Protect your domain with Zone Holds


Today, we are announcing Zone Holds, a new capability for enterprise customers that gives them control of if and when someone else can add the same zone to another Cloudflare account. When multiple teams at a company want to use Cloudflare, one team might accidentally step on another’s toes and try to manage the same zone in two accounts. Zone Holds ensure that this cannot happen by enforcing that only one account can contain a given domain, optionally inclusive of subdomains or custom hostnames, unless explicit permission is granted by the account owner of the zone.
What can go wrong today
Cloudflare already requires zones to be authenticated via DNS before traffic is proxied through our global network. This ensures that only domain owners can authorize traffic to be sent through and controlled with Cloudflare. However, many of our customers are large organizations with many teams all trying to protect and accelerate their web properties. In these cases, one team may not realize that a given domain is already being protected with Cloudflare. If they activate a second instance of the same domain in Cloudflare, they end up replacing the original zone that another team was already managing with Cloudflare. Continue reading
IPv6 Buzz 123: Why You Need An IPv6 Security Plan
Today's IPv6 Buzz podcast explores why you need a plan for IPv6 security. Even if you haven't actively deployed IPv6, you've got v6-enabled hosts on your LAN and remote workers connecting to you over v6 networks. We discuss key elements to consider in your plan, evaluating IPv6 support in security products and services, and more.
The post IPv6 Buzz 123: Why You Need An IPv6 Security Plan appeared first on Packet Pushers.
IPv6 Buzz 123: Why You Need An IPv6 Security Plan
Today's IPv6 Buzz podcast explores why you need a plan for IPv6 security. Even if you haven't actively deployed IPv6, you've got v6-enabled hosts on your LAN and remote workers connecting to you over v6 networks. We discuss key elements to consider in your plan, evaluating IPv6 support in security products and services, and more.Kicking the Tires of GitHub Copilot
A friend sent me a video demo of his AI-driven network device configuration proof-of-concept. Before commenting on that idea, I wanted to see how well AI works as an assistant. Once Kristian Larsson mentioned he was using GitHub Copilot, it was obvious what to do next: try it out while working on the next netlab release.
TL&DR:
- It works.
- Some Copilot suggestions are uncannily accurate; others are fishing expeditions.
- It’s bland.
Kicking the Tires of GitHub Copilot
A friend sent me a video demo of his AI-driven network device configuration proof-of-concept. Before commenting on that idea, I wanted to see how well AI works as an assistant. Once Kristian Larsson mentioned he was using GitHub Copilot, it was obvious what to do next: try it out while working on the next netlab release.
TL&DR:
- It works.
- Some Copilot suggestions are uncannily accurate; others are fishing expeditions.
- It’s bland.
Juniper Version Selection
Picking the right Junos version is important. If you’re not familiar with Juniper, finding and downloading the right software package is confusing. Here’s some guidance on picking the right version.
It’s useful to understand Junos version numbering, and the upgrade policy. Then check the Suggested Releases page to see what they recommend, check if that makes sense, and figure out how to get from here to there.
Understanding Version Numbering
These days Juniper publishes a new release train every quarter. Versioning is simple “<year>.<quarter>.R<release number>”. So 21.4R1 is released in the 4th quarter of 2021. New releases add new features and support new hardware. Configs may break
They then publish “service releases” on top of that, for example 21.4R1-S1 and 21.4R1-S2. These are supposed to only be bugfixes, but complacency breeds contempt. So sometimes they throw in throw in breaking changes that may render your existing config non-bootable, because why the hell not? Continue reading
Perfection Paralysis

This is a sort of companion piece to my post last week because I saw a very short post here about doing less. It really hit home with me because I’m just as bad as Shawn about wanting everything to be perfect when I write it or create it.
Maximizing Mistakes
One of the things that I’ve noticed in a lot of content that I’ve been consuming recently is the inclusion of mistakes. When you’re writing you have ample access to a backspace key so typos shouldn’t exist (and autocorrect can bugger off). But in video and audio content you can often make a mistake and not even realize it. Flubbing a word or needed to do a retake for something happens quite often, even if you never see or hear them.
What has me curious and a bit interested is that more of those quick errors are making it in. These are things that could easily be fixed in post production and yet they stay. It’s almost like the creators are admitting that mistakes happen and it’s hard to read scripts perfectly every time like some kind of robot. Honest mistakes over things like pronunciation or difficult word combinations Continue reading
Why AI Cybersecurity Is So Important for Network Teams
Network security teams must level up their observability, automation, and cybersecurity tools to be ready for AI-enabled cyber attacks.Day Two Cloud 189: The Cloud Network Engineer Career Path With Kam Agahian
Today on Day Two Cloud we explore what it takes to transition from traditional networking to a career as a cloud network engineer. Guest Kam Agahian shares insights from his own career journey about what's the same and what's different between on-prem and cloud networking, what skills might you want to pick up to make the transition, recommended certifications, and more.
