Brocade BNA API
Brocade Network Advisor (BNA) has a REST API for accessing Fibre Channel-related data. The documentation includes a sample Python script showing how to connect to the API to retrieve Fabric info. The script given only works with Python 3.x. It’s also a pain to copy out of the documentation as you end up with a few extra characters in there. Here’s a version that will work with Python 2.7. I’ve also made a few other modifications – in this one, you can set the BNA IP, Username & Password at the top of the script. I’ve also made it PEP8-compliant.
#!/usr/bin/env python
import httplib
import json
import sys
BNAServer = "10.200.5.181"
BNAUsername = "Administrator"
BNAPassword = "password"
# Create HTTPConnection object and connect to the server.
connection = httplib.HTTPConnection(BNAServer)
###########################
# Log in to Network Advisor
###########################
# Send login request
connection.request(
'POST',
'/rest/login',
headers={
"WSUsername": BNAUsername,
"WSPassword": BNAPassword,
"Accept": "application/vnd.brocade.networkadvisor+json;version=v1"}
)
print()
print("Sending login request to Network Advisor...")
# Get the response
response = connection.getresponse()
# Display the response status print()
print ("Status= ", response.status)
# If successful (status = 200), display the returned session token
if response.status Continue reading
Intelligent Bandwidth Decisions at the WAN Edge
Business Critical Applications and Intelligent Decision Making at the WAN Edge….. these are the things I’ve been focusing on in the past few blogs. To me, PfRv3 and DMVPN are the dynamic duo of Cisco’s IWAN that help you learn about and avoid impairments (delay, loss, jitter) along the path that business critical traffic takes.
Let’s take this even further though. How else can IWAN’s Intelligent Path Control help us apply the mentality of the 7Ps (“Prior proper preparation prevents piss poor performance”) to our network and to business critical traffic?
Knowledge… information gathering… awareness. These are the first steps. Once you have the knowledge you can make intelligent decisions based on that knowledge at the WAN edge.
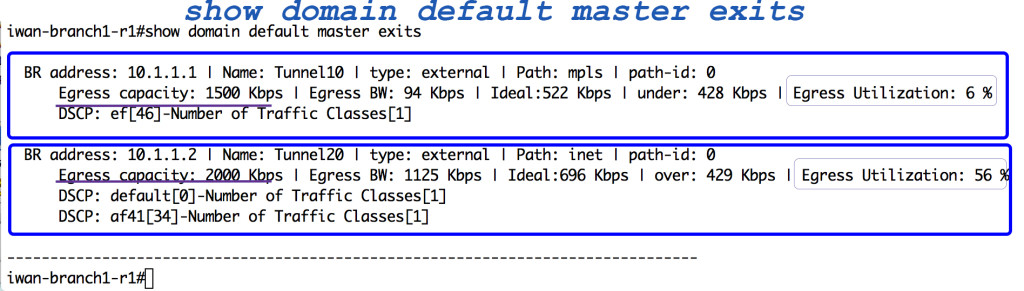
What knowledge?  How about the bandwidth of your WAN links? Wouldn’t it be nice to have facts, such as what their current bandwidth utilization is, be a part of the Intelligent decision making at the WAN edge?
How about the bandwidth of your WAN links? Wouldn’t it be nice to have facts, such as what their current bandwidth utilization is, be a part of the Intelligent decision making at the WAN edge?
We can do that for you now. We can use what your current egress utilization is on your WAN links in the intelligent decision making process that PfRv3 does for you at Continue reading
MikroTik CCR1072-1G-8S+ Review – Part 3 – 80 Gbps Throughput testing
[adrotate banner=”5″]
[metaslider id=249]
The 80 Gbps barrier has finally been broken (and yes we are rounding up) !!!!
Well at least it has been reached by someone other than MikroTik. It’s taken us quite a while to get all the right pieces to push 80 Gbps of traffic through the CC1072 but with the latest round of servers that just got delivered to our lab, we were able to go beyond our previous high water mark of 54 Gbps all the way to just under 80 Gbps. There have been a number of questions about this particular router and what the performance will look like in the real world. While this is still a lab test, we are using non-MikroTik equipment and iperf which is considered an extremely accurate performance measuring tool for TCP and UDP.
Video of the CCR1072-1G-8S+ in action (Turn up your volume to hear the roar of the ESXi servers as they approach 80 Gbps)
How we did it – The Hardware
CCR1072-1G-8S+ – Obviously you can’t have a test of the CCR1072 without one to test on. Our CCR1072-1G-8S+ is a pre-production model so there are some minor differences between it and the Continue reading
MikroTik CCR1072-1G-8S+ Review – Part 3 – 80 Gbps Throughput testing
[adrotate banner=”5″]
[metaslider id=249]
The 80 Gbps barrier has finally been broken (and yes we are rounding up) !!!!
