Day Two Cloud 189: The Cloud Network Engineer Career Path With Kam Agahian
Today on Day Two Cloud we explore what it takes to transition from traditional networking to a career as a cloud network engineer. Guest Kam Agahian shares insights from his own career journey about what's the same and what's different between on-prem and cloud networking, what skills might you want to pick up to make the transition, recommended certifications, and more.
The post Day Two Cloud 189: The Cloud Network Engineer Career Path With Kam Agahian appeared first on Packet Pushers.
Day Two Cloud 189: The Cloud Network Engineer Career Path With Kam Agahian
Today on Day Two Cloud we explore what it takes to transition from traditional networking to a career as a cloud network engineer. Guest Kam Agahian shares insights from his own career journey about what's the same and what's different between on-prem and cloud networking, what skills might you want to pick up to make the transition, recommended certifications, and more.Introducing Calico Runtime Threat Defense—The most extensive security coverage for containers and Kubernetes
Containerized applications are complex, which is why an effective container security strategy is difficult to design and execute. As digitalization continues to push applications and services to the cloud, bad actors’ attack techniques have also become more sophisticated, which further challenges container security solutions available on the market.
Despite the discussion around agent vs agentless in the cloud security landscape and which type of solution is better, the most valuable solution is one that provides a wide breadth of coverage. Calico is unique as it is already installed as part of the underlying platform and provides the dataplane for a Kubernetes cluster. When Calico Cloud or Calico Enterprise is deployed, security and observability capabilities can be enabled on top of these core components. We provide a simple plug-and-play active security solution that focuses on securing workloads and the Kubernetes platform with the least amount of complexity and configuration.
Runtime attack vectors
Cloud-native applications are susceptible to many attack vectors. We have broken them down to eight, as seen in the following illustration:
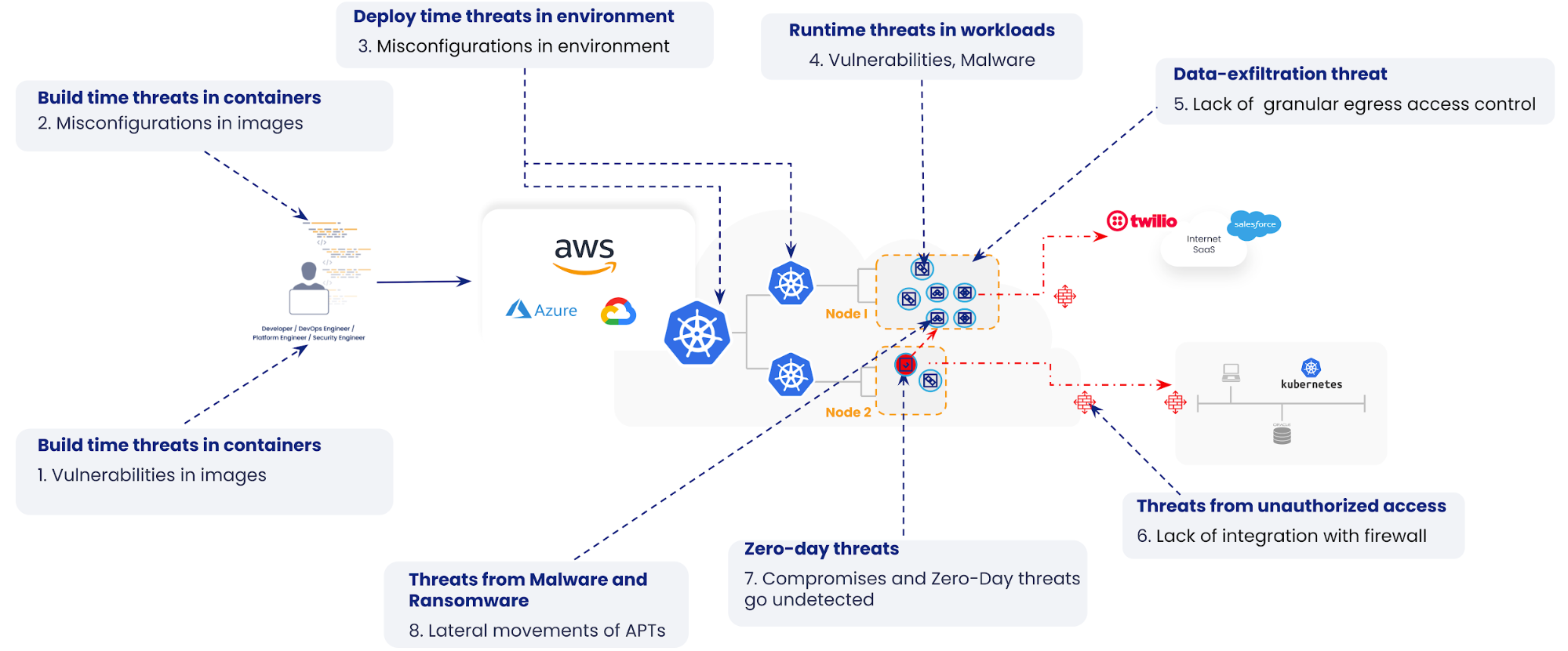
In previous blogs, we have explained how the use of vulnerability management, zero-trust workload security, and microsegmentation can help reduce the Continue reading
New: High Availability Clusters in Networking
Years ago I loved ranting about the stupidities of building stretched VLANs to run high-availability network services clusters with two nodes (be it firewalls, load balancers, or data center switches with centralized control plane) across multiple sites.
