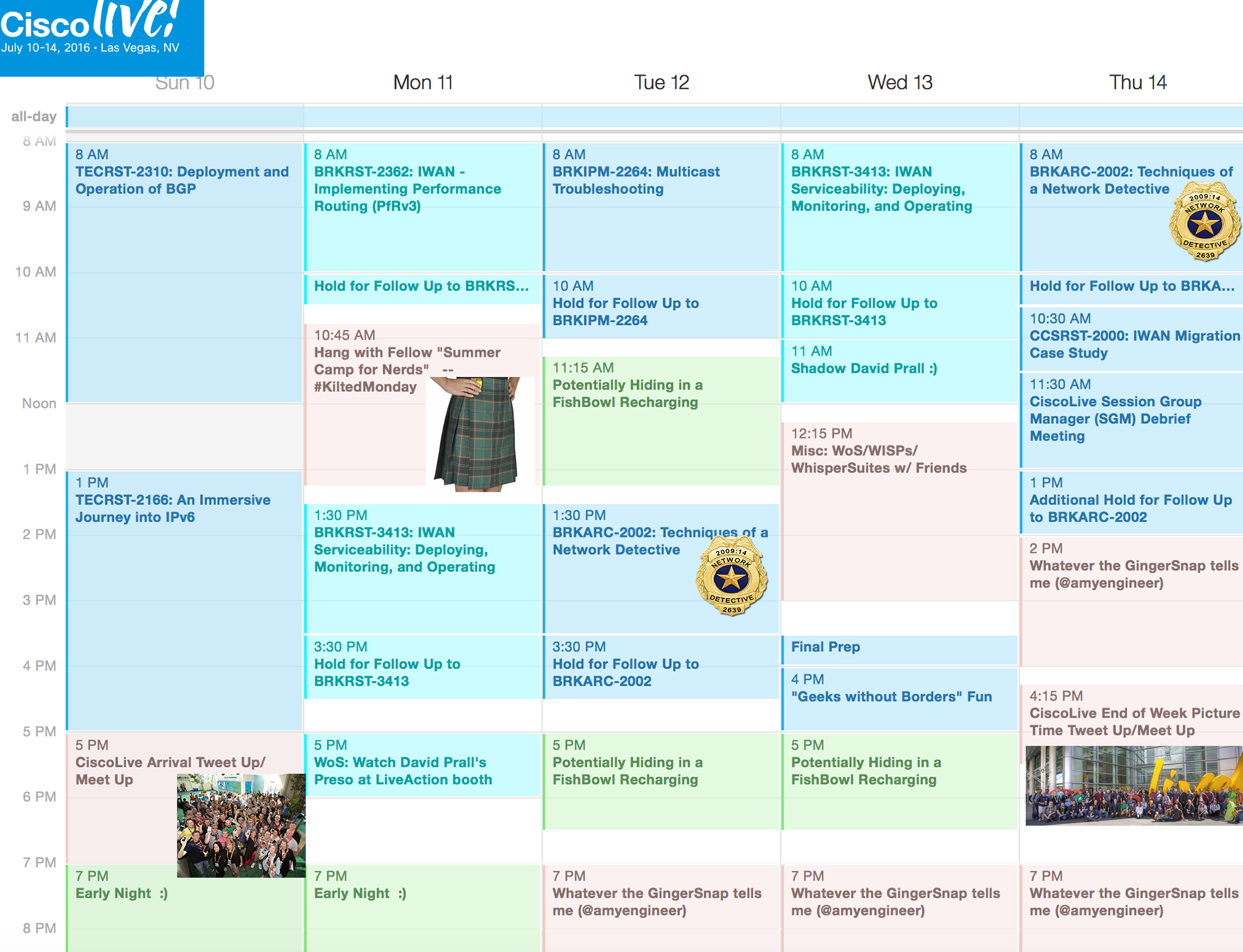
My Cisco Live 2016 Schedule
Ever since my blog, CiscoLive 2016: ‘Summer Camp for Geeks’, I’ve been getting questions about what my personal CLUS schedule typically looks like for the week. CiscoLive 2016 will be my 11th CiscoLive US (“#CLUS”) and my 13th CiscoLive in general.
It is my favorite work week of the ENTIRE year. And I look forward to it a great deal. At the same time…. it is not even one full week and one can miss so much they wished they hadn’t missed because the time flies by so quickly. And yes… I have learned this the hard way.
So… first things first – I came up with the list of things that are prioritizes to me for the week.
All that said…… Here ya go. My CiscoLive (CLUS) schedule for the week.
- Teach
- Recharge
- Learn
- Play and Have Fun
Reading List: 060916
A few of the papers, RFCs, and drafts I’m reading this week, along with a short description of each.
A Survey of Worldwide Censorship Techniques
draft-hall-censorship-tech-03
Censorship is a large problem on the Internet—but it’s often difficult to find any good description of the various ways censors can both find and block “offending” content. This draft is a short, readable overview of the various techniques actually seen in the wild, along with pointers to research about the techniques themselves, and instances where they’ve been used in the real world.
IPv6 Extension Headers and Packet Drops
draft-gont-v6ops-ipv6-ehs-in-real-world
One of the interesting features of IPv6 is its support for extension headers, which are variable length bits of information—metadata about the packet, for instance—that can be attached to a packet and processed by either the receiving host or forwarding devices along the way. Extension headers are useful, in that they allow IPv6 to be easily extended on the fly, rather than forcing the protocol designer to create a set of metadata “in stone.” Extension headers, however, are also controversial; how should an ASIC designer decide which ones to support in hardware, and how should extension headers that cannot be handled in hardware Continue reading
Communications of the Bolek Trojan
A few weeks ago CERT Polska released a short blog post introducing a new malware family now known as Bolek. PhishMe and Dr.Web have since added some additional insight into the family. Browsing through a memory dump of the malware, a Webinjects section sticks out. Webinjects usually imply banking malware, so it seems Bolek picks […]ECI Offers Optical Bandwidth on Demand
 It's part of ECI’s SDN applications.
It's part of ECI’s SDN applications.