Well at least it has been reached by someone other than MikroTik. It’s taken us quite a while to get all the right pieces to push 80 Gbps of traffic through the CC1072 but with the latest round of servers that just got delivered to our lab, we were able to go beyond our previous high water mark of 54 Gbps all the way to just under 80 Gbps. There have been a number of questions about this particular router and what the performance will look like in the real world. While this is still a lab test, we are using non-MikroTik equipment and iperf which is considered an extremely accurate performance measuring tool for TCP and UDP.
Video of the CCR1072-1G-8S+ in action (Turn up your volume to hear the roar of the ESXi servers as they approach 80 Gbps)
How we did it – The Hardware
CCR1072-1G-8S+ – Obviously you can’t have a test of the CCR1072 without one to test on. Our CCR1072-1G-8S+ is a pre-production model so there are some minor differences between it and the Continue reading
Xirrus Offers New Security Option For Public Wi-Fi
Xirrus is launching a new security feature to encrypt wireless connections between a device and an AP on a public Wi-Fi network. While it's easy to use, it does have limitations.
The post Xirrus Offers New Security Option For Public Wi-Fi appeared first on Packet Pushers.
Dispelling the myths of hybrid hosting
This vendor-written tech primer has been edited by Network World to eliminate product promotion, but readers should note it will likely favor the submitter’s approach.
When the Amazon Web Services platform failed recently some of the internet’s biggest sites -- including Netflix and Tinder – suffered extended outages. The culprit? AWS's NoSQL database DynamoDB, where increased error rates led to increased errors and latency in more than 20 AWS services.
These and other sites wouldn’t have had a problem if they used hybrid hosting, the best way to architect modern apps. Hybrid hosting lets businesses set up their databases on dedicated servers, put their front-end Web apps in the cloud, then tie everything together with a single click.
To read this article in full or to leave a comment, please click here
AWS Wants an Even Bigger Piece of IoT
 IoT has already come to AWS. Amazon wants to take advantage by making the Internet of Things even easier.
IoT has already come to AWS. Amazon wants to take advantage by making the Internet of Things even easier.
WLAN Spending Fuels Enterprise Network Market Growth
Companies are upgrading their networks to increase wireless capacity while moving cautiously with SDN, new market research shows.NetDevOps: Networking Methods with a DevOps Mindset
DevOps brings together software developers and IT operations through mutual and organic cooperation and collaboration. In legacy IT shops, the roles of developers and IT operations are logically segregated, which stifles progress and prohibits progressive integration efforts. Products that leverage DevOps provide developers self-service capabilities they’ve never had before — eliminating provisioning bottlenecks and adapting to changes quickly. The platform becomes highly scalable and flexible, removing much of the “red tape” in getting things done.
This is all well and good, and is often sufficient for most, but networking is often neglected as a part of the DevOps model. Common questions that arise include the following:
- Is your current networking strategy holding you back from scaling new projects quickly?
- Is your network topology designed to quickly add and remove compute infrastructure?
- How can your network integrate in a DevOps orchestrated world?
This is where including DevOps for networking comes in, or “NetDevOps.” Traditional networking infrastructure can be difficult to manage when requiring agility with updated tools. If your organization is already implementing DevOps principles or has an organization that is flat or non-siloed, integrating networking into your framework may be right for you.
NetDevOps extends what you’re already doing Continue reading
PQ 58: Alibi Routing With UMD’s Dave Levin
In this podcast, Packet Pushers co-host Ethan Banks gets a bit into the weeds with University of Maryland's Dave Levin in this detailed discussion of Alibi Routing, a privacy-driven research project to prove that traffic flowing between a particular source and destination did not traverse a specific geographic region.
The post PQ 58: Alibi Routing With UMD’s Dave Levin appeared first on Packet Pushers.
Banks Bet Their Money On Private Cloud
As banks move toward a cloud-based infrastructure, they must protect their assets while understanding that the network is a fundamental contributor to the cloud and to their customers' quality of experience.Doubling the speed of jpegtran with SIMD
It is no secret that at CloudFlare we put a great effort into accelerating our customers' websites. One way to do it is to reduce the size of the images on the website. This is what our Polish product is for. It takes various images and makes them smaller using open source tools, such as jpegtran, gifsicle and pngcrush.
However those tools are computationally expensive, and making them go faster, makes our servers go faster, and subsequently our customers' websites as well.
Recently, I noticed that we spent ten times as much time "polishing" jpeg images as we do when polishing pngs.
We already improved the performance of pngcrush by using our supercharged version of zlib. So it was time to look what can be done for jpegtran (part of the libjpeg distribution).
Quick profiling
To get fast results I usually use the Linux perf utility. It gives a nice, if simple, view of the hotspots in the code. I used this image for my benchmark.
perf record ./jpegtran -outfile /dev/null -progressive -optimise -copy none test.jpeg
And we get:
perf report
54.90% lt-jpegtran libjpeg.so.9.1.0 [.] encode_mcu_AC_refine
Continue reading
Douglas Comer on the Future of Networking
Jim Small asked me what I thought about the Future of Networking Packet Pushers podcast with Douglas Comer. I decided to listen to it while driving toward one of my recent hikes, and it was a great decision– it was the best Packet Pushers podcast I listened to in a long while.
Read more ...