I collected pointers to those blog posts and other ipSpace.net HA cluster resources on the new High Availability Service Clusters page.
New: High Availability Clusters in Networking
Years ago I loved ranting about the stupidities of building stretched VLANs to run high-availability network services clusters with two nodes (be it firewalls, load balancers, or data center switches with centralized control plane) across multiple sites.
I collected pointers to those blog posts and other ipSpace.net HA cluster resources on the new High Availability Service Clusters page.
Avoiding the Risks of Unmanaged Networks
Enterprises can reduce their risks from unmanaged networks by gaining visibility to the complete network path that delivers their users' experiences.Cloudflare’s view of the Virgin Media outage in the UK
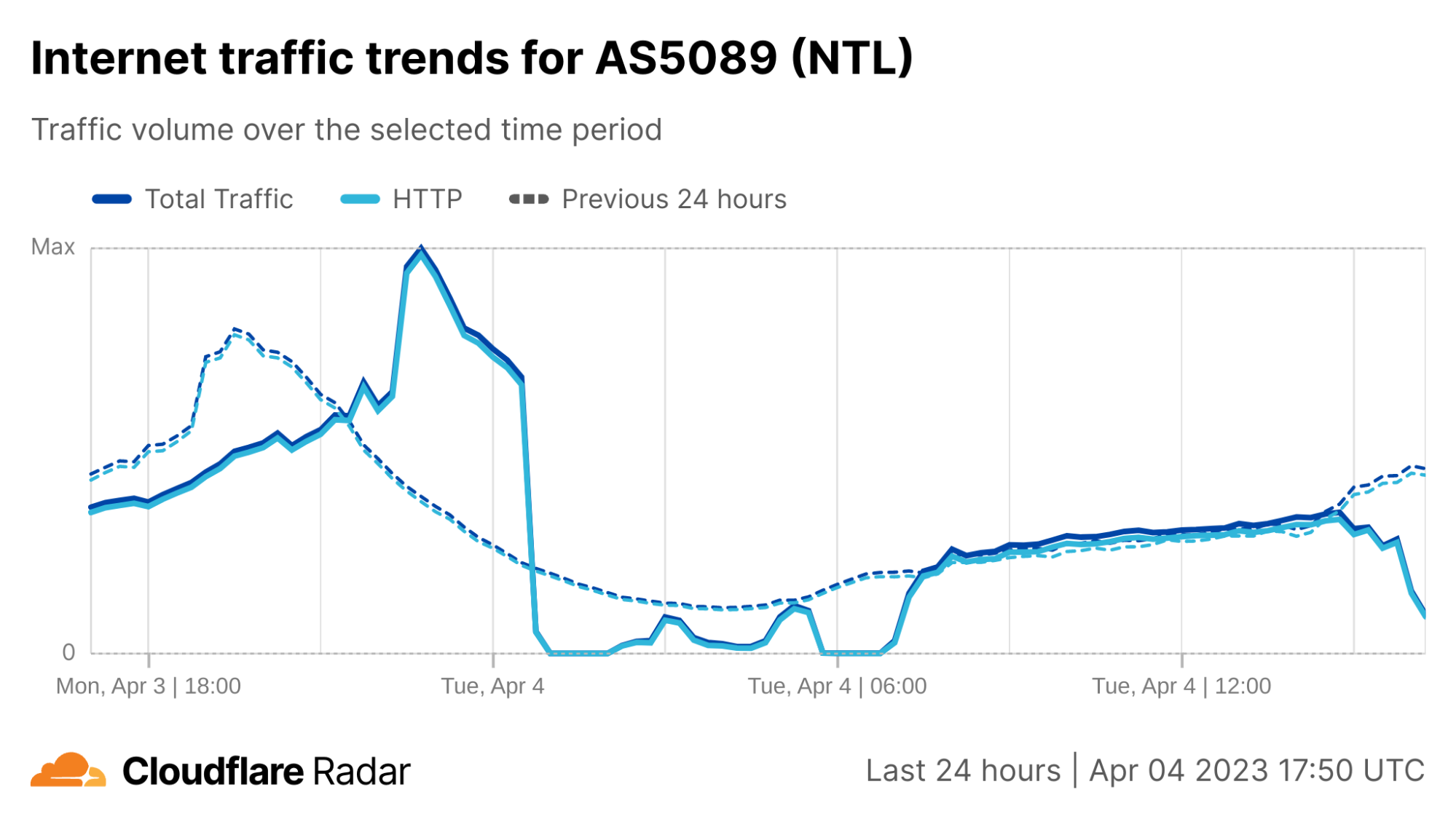
Just after midnight (UTC) on April 4, subscribers to UK ISP Virgin Media (AS5089) began experiencing an Internet outage, with subscriber complaints multiplying rapidly on platforms including Twitter and Reddit.