The post Day Two Cloud 189: The Cloud Network Engineer Career Path With Kam Agahian appeared first on Packet Pushers.
Day Two Cloud 189: The Cloud Network Engineer Career Path With Kam Agahian
Today on Day Two Cloud we explore what it takes to transition from traditional networking to a career as a cloud network engineer. Guest Kam Agahian shares insights from his own career journey about what's the same and what's different between on-prem and cloud networking, what skills might you want to pick up to make the transition, recommended certifications, and more.Introducing Calico Runtime Threat Defense—The most extensive security coverage for containers and Kubernetes
Containerized applications are complex, which is why an effective container security strategy is difficult to design and execute. As digitalization continues to push applications and services to the cloud, bad actors’ attack techniques have also become more sophisticated, which further challenges container security solutions available on the market.
Despite the discussion around agent vs agentless in the cloud security landscape and which type of solution is better, the most valuable solution is one that provides a wide breadth of coverage. Calico is unique as it is already installed as part of the underlying platform and provides the dataplane for a Kubernetes cluster. When Calico Cloud or Calico Enterprise is deployed, security and observability capabilities can be enabled on top of these core components. We provide a simple plug-and-play active security solution that focuses on securing workloads and the Kubernetes platform with the least amount of complexity and configuration.
Runtime attack vectors
Cloud-native applications are susceptible to many attack vectors. We have broken them down to eight, as seen in the following illustration:
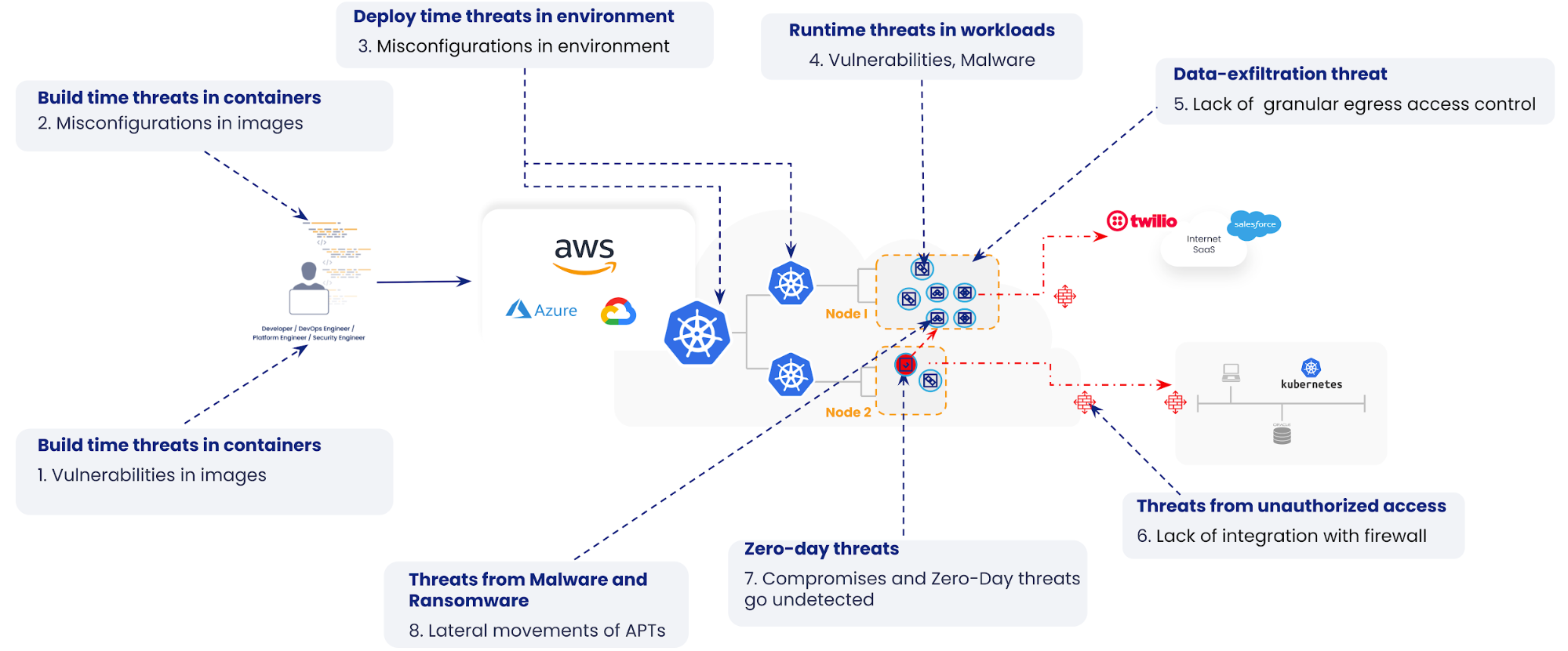
In previous blogs, we have explained how the use of vulnerability management, zero-trust workload security, and microsegmentation can help reduce the Continue reading