Cloudflare Radar data shows Virgin Media traffic dropping to near-zero around 00:30 UTC, as seen in the figure below. Connectivity showed some signs of recovery around 02:30 UTC, but fell again an hour later. Further nominal recovery was seen around 04:45 UTC, before again experiencing another complete outage between around 05:45-06:45 UTC, after which traffic began to recover, reaching expected levels around 07:30 UTC.
After the initial set of early-morning disruptions, Virgin Media experienced another round of issues in the afternoon. Cloudflare observed instability in traffic from Virgin Media’s network (called an autonomous system in Internet jargon) AS5089 starting around 15:00 UTC, with a significant drop just before 16:00 UTC. However in this case, it did not appear to be a complete outage, with traffic recovering approximately a half hour later.
Virgin Media’s Twitter account acknowledged the early morning disruption several hours after it began, posting responses stating “We’re aware of an issue that is affecting broadband services for Virgin Media customers as well as our contact centres. Our teams Continue reading
4 Ways to Prevent Data Loss In the Cloud
For businesses to maximize cloud’s potential and use it efficiently for data management, they will have to take data protection seriously.Real-time flow analytics on VyOS
VyOS with Host sFlow agent describes support for streaming sFlow telemetry added to the open source VyOS router operating system. This article describes how to install analytics software on a VyOS router by configuring a container.vyos@vyos:~$ add container image sflow/ddos-protectFirst, download the sflow/ddos-protect image.
vyos@vyos:~$ mkdir -m 777 /config/sflow-rtCreate a directory to store persistent container state.
set container name sflow-rt image sflow/ddos-protect set container name sflow-rt allow-host-networks set container name sflow-rt arguments '-Dhttp.hostname=10.0.0.240' set container name sflow-rt environment RTMEM value 200M set container name sflow-rt memory 0 set container name sflow-rt volume store source /config/sflow-rt set container name sflow-rt volume store destination /sflow-rt/storeConfigure a container to run the image. The RMEM environment variable setting limits the amount of memory that the container will use to 200M bytes. The -Dhttp.hostname argument sets the internal web server to listen on management address, 10.0.0.240, assigned to eth0 on this router. The container has is no built-in authentication, so access needs to be limited using an ACL or through a reverse proxy - see Download and install.
set system sflow interface eth0 set system sflow interface eth1 set system sflow interface Continue reading
Oxy: the journey of graceful restarts
Any software under continuous development and improvement will eventually need a new version deployed to the systems running it. This can happen in several ways, depending on how much you care about things like reliability, availability, and correctness. When I started out in web development, I didn’t think about any of these qualities; I simply blasted my new code over FTP directly to my /cgi-bin/ directory, which was the style at the time. For those of us producing desktop software, often you sidestep this entirely by having the user save their work, close the program and install an update – but they usually get to decide when this happens.
At Cloudflare we have to take this seriously. Our software is in constant use and cannot simply be stopped abruptly. A dropped HTTP request can cause an entire webpage to load incorrectly, and a broken connection can kick you out of a video call. Taking away reliability creates a vacuum filled only by user frustration.
The limitations of the typical upgrade process
There is no one right way to upgrade software reliably. Some programming languages and environments make it easier than others, but in a Turing-complete language few things are impossible.
netlab Release 1.5.1: VLAN and VRF Links
netlab release 1.5.1 makes it easier to create topologies with lots of VRF- or VLAN access links, or topologies with numerous similar links. It also includes support for D2 diagram scripting language in case you prefer its diagrams over those generated by Graphviz.
Even if you don’t find those features interesting (more about them later), you might want to upgrade to fix a nasty container-related behavior I discovered in recently-upgraded Ubuntu servers.
